palo alto networks XDR-ENGINEER Exam Questions
Questions for the XDR-ENGINEER were updated on : Feb 18 ,2026
Page 1 out of 4. Viewing questions 1-15 out of 50
Question 1
[Detection Engineering]
Which XQL query can be saved as a behavioral indicator of compromise (BIOC) rule, then converted
to a custom prevention rule?
- A. dataset = xdr_data| filter event_type = ENUM.DEVICE and action_process_image_name = "**"and action_process_image_command_line = "-e cmd*"and action_process_image_command_line != "*cmd.exe -a /c*"
- B. dataset = xdr_data| filter event_type = ENUM.PROCESS and event_type = ENUM.DEVICE and action_process_image_name = "**"and action_process_image_command_line = "-e cmd*"and action_process_image_command_line != "*cmd.exe -a /c*"
- C. dataset = xdr_data| filter event_type = FILE and (event_sub_type = FILE_CREATE_NEW or event_sub_type = FILE_WRITE or event_sub_type = FILE_REMOVE or event_sub_type = FILE_RENAME) and agent_hostname = "hostname"| filter lowercase(action_file_path) in ("/etc/*", "/usr/local/share/*", "/usr/share/*") and action_file_extension in ("conf", "txt")| fields action_file_name, action_file_path, action_file_type, agent_ip_addresses, agent_hostname, action_file_path
- D. dataset = xdr_data| filter event_type = ENUM.PROCESS and action_process_image_name = "**"and action_process_image_command_line = "-e cmd*"and action_process_image_command_line != "*cmd.exe -a /c*"
Answer:
D
Question 2
[Data Ingestion and Integration]
A new parsing rule is created, and during testing and verification, all the logs for which field data is to
be parsed out are missing. All the other logs from this data source appear as expected. What may be
the cause of this behavior?
- A. The Broker VM is offline
- B. The parsing rule corrupted the database
- C. The filter stage is dropping the logs
- D. The XDR Collector is dropping the logs
Answer:
C
Question 3
[Cortex XDR Agent Configuration]
Multiple remote desktop users complain of in-house applications no longer working. The team uses
macOS with Cortex XDR agents version 8.7.0, and the applications were previously allowed by
disable prevention rules attached to the Exceptions Profile "Engineer-Mac." Based on the images
below, what is a reason for this behavior?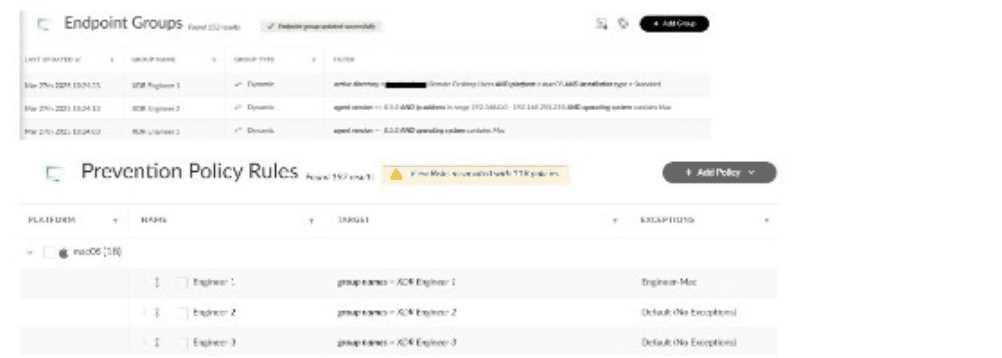
- A. Endpoint IP address changed from 192.168.0.0 range to 192.168.100.0 range
- B. The Cloud Identity Engine is disconnected or removed
- C. XDR agent version was downgraded from 8.7.0 to 8.4.0
- D. Installation type changed from VDI to Kubernetes
Answer:
A
Question 4
[Detection Engineering]
During a recent internal purple team exercise, the following recommendation is given to the
detection engineering team: Detect and prevent command line invocation of Python on Windows
endpoints by non-technical business units. Which rule type should be implemented?
- A. Analytics Behavioral Indicator of Compromise (ABIOC)
- B. Behavioral Indicator of Compromise (BIOC)
- C. Correlation
- D. Indicator of Compromise (IOC)
Answer:
B
Question 5
[Data Ingestion and Integration]
When onboarding a Palo Alto Networks NGFW to Cortex XDR, what must be done to confirm that
logs are being ingested successfully after a device is selected and verified?
- A. Conduct an XQL query for NGFW log data
- B. Wait for an incident that involves the NGFW to populate
- C. Confirm that the selected device has a valid certificate
- D. Retrieve device certificate from NGFW dashboard
Answer:
A
Question 6
[Playbook Creation and Automation]
An XDR engineer is configuring an automation playbook to respond to high-severity malware alerts
by automatically isolating the affected endpoint and notifying the security team via email. The
playbook should only trigger for alerts generated by the Cortex XDR analytics engine, not custom
BIOCs. Which two conditions should the engineer include in the playbook trigger to meet these
requirements? (Choose two.)
