Splunk SPLK-2003 Exam Questions
Questions for the SPLK-2003 were updated on : Feb 18 ,2026
Page 1 out of 8. Viewing questions 1-15 out of 110
Question 1
How can a user with the username "pat" configure the Analyst Queue to only show new events that
are assigned to the current user?
- A. Create a filter for label-new and owner-pat.
- B. Create a filter for status-open and owner-pat.
- C. Create a filter for status=new and owner=pat.
- D. Create a filter for status=new or owner=pat.
Answer:
C
Explanation:
To configure the Analyst Queue to only show new events that are assigned to the current user "pat",
the correct filter would involve two conditions:
status=new: This ensures that only new events are displayed.
owner=pat: This ensures that the displayed events are specifically assigned to the user "pat."
By applying both of these filters, the user will only see events that are both in the "new" status and
assigned to them. The other options, such as filtering for "label" or using "or" in the filter, would
either result in showing incorrect data or broader results that are not restricted to new events
assigned to the user.
Reference:
Splunk SOAR Documentation: Analyst Queue Filters.
Splunk SOAR User Guide for Customizing Event Views.
Question 2
Regarding the Splunk SOAR Automation Broker requirements, which of the following statements is
not correct?
- A. The Splunk SOAR Automation Broker requires outbound/egress connectivity to the Splunk SOAR (Cloud) or Splunk SOAR (On-premises) instance.
- B. The Splunk SOAR Automation Broker must be able to connect to TCP port 443 (HTTPS) on the Splunk SOAR (Cloud) or Splunk SOAR (On-premises) instance.
- C. The Splunk SOAR Automation Broker requires both inbound/ingress and outbound/egress connectivity to the Splunk SOAR (Cloud) or Splunk SOAR (On-premises) instance.
- D. The Splunk SOAR Automation Broker requires inbound/ingress network connection from the Splunk SOAR (Cloud) or Splunk SOAR (On-premises) instance.
Answer:
D
Explanation:
The Splunk SOAR Automation Broker does not require inbound/ingress network connections from
the Splunk SOAR (Cloud) or (On-premises) instance. Instead, it requires only outbound/egress
connectivity. The Automation Broker is responsible for securely communicating with SOAR to execute
actions, retrieve data, and send results, but this communication is initiated from the Automation
Broker towards SOAR, using outbound connections (typically over TCP port 443). This ensures that no
inbound connections need to be established, which simplifies firewall and security configurations.
Thus, option D is the incorrect statement, making it the right answer for this question.
Reference:
Splunk SOAR Documentation: Automation Broker Requirements.
Splunk SOAR Cloud and On-Premises Deployment Guide.
Question 3
Which of the following is true about a child playbook?
- A. The child playbook does not have access to the parent playbook's container or action result data.
- B. The child playbook does not have access to the parent playbook's container, but to the parent's action result data.
- C. The child playbook has access to the parent playbook's container and the parent's action result data.
- D. The child playbook has access to the parent playbook's container, but not to the parent's action result data.
Answer:
C
Explanation:
In Splunk SOAR, a child playbook can access both the container data and the action result data from
the parent playbook. This capability allows child playbooks to continue processing data or actions
that were initiated by the parent playbook, ensuring smooth data flow and facilitating complex
workflows across multiple playbooks. When a parent playbook calls a child playbook, the container
(which holds the event and artifact data) and action results (which hold the outputs of previously
executed actions) are passed to the child playbook.
This access enables more flexible and powerful automation by allowing the child playbook to build
upon the work done by the parent.
Reference:
Splunk SOAR Playbook Documentation.
Splunk SOAR Playbook Development Best Practices.
Question 4
A new project requires event data from SOAR to be sent to an external system via REST. All events
with the label notable that are in new status should be sent. Which of the following REST Django
expressions will select the correct events?
A.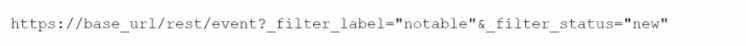
B.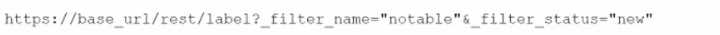
C.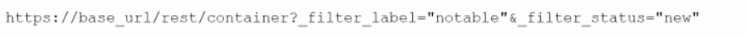
D.
