ServiceNow CIS-SIR Exam Questions
Questions for the CIS-SIR were updated on : Feb 18 ,2026
Page 1 out of 4. Viewing questions 1-15 out of 60
Question 1
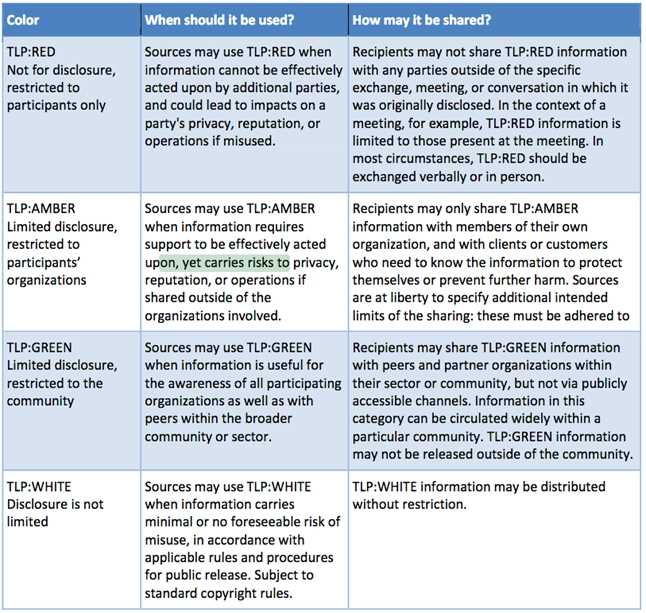
Security tag used when a piece of information requires support to be effectively acted upon, yet
carries risks to privacy, reputation, or operations if shared outside of the organizations involved.
A. TLP:GREEN
B. TLP:AMBER
C. TLP:RED
D. TLP:WHITE
Answer:
B
Question 2
A Post Incident Review can contain which of the following? (Choose three.)
- A. Post incident Question:naires
- B. An audit trail
- C. Attachments associated with the security incident
- D. Key incident fields
- E. Performance Analytics reports
Answer:
ABD
Question 3
Which one of the following reasons best describes why roles for Security Incident Response (SIR)
begin with "sn_si"?
- A. Because SIR is a scoped application, roles and script includes will begin with the sn_si prefix
- B. Because the Security Incident Response application uses a Secure Identity token
- C. Because ServiceNow checks the instance for a Secure Identity when logging on to this scoped application
- D. Because ServiceNow tracks license use against the Security Incident Response Application
Answer:
B
Question 4
Which of the following is an action provided by the Security Incident Response application?
- A. Create Outage state V1
- B. Create Record on Security Incident state V1
- C. Create Response Task set Incident state V1
- D. Look Up Record on Security Incident state V1
Answer:
D
Question 5
What specific role is required in order to use the REST API Explorer?
- A. admin
- B. sn_si.admin
- C. rest_api_explorer
- D. security_admin
Answer:
AC
Reference: https://developer.servicenow.com/dev.do#!/learn/learning-plans/orlando/
technology_partner_program/app_store_learnv2_rest_orlando_introduction_to_the_rest_api_explo
rer
Question 6
What field is used to distinguish Security events from other IT events?
- A. Type
- B. Source
- C. Classification
- D. Description
Answer:
C
Reference: https://docs.servicenow.com/bundle/paris-security-management/page/product/security-incident-response/concept/c_ScIncdUseAlrts.html
Question 7
Which of the following fields is used to identify an Event that is to be used for Security purposes?
- A. IT
- B. Classification
- C. Security
- D. CI
Answer:
B
Reference: https://docs.servicenow.com/bundle/paris-it-operations-management/page/product/event-management/task/t_EMManageEvent.html
Question 8
When a service desk agent uses the Create Security Incident UI action from a regular incident, what
occurs?
- A. The incident is marked resolved with an automatic security resolution code
- B. A security incident is raised on their behalf but only a notification is displayed
- C. A security incident is raised on their behalf and displayed to the service desk agent
- D. The service desk agent is redirected to the Security Incident Catalog to complete the record producer
Answer:
A
Question 9
David is on the Network team and has been assigned a security incident response task. What role
does he need to be able to view and work the task?
- A. Security Analyst
- B. Security Basic
- C. External
- D. Read
Answer:
A
Question 10
Which of the following tag classifications are provided baseline? (Choose three.)
- A. Traffic Light Protocol
- B. Block from Sharing
- C. IoC Type
- D. Severity
- E. Cyber Kill Chain Step
- F. Escalation Level
- G. Enrichment whitelist/blacklist
Answer:
ACG
Reference: https://docs.servicenow.com/bundle/paris-security-management/page/product/security-operations-common/task/create-class-group-and-tags.html
Question 11
Which of the following process definitions are not provided baseline?
- A. NIST Open
- B. SAN Stateful
- C. NIST Stateful
- D. SANS Open
Answer:
A
Question 12
A flow consists of
. (Choose two.)
- A. Scripts
- B. Actions
- C. Processes
- D. Actors
- E. Triggers
Answer:
BE
Reference: https://docs.servicenow.com/bundle/paris-servicenow-platform/page/administer/flow-designer/concept/flows.html
Question 13
The EmailUserReportedPhishing script include processes inbound emails and creates a record in
which table?
- A. ar_sn_si_phishing_email
- B. sn_si_incident
- C. sn_si_phishing_email_header
- D. sn_si_phishing_email
Answer:
A
Question 14
Using the KB articles for Playbooks tasks also gives you which of these advantages?
- A. Automated activities to run scans and enrich Security Incidents with real time data
- B. Automated activities to resolve security Incidents through patching
- C. Improved visibility to threats and vulnerabilities
- D. Enhanced ability to create and present concise, descriptive tasks
Answer:
C
Question 15
Why is it important that the Platform (System) Administrator and the Security Incident administrator
role be separated? (Choose three.)
- A. Access to security incident data may need to be restricted
- B. Allow SIR Teams to control assignment of security roles
- C. Clear separation of duty
- D. Reduce the number of incidents assigned to the Platform Admin
- E. Preserve the security image in the company
Answer:
BCD