netskope NSK300 Exam Questions
Questions for the NSK300 were updated on : Feb 20 ,2026
Page 1 out of 4. Viewing questions 1-15 out of 60
Question 1
Your customer is currently using Directory Importer with Active Directory (AD) to provision users to
Nelskope. They have recently acquired three new companies (
- A. Users from Company B and Company C cannot be provisioned because the customer is already using AD Importer.
- B. Either Company B or Company C users cannot be provisioned because integration with only one SCIM solution is allowed.
- C. Users from Companies A. B, and C can be provisioned to Netskope by deploying additional AD Importers and integrating more than one SCIM solution.
- D. Company A users cannot be provisioned to Netskope because the customer is already using AD Importer to import users from another Active Directory environment.
Answer:
C
Explanation:
Users from Companies A, B, and C can indeed be provisioned to Netskope. Company A, which uses
Active Directory, can continue to use the existing AD Importer. For Company B that uses Azure AD
and Company C that uses Okta Universal Directory, integration with SCIM (System for Cross-domain
Identity Management) solutions is possible.
Netskope supports provisioning users from multiple
directories, including Active Directory and cloud-based identity providers like Azure AD and Okta, by
using additional AD Importers and integrating more than one SCIM solution12
.
Reference: The correct approach for provisioning users from different companies that use various
directory services is supported by Netskope’s capabilities to integrate with multiple identity
providers and directory services, as outlined in their documentation and community resources12
.
Question 2
You are troubleshooting an issue with users who are unable to reach a financial SaaS application
when their traffic passes through Netskope. You determine that this is because of IP restrictions in
place with the SaaS vendor. You are unable to add Netskope's IP ranges at this time, but need to
allow the traffic.
How would you allow this traffic?
- A. Use NPAto implement Source IP anchonng so the traffic will egress from the corporate data center.
- B. Use Explicit Proxy Over Tunnel (EPoT) so the traffic will egress from the corporate data center.
- C. Use Cloud Explicit Proxy so the traffic will egress from the corporate data center
- D. Use an IPsec tunnel to forward traffic so it will egress from the corporate data center
Answer:
C
Explanation:
To allow traffic to a financial SaaS application that is being blocked due to IP restrictions, the best
option is to use Cloud Explicit Proxy. This method allows traffic to egress from the corporate data
center without requiring Netskope’s IP ranges to be added to the SaaS vendor’s allowlist.
By
configuring an allowlist in the Cloud Explicit Proxy settings, you can add any source egress IP
addresses for your on-premises users, and Netskope will allow the traffic from the added user and IP
address without authenticating1
.
Reference: The process for configuring an allowlist in Cloud Explicit Proxy to manage
unauthenticated traffic from specific IP addresses is detailed in the Netskope Knowledge Portal1
. This
solution is suitable for scenarios where adding Netskope’s IP ranges to the SaaS vendor’s IP
restrictions is not feasible.
Question 3
Your company just had a new Netskope tenant provisioned and you are asked to create a secure
tenant configuration. In this scenario, which two default settings should you change? {Choose two.)
- A. Change Safe Search to Disabled
- B. Change Untrusted Root Certificate to Block.
- C. Change the No SNI setting to Block.
- D. Change "Disallow concurrent logins by an Admin" to Enabled.
Answer:
B, D
Explanation:
For a new Netskope tenant provisioned, to create a secure tenant configuration, you should
consider changing the following default settings:
B . Change Untrusted Root Certificate to Block: This setting will ensure that any traffic coming from
an untrusted root certificate is blocked, which is a critical security measure to prevent man-in-the-
middle attacks and other types of cyber threats1
.
D . Change “Disallow concurrent logins by an Admin” to Enabled: This setting will prevent multiple
concurrent logins by the same admin account, which is an important security control to mitigate the
risk of unauthorized access.
If an admin’s credentials are compromised, this setting will help limit the
potential damage by ensuring that only one session can be active at a time1
.
These changes are part of the recommended security hardening guidelines for Netskope tenants to
enhance the overall security posture of the tenant environment.
Reference: The recommendations for changing default settings for a secure tenant configuration are
based on Netskope’s security hardening guidelines, which provide detailed instructions on how to
enhance the security of Netskope products and components deployed in customer environments1
.
Question 4
You have an NG-SWG customer that currently steers all Web traffic to Netskope using the Netskope
Client. They have identified one new native application on Windows devices that is a certificate-
pinned application. Users are not able to access the application due to certificate pinning. The
customer wants to configure the Netskope Client so that the traffic from the application is steered to
Netskope and the application works as expected.
Which two methods would satisfy the requirements? (Choose two.)
- A. Bypass traffic using the bypass action in the Real-time Protection policy.
- B. Configure the SSL Do Not Decrypt policy to not decrypt traffic for domains used by the native application.
