oracle 1Z0-1084-21 Exam Questions
Questions for the 1Z0-1084-21 were updated on : Jul 05 ,2025
Page 1 out of 5. Viewing questions 1-15 out of 74
Question 1
Which one of the statements describes a service aggregator pattern?
- A. Serverless function execution is fully managed by a third party
- A. It is implemented in each service separately and uses a streaming service
- B. Long running tasks are perfectly suited for serverless
- B. It involves implementing a separate service that makes multiple calls to other backend services
- C. Applications running on a FaaS (Functions as a Service) platform
- C. It uses a queue on both sides of the service communication
- D. Application DevOps team is responsible for scaling
- D. It involves sending events through a message broker
- E. Serverless function state should never be stored externally
Answer:
B
Explanation:
Service Aggregator Pattern
Another option for eliminating microservice-to-microservice coupling is an
Aggregator microservice
,
shown in purple in Figure 4-10.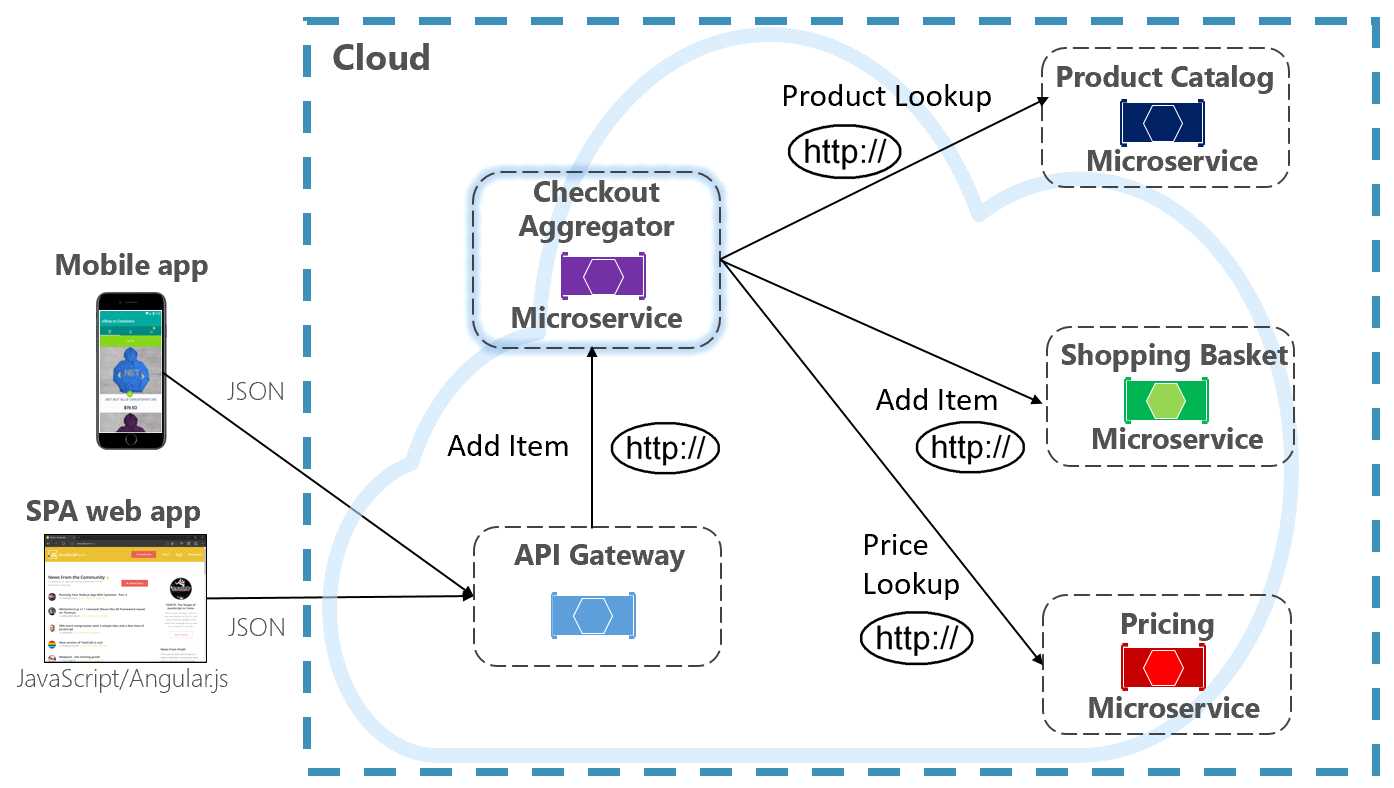
The pattern isolatesanoperation that makes calls to multipleback-end microservices, centralizing its
logic into a specialized microservice. The purple checkout aggregator microservice in the previous
figure orchestrates the workflow for the Checkout operation. It includes calls to several back-end
microservices in a sequenced order. Data from the workflow is aggregated and returned to the caller.
