oracle 1Z0-1104-25 Exam Questions
Questions for the 1Z0-1104-25 were updated on : Feb 18 ,2026
Page 1 out of 3. Viewing questions 1-15 out of 36
Question 1
"Your company is in the process of migrating its sensitive data to Oracle Cloud Infrastructure (OCI)
and is prioritizing the strongest possible security measures. Encryption is a key part of this strategy,
but you are particularly concerned about the physical security of the hardware where your
encryption keys will be stored.
Which characteristic of OCI Key Management Service (KMS) helps ensure the physical security of
your encryption keys?
- A. Granular customer control over key access permissions
- B. Centralized key management for simplified administration
- C. Seamless integration with other OCI services for streamlined workflows
- D. Utilization of FIPS 140-2 validated Hardware Security Modules (HSMs)"
Answer:
D
Question 2
"Your company is building a highly available and secure web application on OCI. Because of
increasing malicious web-based attacks, the security team has mandated that web servers should
not be exposed directly to the Internet.
How should you architect the solution while ensuring fault tolerance and security?
- A. Deploy at least three web servers in different fault domains within a public subnet, each with a public IP address. Deploy Web Application Firewall (WAF), and configure an origin for each public IP.
- B. Deploy at least three web servers in different fault domains within a private subnet. Place a public load balancer in a public subnet, but skip WAF configuration.
- C. Deploy at least three web servers in different fault domains within a private subnet. Place a public load balancer in a public subnet and configure a back-end set for all web servers. Deploy Web Application Firewall (WAF) and set the load balancer public IP address as the origin.
- D. Deploy at least three web servers in different fault domains within a public subnet. Use OCI Traffic Management service for DNS-based load balancing."
Answer:
C
Question 3
"A company, ABC, is planning to launch a new web application on OCI. Based on past experiences,
they expect a significant surge in traffic after the launch. You are responsible for ensuring that the
application is highly available.
Which step would you perform to achieve this goal?
- A. Use a Virtual Cloud Network (VCN) with subnets, security lists, and routing rules to isolate the web application from the Internet and other resources.
- B. Implement security controls, such as web application firewalls, to protect against common attack vectors.
- C. Configure Cloud Guard to prevent large amounts of traffic from reaching the web application.
- D. Use a load balancer to distribute incoming traffic evenly across multiple instances of the web application."
Answer:
D
Question 4
A company has deployed OCI Zero Trust Packet Routing (ZPR) to secure its network. They have two
compute instances, VM1-01 and VM-02, in a public subnet. VM-01 is tagged with the security
attribute app:vm01, and VM-02 is tagged with app:vm02. The VCN is labeled with network:vcn01,
The ZPR policy states:
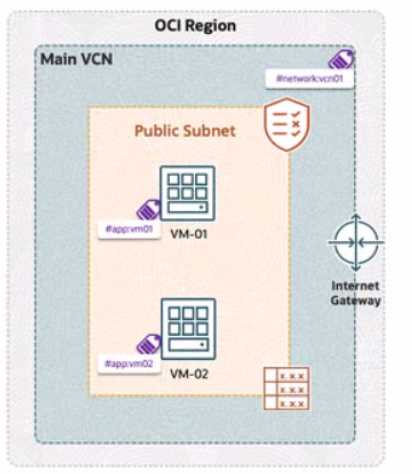
"What is the expected outcome of this policy?
- A. VM-02 can SSH into VM-01, but VM-01 cannot SSH into VM-02.
- B. VM-01 can SSH into VM-02, but VM-02 cannot SSH into VM-01.
- C. Both VM-01 and VM-02 can SSH into each other.
- D. Neither VM-01 nor VM-02 can SSH into each other."
Answer:
B
Question 5
"A programmer is developing a Node.js application which will run on a Linux server on their on-
premises data center. This application will access various Oracle Cloud Infrastructure (OCI) services
using OCI SDKs.
What is the secure way to access OCI services with OCI Identity and Access Management (IAM)?
- A. Create a new OCI IAM user, add the user to a group associated with a policy that grants the desired permissions to OCI services. In the on-premises Linux server, add the user name and password to a file used by Node.js authentication.
- B. Create a new OCI IAM user, add the user to a group associated with a policy that grants the desired permissions to OCI services. In the on-premises Linux server, generate the keypair used for signing API requests and upload the public key to the IAM user.
- C. Create a new OCI IAM user associated with a dynamic group and a policy that grants the desired permissions to OCI services. Add the on-premises Linux server in the dynamic group.
- D. Create an OCI IAM policy with appropriate permissions to access the required OCI services and assign the policy to the on-premises Linux server."
Answer:
B
Question 6
"A business has a hybrid cloud infrastructure with Oracle Linux instances running in OCI and on-
premises. They want to reduce the amount of bandwidth used when patching systems.
Which component of OS Management Hub can help to reduce the bandwidth usage for patching?
