oracle 1Z0-404 Exam Questions
Questions for the 1Z0-404 were updated on : Jul 05 ,2025
Page 1 out of 5. Viewing questions 1-15 out of 70
Question 1
What configuration step is required for booting the Session Border Controller from an
external FTP server?
- A. Navigate to the bootparams configuration branch and set the host inet field to the IP address of the external BOOTP Server from which the Session Border Controller can boot.
- B. Navigate to the system configuration branch and set the ip address field of the wancom1 management interface.
- C. Navigate to the bootparams configuration branch and set the ip address field of the destination SIP device with which the Session Border Controller needs to interact.
- D. Navigate to the system configuration branch and set the ip address field of the wancom0 management interface.
- E. Navigate to the bootparams configuration branch, set the host inet or Host IP, FTP username, and FTP password for the external FTP Server in which the image file resides.
Answer:
C
Question 2
You are configuring access rules in a Session Border Controller Peering architecture.
Which configuration step is required to allow access from any User Agent (UA)?
- A. Navigate to the sip-port configuration element and set the allow-anonymous parameter to all.
- B. Navigate to the realm-config configuration element and set the addr-prefix parameter to the IP subnet of your trusted User Agent (UA).
- C. Navigate to the sip-port configuration element and set the allow-anonymous parameter to address-prefix.
- D. Navigate to the session-agent configuration element and set the ip-address parameter to the IP subnet of your trusted User Agent (UA).
- E. Navigate to the sip-port configuration element and set the allow-anonymous parameter to agents-only.
Answer:
A
Question 3
Which two functionalities are provided by Session Border Controllers? (Choose two.)
- A. they span multiple networks and provide edge proxy functions between them
- B. they are session-aware devices that enable control of end-to-end interactive communications across PSTN network borders
- C. they enable premium interactive services across IP network borders by complementing existing edge routers
- D. they provide routing functions for IP, TCP, and SMTP using application parameters.
- E. they replace typical edge routers and firewalls in order to provide a unified network border for signaling and media control
Answer:
A,C
Question 4
What mechanism is used to ensure adjacent devices can redirect their Ethernet traffic to the
Session Border Controller that takes over, when a Session Border Controllers fails over?
- A. Gratuitous ARP
- B. Reverse ARP
- C. Proxy ARP
- D. HSRP
- E. BOOTP
Answer:
B
Question 5
Which three statements are true about SIP, per RFC 326? (Choose three.)
- A. SIP does not provide for resource reservation.
- B. SIP defines native methods for negotiating media streams.
- C. A SIP transaction occurs between a client and a server.
- D. To set up a voice session, SIP relies on protocols such as SDP and RTP.
- E. SIP signaling can only be used for voice over IP thereby limiting its use as a general signaling protocol.
Answer:
C,D,E
Question 6
You configured the Session Agent Group (SAG) element. You want the Session Agent to be
selected in the order in which they are listed in the destination list, with each agent selected
in turn, one per session.
How would you accomplish this?
- A. Navigate to the session-agent configuration element and set the strategy parameter to sequential.
- B. Navigate to the session-agent configuration element and set the strategy parameter to propdist.
- C. Navigate to the session-agent configuration element and set the strategy parameter to hunt.
- D. Navigate to the session-agent configuration element and set the strategy parameter to roundrobin.
- E. Navigate to the session-agent configuration element and set the strategy parameter to leastbusy.
Answer:
D
Question 7
Which action triggers the 180 Ringing response in a User Agent Client (UAC)?
- A. the subscription to a SIP presence service
- B. the generation of a remote ring-back tone
- C. the generation of a local ring-back tone
- D. the establishment of a SIP session
- E. the termination of a SIP session
Answer:
C
Question 8
Which two statements describe the functions of Session Border Controllers? (Choose two.)
- A. they replace typical edge routers and firewalls in order to provide a unified network border for signaling and media control
- B. they are session-aware devices that enable control of end-to-end interactive communications across IP network borders
- C. they are based on the Windows operating system
- D. they provide routing functions for IP, TCP, and SMTP using application parameters
- E. they provide signaling proxy functions for SIP, H.323, and MGCP, which includes access control, signaling constraints, and topology hiding
Answer:
A,E
Question 9
You are configuring a sip-interface configuration element. You encounter the error message:
Error 409 saving configuration SipInterface.