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
C
Explanation:
The correct REST Django expression to retrieve events with the label "notable" that are in the "new"
status is using the container endpoint, as containers are used to store events and associated data in
Splunk SOAR. The expression correctly filters the events by label (_filter_label="notable") and status
(_filter_status="new"), ensuring only notable events that are still in the "new" status are selected.
A and D reference the wrong endpoints (event and notable respectively), which do not align with the
container-based model used in Splunk SOAR for storing and filtering events.
B is incorrect due to the use of _filter_name instead of _filter_label, which is not a valid filter in this
context.
Reference:
Splunk SOAR Documentation: REST API Endpoints.
Splunk SOAR Developer Guide: Using Django REST for Filtering.
Question 5
Playbooks typically handle which types of data?
- A. Container data, Artifact CEF data, Result data. Threat data
- B. Container CEF data, Artifact data, Result data, List data
- C. Container data, Artifact CEF data, Result data, List data
- D. Container data, Artifact data, Result data, Threat data
Answer:
C
Explanation:
Playbooks in Splunk SOAR are designed to handle various types of data to automate responses to
security incidents. The correct types of data handled by playbooks include:
Container Data: Containers are used to group related data for an incident or event. Playbooks can
access this information to perform actions and make decisions.
Artifact CEF Data: Artifacts hold detailed information about the event or incident, including CEF
(Common Event Format) data. Playbooks often process this CEF data for various actions.
Result Data: This refers to the data generated from actions executed by the playbook, such as results
from API calls, integrations, or automated responses.
List Data: Lists in Splunk SOAR are collections of reusable data (such as IP blocklists, whitelists, etc.)
that playbooks can access to check values or make decisions based on external lists.
The inclusion of List data instead of Threat data distinguishes this option from others, as lists are
more directly used by playbooks during execution, whereas threat data is a broader category that is
often processed but not always directly handled by playbooks.
Reference:
Splunk SOAR Documentation: Playbook Data Handling.
Splunk SOAR Best Practices: Automating with Playbooks.
Question 6
Two action blocks, geolocate_ip 1 and file_reputation_2, are connected to a decision block. Which of
the following is a correct configuration for making a decision on the action results from one of the
given blocks?
A.
B.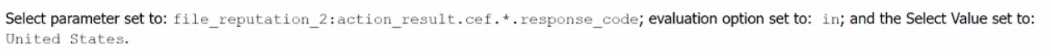
C.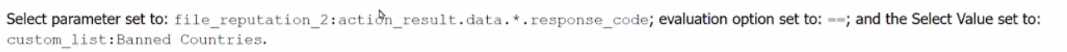
D.
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
A
Explanation:
In the given decision block, you are trying to evaluate the results of two action blocks:
geolocate_ip_1 and file_reputation_2. The correct configuration for making a decision based on the
result of geolocate_ip_1 is by checking the country_iso_code field from the action result and setting
the evaluation option to != (not equal), with no specific value provided in the "Select Value" box. This
essentially checks whether a valid country ISO code exists in the action result and proceeds if it's not
empty or different from a specific value. This is a common check when working with geolocation
results to see if a response has been returned.
Other options (B, C, and D) include response codes or list comparisons, which do not align with the
decision structure mentioned, which needs to operate based on a country_iso_code field.
Reference:
Splunk SOAR Playbook Development Guide.
Splunk SOAR Documentation on Decision Blocks and Action Result Evaluation.
Question 7
Which visual playbook editor block is used to assemble commands and data into a valid Splunk
search within a SOAR playbook?
- A. An action block.
- B. A filter block.
- C. A format block.
- D. A prompt block.
Answer:
C
Explanation:
In Splunk SOAR playbook development, the format block is used to assemble commands and data
into a valid Splunk search query. This block allows users to structure and manipulate strings,
dynamically inserting variables, and constructing the precise format needed for a search query. By
using a format block, playbooks can integrate data from various sources and ensure that it is
assembled correctly before passing it to subsequent actions, such as executing a Splunk search.
Other blocks, like action, filter, and prompt blocks, serve different purposes (e.g., running actions,
filtering data, or prompting for user input), but the format block is specifically designed for building
structured data or queries like Splunk searches.
Reference:
Splunk SOAR Documentation: Playbook Blocks Overview.