- A. Management stations
- B. Management agents
- C. Dynamic groups
- D. Profiles"
Answer:
D
Question 7
Based on the provided diagram, you have a group of critical compute instances in a private subnet
that require vulnerability using the Oracle Cloud Infrastructure (OCI) Vulnerability Scanning Service
(VSS).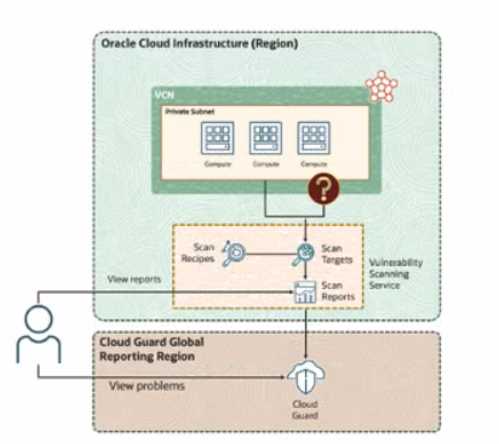
"What additional configuration is required to enable VSS to scan instances in the private subnet
- A. VSS cannot scan private instances. You need to move them to a public subnet for vulnerability scanning.
- B. Configure a service gateway in the VCN and a route rule to direct traffic for the VSS service through the gateway.
- C. No additional configuration is needed. VSS can access private instances by default.
- D. Use an OCI Bastion session to establish connectivity and forward scan results from the private instances."
Answer:
B
Question 8
"You are designing a secure access strategy for compute instances deployed within a private subnet
of an OCI Virtual Cloud Network (VCN). Your security policy requires that no compute instances in the
private subnet should have direct Internet access, and administrative access should be controlled.
Which statement best describes the role of an OCI Bastion in securing access to these private
compute instances?
- A. It provides a direct public endpoint for the compute instance, enabling remote access.
- B. It serves as a secondary authentication point, verifying user credentials before granting access to the compute instance.
- C. It acts as a firewall, blocking any external access to the private compute instance.
- D. It creates a secure, publicly accessible entry point to access target resources in a private subnet."
Answer:
D
Question 9
"You are part of the security operations of an organization with thousands of users accessing Oracle
Cloud Infrastructure (OCI). It is reported that an unknown user action was executed resulting in
configuration errors. You are tasked with identifying the details of all users who were active in the
last six hours along with any REST API calls that were executed.
Which OCI feature should you use?
- A. Audit Analysis Dashboard
- B. Management Agent Log Ingestion
- C. Object Collection Rule
- D. Service Connector Hub"
Answer:
A
Question 10
Which are the essential components to create a rule for the Oracle Cloud Infrastructure (OCI) Events
Service?
- A. Install Key and Service Connector
- B. Rule Conditions and Management Agent Cloud Service
- C. Rule Conditions and Actions
- D. Install Key and Actions
Answer:
C
Question 11
You are the first responder of a security incident for ABC Org. You have identified several IP addresses
and URLs in the logs that you suspect may be related to the incident. However, you need more
information to confidently determine whether they are indeed malicious or not.
Which OCI service can you use to obtain a more refined information and confidence score for these
identified indicators?
- A. OCI Incidence Responder
- B. OCI Threat Intelligence
- C. OCI Web Application Firewall
- D. OCI Security Zones
Answer:
B
Question 12
You're managing an Oracle Cloud Infrastructure (OCI) environment where a public website hosts
downloadable assets stored in Object Storage buckets. These buckets need to be publicly accessible
for website visitors, but Cloud Guard keeps flagging them as security risks.
How can Cloud Guard be configured to ignore problems specific to public buckets while still ensuring
security checks are applied to other resources that require them?
- A. A public bucket is a security risk, so Cloud Guard will keep detecting it.
- B. Resolve or remediate the problems by making the buckets private.
- C. Dismiss problems associated with those resources.
- D. Fix the baseline by configuring the Conditional groups for the detector.
Answer:
D
Question 13
Which Oracle Data Safe feature enables the Internal test, development, and analytics teams to
operate effectively while minimizing their exposure to sensitive data?
- A. Security assessment
- B. Data encryption
- C. Data auditing
- D. Sensitive data discovery
Answer:
D
Question 14
When trying to encrypt plaintext using Command Line Interface (CLI), the developer gets a Service
Error. This is the command the developer tried to run: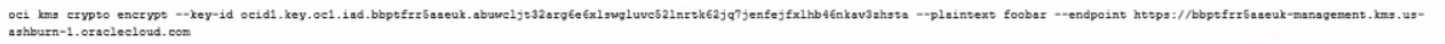
What is the reason for this error?
- A. The developer forgot to specify the region.
- B. The user should pass the key version OCID instead of the key OCID.
- C. The developer has the wrong endpoint.
- D. The plaintext needs to be in JSON form.
Answer:
B
Question 15
You are a security architect at your organization and have noticed an increase in cyberattacks on your
applications, including Cross-Site Scripting (XSS) and SQL Injection. To mitigate these threats, you
decide to use OCI Web Application Firewall (WAF).
Which type of OCI WAF rule should you configure to protect against these attacks?
- A. Access control rule
- B. Protection rule
- C. Rate Limiting rule
- D. Encryption rule
Answer:
B