- C. Configure domain exceptions in the steering configuration for the domains used by the native application.
- D. Tunnel traffic to Netskope and bypass traffic inspection at the Netskope proxy.
Answer:
BC
Explanation:
To address the issue of a certificate-pinned application not being accessible due to certificate
pinning, while still steering the traffic to Netskope, the two methods that would satisfy the
requirements are:
B: Configure the SSL Do Not Decrypt policy to not decrypt traffic for domains used by the native
application. This ensures that the SSL traffic for the specified domains is not decrypted, thus avoiding
issues with certificate pinning.
C: Configure domain exceptions in the steering configuration for the domains used by the native
application.
By setting domain exceptions, traffic to these domains will bypass SSL decryption,
allowing the certificate-pinned application to function as expected1
.
These methods are in line with Netskope’s capabilities for handling certificate-pinned applications,
which often require bypassing decryption to prevent breaking the application’s functionality due to
its security features1
.
Reference: The Netskope Knowledge Portal provides detailed information on managing certificate-
pinned applications, including how to configure SSL Do Not Decrypt policies and domain exceptions
in the steering configuration1
.
Additionally, the Netskope Community Forum offers insights and best
practices for handling certificate-pinned applications2
.
Question 5
Your CISO asks that you to provide a report with a visual representation of the top 10 applications (by
number of objects) and their risk score. As the administrator, you decide to use a Sankey visualization
in Advanced Analytics to represent the data in an efficient manner.
In this scenario, which two field types are required to produce a Sankey Tile in your report? {Choose
two.)
- A. Dimension
- B. Measure
- C. Pivot Ranks
- D. Period of Type
Answer:
AB
Explanation:
To produce a Sankey Tile in a report that visually represents the top 10 applications by number of
objects and their risk score, you would need:
Dimension (A): This field type would be used to represent the nodes in the Sankey visualization,
which could be the applications in this case1
.
Measure (B): This field type would provide the weight of the links between the nodes, representing
the number of objects or the risk score associated with each application1
.
These two field types are essential for creating a Sankey visualization as they define the structure and
flow of data between different stages or categories within the visualization.
Reference: The requirements for creating a Sankey visualization are based on the general principles
of data visualization and the specific features of Sankey diagrams, which typically involve dimensions
and measures to represent the flow of data1
.
Question 6
You created a Real-time Protection policy that blocks all activities to non-corporate S3 buckets, but
determine that the policy is too restrictive. Specifically, users are complaining that normal websites
have stopped rendering properly.
How would you solve this problem?
- A. Create a Real-time Protection policy to allow the Browse activity to the Amazon S3 application.
- B. Create a Real-time Protection policy to allow the Browse activity to the Cloud Storage category
- C. Create a Real-time Protection policy to allow the Download activity to the Cloud Storage category
- D. Create a Real-time Protection policy to allow the Download activity to the Amazon S3 application
Answer:
B
Explanation:
To solve the problem of normal websites not rendering properly due to a Real-time Protection policy
that blocks all activities to non-corporate S3 buckets, the best solution is to create a Real-time
Protection policy to allow the Browse activity to the Cloud Storage category. This approach will
enable users to view content from various cloud storage services, including Amazon S3, without
allowing full access to non-corporate S3 buckets.
It’s a more granular and less restrictive policy that
allows necessary browsing activities while still maintaining control over the upload and download
activities to non-corporate buckets1
.
Reference: The Netskope Knowledge Portal provides information on how to configure Real-time
Protection policies, including how to set up policies that allow certain activities while blocking
others1
.
Additionally, the Netskope Community Forum offers insights into best practices for policy
configuration to avoid overly restrictive rules that can impact normal web browsing
Question 7
You want to verify that Google Drive is being tunneled to Netskope by looking in the nsdebuglog file.
You are using Chrome and the Netskope Client to steer traffic. In this scenario, what would you
expect to see in the log file?
A)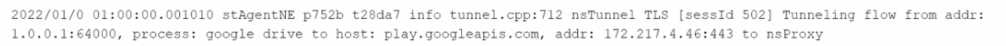
B)
C)
D)
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
A
Explanation:
When verifying that Google Drive traffic is being tunneled to Netskope using Chrome and the
Netskope Client, you would expect to see log entries indicating that the traffic is being directed
through Netskope’s proxy. Specifically, Option A is correct as it shows the process “google drive”
being tunneled to nsProxy. The log entry for Option A indicates that a TLS tunneling flow from a local
address and process (Google Drive) is being directed to a host (play.googleapis.com) and then to
Netskope’s proxy (nsProxy).
This is consistent with how Netskope tunnels specified traffic for security
and policy enforcement1
.
Reference: The expected log entries are based on the standard operation of Netskope Client and how
it steers traffic to Netskope’s cloud services, as detailed in Netskope’s documentation1
.