- A. Alert severity is High
- B. Alert source is Cortex XDR Analytics
- C. Alert category is Malware
- D. Alert status is New
Answer:
A,C
Question 7
[Data Ingestion and Integration]
What is a benefit of ingesting and forwarding Palo Alto Networks NGFW logs to Cortex XDR?
- A. Sending endpoint logs to the NGFW for analysis
- B. Blocking network traffic based on Cortex XDR detections
- C. Enabling additional analysis through enhanced application logging
- D. Automated downloading of malware signatures from the NGFW
Answer:
C
Question 8
[Maintenance and Troubleshooting]
After deploying Cortex XDR agents to a large group of endpoints, some of the endpoints have a
partially protected status. In which two places can insights into what is contributing to this status be
located? (Choose two.)
- A. Management Audit Logs
- B. XQL query of the endpoints dataset
- C. All Endpoints page
- D. Asset Inventory
Answer:
B,C
Question 9
[Planning and Installation]
The most recent Cortex XDR agents are being installed at a newly acquired company. A list with
endpoint types (i.e., OS, hardware, software) is provided to the engineer. What should be cross-
referenced for the Linux systems listed regarding the OS types and OS versions supported?
- A. Content Compatibility Matrix
- B. Kernel Module Version Support
- C. End-of-Life Summary
- D. Agent Installer Certificate
Answer:
B
Question 10
[Planning and Installation]
During deployment of Cortex XDR for Linux Agents, the security engineering team is asked to
implement memory monitoring for agent health monitoring. Which agent service should be
monitored to fulfill this request?
- A. dypdng
- B. clad
- C. pyxd
- D. pmd
Answer:
D
Question 11
[Maintenance and Troubleshooting]
When isolating Cortex XDR agent components to troubleshoot for compatibility, which command is
used to turn off a component on a Windows machine?
- A. "C:\Program Files\Palo Alto Networks\Traps\xdr.exe" stop
- B. "C:\Program Files\Palo Alto Networks\Traps\cytool.exe" runtime stop
- C. "C:\Program Files\Palo Alto Networks\Traps\xdr.exe" -s stop
- D. "C:\Program Files\Palo Alto Networks\Traps\cytool.exe" occp
Answer:
B
Question 12
[Cortex XDR Agent Configuration]
Which two steps should be considered when configuring the Cortex XDR agent for a sensitive and
highly regulated environment? (Choose two.)
- A. Enable critical environment versions
- B. Create an agent settings profile where the agent upgrade scope is maintenance releases only
- C. Create an agent settings profile, enable content auto-update, and include a delay of four days
- D. Enable minor content version updates
Answer:
B,C
Question 13
[Cortex XDR Agent Configuration]
Some company employees are able to print documents when working from home, but not on
network-attached printers, while others are able to print only to file. What can be inferred about the
affected users’ inability to print?
- A. They may be attached to the default extensions policy and profile
- B. They may have a host firewall profile set to block activity to all network-attached printers
- C. They may have different disk encryption profiles that are not allowing print jobs on encrypted files
- D. They may be on different device extensions profiles set to block different print jobs
Answer:
B
Question 14
[Detection Engineering]
An analyst considers an alert with the category of lateral movement to be allowed and not needing
to be checked in the future. Based on the image below, which action can an engineer take to address
the requirement?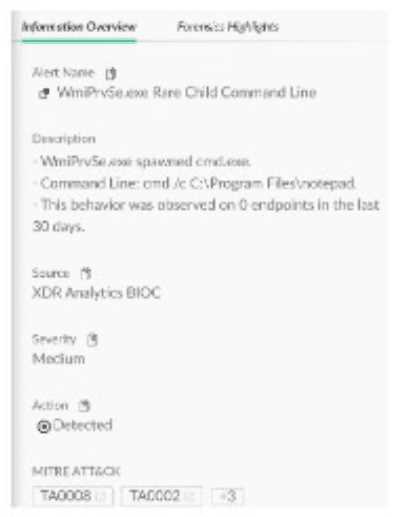
- A. Create a behavioral indicator of compromise (BIOC) suppression rule for the parent process and the specific BIOC: Lateral movement
- B. Create an alert exclusion rule by using the alert source and alert name
- C. Create a disable injection and prevention rule for the parent process indicated in the alert
- D. Create an exception rule for the parent process and the exact command indicated in the alert
Answer:
B
Question 15
[Post-Deployment Management and Configuration]
Based on the SBAC scenario image below, when the tenant is switched to permissive mode, which
endpoint(s) data will be accessible?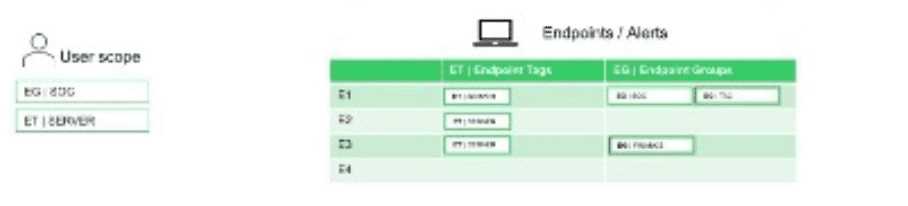
- A. E1 only
- B. E2 only
- C. E1, E2, and E3
- D. E1, E2, E3, and E4
Answer:
C