While it still implements direct HTTP calls, the aggregator microservice reduces direct dependencies
among back-end microservices.
Reference:
https://docs.microsoft.com/en-us/dotnet/architecture/cloud-native/service-to-service-
communication#:~:text=Service%20Aggregator%20Pattern&text=The%20pattern%20isolates%20an
%20operation,logic%20into%20a%20specialized%20microservice.&text=While%20it%20still%20impl
ements%20direct,dependencies%20among%20back%2Dend%20microservices.
Question 2
Which two statements accurately describe an Oracle Functions application?
- A. Controlling access to OCI resources
- A. A small block of code invoked in response to an Oracle Cloud Infrastructure (OCI) Events service
- B. Enabling CORS (Cross-Origin Resource Sharing) support
- B. A Docker image containing all the functions that share the same configuration
- C. Limiting the number of requests sent to backend services
- C. An application based on Oracle Functions, Oracle Cloud Infrastructure (OCI) Events and OCI API Gateway services
- D. Providing authentication and authorization
- D. A common context to store configuration variables that are available to all functions in the application
- E. A logical group of functions
Answer:
DE
Explanation:
Oracle Functions Concepts:
This topic describes key concepts you need to understand when using Oracle Functions.
Applications:
In Oracle Functions, an application is:
1. a logical grouping of functions
2. a common context to store configuration variables that are available to all functions in the
application
3. a way to ensure function runtime isolation
When you define an application in Oracle Functions, you specify the subnets in which to run the
functions in the application. When functions from different applications are invoked simultaneously,
Oracle Functions ensures these function executions are isolated from each other.
Oracle Functions shows applications and their functions in the Console.
Reference:
https://docs.cloud.oracle.com/en-us/iaas/Content/Functions/Concepts/functionsconcepts.htm
Question 3
You have been asked to create a stateful application deployed in Oracle Cloud Infrastructure (OCI)
Container Engine for Kubernetes (OKE) that requires all of your worker nodes to mount and write
data to persistent volumes.
Which two OCI storage services should you use?
- A. It cannot be done.
- A. Use OCI File Services as persistent volume.
- B. Use remote-exec
- B. Use GlusterFS as persistent volume.
- C. Download the script to a local desktop and execute the script.
- C. Use OCI Block Volume backed persistent volume.
- D. Use /bin/sh with the full path to the location of the script to execute the script.
- D. Use open source storage solutions on top of OCI.
- E. Use OCI Object Storage as persistent volume.
Answer:
AC
Explanation:
A PersistentVolume (PV)is a piece of storage in the cluster that has been provisioned by an
administrator. PVs are volume plugins like Volumes, but have a lifecycle independent of any
individual Pod that uses the PV.
A PersistentVolumeClaim (PVC)is a request for storage by a user. It is similar to a Pod. Pods consume
node resources and PVCs consume PV resources.
If you intend to create Kubernetes persistent volumes, sufficient block volume quota must be
available in each availability domain to meet the persistent volume claim. Persistent volume claims
must request a minimum of 50 gigabytes
You can define and apply a persistent volume claim to your cluster, which in turn creates a persistent
volume that's bound to the claim. A claim is a block storage volume in the underlying IaaS provider
that's durable and offers persistent storage, enabling your data to remain intact, regardless of
whether the containers that the storage is connected to are terminated.
