oracle 1Z0-1104-21 Exam Questions
Questions for the 1Z0-1104-21 were updated on : Jul 08 ,2025
Page 1 out of 7. Viewing questions 1-15 out of 94
Question 1
When creating an OCI Vault, which factors may lead to select the Virtual Private Vault ? Select TWO
correct answers
- A. Need for more than 9211 key versions
- B. Greater degree of isolation
- C. To mask Pll data for non-production environment
- D. Ability to back up the vault
Answer:
BD
Explanation:
Question 2
Cloud Guard detected a risk score of zero in the dashboard, what does this mean ?
- A. Risk score doesn't say anything. These are just numbers
- B. LOW or MINOR issues
- C. Larger number of problems that have high risk levels ( HIGH or CRITICAL )
- D. No problem detected for any resource
Answer:
D
Explanation: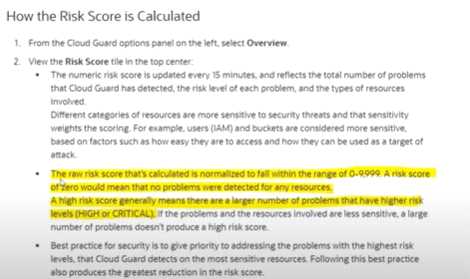
Question 3
With regard to vulnerability and cloud penetration testing, which rules of engagement apply? Select
TWO correct answers.
- A. Any port scanning must be performed in an aggressive mode
- B. Physical penetration and vulnerability testing of Oracle facilities is prohibited
- C. Testing should target any other subscription or any other Oracle Cloud customer resources
- D. You are responsible for any damages to Oracle Cloud customers that are caused by your testing activities
Answer:
BD
Explanation: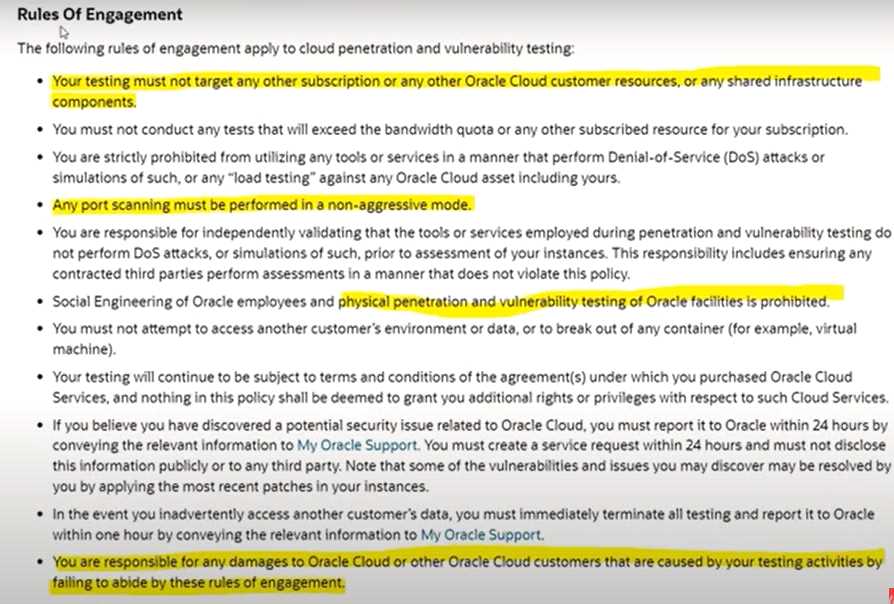
Question 4
How can you establish private connectivity over two VCN within same OCI region without traversing
the traffic over public internet ?
