Pegasystems PEGAPCLSA86V2 Exam Questions
Questions for the PEGAPCLSA86V2 were updated on : Feb 18 ,2026
Page 1 out of 10. Viewing questions 1-15 out of 148
Question 1
You are designing a case life cycle to process fraudulent charge claims. After a list of suspected
fraudulent charge is submitted, the case advances to the processing stage. In the first step of
theprocess fraud claim process, a seprate child case must be created for each suspected fraudulent
charge.
After all necessary fraudulent charge cases are created, the parent cse advance to the next step
where the customer is notified that their claims are being processed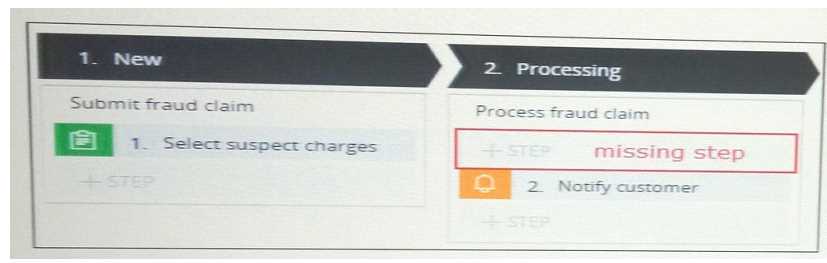
choose three actions needed to configure the missing step so that a separate child case is created for
each fraudulent charge selected
- A. Add a customer split for each process step to the cse life cycle and configure it ti create child cases.
- B. configure data propagation to map property value between the parent and clid cases.
- C. add a create case smart shape to the case life cycle and configure it to be created a case
- D. add a create case smart setup to the cse life cycle and configure it to creare child cases
- E. use a page list property to store the fraudulent claim items and identify the number if child cases to create
Answer:
B, D, E
Question 2
Consider the following requirement:
case worker must be able to add a work party when creating a case
select the configuration option that fulfills this requirement
- A. add a data transform to the pyCaseManagementDefault work parties rule
- B. Ensure the addparty user action is available as a local action C.add the addworkObjectparty activity to the assigments
- D. select the VOE? option on the pyCaseManagementDefault work parties rule
Answer:
D
Question 3
A user report poor application performance at 5:00 pm yesterday. which two tools do you use to
review the user's session to identify the cause of the poor performance ?
- A. performance profiler
- B. my performance Details report
- C. Alerts log
- D. tracer
Answer:
B, C
Question 4
You want to create a dynamic system setting to adjust an alert threshold for you application in
Production which three tasks do you perform to configure the DSS record?
- A. specifying the node ID of the system used for performance monitoring
- B. Appending / default to the setting purpose
- C. Setting the owing ruleset tp pega-Engine
- D. Prepending prconfig/ to the setting purpose
- E. setting the owning ruleset to one of the application rulesets
Answer:
B, C, D
Question 5
You are audit a property named. Generic Code. The label on the form is named suggested generic
substitute. when the field value changes, you want the history details to show as the name of the
label.
you also want to record the name of the property
How do you ensure that the entry shows both the label and the property name?
- A. On the pyTracksecurtiyChanges data tranform, in the source field, enter "suggested generic substitue (. GenricCode)"
- B. on the pyTracksecurtiyChanges declare trigger activity, enter GenericCode as a parameter name and "suggested generic substitute" as a perameter description
- C. on the work management landing page> Filed level Auditing tab in the source filed enter GenericCode. in the Description filed enter "suggested generic substitute"
- D. on the work management landing page > Filed level Auditing tab,, in the source filed enter "suggested generic substituite(. GeneriCode)"
Answer:
A
Question 6
A recent review of the audit polices log show that a specific IP address has made a large number of
failed login attempts within a few minutes you suspect that it is an internet bot attack
Select two options you can configure to prevent the bot from accessing you application
- A. Enable the CAPTCHA security policy
- B. Enable an authentication lockout policy
- C. Enable a contect security policy
- D. Enable a failed login attempts security event
Answer:
A, B
Question 7
You need to define a new LDAP authentication servlet because all of the standard LDAP servlets are
being used in authentication services
which two task do you perform to implement this requirement
- A. Copy an existing LDAP servlet and rename it
- B. Create a new mapping servlet and URL pattern
- C. add a new URL pattern to the existing mapping servlet
- D. rename an existing LDAP servlet
Answer:
A, B
Question 8
An application uses LDP authentication users have role and application attributes, but not access
group attributes. select the two tasks required to configure the application to uses LDAP attributes to
determine the access group for a user
- A. Create a decision table that evaluate role and application properties that return access group
- B. Configure the authentication mapping to evaluate the decision table
- C. Create a decision table that evaluate role and application attribute value that return access group
- D. Add a method to the authentication activity to evaluate the decision table
Answer:
C, D
Question 9
which two of the following action are required to configure your application to support SSO
authentication ?