With Oracle Cloud Infrastructure as the underlying IaaS provider, you can provision persistent volume
claims by attaching volumes from theBlock Storage service.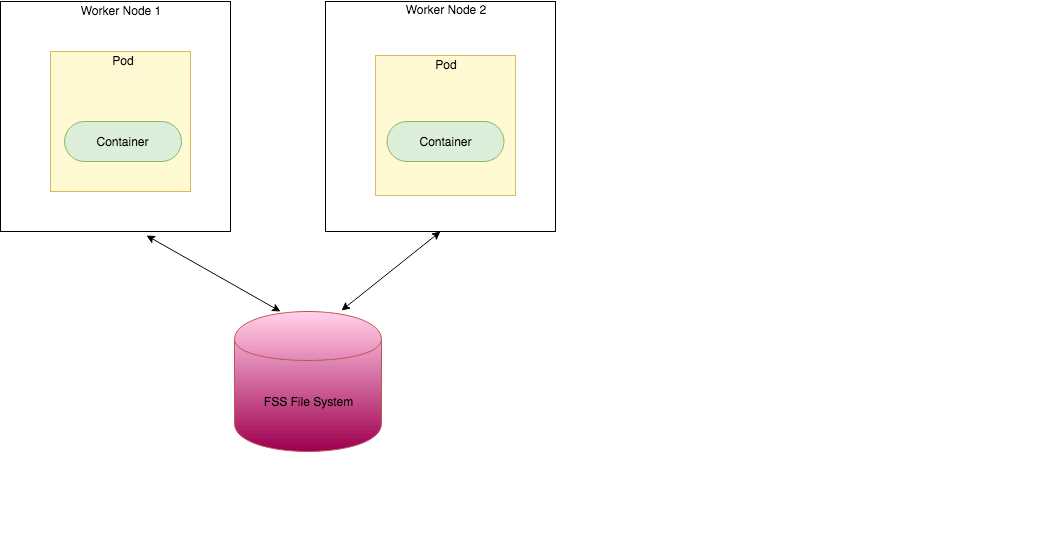
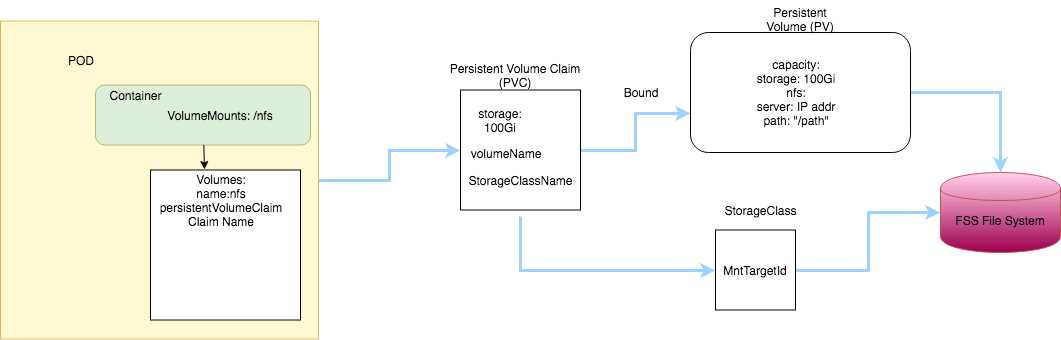
https://oracle.github.io/weblogic-kubernetes-operator/faq/oci-fss-pv/
https://kubernetes.io/docs/concepts/storage/persistent-volumes/
Question 4
You are a consumer of Oracle Cloud Infrastructure (OCI) Streaming service. Which API should you use
to read and process the stream?
- A. In blue/green, application is deployed in minor increments to a select group of people. In canary, both old and new applications are simultaneously in production.
- A. ListMessages
- B. In blue/green, both old and new applications are in production at the same time. In canary, application is deployed incrementally to a select group of people.
- B. GetMessages
- C. In blue/green, current applications are slowly replaced with new ones. In canary, both old and new applications are in production at the same time.
- C. GetObject
- D. In blue/green, current applications are slowly replaced with new ones. In canary, application is deployed incrementally to a select group of people.
- D. ReadMessages
Answer:
B
Explanation:
https://docs.cloud.oracle.com/en-us/iaas/Content/Streaming/Concepts/streamingoverview.htm
Building consumers to read and process messages from a stream using the
GetMessages
API .
