palo alto networks PCCSA Exam Questions
Questions for the PCCSA were updated on : Jun 26 ,2025
Page 1 out of 6. Viewing questions 1-15 out of 79
Question 1
DRAG DROP
Match each set of terms to their associated security layer.
Select and Place: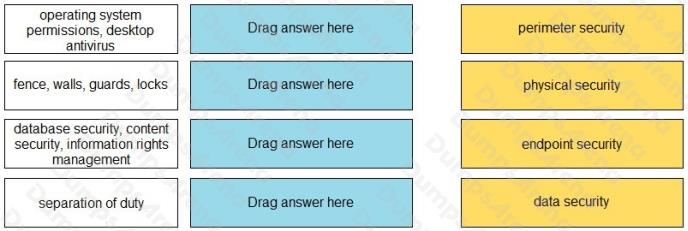
Answer:
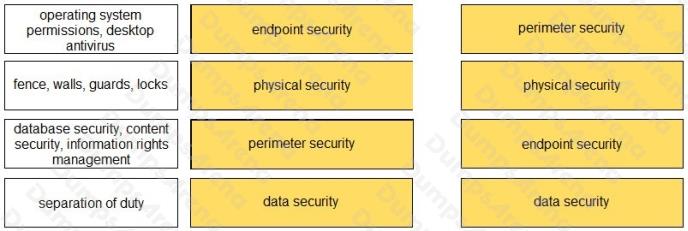
Question 2
You discover malware has corrupted the BIOS on your laptop. Which type of malware is this?
- A. bootkit
- B. exploit
- C. rootkit
- D. vulnerability
Answer:
A
Question 3
What are two methods to securely transmit personally identifiable information? (Choose two.)
- A. data checksumming
- B. data fragmentation
- C. data encryption
- D. encrypted tunnels
Answer:
C D
Question 4
Which type of cloud computing deployment is available to any person or organization who can pay the usage fees?
- A. public
- B. hybrid
- C. private
- D. local
Answer:
A
Question 5
Which two reconnaissance tools might an attacker use to scan for vulnerable network services and settings? (Choose two.)
- A. bandwidth analyzer
- B. intrusion detection
- C. port scanner
- D. password cracker
Answer:
C D
Question 6
What is the result of deploying virtualization in your data center?
- A. reduced security threat
- B. reduced operational costs
- C. increased hardware capital costs
- D. increased host provisioning
Answer:
B
Question 7
When a company chooses to deploy a branch location with antivirus software, which risk model are they using to manage
risk?
- A. limiting
- B. assuming
- C. transferring
- D. avoiding
Answer:
A
Question 8
An attacker emails a malicious URL link to 50,000 email addresses. The email states that users can click the link to view the
latest celebrity news, but the link also secretly infects the users laptop. This scenario describes which type of attack?
- A. whaling
- B. phishing
- C. drive-by download
- D. pharming
Answer:
B
Question 9
Which option describes a characteristic of a next-generation firewall but not a UTM device?
- A. Content inspection engines operate in individual silos.
- B. Content inspection engines use tightly integrated operation.
- C. Content inspection engines process traffic serially, not in parallel.
- D. Content inspection engines run on the same hardware and memory resources.
Answer:
B
Question 10
What is a component of a public key infrastructure?
- A. Key Distribution Center
- B. KDC ticket
- C. SSH key
- D. certificate authority
Answer:
D
Question 11
DRAG DROP
Match the common TCP/IP protocol with its corresponding port(s).
Select and Place: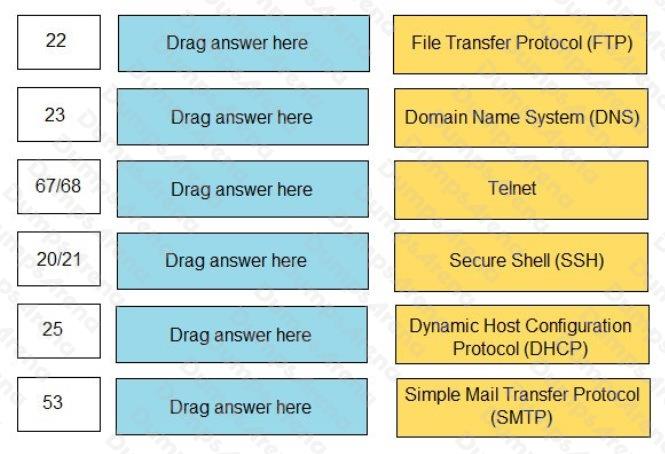
Answer:
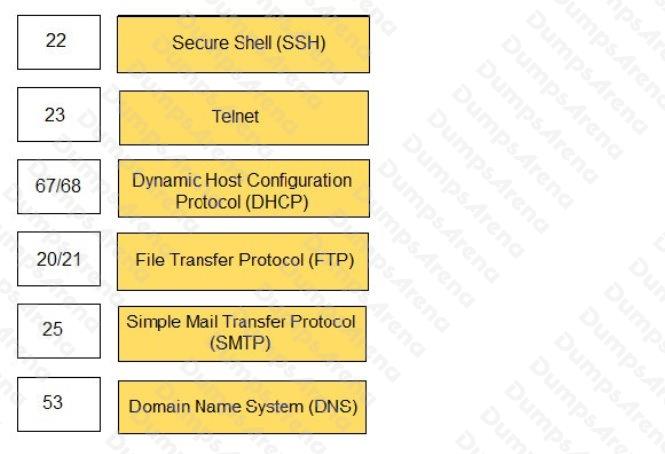
Question 12
You discover an infected email attachment that contains software code that attacks a known vulnerability in a popular social
networking application. This type of software code belongs to which type of malware category?
- A. social engineering
- B. virus
- C. pharming
- D. exploit
Answer:
D
Question 13
Which well-known port is associated with the Simple Mail Transfer Protocol?
- A. 143
- B. 25
- C. 997
- D. 40
Answer:
B
Question 14
Which data security compliance standard is used to protect credit cardholder data wherever it is processed, stored, or
transmitted?
- A. Property Card Industry
- B. Payment Card Industry
- C. Personal Card Industry
- D. Payment Club Industry
Answer:
B
Question 15
Which security component should you configure to block viruses not seen and blocked by the perimeter firewall?
- A. strong endpoint passwords
- B. endpoint disk encryption
- C. endpoint antivirus software
- D. endpoint NIC ACLs
Answer:
C