palo alto networks PCNSC Exam Questions
Questions for the PCNSC were updated on : Apr 19 ,2025
Page 1 out of 6. Viewing questions 1-15 out of 77
Question 1
Which three authentication faction factors does PAN-OS® software support for MFA? (Choose three.)
- A. Voice
- B. Pull
- C. SMS
- D. Push
- E. Okta Adaptive
Answer:
A B D
Question 2
A speed/duplex negotiation mismatch is between the Palo Alto Networks management port and the switch it connect.
How would an administrator configure the interface to IGbps?
- A. set deviceconfig system speed-duplex 10Gbps-full-duplex
- B. set deviceconfig interface speed-duplex 1Gbs--full-duplex
- C. set deviceconfig interface speed-duplex 1Gbs--half-duplex
- D. set deviceconfig system speed-duplex 1Gbs--half-duplex.
Answer:
D
Question 3
An administrator sees several inbound sessions identified as unknown tcp in the Traffic logs. The administrator determines
that these sessions are from external users accessing the companys propriety accounting application. The administrator
wants to reliability identity this as their accounting application and to scan this traffic for threats.
Which option would achieve this result?
- A. Create an Application Override policy and a custom threat signature for the application.
- B. Create a custom App-ID and use the "ordered condition cheek box.
- C. Create an Application Override policy
- D. Create a custom App-ID and enable scanning on the advanced tab.
Answer:
A
Question 4
A Company needs to preconfigured firewalls to be sent to remote sites with the least amount of preconfiguration. Once
deployed, each firewall must establish secure tunnels back to multiple regional data centers to include the future regional
data centers.
Which VPN configuration would adapt to changes when deployed to Hie future site?
- A. preconfigured GlobalProtcet satellite
- B. preconfigured GlobalProtcet client
- C. preconfigured iPsec tunnels
- D. preconfigured PPTP Tunnels
Answer:
A
Question 5
An administrator has users accessing network resources through Citrix XenApp 7 .x. Which User-ID mapping solution will
map multiple mat who using Citrix to connect to the network and access resources?
- A. Client Probing
- B. Globa1Protect
- C. Terminal Services agent
- D. Syslog Monitoring
Answer:
C
Question 6
An administrator wants multiple web servers in the DMZ to receive connections from the internet. Traffic destined for
206.15.22.9 port 80/TCP needs to be forwarded to the server at 10 1.22
Based on the information shown in the age, which NAT rule will forward web-browsing traffic correctly?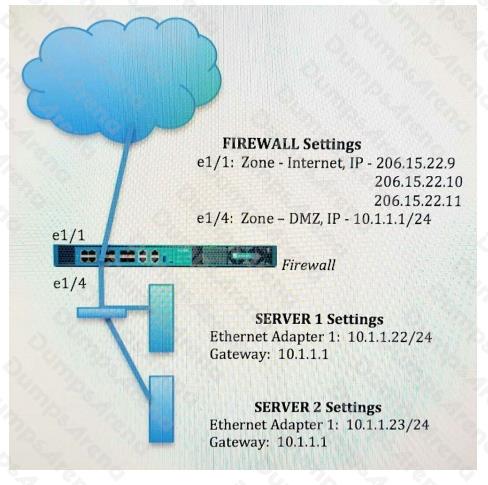
A)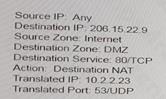
B)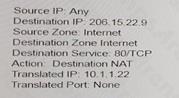
C)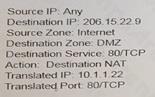
D)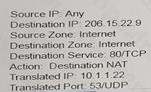
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
A
Question 7
Refer to the exhibit.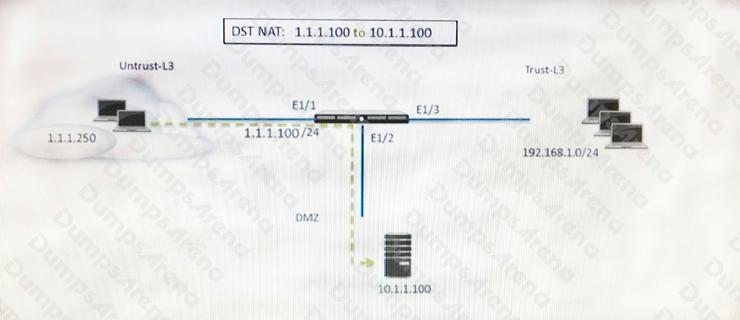
A web server in the DMZ is being mapped to a public address through DNAT. Which Security policy rule will allow traffic to
flow to the web server?