How Streaming Works:
The Streaming serviceprovides a robust, scalable mechanism that you can use to produce and
consume high volumes of data between application components.
Here's how Streaming works: aproducerpublishesmessagesto astream, which is an append-only
log. These messages are distributed among the partitions using the message's key.
Streams are divided into a number ofpartitionsfor scalability. Partitions allow you to distribute a
stream by splitting messages across multiple nodes (or brokers). Each partition can be placed on a
separate machine to allow multiple consumers to read a stream in parallel. Multiple consumers can
read from any partition regardless of where the partition is hosted.
Aconsumercanread messages from one or more streams.Each message within a stream is marked
with an offset value, so a consumer can pick up where it left off if it is interrupted.
You can use the Streaming service by:
A.Creating a stream using the Console or API.
B.Using a producer to publish data to the stream.
C. Building consumerstoreadand processmessagesfrom astream using the
GetMessages
API ..
Reference:
https://docs.cloud.oracle.com/en-us/iaas/Content/Streaming/Concepts/streamingoverview.htm
Question 5
Which two handle Oracle Functions authentication automatically?
- A. Oracle Cloud Infrastructure SDK
- B. cURL
- C. Oracle Cloud Infrastructure CLl
- D. Oracle Cloud Infrastructure CLI
- D. Signed HTTP Request
- E. Fn Project CLI
Answer:
CE
Explanation:
If you use theFn Project CLI or the Oracle Cloud Infrastructure CLI to invoke a
function,authentication is handled for you.See
Using the Fn Project CLI to Invoke
Functions
and
Using the Oracle Cloud Infrastructure CLI to Invoke Functions
.
If you use an Oracle Cloud Infrastructure SDK to invoke a function, you can use the SDK to handle
authentication. See
Using SDKs to Invoke Functions
.
If you make a signed HTTP request to a function's invoke endpoint, you'll have to handle
authentication yourself by including a signature and the OCID of the compartment to which the
function belongs in the request header
Fn Project CLIyou can create an Fn Project CLI Context to Connect to Oracle Cloud Infrastructure and
specify --provider oracle This option enables Oracle Functions to perform authentication and
authorization using Oracle Cloud Infrastructure request signing, private keys, user groups, and
policies that grant permissions to those user groups.
Reference:
https://blogs.oracle.com/developers/oracle-functions-invoking-functions-automatically-with-cloud-
events
https://docs.cloud.oracle.com/en-us/iaas/Content/Functions/Tasks/functionsinvokingfunctions.htm
Question 6
You are building a cloud native, serverless travel application with multiple Oracle Functions in Java,
Python and Node.js. You need to build and deploy these functions to a single applications named
travel-app.
Which command will help you complete this task successfully?
- A. Penetration testing
- A. oci fn function deploy --ap travel-ap --all
- B. Automated testing
- B. fn -v deploy --ap travel-ap -- all
- C. Integration testing
- C. oci fn application --application-name-ap deploy --all
- D. A/B testing
- D. fn function deploy --all --application-name travel-ap
Answer:
B
Explanation:
To get started with Oracle Functions:
Creating, Deploying, and Invoking a Helloworld Function
Step 6- Change directory to the newly created helloworld-func directory.
Step 7- Enter the following single Fn Project commandto build the function and its dependencies as
a Docker image called helloworld-func, push the image to the specified Docker registry, and deploy
the function to Oracle Functions in the helloworld-app:
$ fn -v deploy --app helloworld-app
The-voption simply shows more detail about what Fn Project commands are doing (see
Using the Fn
Project CLI with Oracle Functions
).
Reference:
https://docs.cloud.oracle.com/en-us/iaas/Content/Functions/Tasks/functionscreatingfirst.htm
Question 7
A pod security policy (PSP) is implemented in your Oracle Cloud Infrastructure Container Engine for
Kubernetes cluster Which rule can you use to prevent a container from running as root using PSP?
- A. Create a Kubernetes secret with contents from the instance Wallet files. Use this secret to create a volume mounted to the appropriate path in the application deployment manifest.
- A. NoPrivilege
- B. Install the Oracle Cloud Infrastructure Service Broker on the Kubernetes cluster and deploy ServiceInstance and ServiceBinding resources for ATP. Then use the specified binding name as a volume in the application deployment manifest.