Question 8
Users in your network are attempting to reach a website that has a self-signed certificate using a GRE
tunnel to Netskope. They are currently being blocked by Netskope with an SSL error. How would you
allow this traffic?
- A. Configure a Do Not Decrypt SSL Decryption rule to allow traffic to pass.
- B. Configure a Real-time Protection policy with the action set to Allow.
- C. Set the No SNI setting in Netskope to Bypass.
- D. Ensure that the users add the self-signed certificate to their local certificate store.
Answer:
A
Explanation:
To allow traffic from a website with a self-signed certificate that is being blocked by Netskope with
an SSL error, the correct action is to configure a Do Not Decrypt SSL Decryption rule. This rule will
allow the traffic to pass without being decrypted, thus bypassing the SSL error caused by the self-
signed certificate.
This is a common practice for handling traffic from trusted internal applications or
specific external sites that use self-signed certificates1
.
Reference: The Netskope Community Forum discusses the application of exceptions for sites with
self-signed certificates and the use of SSL decryption policies to bypass the blocking1
.
Additionally,
the Netskope Knowledge Portal provides information on managing error settings and configuring SSL
decryption rules2
.
Question 9
A company needs to block access to their instance of Microsoft 365 from unmanaged devices. They
have configured Reverse Proxy and have also created a policy that blocks login activity for the AD
group "marketing-users" for the Reverse Proxy access method. During UAT testing, they notice that
access from unmanaged devices to Microsoft 365 is not blocked for marketing users.
What is causing this issue?
- A. There is a missing group name in the SAML response.
- B. The username in the name ID field is not in the format of the e-mail address.
- C. There is an invalid certificate in the SAML response.
- D. The username in the name ID field does not have the "marketing-users" group name.
Answer:
A
Explanation:
The issue is likely caused by a missing group name in the SAML response (A). When access to
Microsoft 365 from unmanaged devices is not blocked as expected, despite having a policy in place,
it often indicates that the SAML assertion is not correctly identifying the user as a member of the
restricted group. In this case, the “marketing-users” group name should be present in the SAML
response to enforce the policy that blocks login activity for this group. If the group name is missing,
the policy will not apply, and users will not be blocked as intended.
Reference: This explanation is consistent with the configuration requirements for access control using
SAML responses, as detailed in Netskope’s documentation on Reverse Proxy and SAML integration1
.
Question 10
A company wants to capture and maintain sensitive Pll data in a relational database to help their
customers. There are many employees and contractors that need access to sensitive customer data
to perform their duties The company wants to prevent the exfiltration of sensitive customer data by
their employees and contractors.
In this scenario. what would satisfy this requirement?
- A. fingerprinting
- B. exact data match
- C. regular expression
- D. machine learning
Answer:
A
Explanation:
Fingerprinting would satisfy the requirement to prevent the exfiltration of sensitive Personally
Identifiable Information (PII) data by employees and contractors. Fingerprinting is a data protection
technique that involves creating a unique digital representation of sensitive data. This allows for the
detection of any exact or partial matches of the fingerprinted data leaving the company’s
environment, thereby preventing unauthorized data exfiltration.
It is particularly effective in
scenarios where multiple individuals require access to sensitive data, as it can protect against both
inadvertent and malicious attempts to move data outside of authorized channels1
.
Reference: Netskope’s Data Loss Prevention (DLP) capabilities include fingerprinting as a method to
secure sensitive data consistently across the enterprise1
.
The Netskope Knowledge Portal provides
further information on how to enable and configure fingerprinting and other DLP settings to protect
sensitive PII data2
.
Question 11
You jus! deployed and registered an NPA publisher for your first private application and need to
provide access to this application for the Human Resources (HR) users group only. How would you
accomplish this task?
- A. 1. Enable private app steering in the Steering Configuration assigned to the HR group. 2. Create a new Private App. 3. Create a new Real-time Protection policy as follows; Source = HR user group Destination = Private App Action = Allow
- B. 1. Create a new private app and assign it to the HR user group. 2. Create a new Real-time Protection policy as follows: Source = HR user group Destination = Private App Action = Allow.
- C. 1. Enable private app steering in Tenant Steering Configuration. 2. Create a new private app and assign it to the HR user group.
- D. 1. Enable private app steering in the Steering Configuration assigned to the HR group. 2. Create a new private app and assign it to the HR user group 3. Create a new Real-time Protection policy as follows: Source = HR user group Destination = Private App Action = Allow
Answer:
D
Explanation:
To provide access to a private application for the Human Resources (HR) users group only after
deploying and registering an NPA publisher, you would need to:
Enable private app steering in the Steering Configuration assigned to the HR group: This ensures that
only traffic from the HR user group is steered towards the private application.
