Splunk SPLK-5001 Exam Questions
Questions for the SPLK-5001 were updated on : Feb 18 ,2026
Page 1 out of 7. Viewing questions 1-15 out of 99
Question 1
An analysis of an organization’s security posture determined that a particular asset is at risk and a
new process or solution should be implemented to protect it. Typically, who would be in charge of
designing the new process and selecting the required tools to implement it?
- A. SOC Manager
- B. Security Engineer
- C. Security Architect
- D. Security Analyst
Answer:
C
Question 2
According to David Bianco's Pyramid of Pain, which indicator type is least effective when used in
continuous monitoring?
- A. Domain names
- B. TTPs
- C. NetworM-lost artifacts
- D. Hash values
Answer:
D
Question 3
Refer to the exibit.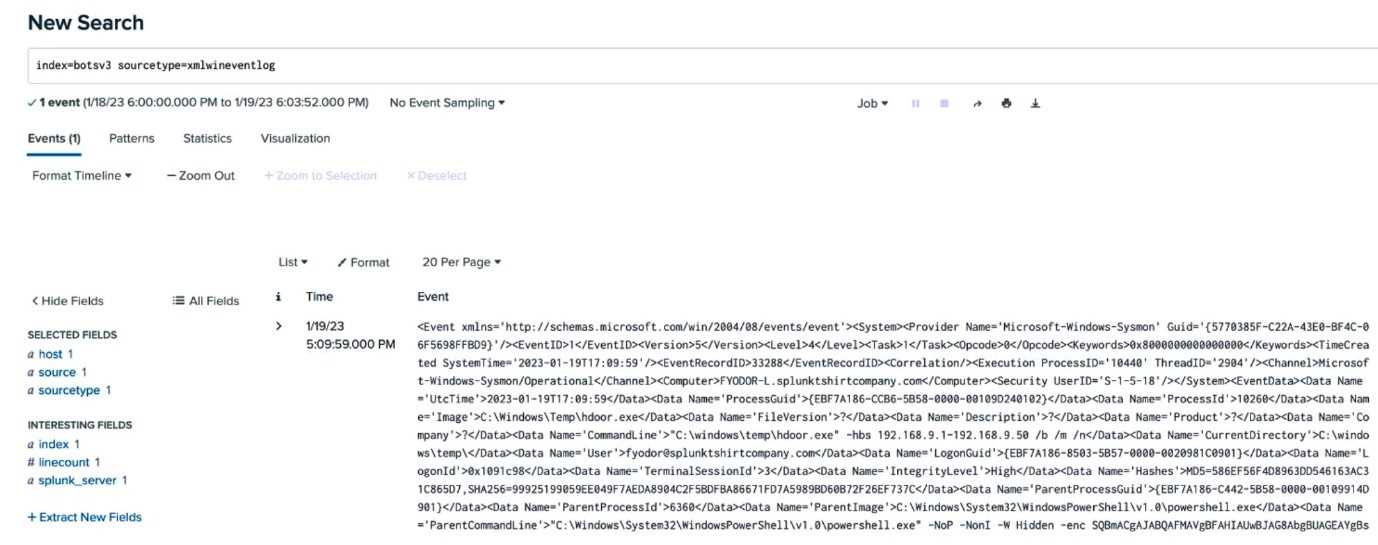
An analyst is building a search to examine Windows XML Event Logs, but the initial search is not
returning any extracted fields. Based on the above image, what is themost likelycause?
- A. The analyst does not have the proper role to search this data.
- B. The analyst is searching newly indexed data that was improperly parsed.
- C. The analyst did not add the excract command to their search pipeline.
- D. The analyst is not in the Drooer Search Mode and should switch to Smart or Verbose.
Answer:
D
Question 4
An analyst is attempting to investigate a Notable Event within Enterprise Security. Through the
course of their investigation they determined that the logs and artifacts needed to investigate the
alert are not available.
What event disposition should the analyst assign to the Notable Event?
- A. Benign Positive, since there was no evidence that the event actually occurred.
- B. False Negative, since there are no logs to prove the activity actually occurred.
- C. True Positive, since there are no logs to prove that the event did not occur.
- D. Other, since a security engineer needs to ingest the required logs.