- B. RunOnlyAsUser
- C. Use Kubernetes secrets to configure environment variables on the container with ATP instance OCID, and OCI API credentials. Then use the CreateConnection API endpoint from the service runtime.
- C. MustRunAsNonRoot
- D. Enable Oracle REST Data Services for the required schemas and connect via HTTPS.
- D. forbiddenRoot
Answer:
C
Explanation:
What is a Pod Security Policy?
APod Security Policyis a cluster-level resource that controls security sensitive aspects of the pod
specification. The
PodSecurityPolicy
objects define a set of conditions that a pod must run with in
order to be accepted into the system, as well as defaults for the related fields. They allow an
administrator to control the following:
Privilege Escalation
These options control theallowPrivilegeEscalationcontainer option. This bool directly controls
whether the
no_new_privs
flag gets set on the container process. This flag will
preventsetuidbinaries from changing the effective user ID, and prevent files from enabling extra
capabilities (e.g. it will prevent the use of thepingtool).This behavior is required to effectively
enforceMustRunAsNonRoot.
example:
# Require the container to run without root privileges.
rule: 'MustRunAsNonRoot'
Reference:
https://kubernetes.io/docs/concepts/policy/pod-security-policy/
Question 8
You are working on a serverless DevSecOps application using Oracle Functions. You have deployed a
Python function that uses the Oracle Cloud Infrastructure (OCI) Python SDK to stop any OC1 Compute
instance that does not comply with your corporate security standards There are 3 non compliant OCI
Compute instances.
However, when you invoke this function none of the instances were stopped. How should you
troubleshoot this?
- A. fn function deploy --all --application-name travel-app
- A. There is no way to troubleshoot a function running on Oracle Functions.
- B. fn deploy --app travel-app --all
- B. Enable function logging in the OCI console, include some print statements in your function code and use logs to troubleshoot this.
- C. oci fn application --application-name travel-app deploy --all
- C. Enable function remote debugging in the OCI console, and use your favorite IDE to inspect the function running on Oracle Functions.
- D. oci fn function deploy --app travel-app --all
- D. Enable function tracing in the OCI console, and go to OCI Monitoring console to see the function stack trace.
Answer:
B
Explanation:
Storing and Viewing Function Logs:
When a function you've deployed to Oracle Functions is invoked,you'll typically want to store the
function's logsso that you can review them later. You specify where Oracle Functions stores
afunction's logs by setting a logging policy for the application containing the function.
You can specify that Oracle Functions:
Stores logs in Oracle Cloud Infrastructure. Until an Oracle Cloud Infrastructure logging service is
released, Oracle Functions storeslogs as files in a storage bucket in Oracle Cloud Infrastructure
Object Storage.
Note that to view function logs in a storage bucket,the group to which you belong must have been
granted access with the following identity policy statements:
Allow group <group-name> to manage object-family in compartment <compartment-name>
Allow group <group-name> to read objectstorage-namespaces in compartment <compartment-
name>(Usually created when configuring your tenancy for function development. See
Create a
Policy to Give Oracle Functions Users Access to Oracle Cloud Infrastructure Registry Repositories
.)
Stores logs by exporting them to an external logging destination like Papertrail. Note that to use an
external logging destination, you must have set up a VCN with public subnets and an internet
gateway (see
Create the VCN and Subnets to Use with Oracle Functions, if they don't exist already
).
You set application logging policies in the Console.
Reference:
https://docs.cloud.oracle.com/en-
us/iaas/Content/Functions/Tasks/functionsexportingfunctionlogfiles.htm
Question 9
Which statement accurately describes Oracle Cloud Infrastructure (OCI) Load Balancer integration
with OCI Container Engine for Kubernetes (OKE)?
- A. Invoke from Oracle Cloud Infrastructure CLI
- A. OKE service provisions an OCI Load Balancer instance for each Kubernetes service with LoadBalancer type in the YAML configuration.
- B. Trigger by an event in Oracle Cloud Infrastructure Events service
- B. OCI Load Balancer instance provisioning is triggered by OCI Events service for each Kubernetes service with LoadBalancer type in the YAML configuration.