- A. NAT Gateway
- B. Data Guard
- C. Remote VCN Peering
- D. Local VCN Peering
Answer:
D
Explanation: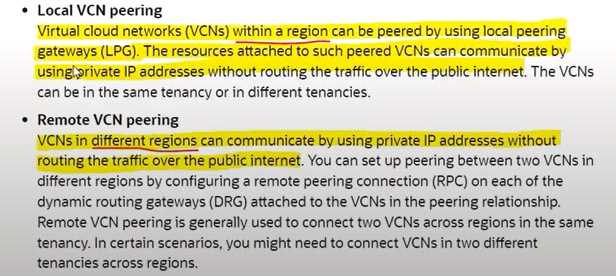
Question 5
Which security issues can be identified by Oracle Vulnerability Scanning Service? Select TWO correct
answers
- A. Distributed Denial of Service (DDoS)
- B. Ports that are unintentionally left open can be a potential attack vector for cloud resources
- C. SQL Injection
- D. CIS published Industry-standard benchmarks
Answer:
BD
Explanation: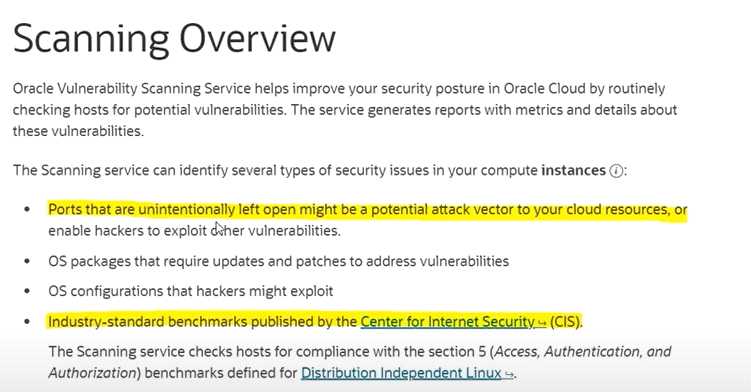
Question 6
Which resources can be used to create and manage from Vault Service ? Select TWO correct answers
- A. Secret
- B. IAM
- C. Keys
- D. Cloud Guard
Answer:
AC
Explanation: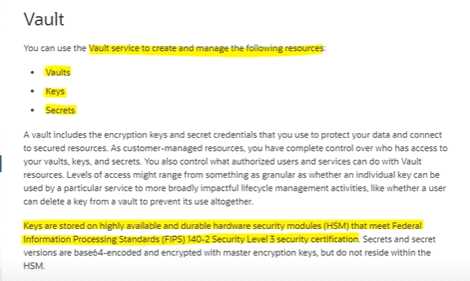
Question 7
Which VCN configuration is CORRECT with regard to VCN peering within a same region ?
- A. 12.0.0.0/16 and 194.168.0.0/16
- B. 12.0.0.0/16 and 12.0.0.0/16 C 194.168.0.0/24 and 194.168.0.0/24
- D. 194.168.0.0/24 and 194.168.0.0/16
Answer:
A
Question 8
Which IAM policy should be created to give XYZ the ability to list contents of a resource excluding the
f needs to authenticate in prod compartment ? Principle of least priviledge should be used.