Identify the cause of the error.
- A. You are creating a sip-port element with the same address parameter value of another sip- port.
- B. You are creating a sip-port element with the same port parameter value of another sip-port.
- C. You are creating a sip-port element with the same transport-protocol parameter value of another sip-port.
- D. You are creating a sip-interface element with the same realm-id parameter value of another sip-interface.
- E. You are creating a sip-interface element with a different realm-id parameter value of another sip-interface.
Answer:
B
Question 10
You are configuring access rules in a Session Border Controller Peering architecture.
Which two configuration steps are required to allow access only from User Agents (UAs)
configured as session agents? (Choose two.)
- A. Navigate to the sip-port configuration element and set the allow-anonymous parameter to all.
- B. Navigate to the session-agent configuration element and set the ip-address parameter to the IP subnet of your trusted User Agent (UA).
- C. Navigate to the realm-config configuration element and set the addr-prefix parameter to the IP subnet of your trusted User Agent (UA).
- D. Navigate to the sip-port configuration element and set the allow-anonymous parameter to agents-only.
- E. Navigate to the sip-port configuration element and set the allow-anonymous parameter to address-prefix.
Answer:
B,E
Question 11
When setting up the registration-caching parameter to enabled in the sip-interface
configuration element, _____________.
- A. the Session Border Controller will never use the SIP-NAT mechanism for routing
- B. the Session Border Controller will not use the registration cache for routing
- C. all endpoints in the realm will be cached when registered
- D. only endpoints behind NAT in the realm will be cached when registered
- E. the Session Border Controller will never use the local-policy mechanism for routing
Answer:
A
Question 12
What is the effect of executing the save-config command in superuser mode?
- A. The running configuration version is reset to 1.
- B. The running configuration version does not increase and is equal to the saved configuration version.
- C. The saved configuration version increases by 1 and is higher than the running configuration version.
- D. The running configuration version increases by 1 and is higher than the saved configuration version.
- E. The editing configuration version increases by 1 and is higher than the saved configuration version.
Answer:
C
Question 13
You are configuring a network interface to enable the Session Border Controller to use the
interface for signaling and media.
Identify two valid configuration steps for supporting VLAN 12 (Choose two.)
- A. Navigate to the network-interface configuration element and set the sub-port-id parameter to 12.
- B. Navigate to the network-interface configuration element and set the sub-port-id parameter to 0.
- C. Navigate to the phy-interface configuration element and configure the hip-id parameter.
- D. Navigate to the phy-interface configuration element and configure the pri-utility-address parameter.
- E. Navigate to the network-interface configuration element and configure the name parameter.
Answer:
A,C
Question 14
You are examining a SIP packet. There is no final response to the ACK method.
What is the reason for this?
- A. The ACK method was defined only in RFC 2543 and it has been deprecated.
- B. The ACK method is part of the INVITE transaction.
- C. The ACK method is an exception in RFC 3261.
- D. The ACK method is an optional SIP method.
- E. The ACK method was replaced with the CANCEL method in RFC 3261.
Answer:
B
Question 15
View the Exhibit.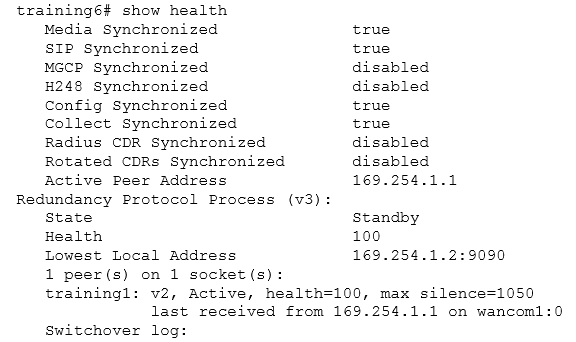
Which statement is true about this output of the show health command?
- A. The two nodes have different health scores.
- B. The training1 peer is the standby node.
- C. The switchover berpd force command was executed to do a manual failover.
- D. The training6 peer is the active node.
- E. The training6 peer will wait 1050 ms before considering the training1 peer out of service.
Answer:
E