- C. Invoke from Fn Project CLI
- C. OCI Load Balancer instance must be manually provisioned for each Kubernetes service that requires traffic balancing.
- D. Invoke from Docker CLI
- D. OKE service provisions a single OCI Load Balancer instance shared with all the Kubernetes services with LoadBalancer type in the YAML configuration.
- E. Send a signed HTTP requests to the function’s invoke endpoint
Answer:
D
Explanation:
If you are running your Kubernetes cluster on Oracle Container Engine for Kubernetes (commonly
known as OKE), you can have OCI automatically provision load balancers for you by creating
aServiceof typeLoadBalancerinstead of (or in addition to) installing an ingress controller like Traefik
or Voyage
YAML file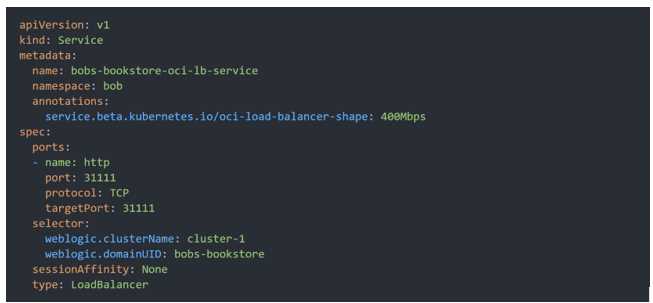
When you apply this YAML file to your cluster, you will see the new service is created. After a short
time (typically less than a minute) the OCI Load Balancer will be provisioned.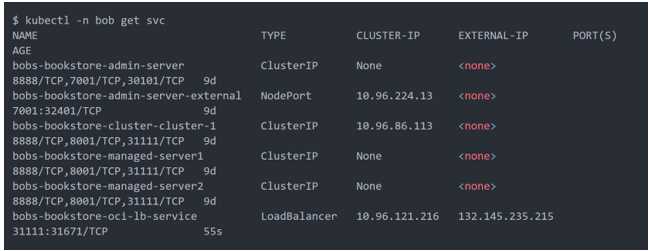
https://oracle.github.io/weblogic-kubernetes-operator/faq/oci-lb/
Question 10
Which Oracle Cloud Infrastructure (OCI) load balancer shape is used by default in OCI container
Engineer for Kubernetes?
- A. (request-target)
- A. 400 Mbps
- B. host
- B. 8000 Mbps
- C. date or x-date
- C. There is no default. The shape has to be specified.
- D. content-type
- D. 100 Mbps
Answer:
D
Explanation:
Specifying Alternative Load Balancer Shapes
The shape of an Oracle Cloud Infrastructure load balancer specifies its maximum total bandwidth
(that is, ingress plus egress).By default, load balancers are created with a shape of 100Mbps. Other
shapes are available, including 400Mbps and 8000Mbps.
SHAPE
A template that determines the load balancer's total pre-provisioned maximum capacity (bandwidth)
for ingress plus egress traffic. Available shapes include 10Mbps, 100 Mbps, 400 Mbps, and 8000
Mbps.
Reference:
https://docs.cloud.oracle.com/en-us/iaas/Content/ContEng/Tasks/contengcreatingloadbalancer.htm
https://docs.cloud.oracle.com/en-us/iaas/Content/Balance/Concepts/balanceoverview.htm
Question 11
You have written a Node.js function and deployed it to Oracle Functions. Next, you need to call this
function from a microservice written in Java deployed on Oracle Cloud Infrastructure (OCI) Container
Engine for Kubernetes (OKE).
Which can help you to achieve this?
- A. Service choreography relies on a central coordinator.
- A. Use the OCI CLI with kubect1 to invoke the function from the microservice.
- B. Service choreography should not use events for communication.
- B. Oracle Functions does not allow a microservice deployed on OKE to invoke a function.
- C. Services involved in choreography communicate through messages/messaging systems.
- C. OKE does not allow a microservice to invoke a function from Oracle Functions.
- D. Decision logic in service choreography is distributed.
- D. Use the OCI Java SDK to invoke the function from the microservice.
- E. Service choreographer is responsible for invoking other services.