Splunk SOAR Playbook Editor Guide: Using the Format Block.
Question 8
Which of the following are tabs of an asset configuration?
- A. Asset Name, Asset IP, Asset URL, Asset Nickname
- B. Tags, Asset Name, Asset Date, Asset Order
- C. App Name, App Order, App Expiry, App Version
- D. Asset Info, Asset Settings, Approval Settings, Access Control
Answer:
D
Explanation:
In Splunk SOAR, the asset configuration consists of several key tabs that are essential for setting up
and managing an asset. These tabs include:
Asset Info: Contains general information about the asset, such as its name and description.
Asset Settings: This tab allows for configuring specific settings related to the asset, including any
connections or integrations.
Approval Settings: This section manages settings related to the approval process for actions that
require explicit authorization.
Access Control: This tab helps control user access to the asset, specifying permissions and roles.
These four tabs are essential for configuring an asset in SOAR, making sure the asset works as
expected and that the right people have access to it.
Reference:
Splunk SOAR Documentation: Asset Configuration.
Splunk SOAR Best Practices: Asset Management and Configuration.
Question 9
Which of the following is the best option for an analyst who wants to run a single action on an event?
- A. Open the event and run this single action from the Investigation View.
- B. Create a playbook with a single action then use the Playbook Debugger on the event ID.
- C. Create a playbook with the action and run it from the Investigation View.
- D. Open a playbook with a single action, mark it active, and then use the Playbook Debugger on the event ID.
Answer:
A
Explanation:
The best option for an analyst who wants to run a single action on an event is to open the event and
run the action directly from the Investigation View. The Investigation View allows users to interact
with events directly, and provides the ability to execute specific actions without the need for
playbook development or debugging. This is the most straightforward and efficient way to execute a
single action on an event, without the overhead of creating or editing playbooks.
While creating a playbook and using the Playbook Debugger are viable options, they introduce
unnecessary complexity for running just one action. The goal is to allow the analyst to act quickly and
efficiently within the Investigation View.
Reference:
Splunk SOAR Documentation: Investigation View Overview.
Splunk SOAR Best Practices for Running Actions on Events.
Question 10
How can parent and child playbooks pass information to each other?
- A. The parent can pass arguments to the child when called, and the child can return values from the end block.
- B. The parent can pass arguments to the child when called, but the child can only pass values back as new artifacts in the event.
- C. The parent must create a new artifact in the event named arg_xxx, and the child must return values by creating artifacts with the naming convention return_xxx.
- D. The parent must create a new artifact in the event named return_xxx, and the child must return values by creating artifacts with the naming convention arg_xxx.
Answer:
A
Explanation:
In Splunk SOAR, parent and child playbooks can pass information between each other using
arguments. The parent playbook can pass specific arguments to the child playbook when it is called,
enabling the child playbook to utilize these values in its execution. Once the child playbook finishes
its execution, it can return values through the end block. This mechanism allows for efficient and
structured communication between parent and child playbooks, enabling complex, multi-step
automation workflows.
Other options are incorrect because creating artifacts with specific naming conventions is not
necessary for passing information between playbooks, and artifacts are not used for argument or
result passing between playbooks in this manner.
Reference:
Splunk SOAR Documentation: Playbook Development Guide.
Splunk SOAR Best Practices: Parent and Child Playbooks Communication.
Question 11
Which of the following cannot be marked as evidence in a container?
- A. Action result
- B. Artifact
- C. Note
- D. Comment
Answer:
D
Explanation:
In Splunk SOAR, the following elements can be marked as evidence within a container: action results,
artifacts, and notes. These are crucial elements that contribute directly to incident analysis and can
be selected as evidence to support investigation outcomes or legal proceedings.
However, comments cannot be marked as evidence. Comments are usually informal and meant for
communication between users, providing context or updates but not serving as formal evidence
within the system. Action results, artifacts, and notes, on the other hand, contain critical data related
to the incident that could be useful for audit and investigative purposes, making them eligible to be
marked as evidence.
Reference:
Splunk SOAR Documentation: Working with Evidence.
Splunk SOAR Best Practices: Evidence Collection and Management.
Question 12
Which of the following views provides a holistic view of an incident - providing event metadata,
Service Level Agreement status, Severity, sensitivity of an event, and other detailed event info?
