ruckus RCNI Exam Questions
Questions for the RCNI were updated on : Feb 20 ,2026
Page 1 out of 4. Viewing questions 1-15 out of 54
Question 1
When a high CPU alert about an ICX switch is triggered, which command will provide more detail on
the processes taking up CPU cycles?
- A. show cpu histogram
- B. show cpu tasks
- C. show cpu
- D. show process
Answer:
C
Question 2
Which two commands can be used to display the IP address of a device attached to a switch port?
(Choose two.)
- A. show interface
- B. show interface brief wide
- C. show mac-address all
- D. show lldp neighbor detail
- E. show arp
Answer:
D, E
Question 3
Which command could be used to find the system name of an attached device?
- A. show lldp neighbors
- B. show chassis
- C. ping
- D. show inline power
Answer:
B
Question 4
In the following output, what is the bridge priority of the root in hex?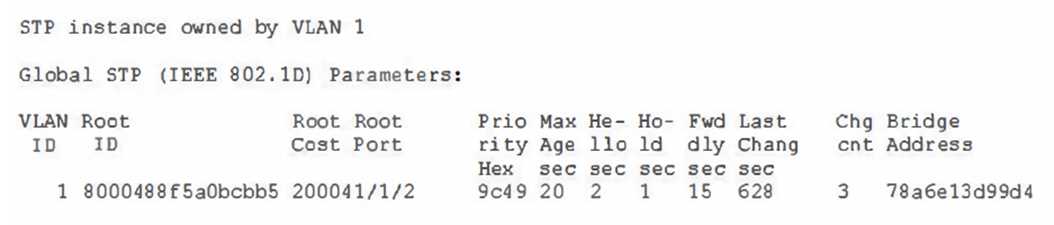
- A. 8000
- B. 0
- C. 9c49
- D. 20009
Answer:
A
Question 5
What is one advantage of the supportsave command versus the show tech-support command?
- A. Uses fewer CPU cycles during execution.
- B. Allows the transfer of collected data to TFTP.
- C. Uploads directly to RUCKUS support.
- D. Generates automatically after a system crash.
Answer:
C
Question 6
Which command can be used to identify Cyclic Redundancy Check (CRC) errors on port Ethernet
1/1/1?
- A. show statistics ethernet 1/1/1
- B. show interfaces brief ethernet 1/1/1
- C. show mac-address ethernet 1/1/1
- D. show port security ethernet 1/1/1
Answer:
A
Question 7
At which prompt can the ping command be executed?
- A. ICX7150-C12 Router(config-if-mgmt-1)#
- B. ICX7150-C12 Router(config)#
- C. ICX7150-C12 Router#
- D. ICX7150-C12 Router(config-if-e1000-1/1/1)#
Answer:
C
Question 8
Why is the following command failing?
RKUS-01(config)#vlan 1
RKUS-01(config-vlan-1)#tagged ethernet 1/2/1
Invalid input -> tagged ethernet 1/2/1
Type ? for a list
- A. This model ICX does not have an interface Ethernet 1/2/1.
- B. The default VLAN cannot be tagged to any interfaces.
- C. VLAN 1 must be configured as a protocol-based VLAN before tagged ports can be added.
- D. A Virtual Ethernet interface must be defined before a tagged port can be added.
Answer:
B
Question 9
In a core/edge network topology, which ports should have Root Guard enabled?
- A. route-only ports facing the WAN
- B. edge ports facing the core
- C. core ports facing the edge
- D. management ports at the core
Answer:
C
Question 10
Which two statements are true when Dynamic Host Configuration Protocol (DHCP) Snooping is
enabled? (Choose two.)
- A. DHCP server interfaces should be trusted.
- B. All interfaces are trusted by default.
- C. DHCP snooping must be enabled globally.
- D. DHCP snooping must be enabled per VLAN.
- E. DHCP snooping must be enabled per interface.
Answer:
A, D
Question 11
For multicast clients to stop receiving traffic using a leave request, which protocol must run on the
local subnet?
- A. IGMPv2
- B. IGMPv1
- C. PIM Dense
- D. IGMP Snooping
Answer:
B
Question 12
Which statement is true about Secure Shell (SSH) functionality in FastIron 08.0.95?
- A. Default login timeout is 30 seconds.
- B. Default SSH authentication type is RSA with 2048-bit modulus.
- C. Server function is disabled by default.
- D. Outbound SSH sessions are not supported.
Answer:
B
Question 13
Based on the following configuration, which statement is true?
ICX-Router (config)# ipv6 unicast-routing
ICX-Router (config)# interface ethernet 1/3/1
ICX-Router (config-if-e1000-1/3/1)# ip address 10.172.10.1/24
ICX-Router (config-if-e1000-1/3/1)# ipv6 address 2001:db8:12d:1300::/64
- A. The ipv6 enable command must also be configured at the interface level.
- B. The interface will transmit and receive both IPv4 and IPv6 traffic simultaneously.
- C. ICX devices do not support IPv4 and IPv6 addresses configured on the same interface.
- D. ICX devices only support dual-stacked IPv4 and IPv6 configuration on a VE interface.
Answer:
B
Question 14
Which three objects can be assigned a Layer 3 address? (Choose three.)
- A. Stack Interface
- B. VxLAN
- C. Virtual LAN
- D. Virtual Ethernet
- E. Loopback
- F. GRE tunnels
Answer:
A, E, F
Question 15
A Core, Aggregation, Edge topology network is running Rapid Spanning Tree Protocol (RSTP). Two
switches at the edge are legacy and run 802.1D.
To influence the convergence time of the legacy switches at the edge, where are the timers
modified?
- A. the route-only port on the upstream gateway
- B. on the two legacy 802.1D switches at the edge
- C. on the Aggregation switches connected to the legacy edge switches
- D. on the root bridge at the core
Answer:
C