nokia 4A0-D01 Exam Questions
Questions for the 4A0-D01 were updated on : Feb 20 ,2026
Page 1 out of 3. Viewing questions 1-15 out of 35
Question 1
Based on the exhibit output, which of the following is NOT the reason the user runs the “baseline
diff” command?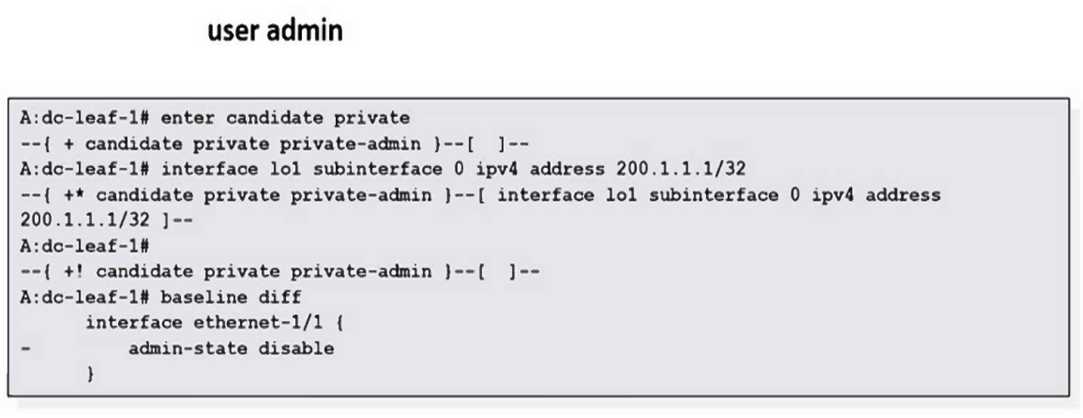
- A. User admin is not able to commit their changes.
- B. Another user has committed changes.
- C. User admin wants to check if there are differences between the current running config and their baseline datastore.
- D. User admin notices that “!” appears in the CLI prompt.
Answer:
A
Explanation:
The "baseline diff" command is used to compare the candidate configuration against the baseline
datastore to see changes or conflicts, especially when multiple users are involved or to verify
differences. It does not indicate that the user is unable to commit changes.
Question 2
How are LLDP frames advertised between two Nokia SR Linux routers?
- B. They are forwarded to the destination node based on the MAC VRF table.
- C. They are periodically flooded to the broadcast MAC address on each interface.
- D. They are routed to the destination node based on the IP VRF forwarding table.
Answer:
B
Explanation:
LLDP frames are periodically sent to a well-known multicast MAC address on each interface to
discover directly connected devices.
Question 3
How does Nokia’s Fabric Services System use a fabric intent to build the DC switch fabric?
- A. It uses a YAML file that defines the intended configuration state of the DC fabric.
- B. It uses a digital sandbox to connect workloads to the DC fabric.
- C. It uses a digital sandbox to build the configuration files for the DC fabric.
- D. It uses telemetry data to build the configuration files for the DC fabric.
Answer:
A
Explanation:
Nokia’s Fabric Services System uses a fabric intent defined in a declarative YAML file to specify the
desired state of the data center fabric, which is then used to build and configure the fabric
accordingly.
Question 4
Which of the following is NOT part of Day 2+ operations with Nokia’s Fabric Services System?
- A. Monitor the data center fabric using model-driven telemetry.
- B. Analyze the overall health of the data center fabric for proactive operations.
- C. Use the digital sandbox to test and validate configuration changes and upgrades.
- D. Use a fabric intent to build and validate design templates.
Answer:
D
Explanation:
Using a fabric intent to build and validate design templates is primarily a Day 0 or Day 1 activity
focused on initial fabric deployment and design, not part of Day 2+ operational tasks like monitoring,
health analysis, or change validation.
Question 5
When autoboot flag is set in grub.cfg, which of the following is NOT performed as part of the Zero
Touch Provisioning (ZTP) autoboot process?
- A. Uses the DHCP server to provide the IP address and default gateway
- B. Uses the Web or FTP server to provide the RPM packages and any necessary images
- C. Downloads and executes provisioning scripts
- D. Uses Nokia’s Fabric Services System to deploy the digital sandbox automatically
Answer:
D
Explanation:
The ZTP autoboot process does not automatically use Nokia’s Fabric Services System to deploy the
digital sandbox; it focuses on network boot, DHCP IP assignment, and downloading/executing
provisioning scripts from web or FTP servers.
Question 6
Which of the following statements about Zero Touch Provisioning (ZTP) is FALSE?
- A. The ZTP process downloads a provisioning script defined in the TLS profile.
- B. The ZTP process is managed by the ZTP application in Nokia SR Linux.
