VMware 2V0-81-20 Exam Questions
Questions for the 2V0-81-20 were updated on : Jul 11 ,2025
Page 1 out of 5. Viewing questions 1-15 out of 70
Question 1
Which file can be used to validate repcli authentication was enabled for Carbon Black Cloud?
- A. C:\Program Files\Confer\repcii.ini
- B. C:\Program Files\Confer\config.ini
- C. C:\Program Files\Confer\cfg.ini
- D. C:\Program Files\Confer\cli.ini
Answer:
A
Reference:
https://community.carbonblack.com/t5/Knowledge-Base/Carbon-Black-Cloud-How-to-
Enable-RepCLI-Authentication-on/ta-p/70393
Question 2
Which is the correct Distinguished Name for connecting NSX-T Data Center to Active Directory, if
your directory name is corp. local?
- A. corp. local
- B. DC=corp. local
- C. DC=corp, DC=local
- D. DC=local, DC=corp
Answer:
C
Reference:
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.1/administration/GUID-8B60D22B-3119-48F6-AEAE-AE27A9372189.html
Question 3
What are two valid time limit selections when creating a Last Seen compliance policy in Workspace
ONE UEM? (Choose two.)
- A. Hours
- B. Minutes
- C. Days
- D. Weeks
- E. Months
Answer:
B, C
Reference:
https://www.niap-ccevs.org/MMO/Product/st_vid11026-aar.pdf
(47)
Question 4
Which is true about Time-Based Firewall Policy rules?
- A. Time-Based policy rules apply only to the NSX Distributed Firewall.
- B. Time-Based policy rules apply to the NSX Gateway and Distributed Firewall.
- C. Time-Based policy rules can only be used one time for NSX Gateway Firewall.
- D. Time-Based policy rules apply only to the NSX Gateway Firewall.
Answer:
B
Reference:
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.1/administration/GUID-8572496E-A60E-48C3-A016-4A081AC80BE7.html
Question 5
An administrator found an unwanted/untrusted application running in their environment.
What is the most efficient way of preventing the unwanted application from running and stopping
any existing instances in Carbon Black Cloud?
- A. Mark the file as a PUP (Potentially Unwanted Program).
- B. Add a rule to each policy for unwanted.exe runs or if running terminate.
- C. Send a delete application request to each machine.
- D. Add the unwanted files hash to the company banned list.
Answer:
D
Reference:
https://community.carbonblack.com/gbouw27325/attachments/gbouw27325/product-
docs-news/3221/1/VMware%20Carbon%20Black%20App%20Control%20User%20Guide%20v8.6.pdf
(77)
Question 6
In the NSX Manager UI, which tab is selected to manage firewall rules?
- A. Plan & Troubleshoot tab
- B. Security tab
- C. Inventory tab
- D. Networking tab
Answer:
B
Question 7
Which is the name of the default policy that is applied to all applications in Workspace ONE Access?
- A. primary_policy
- B. default_policy
- C. default_access_policy_set
- D. default_application_policy
Answer:
C
Reference:
https://theidentityguy.ca/2021/02/25/workspace-one-access-best-practices-in-policy-
management/
Question 8
In a Carbon Black Cloud deployment, which two are recommended troubleshooting steps for Live
Response not working? (Choose two.)
- A. Restart the Live Response Service three times to autocorrect.
- B. Ensure a duplicate Live Response session does not exist.
- C. Confirm Live Response is enabled in Sensor Policy settings.
- D. Ensure the account has RBAC permission for Live Response.
- E. Confirm the Live Response timeline spans the search window.
Answer:
C, D
Reference:
https://developer.carbonblack.com/reference/carbon-black-cloud/platform/latest/live-
response-api/
Question 9
When creating a sensor group in VMware Carbon Black Cloud, which three are valid criteria? (Choose
three.)