- A. Executive
- B. Investigation
- C. Technical
- D. Analyst
Answer:
B
Explanation:
The Investigation view in Splunk SOAR provides a comprehensive and holistic view of an incident.
This view includes vital details such as event metadata, Service Level Agreement (SLA) status,
severity, sensitivity of the event, and other relevant information. It allows analysts to track and
manage incidents effectively by presenting a clear picture of all aspects of the investigation process.
This view is designed to help users take timely actions based on critical data points, making it a
pivotal feature for incident response teams.
Other views like Executive or Analyst may focus on specific reporting or technical details, but the
Investigation view provides the most complete perspective on the incident and its progress.
Reference:
Splunk SOAR Documentation: Investigation View Overview.
Splunk SOAR Incident Response Best Practices.
Question 13
Which of the following items cannot be modified once entered into SOAR?
- A. A container.
- B. An artifact.
- C. A comment.
- D. A note.
Answer:
B
Explanation:
In Splunk SOAR, once an artifact is entered, it cannot be modified. An artifact refers to a piece of data
associated with a specific container, such as log files, emails, or other relevant information in an
incident. The immutable nature of artifacts ensures the integrity and forensic value of the data. By
preventing modification after creation, SOAR maintains a secure and audit-compliant environment,
ensuring that data remains trustworthy throughout the incident's lifecycle. However, containers,
comments, and notes can be updated or modified, making artifacts unique in their immutability.
Reference:
Splunk SOAR User Guide: Artifacts and Containers.
Splunk SOAR Best Practices for Incident Management.
Question 14
On the Splunk search head, when configuring the app to search SOAR searchable content, what are
the two requirements to complete the app setup?
- A. User accounts and universal forwarder.
- B. User accounts and an HTTP Event Collector token.
- C. User accounts and REST API.
- D. User accounts and syslog.
Answer:
B
Explanation:
When configuring the Splunk app on the search head to search SOAR (Splunk's Security
Orchestration, Automation, and Response) searchable content, two key components are required:
User Accounts: The user accounts are necessary to authenticate and authorize users who are
accessing SOAR data through the Splunk app. These accounts manage permissions and access levels
to ensure the proper users can search and interact with the data coming from SOAR.
HTTP Event Collector (HEC) Token: The HEC token is crucial because it allows the Splunk app to
receive data from Splunk SOAR. SOAR sends events and other data to the Splunk platform via HEC.
This token is used for secure communication and authentication between Splunk and SOAR. The
token must be configured in the Splunk app to allow it to collect and search SOAR data seamlessly.
Other options like syslog, REST API, or a universal forwarder are commonly used methods for
ingesting data into Splunk but are not specific requirements for setting up the Splunk app to search
SOAR content. The HTTP Event Collector is the primary method for this setup, along with the correct
user accounts.
Reference:
Splunk Documentation on HTTP Event Collector and SOAR Integration.
Splunk SOAR App Setup Guide for Splunk Search Head Configuration.
Question 15
A user selects the New option under Sources on the menu. What will be displayed?
- A. A list of new assets.
- B. The New Data Ingestion wizard.
- C. A list of new data sources.
- D. A list of new events.
Answer:
B
Explanation:
Selecting the New option under Sources in the Splunk SOAR menu typically initiates the New Data
Ingestion wizard. This wizard guides users through the process of configuring new data sources for
ingestion into the SOAR platform. It is designed to streamline the setup of various data inputs, such
as event logs, threat intelligence feeds, or notifications from other security tools, ensuring that SOAR
can receive and process relevant security data efficiently. This feature is crucial for expanding SOAR's
monitoring and response capabilities by integrating diverse data sources. Options A, C, and D do not
accurately describe what is displayed when the New option under Sources is selected, making option
B the correct choice.
New Data Ingestion wizard allows you to create a new data source for Splunk SOAR (On-premises) by
selecting the type of data, the ingestion method, and the configuration options. The other options
are incorrect because they do not match the description of the New option under Sources on the
menu. For example, option A refers to a list of new assets, which is not related to data ingestion.
Option C refers to a list of new data sources, which is not what the New option does. Option D refers
to a list of new events, which is not the same as creating a new data source.