- C. The ZTP process relies on a DHCP server for an IP address.
- D. ZTP allows a router to become operational in the network without any pre-provisioning.
Answer:
A
Explanation:
The ZTP process downloads a provisioning script typically from a defined URL or server, not from a
TLS profile. The TLS profile is used for securing communications but does not define the provisioning
script location.
Question 7
Which of the following is NOT one of the user types supported in Nokia SR Linux?
- A. SR Linux users
- B. Regular Linux OS users
- C. Container users
- D. Remote users
Answer:
D
Explanation:
Nokia SR Linux supports SR Linux users, regular Linux OS users, and container users. "Remote users"
is not a defined user type within SR Linux user management.
Question 8
Based on the exhibit output, which of the following statements is TRUE?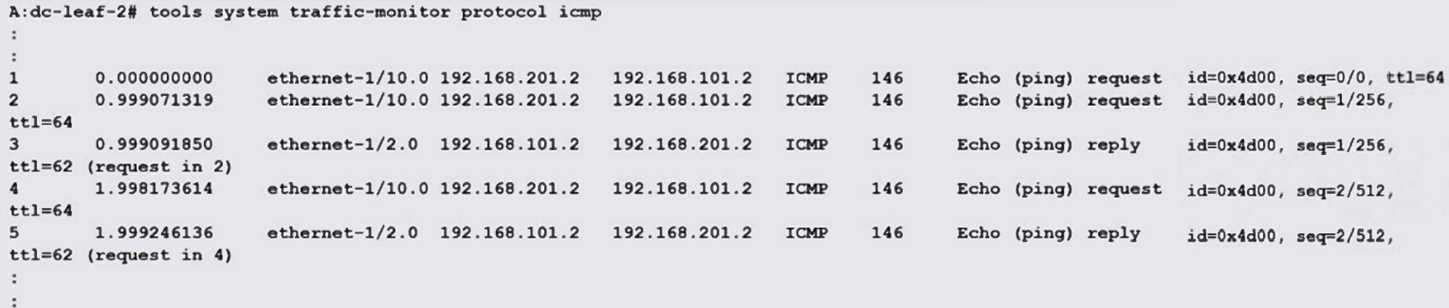
- A. An ACL filter is configured to accept ICMP packets, which are then processed by the tcpdump-like utility.
- B. capture-filter is configured to copy ICMP packets to the CPM where they are processed by the tcpdump-like utility.
- C. A cpm-filter policer is configured to rate limit ICMP packets, which are then captured in a log file.
- D. A cpm-filter is configured to accept ICMP packets, which are then captured in a log file.
Answer:
B
Explanation:
The exhibit shows ICMP packets being captured and displayed by a tcpdump-like utility, which
indicates that a capture-filter is configured to copy ICMP packets to the Control Plane Manager
(CPM) where they are processed and monitored.
Question 9
Which of the following statements about a CPM-filter policer is FALSE?
- A. Hierarchical policing of control plane traffic is supported.
- B. The system-cpu-policer is hardware-based.
- C. The system-cpu-policer acts on the aggregate traffic from all line cards.
- D. CPM-filter entries can use both a distributed-policer and a system-cpu-policer.
Answer:
B
Explanation:
The system-cpu-policer in Nokia SR Linux is software-based, not hardware-based. It acts on aggregate
control plane traffic and supports hierarchical policing with CPM-filter entries using both distributed
and system-cpu-policers.
Question 10
Which of the following Nokia’s SR Linux ACLs is instantiated on all line cards to copy incoming
packets to the CPM?
- A. Capture-filter ACL
- B. CPM-filter ACL
- C. Ingress ACL
- D. Egress ACL
Answer:
B
Explanation:
The CPM-filter ACL is instantiated on all line cards in Nokia’s SR Linux to copy incoming packets to the
Control Plane Manager (CPM) for processing.