Answer:
D
Question 5
An analyst investigates an IDS alert and confirms suspicious traffic to a known malicious IP. What
Enterprise Security data model would they use to investigate which process initiated the network
connection?
- A. Endpoint
- B. Authentication
- C. Network traffic
- D. Web
Answer:
A
Question 6
The Security Operations Center (SOC) manager is interested in creating a new dashboard for
typosquatting after a successful campaign against a group of senior executives. Which existing ES
dashboard could be used as a starting point to create a custom dashboard?
- A. IAM Activity
- B. Malware Center
- C. Access Anomalies
- D. New Domain Analysis
Answer:
D
Question 7
An organization is using Risk-Based Alerting (RBA). During the past few days, a user account
generated multiple risk observations. Splunk refers to this account as what type of entity?
- A. Risk Factor
- B. Risk Index
- C. Risk Analysis
- D. Risk Object
Answer:
D
Question 8
An adversary uses "LoudWiner" to hijack resources for crypto mining. What does this represent in a
TTP framework?
- A. Procedure
- B. Tactic
- C. Problem
- D. Technique
Answer:
A
Question 9
An analysis of an organization’s security posture determined that a particular asset is at risk and a
new process or solution should be implemented to protect it. Typically, who would be in charge of
implementing the new process or solution that was selected?
- A. Security Architect
- B. SOC Manager
- C. Security Engineer
- D. Security Analyst
Answer:
C
Question 10
Upon investigating a report of a web server becoming unavailable, the security analyst finds that the
web server’s access log has the same log entry millions of times:
147.186.119.200 - - [28/Jul/2023:12:04:13 -0300] "GET /login/ HTTP/1.0" 200 3733
What kind of attack is occurring?
- A. Denial of Service Attack
- B. Distributed Denial of Service Attack
- C. Cross-Site Scripting Attack
- D. Database Injection Attack
Answer:
A
Question 11
Which of the following Splunk Enterprise Security features allows industry frameworks such as CIS
Critical Security Controls, MITRE ATT&CK, and the Lockheed Martin Cyber Kill Chain® to be mapped
to Correlation Search results?
- A. Annotations
- B. Playbooks
- C. Comments
- D. Enrichments
Answer:
A
Question 12
During their shift, an analyst receives an alert about an executable being run from
C:\Windows\Temp. Why should this be investigated further?
- A. Temp directories aren't owned by any particular user, making it difficult to track the process owner when files are executed.
- B. Temp directories are flagged as non-executable, meaning that no files stored within can be executed, and this executable was run from that directory.
- C. Temp directories contain the system page file and the virtual memory file, meaning the attacker can use their malware to read the in memory values of running programs.
- D. Temp directories are world writable thus allowing attackers a place to drop, stage, and execute malware on a system without needing to worry about file permissions.
Answer:
D
Question 13
A threat hunter executed a hunt based on the following hypothesis:
As an actor, I want to plant rundll32 for proxy execution of malicious code and leverage Cobalt Strike
for Command and Control.
Relevant logs and artifacts such as Sysmon, netflow, IDS alerts, and EDR logs were searched, and the
hunter is confident in the conclusion that Cobalt Strike is not present in the company’s environment.
Which of the following best describes the outcome of this threat hunt?
- A. The threat hunt was successful because the hypothesis was not proven.
- B. The threat hunt failed because the hypothesis was not proven.
- C. The threat hunt failed because no malicious activity was identified.
- D. The threat hunt was successful in providing strong evidence that the tactic and tool is not present in the environment.
Answer:
D
Question 14
According to Splunk CIM documentation, which field in the Authentication Data Model represents
the user who initiated a privilege escalation?
- A. dest_user
- B. src_user_id
- C. src_user
- D. username
Answer:
C
Question 15
An analyst is looking at Web Server logs, and sees the following entry as the last web request that a
server processed before unexpectedly shutting down:
[51.125.121.100 - [28/01/2006:10:27:10 -0300] "POST /cgi-bin/shurdown/ HTTP/1.0" 200 3304]
What kind of attack is most likely occurring?
- A. Distributed denial of service attack.
- B. Database injection attack.
- C. Denial of service attack.
- D. Cross-Site scripting attack.
Answer:
C