Answer:
D
Explanation:
Invoking Functions
You can invoke a function that you've deployed to Oracle Functions in different ways:
1. Using the Fn Project CLI.
2. Using the Oracle Cloud Infrastructure CLI.
3. Using the Oracle Cloud Infrastructure SDKs.
4. Making a signed HTTP request to the function's invoke endpoint. Every function has an invoke
endpoint.
Using the Fn Project CLI to Invoke Functions
To invoke a function deployed to Oracle Functions using the Fn Project CLI:
Log in to your development environment as a functions developer.
In a terminal window, enter:
$ fn invoke <app-name> <function-name>
Using SDKs to Invoke Functions:
If you're writing a program to invoke a function in a language for which anOracle Cloud
Infrastructure SDK exists,Oracle recommends you use that SDKtosend API requests to invoke the
function. Among other things, the SDK will facilitate Oracle Cloud Infrastructure authentication.
Reference:
https://docs.cloud.oracle.com/en-us/iaas/Content/Functions/Tasks/functionsinvokingfunctions.htm
Question 12
A developer using Oracle Cloud Infrastructure (OCI) API Gateway must authenticate the API requests
to their web application. The authentication process must be implemented using a custom scheme
which accepts string parameters from the API caller. Which method can the developer use In this
scenario?
- A. An HTTP 401 will be returned if the client’s clock is skewed more than 5 minutes from the server’s.
- A. Create an authorizer function using request header authorization.
- B. The request must include an authorization signing string including (but not limited to) x-content-sha256, content-type, and content-length headers.
- B. Create an authorizer function using token-based authorization.
- C. The request does not require an Authorization header.
- C. Create a cross account functions authorizer.
- D. The Content-Type header must be set to application/json
- D. Create an authorizer function using OCI Identity and Access Management based authentication
Answer:
A
Explanation:
Using Authorizer Functions to Add Authentication and Authorization to API Deployments:
You cancontrol access to APIs you deploy to API gateways using an 'authorizer function'(as
described in this topic), or using JWTs (as described in
Using JSON Web Tokens (JWTs) to Add
Authentication and Authorization to API Deployments
).
You can add authentication and authorization functionality to API gatewaysby writing an'authorizer
function'that:
1. Processesrequest attributesto verify the identity of a caller with an identity provider.
2.Determines the operations that the caller is allowed to perform.
3.Returns the operations the caller is allowed to perform as a list of 'access scopes' (an 'access scope'
is an arbitrary string used to determine access).
Optionally returns a key-value pair for use by the API deployment. For example, as a context variable
for use in an HTTP back end definition (see
Adding Context Variables to Policies and HTTP Back End
Definitions
).
Create an authorizer function using request header authorizationimplemented using a custom
scheme which accepts string parameters from the API caller.
Managing Input Parameters
In our case we will need to manage quite a few static parameters in our code.For example the URLs
of the secrets service endpoints, the username and other constant parameterised data. We can
manage these either at Application or Function level (an OCI Function is packaged in an Application
which can contain multiple Functions). In this case I will create function level parameters. You can
use the following command to create the parameters:
fn config function test idcs-assert idcsClientId aedc15531bc8xxxxxxxxxxbd8a193
Reference:
https://technology.amis.nl/2020/01/03/oracle-cloud-api-gateway-using-an-authorizer-function-for-
client-secret-authorization-on-api-access/
https://docs.cloud.oracle.com/en-
us/iaas/Content/APIGateway/Tasks/apigatewayusingauthorizerfunction.htm
https://www.ateam-oracle.com/how-to-implement-an-oci-api-gateway-authorization-fn-in-nodejs-
that-accesses-oci-resources
Question 13
What is one of the differences between a microservice and a serverless function?
- A. Tiller enabled on the OKE cluster
- A. Microservices are used for long running operations and serverless functions for short running operations.
- B. A configured OCI API signing key pair
- B. Microservices always use a data store and serverless functions never use a data store.
- C. An SSH key pair with the public key added to cluster worker nodes
- C. Microservices are stateless and serverless functions are stateful.
- D. Install and configure the OCI CLI
- D. Microservices are triggered by events and serverless functions are not.