Question 11
Based on the exhibit output, what CLI command can be used to display the contents of “bgp-log” in
Nokia’s SR Linux?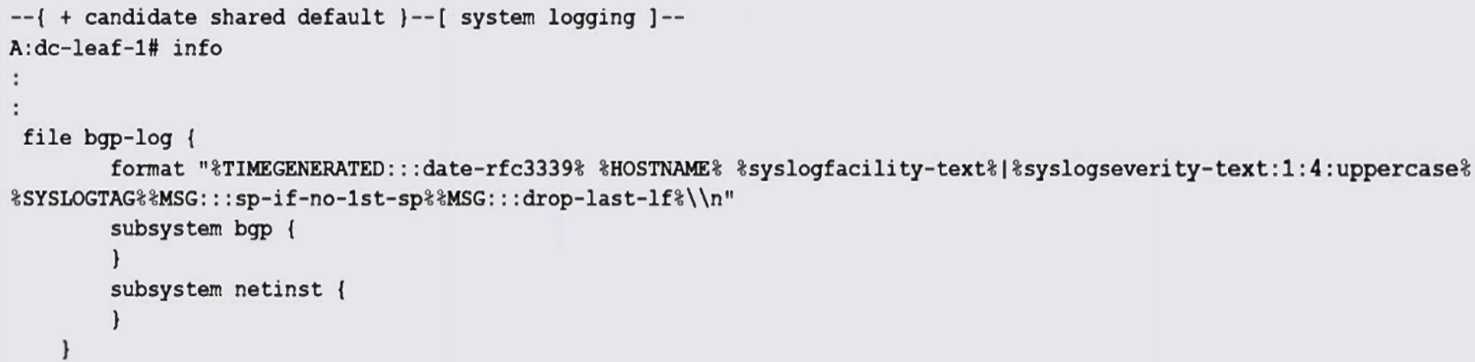
- A. show system logging buffer bgp-log
- B. show system logging file bgp-log
- C. info system logging buffer bgp-log
- D. info system logging file bgp-log
Answer:
B
Explanation:
The "bgp-log" is defined as a log file in the configuration, so the correct command to display its
contents is show system logging file bgp-log.
Question 12
Which of the following is NOT a valid logging source used in Nokia’s SR Linux?
- A. Linux facility + priority
- B. Console
- C. SR Linux subsystem + priority
- D. Syslog filter
Answer:
D
Explanation:
"Syslog filter" is not a logging source; it is a mechanism used to filter log messages. Valid logging
sources in SR Linux include Linux facility + priority, console, and SR Linux subsystem + priority.
Question 13
Which of the following statements about Nokia’s SR Linux logging is FALSE?
- A. SR Linux logs are handled using facility Iocal6 of the native Linux syslog utility.
- B. SR Linux logs can be saved locally as an encrypted file.
- C. SR Linux supports the use of filters to select log messages.
- D. Logging parameter configuration is translated into the /etc/rsyslog.conf file.
Answer:
B
Explanation:
Nokia SR Linux does not natively support saving logs locally as encrypted files. Logs are managed
using standard Linux syslog facilities and can be filtered, but encryption of local log files is not a built-
in feature.
Question 14
Examine the exhibit. What type of information is NOT included in the IMET route advertised by
VTEP1?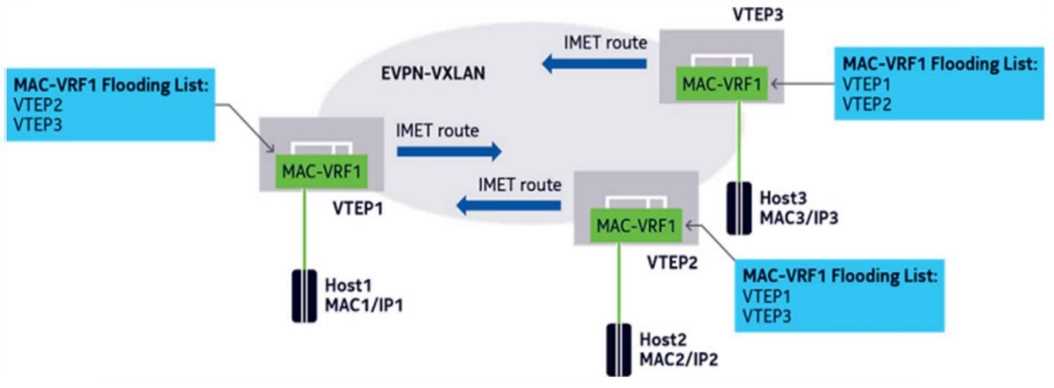
- A. VXLAN network identifier (VNI)
- B. Flooding list
- C. Route distinguisher of VTEP1’s MAC-VRF
- D. IP address of VTEP1
Answer:
C
Explanation:
The IMET route includes the VNI, flooding list, and IP address of the originating VTEP, but it does not
include the route distinguisher of the VTEP’s MAC-VRF.
Question 15
Which of the following statements about multi-homing in EVPN is FALSE?
- A. Type 1 Ethernet Auto-Discovery (A-D) EVPN route is used to support EVPN multi-homing.
- B. Type 4 Ethernet Segment (ES) EVPN route is used for designated forwarder (DF) election for an ES.
- C. The ES identifier (ESI) uniquely identifies an ES and it is locally significant for a particular leaf.
- D. The Ethernet Segment (ES) identifies a set of links that connects a host to one or more leafs.
Answer:
C
Explanation:
The Ethernet Segment Identifier (ESI) uniquely identifies an Ethernet Segment (ES) globally across
the EVPN domain, not just locally for a particular leaf.