- A. Allow group XYZ to manage all resources in compartment != prod
- B. Allow group XYZ to use all resources in compartment != prod
- C. Allow group XYZ to inspect all resources in tenancy where target.compartment.name != prod
- D. Allow group XYZ to read all resources in tenancy where target.compartment.name != prod
Answer:
C
Explanation: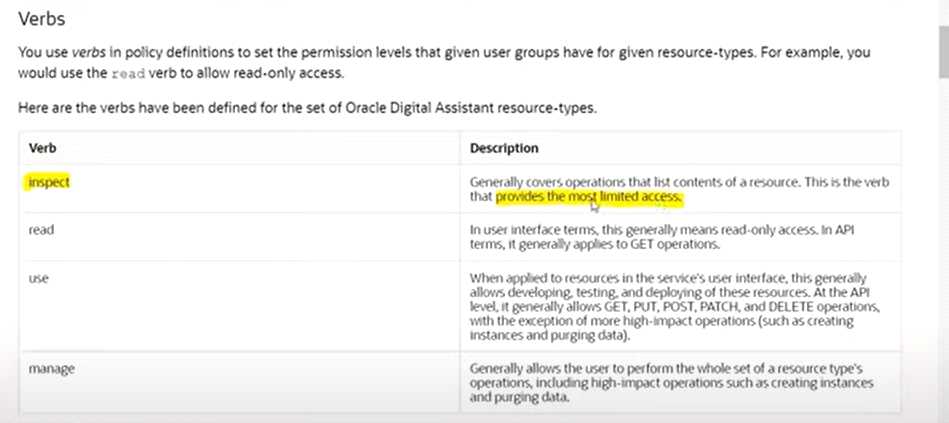
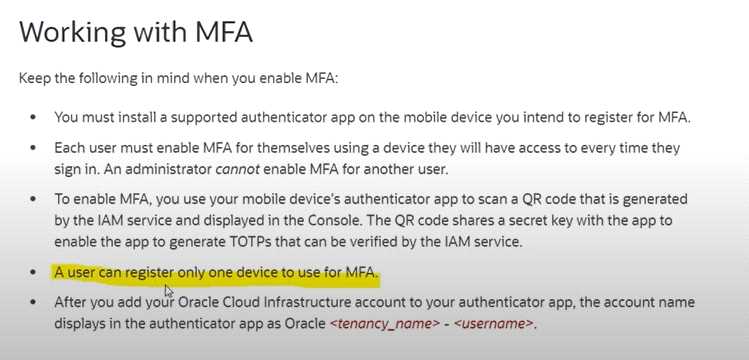
Question 9
Which statements are CORRECT about Multi-Factor Authentication in OCI ? Select TWO correct
answers
- A. Members of the Administrators group can disable MFA for other users
- B. Users cannot enable MFA for themselves
- C. A user can register multiple devices to use for MFA.
- D. Members of the Administrators group cannot enable MFA for another user
Answer:
AD
Explanation: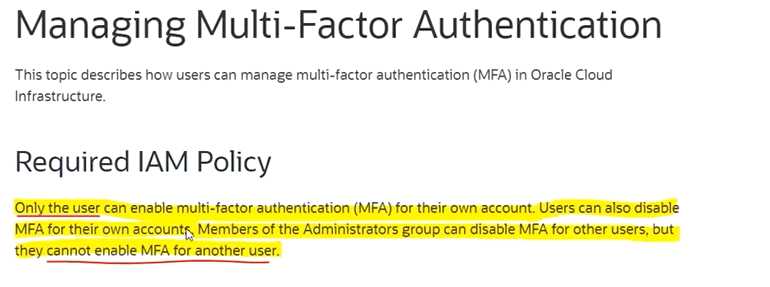
Question 10
Which statements are CORRECT about Security Zone policy in OCI ? Select TWO correct answers
- A. Block volume can be moved from a security zone to a standard compartment
- B. Bucket can't be moved from a security zone to a standard compartment
- C. Resources in a security zone must be accessible from internet
- D. Resources in a security zone must be encrypted using customer-managed keys
Answer:
BD
Explanation: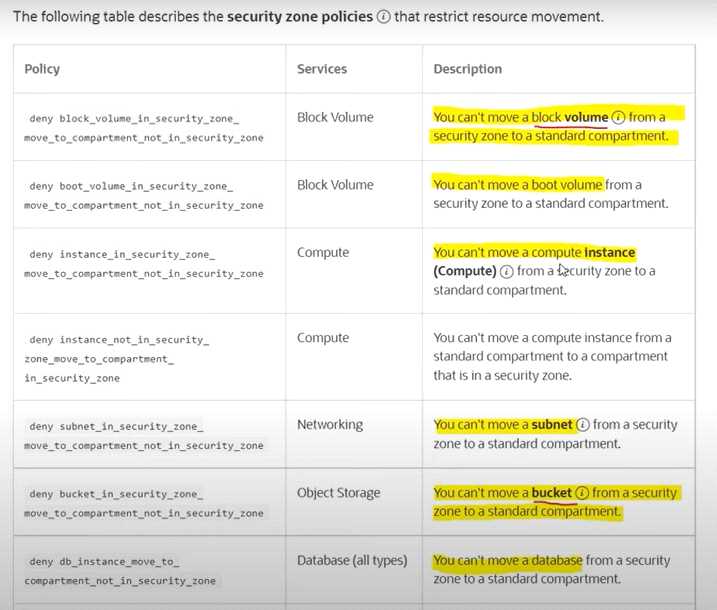
Question 11