- E. OCI Identity and Access Management Auth Token
Answer:
A
Explanation:
microservice is larger and can do more than a function. A function is a relatively small bit of code that
performs only one action in response to an event.
Many microservices can run on several servers, and different instances of a specific microservice can
run on several servers.
In many cases, microservices can be decomposed into a number of smaller stateless functions. The
difference between microservices and functions is not simply the size. Functions are stateless, and
they require no knowledge about or configuration of the underlying serverhence, the
termserverless.
Microservices are best suited for long-running, complex applicationsthat have significant resource
and management requirements. You can migrate an existing monolithic application to microservices,
which makes it easier to modularly develop features for the application and deploy it in the cloud.
Microservices are also a good choice for building e-commerce sites, as they can retain information
throughout a transaction and meet the needs of a 24/7 customer base.
On the other hand, serverless functions only execute when needed. Once the execution is over, the
computing instance that runs the code decommissions itself. Serverless aligns with applications that
are event driven, especially when the events are sporadic and the event processing is not resource-
intensive. Serverless is a good choice when developers need todeploy fast and there are minimal
application scaling concerns.For example, a good use of serverless computing is a scheduled task
that needs to perform some
data aggregation
and will execute for just a few seconds.
Reference:
https://www.cloudflare.com/learning/serverless/glossary/serverless-microservice/
https://developer.oracle.com/java/fn-project-introduction.html
https://searchapparchitecture.techtarget.com/answer/When-should-I-choose-between-serverless-
and-microservices
Question 14
Which is NOT a valid option to execute a function deployed on Oracle Functions?
- A. OCI Load Balancer instance provisioning is triggered by OCI Events service for each Kubernetes service with LoadBalancer type in the YAML configuration.
- A. Send a signed HTTP requests to the function's invoke endpoint
- B. OKE service provisions an OCI Load Balancer instance for each Kubernetes service with LoadBalancer type in the YAML configuration.
- B. Invoke from Oracle Cloud Infrastructure CLI
- C. OCI Load Balancer instance must be manually provisioned for each Kubernetes service that requires traffic balancing.
- C. Invoke from Docker CLI
- D. OKE service provisions a single OCI Load Balancer instance shared with all the Kubernetes services with LoadBalancer type in the YAML configuration.
- D. Trigger by an event in Oracle Cloud Infrastructure Events service
- E. Invoke from Fn Project CLI
Answer:
C
Explanation:
You can invoke a function that you've deployed to Oracle Functions in different ways:
Using the Fn Project CLI.
Using the Oracle Cloud Infrastructure CLI.
Using the Oracle Cloud Infrastructure SDKs.
Making a signed HTTP request to the function's invoke endpoint. Every function has an invoke
endpoint.
Each of the above invokes the function via requests to the API. Any request to the API must be
authenticated by including a signature and the OCID of the compartment to which the function
belongs in the request header. Such a request is referred to as a 'signed' request. The signature
includes Oracle Cloud Infrastructure credentials in an encrypted form.
Question 15
Per CAP theorem, in which scenario do you NOT need to make any trade-off between the
guarantees?
- A. Use a third party service integration to implement a DDoS attack mitigation.
- A. when there are no network partitions
- B. Use OCI virtual cloud network (VCN) segregation to control DDoS.
- B. when the system is running in the cloud
- C. Use OCI API Gateway service and configure rate limiting.
- C. when the system is running on-premise
- D. Re-write your web service and implement rate limiting.
- D. when you are using load balancers
Answer:
A
Explanation:
(1) CAP THEOREM
"CONSISTENCY, AVAILABILITY and PARTITION TOLERANCE are the features that we want in our
distributed system together"
Of three properties of shared-data systems (Consistency, Availability andtolerance to network
Partitions) only two can be achieved at any given moment in time.
(2) In a distributed system, you can have both Consistency and Availability,exceptwhen there is a
Partition:
Relaxing the consistency requirements usually makes it easier to maintain availability, but the CAP
theorem is not an excuse to give up strong consistency across the board. A well-designed system can
balance both availability and consistency while tolerating partitions over a range of tradeoffs, where
eventual consistency is just one possibility.
Reference:
https://blogs.oracle.com/maa/the-cap-theorem:-consistency-and-availability-except-when-
partitioned