- A. configuring the authentication activity to identify the operator in the system
- B. configure the application record to use external authentication
- C. configure required mapping between LDAP attributes and operator properties
- D. configure model operator records for each access group in your application
Answer:
A, C
Question 10
You add database connection information to prconfig.xml and want to encrypt the password in the
connection information how do you encrypt the password?
- A. create an encrypted keyring password and replace the unencypted password in prconfig.xml
- B. enter a password in an application ID instance and reference the external system
- C. create an encrypted password with PR cipherGenerator and reference the external system
- D. create an encrypted password with passGen and replace the unencrypted password in pconfig.xml
Answer:
A
Question 11
How do you encrypt the storage stream of the class MyOrg-HR-Work-RFP?
- A. Build a site-specific encrypting cypher and select Encrypt BLOB? on the class group for MyOrg- HRWork-RFP
- B. Build a site-specific encrypting cypher and select Encrypt BLOB? on the class MyOrg-HR-Work-RFP
- C. Select Encrypt BLOB? on the class MyOrg-HR-Work-RFP
- D. Encrypt the pzPvStream colum of the DB table mapped to MyOrg-HR-Work-RFP class using DB tools
Answer:
B
Question 12
DRAG DROP
An application uses LDAP authentication and create operators dynamically based on a model operate
recorded select and move the three options needed to complete the configuration to configuration
column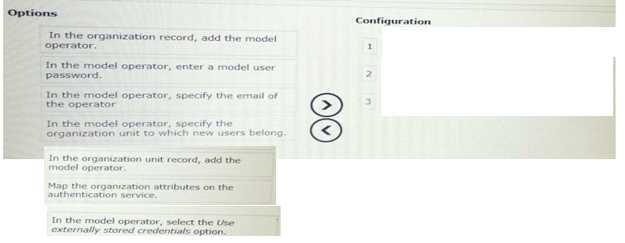
Answer:
None
Explanation: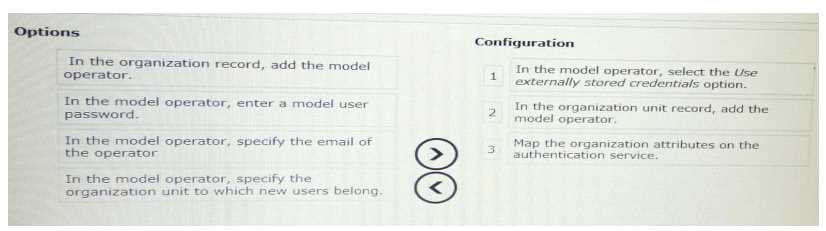
Question 13
An application allows users to manage Account cases. You need to configure security so that users
are allowed to view and update account only if they are the primary or secondary owner
how do you implement this requirement?
- A. create a when rule that validate id the current user is either a primay or secondary owner of the account configure then when rule in the required conditions section on all flow actions that allow account updates.
- B. create a privilage and configure it to validate if the current user is either a primary or secondary owner of the account. Assign the privilege for read and write instances of the account class in the user's access role.
- C. create an access when rule that validate if the current user is either a primary or secondary owner of the account. Assign the access when rule for read and write instances of the account class in the user's vaccess role.
- D. create an access when rule that validate if the current user is either a primay or secondary owner of the ccount. Configure the access when rule on the Accouny case type to ensure authorized access
Answer:
C
Question 14
You deplyed a pega web mashup implementation into production and are using IACAuthentication.
which two action ensure that the external authentication module, and not another source, has
validated the user?
- A. In the IACAuthentication service, map a passoword attribute form the LDAP server used by the external
- B. In an IAC authentication activity, add a step to idenify the security token provied by the external authentication module.
- C. in the IACAuthentication service, specify the appropriate bind password used by the host system
- D. In an IAC authentication activity, add steps that return the security token to the external authentication module for verification.
Answer:
B, D
Question 15
A security requirement states that personal data should only be visible to managers in the HR
organization. All personal data is contained in a single section.
How do you restrict access to personal data ?
- A. configure a visible when rule on the section
- B. Create an Access control policy restricting access to the properties
- C. Add an Access when to relevent properties.
- D. Define a privilege for the section and add the privilege to appropriate roles
Answer:
D