Oracle Object Storage achieves data durability by which of the mechanisms ? Select TWO correct
answers
- A. Service Gateway
- B. Redundant Storage across availability domains
- C. Redundant Array of Independent Disks
- D. Object Versioning
Answer:
BD
Explanation: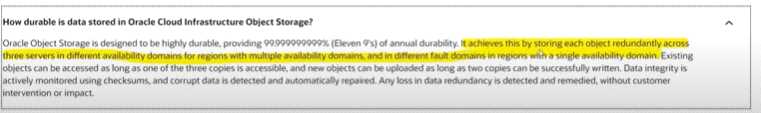
Question 12
Which OCI services can encrypt all data-at-rest ? Select TWO correct answers
- A. File Storage
- B. NAT Gateway
- C. Block Volumes
- D. Geolocation Steering
Answer:
AC
Explanation: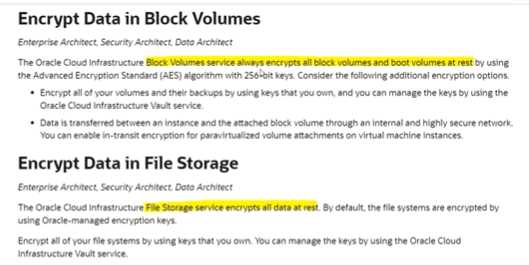
Question 13
As a Security Admin you want to inspect the metadata and actual data in your Oracle databases to
discover sensitive data and provide comprehensive results listing the sensitive columns and related
information. Which Data Safe feature will help you to achieve the above requirement ?
- A. Data Masking
- B. Data Discovery
- C. Security Assessment
- D. User Assessment
Answer:
B
Explanation: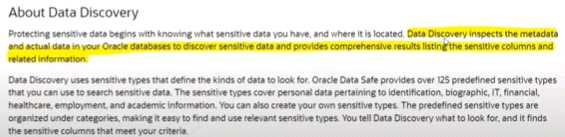
Question 14
What is the matching rule syntax for a single condition?
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
C
Explanation: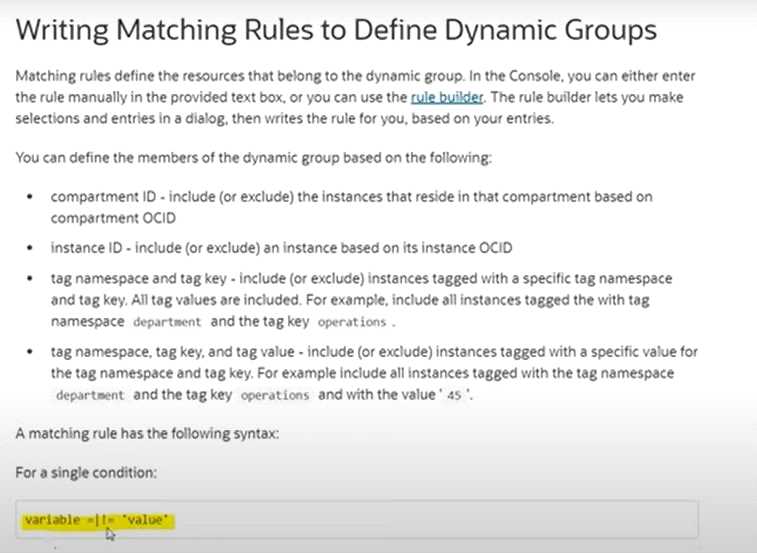
Question 15
What is the configuration to avoid publishing messages during the specified time range known as?
- A. Trigger rule
- B. Statistic
- C. Resource group
- D. Suppression
Answer:
D
Explanation: