VMware 1V0-81-20 Exam Questions
Questions for the 1V0-81-20 were updated on : Jul 06 ,2025
Page 1 out of 4. Viewing questions 1-15 out of 55
Question 1
Which VMware product allows you to query an endpoint like a database?
- A. VMware NSX-T Data Center
- B. VMware Carbon Black Audit & Remediation
- C. VMware Workspace ONE UEM
- D. VMware Carbon Black Endpoint Standard
Answer:
C
Question 2
Which three are industry best practices of Zero Trust framework? (Choose three.)
- A. Employee machines need to have a passcode profile setup
- B. Employee machines on Internal network are trusted and have access to all internal resources
- C. Employee machines are checked for compliance before they get access to applications
- D. Employees are not required to provide MFA to access internal resources over VPN
- E. Employees get access to only the required resources to get their job done
Answer:
A, C, E
Question 3
Which three default connectors are available in Workspace ONE Intelligence to execute automation
actions? (Choose three.)
- A. ServiceNow
- B. vRealize Operations Manager
- C. Slack
- D. Log Insight
- E. Workspace ONE UEM
Answer:
A, C, E
Explanation:
Reference:
https://docs.vmware.com/en/VMware-Workspace-ONE/services/intelligence-documentation/GUID-21_intel_automations.html
Question 4
Refer to the exhibit.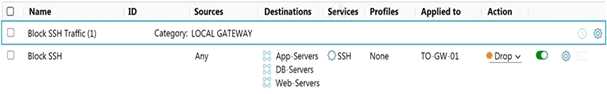
Which statement is true about the firewall rule?
- A. It is a gateway firewall applied to a Tier-0 gateway that drops traffic on port 22
- B. It is a distributed firewall applied to App-Services, DB-Servers and Web-Servers that rejects traffic on port 22
- C. It is a distributed firewall applied to App-Services, DB-Servers and Web-Servers that drops traffic on port 22
- D. It is a gateway firewall applied to a Tier-0 gateway that rejects traffic on port 22
Answer:
A
Question 5
Refer to the exhibit.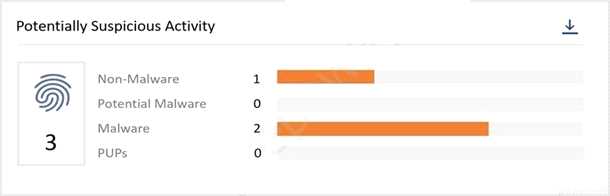
From the VMware Carbon Black Cloud console, what page do you go to after clicking the Non-
Malware bar in the Potentially Suspicious Activity chart?
- A. Notifications page with the selected alert filtered
- B. Reputations page with the selected reputation filtered
- C. Investigate page with the selected reputation filtered
- D. Alerts page with the selected alert filtered
Answer:
D
Reference:
https://docs.vmware.com/en/VMware-Carbon-Black-Cloud/services/carbon-black-cloud-
user-guide.pdf
(15)
Question 6
Which four alert filters are available in the VMware Carbon Black Cloud Investigate page? (Choose
four.)
- A. Watchlist
- B. Target Value
- C. Policy
- D. Security Alert List
- E. Effective Reputation
- F. Alert Severity
Answer:
A, B, C, F
Question 7
Which is a common solution to implement for inbound network attacks?
- A. Load Balancer
- B. Firewall
- C. Proxy
- D. Reverse Proxy
Answer:
B
Question 8
Which two are true about a VMware Service-defined Firewall? (Choose two.)
- A. A firewall that allows you to use 3rd party features like IDS/IPS, threat protection, anti-bot, and anti-virus solutions
- B. A firewall that blocks external access into your internal network based on IP services
- C. A firewall that enforces policy for North-South traffic
- D. A firewall that is auto scalable as new workloads are deployed
- E. A firewall that provides East-West protection between internal applications
Answer:
A, E
Question 9
Which of the following is true about VMware Carbon Black Cloud Enterprise EDR watchlists?
- A. They only update annually
- B. You cannot customize them
- C. They are made up of reports
- D. Each watchlist is user specific
Answer:
D
Reference:
https://docs.vmware.com/en/VMware-Carbon-Black-
EDR/7.5/VMware%20Carbon%20Black%20EDR%207.5%20User%20Guide.pdf
Question 10
A technician has been asked to confirm a specific browser extension does not exist on any endpoint
in their environment.
Which is the VMware Carbon Black tool to use for this task?
- A. Enterprise EDR
- B. EDR
- C. Audit and Remediation
- D. Endpoint Standard
Answer:
A
Question 11
Which three Workspace ONE UEM capabilities are used to configure security policies on Windows 10
desktops? (Choose three.)
- A. Application Profiles
- B. Custom XML
- C. Custom Attributes
- D. Baselines
- E. Native Profiles
Answer:
B, C, D
Explanation:
Reference:
https://docs.vmware.com/en/VMware-Workspace-ONE-UEM/services/Windows_Desktop_Device_Management/GUID-uemWindeskProfiles.html
Question 12
Which would require a Layer 7 Firewall?
- A. block a specific port
- B. block a subnet range
- C. block a host
- D. block a specific application
Answer:
D
Explanation:
Reference:
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.1/administration/GUID-8F3CB282-B38E-49E1-951A-7D6B972B1FB7.html
Question 13
VMware’s Intrinsic Security layer includes functionality for which control points?
- A. networks, workloads, endpoints, identity, and clouds
- B. applications, workloads, devices, identity, virtual infrastructure
- C. networks, containers, devices, users, and VMware Cloud
- D. applications, users, networks, data center perimeter, vSphere
Answer:
A
Reference:
https://www.globalknowledge.com/en-gb/resources/articles/what-is-intrinsic-security
Question 14
Which three are key features of VMware Carbon Black Cloud Enterprise EDR? (Choose three.)
- A. self-service security remediation
- B. continuous and centralized recording
- C. attack chain visualization and search
- D. live response for remote remediation
- E. frequent Antivirus pattern updates
Answer:
B, C, D
Reference:
https://www.vmware.com/content/dam/digitalmarketing/vmware/en/pdf/docs/vmwcb-
enterprise-edr-datasheet.pdf
(2)
Question 15
What are three core characteristics of VMware’s Intrinsic Security solution? (Choose three.)
- A. integrated
- B. extensible
- C. unified
- D. content-centric
- E. centrally managed
- F. built-in
Answer:
A, C, F