palo alto networks PCCSE Exam Questions
Questions for the PCCSE were updated on : Jul 05 ,2025
Page 1 out of 23. Viewing questions 1-10 out of 221
Question 1
DRAG DROP You wish to create a custom policy with build and run subtypes.
Match the query types for each example.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
Select and Place: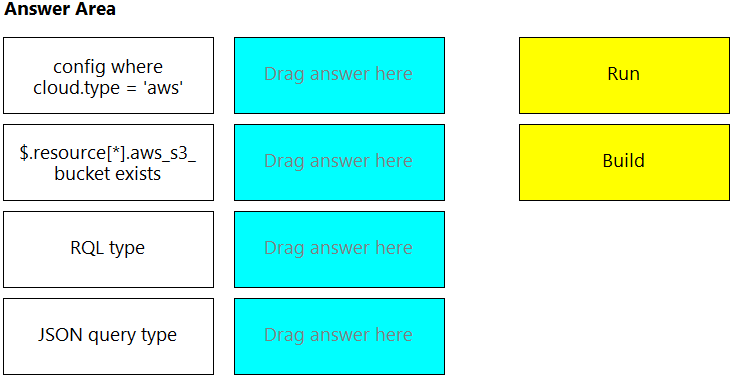
Answer:
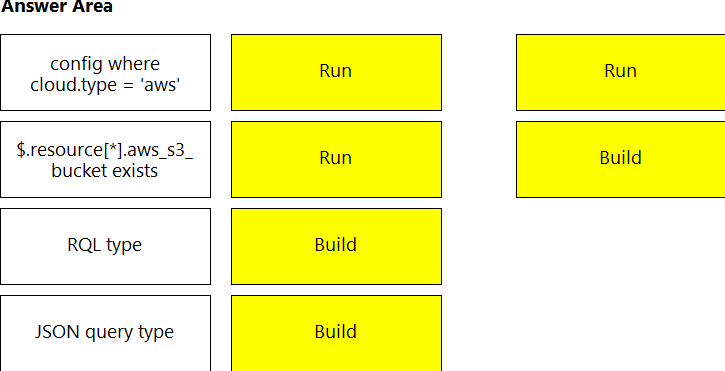
Reference:
https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-policies/create-a-policy.html
Question 2
Which two integrated development environment (IDE) plugins are supported by Prisma Cloud as part of its Code Security? (Choose two.)
- A. BitBucket
- B. Visual Studio Code
- C. CircleCI
- D. IntelliJ
Answer:
ad
Question 3
A DevOps lead reviewed some system logs and notices some odd behavior that could be a data exfiltration attempt. The DevOps lead only has access to vulnerability data in Prisma Cloud Compute, so the DevOps lead passes this information to SecOps.
Which pages in Prisma Cloud Compute can the SecOps lead use to investigate the runtime aspects of this attack?
- A. The SecOps lead should investigate the attack using Vulnerability Explorer and Runtime Radar.
- B. The SecOps lead should use Incident Explorer and Compliance Explorer.
- C. The SecOps lead should use the Incident Explorer page and Monitor > Events > Container Audits.
- D. The SecOps lead should review the vulnerability scans in the CI/CD process to determine blame.
Answer:
b
Reference:
https://docs.paloaltonetworks.com/prisma/prisma-cloud/19-11/prisma-cloud-compute-edition-admin/runtime_defense/incident_explorer.html
Question 4
Which of the following is a reason for alert dismissal?
- A. SNOOZED_AUTO_CLOSE
- B. ALERT_RULE_ADDED
- C. POLICY_UPDATED
- D. USER_DELETED
Answer:
a
Question 5
An administrator has access to a Prisma Cloud Enterprise.
What are the steps to deploy a single container Defender on an ec2 node?
- A. Pull the Defender image to the ec2 node, copy and execute the curl | bash script, and start the Defender to ensure it is running.
- B. Execute the curl | bash script on the ec2 node.
- C. Configure the cloud credential in the console and allow cloud discovery to auto-protect the ec2 node.
- D. Generate DaemonSet file and apply DaemonSet to the twistlock namespace.
Answer:
d
Reference:
https://docs.twistlock.com/docs/compute_edition/install/install_kubernetes.html
Question 6
Per security requirements, an administrator needs to provide a list of people who are receiving e-mails for Prisma Cloud alerts.
Where can the administrator locate this list of e-mail recipients?
- A. Target section within an Alert Rule.
- B. Notification Template section within Alerts.
- C. Users section within Settings.
- D. Set Alert Notification section within an Alert Rule.
Answer:
a
Question 7
A customer has a requirement to restrict any container from resolving the name www.evil-url.com.
How should the administrator configure Prisma Cloud Compute to satisfy this requirement?
- A. Choose copy into rule for any Container, set www.evil-url.com as a blocklisted DNS name in the Container policy and set the policy effect to alert.
- B. Set www.evil-url.com as a blocklisted DNS name in the default Container runtime policy, and set the effect to block.
- C. Choose copy into rule for any Container, set www.evil-url.com as a blocklisted DNS name, and set the effect to prevent.
- D. Set www.evil-url.com as a blocklisted DNS name in the default Container policy and set the effect to prevent.
Answer:
a
Question 8
How often do Defenders share logs with Console?
- A. Every 10 minutes
- B. Every 30 minutes
- C. Every 1 hour
- D. Real time
Answer:
c
Question 9
The security auditors need to ensure that given compliance checks are being run on the host.
Which option is a valid host compliance policy?
- A. Ensure functions are not overly permissive.
- B. Ensure host devices are not directly exposed to containers.
- C. Ensure images are created with a non-root user.
- D. Ensure compliant Docker daemon configuration.
Answer:
c
Question 10
Which three public cloud providers are supported for VM image scanning? (Choose three.)
- A. GCP
- B. Alibaba
- C. Oracle
- D. AWS
- E. Azure
Answer:
ade