- A. Location Name
- B. Organizational Username
- C. Active Directory Organizational Unit
- D. Subnet
- E. Device Name
Answer:
C, D, E
Reference:
https://docs.vmware.com/en/VMware-Carbon-Black-Cloud/services/carbon-black-cloud-user-guide/GUID-741989BE-4844-4953-B7FE-89A05A81EBE7.html
Question 10
An organization is expanding NSX to deploy the NSX Distributed Firewall on an AWS VPC and Azure
VNET.
Which statement is true concerning the expansion?
- A. The request is not possible because NSX works only in VMware environments.
- B. NSX can only manage native security components on AWS and Azure with agent based mode.
- C. NSX can only do an agent based mode on AWS and Azure.
- D. NSX can choose native security components on AWS and Azure or agent based mode.
Answer:
B
Reference:
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.1/administration/GUID-9522BEC9-E85E-41DC-8AF5-2652A647730F.html
Question 11
What is the correct sequence of options when creating a new compliance policy in Workspace ONE
UEM?
- A. Actions, Assignment, Rules, Summary
- B. Rules, Actions, Assignment, Summary
- C. Assignment, Rules, Actions, Summary
- D. Rules, Assignment, Actions, Summary
Answer:
B
Reference:
https://docs.vmware.com/en/VMware-Workspace-ONE-UEM/services/UEM_Managing_Devices/GUID-AddACompliancePolicy.html
Question 12
Which is the built-in two factor authentication method in Workspace ONE Access?
- A. VMware Verify
- B. VMware SMS
- C. VMware Auth
- D. VMware Push
Answer:
A
Reference:
https://docs.vmware.com/en/VMware-Workspace-ONE-Access/services/ws1_access_authentication_cloud/GUID-FE8A5B1C-BC17-4A5C-BC8D-614C5EE4057A.html
Question 13
Refer to the exhibit.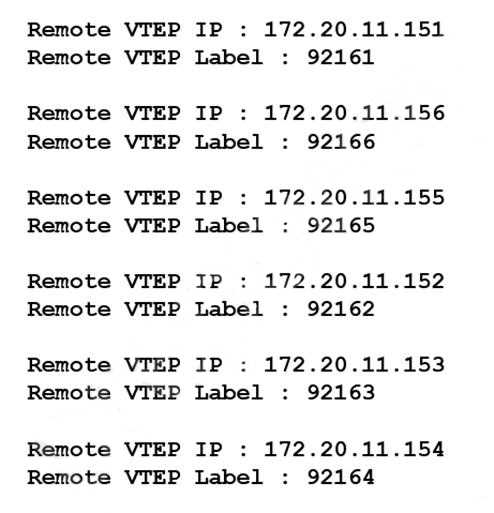
What command was run on the NSX Edge node to pull this information?
- A. get tunnel-ID
- B. show vteps
- C. get vteps
- D. list vteps
Answer:
C
Reference:
https://vdc-download.vmware.com/vmwb-repository/dcr-public/c3fd9cef-6b2b-4772-93be-3fe60ce064a1/1f67b9e1-b111-4de7-9ea1-39931d28f560/NSX-T%20Command-Line%20Interface%20Reference.html#get%20vteps
Question 14
What command does an administrator use on an ESXi Transport Node to check connectivity with the
management plane?
- A. esxcli network ip connection list 1234
- B. esxcli firewall ip connection list | grep 1234
- C. esxcli ip connection 1234
- D. esxcli network ip connection list | grep 1234
Answer:
D
Reference:
https://docs.vmware.com/en/VMware-NSX-Data-Center-for-vSphere/6.4/com.vmware.nsx.troubleshooting.doc/GUID-18EDB577-1903-4110-8A0B-FE9647ED82B6.html
Question 15
Which Carbon Black Cloud feature allows an administrator to audit at scale and identify gaps in least
privilege configuration controls?
- A. Watchlist
- B. Live Query
- C. Investigate
- D. CB Baseline Tool
Answer:
C
Reference:
https://community.carbonblack.com/gbouw27325/attachments/gbouw27325/product-
docs-news/3221/1/VMware%20Carbon%20Black%20App%20Control%20User%20Guide%20v8.6.pdf