- A. Untrust (any) to Untrust (10. 1.1. 100), web browsing – Allow
- B. Untrust (any) to Untrust (1. 1. 1. 100), web browsing – Allow
- C. Untrust (any) to DMZ (1. 1. 1. 100), web browsing – Allow
- D. Untrust (any) to DMZ (10. 1. 1. 100), web browsing – Allow
Answer:
B
Question 8
Which feature can be configured on VM-Series firewalls'?
- A. aggregate interlaces
- B. multiple virtual systems
- C. Globallprotect
- D. machine learning
Answer:
C
Question 9
A web server is hosted in the DMZ and the server re configured to listen for income connections on TCP port
443. A Security policies rules allowing access from the Trust zone to the DMZ zone needs to be configured to allow web-
browsing access. The web server host its contents over Traffic from Trust to DMZ is being decrypted with a Forward Proxy
rule.
Which combination of service and application, and order of Security policy rules needs to be configured to allow cleaned
web-browsing traffic to the server on tcp/443?
- A. Rule# 1 application: ssl; service application-default: action allow Role # 2 application web browsing, service application default, action allow
- B. Rule #1application web-browsing, service service imp action allow Rule #2 application ssl. service application -default, action allow
- C. Rule#1 application web-brows.no service application-default, action allow Rule #2 application ssl. Service application- default, action allow
- D. Rule#1application: web-biows.no; service service-https action allow Rule#2 application ssl. Service application-default, action allow
Answer:
C
Question 10
VPN traffic intended for an administrator's Palo Alto Networks NGfW is being maliciously intercepted and retransmitted by
the interceptor. When Creating a VPN tunnel, which protection profile cm be enabled to prevent this malicious behavior?
- A. zone Protection
- B. Web Application
- C. DoS Protection
- D. Replay
Answer:
A
Question 11
A session in the Traffic log is reporting the application as "incomplete
What does "incomplete" mean?
- A. The three-way TCP handshake did not complete.
- B. Data was received but wan instantly discarded because of a Deny policy was applied before App ID could be applied.
- C. The three-way TCP handshake was observed, but the application could not be identified.
- D. The traffic is coming across UDP, and the application could not be identified.
Answer:
A
Question 12
An administrator has enabled OSPF on a virtual router on the NGFW OSPF is not adding new routes to the virtual router.
Which two options enable the administrator top troubleshoot this issue? (Choose two.)
- A. Perform a traffic pcap at the routing stage.
- B. View System logs.
- C. Add a redistribution profile to forward as BGP updates.
- D. View Runtime Status virtual router.
Answer:
B D
Question 13
An organization has Palo Alto Networks MGfWs that send logs to remote monitoring and security management platforms.
The network team has report has excessive traffic on the corporate WAN. How could the Palo Alto Networks NOFW
administrator reduce WAN traffic while maintaining support for all the existing monitoring/security platforms?
- A. forward logs from firewalls only to Panorama, and have Panorama forward log* lo other external service.
- B. Any configuration on an M-500 would address the insufficient bandwidth concerns.
- C. Configure log compression and optimization features on all remote firewalls.
- D. Forward logs from external sources to Panorama for correlation, arid from Panorama send to the NGFW
Answer:
A
Question 14
A Palo Alto Networks NGFW just submitted a file lo WildFire tor analysis Assume a 5-minute window for analysis. The
firewall is configured to check for verdicts every 5 minutes.
How quickly will the firewall receive back a verdict?
- A. 10 to 15 minutes
- B. 5 to 10 minutes
- C. More than 15 minutes
- D. 5 minutes
Answer:
B
Question 15
Winch three steps will reduce the CPU utilization on the management plane? (Choose three. ) Disable logging at session
start in Security policies.
- A. Disable predefined reports.
- B. Reduce the traffic being decrypted by the firewall.
- C. Disable SNMP on the management interface.
- D. Application override of SSL application.
Answer:
A B C