Create a new private app and assign it to the HR user group: This step involves defining the private
application within Netskope and specifying that only the HR user group should have access to it.
Create a new Real-time Protection policy as follows:
Source = HR user group: This specifies that the policy applies to the HR user group.
Destination = Private App: This defines the private application as the destination for the policy.
Action = Allow: This action allows the HR user group to access the private application.
By following these steps, you can ensure that only the HR user group has access to the private
application, aligning with the principles of least privilege and zero trust access control.
Reference: The process for providing access to a private application for a specific user group is
detailed in Netskope’s documentation on Private Access and Private App Management12
.
Question 12
Review the exhibit.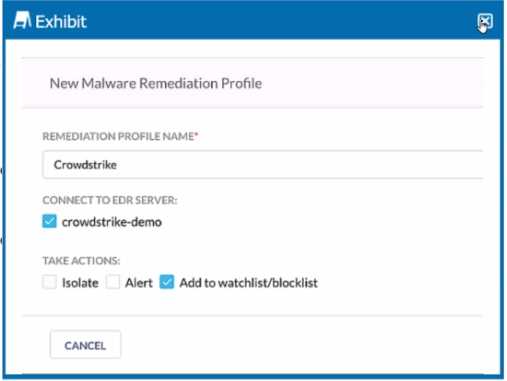
You are asked to integrate Netskope with Crowdstrike EDR. You added the Remediation profile
shown in the exhibit.
Which action will this remediation profile take?
- A. The endpoint will be isolated.
- B. The malware hash will be added as an IOC in Crowdstrike.
- C. The malware will be quarantined.
- D. The malware hash will be added as an IOC in Netskope.
Answer:
A
Explanation:
The remediation profile shown in the exhibit will take the action of isolating the endpoint. This is
indicated by the “Isolate” option being checked under “TAKE ACTIONS” in the configuration settings.
When this option is selected, the remediation profile is configured to isolate the endpoint upon
detection of a threat, which is a common response to contain a potential security breach and prevent
further spread of malware within the network1
.
Reference: The Netskope Knowledge Portal provides detailed information on integrating CrowdStrike
for EDR and the actions that can be taken by remediation profiles, including endpoint isolation1
.
Further details on the integration process and remediation actions can be found in the
documentation provided by Netskope23
.
Question 13
Your client is an NG-SWG customer. They are going to use the Explicit Proxy over Tunnel (EPoT)
steering method. They have a specific list of domains that they do not want to steer to the Netskope
Cloud.
What would accomplish this task''
- A. Define exception domains in the PAC file.
- B. Define exceptions in the Netskope steering configuration
- C. Create a real-time policy with a bypass action.
- D. Use an SSL decryption policy.
Answer:
A
Explanation:
To accomplish the task of not steering specific domains to the Netskope Cloud while using the
Explicit Proxy over Tunnel (EPoT) steering method, you would define exception domains in the PAC
file (A).
This is because the PAC file is used to specify which domains should bypass the proxy and
connect directly, thus allowing for granular control over the traffic that is steered to Netskope1
.
Reference: The use of PAC files for steering exceptions is a standard practice in proxy configurations
and is supported by Netskope’s EPoT steering method as outlined in their documentation1
.
Question 14
You are asked to ensure that a Web application your company uses is both reachable and decrypted
by Netskope. This application is served using HTTPS on port 6443. Netskope is configured with a
default Cloud Firewall configuration and the steering configuration is set for All Traffic.
Which statement is correct in this scenario?
- A. Create a Firewall App in Netskope along with the corresponding Real-time Protection policy to allow the traffic.
- B. Nothing is required since Netskope is steering all traffic.
- C. Enable "Steer non-standard ports" in the steering configuration and add the domain and port as a new non-standard port
- D. Enable "Steer non-standard ports" in the steering configuration and create a corresponding Real- time Protection policy to allow the traffic
Answer:
C
Explanation:
To ensure that the web application using HTTPS on port 6443 is both reachable and decrypted by
Netskope, the correct action is to enable “Steer non-standard ports” in the steering configuration and
add the domain and port as a new non-standard port. This is because Netskope’s default
configuration steers standard HTTP/HTTPS traffic, typically on ports 80 and 443.
Since port 6443 is a
non-standard port for HTTPS traffic, it requires explicit configuration to be steered through
Netskope1
.
Reference: The process for configuring non-standard ports in Netskope is detailed in the Netskope
Knowledge Portal, which provides step-by-step instructions on how to steer HTTP(S) traffic over non-
standard ports1
. This includes adding the specific non-standard port number in the steering
configuration to ensure that traffic to and from that port is properly handled by Netskope.
Question 15
You have enabled CASB traffic steering using the Netskope Client, but have not yet enabled a Real-
time Protection policy. What is the default behavior of the traffic in this scenario?
- A. Traffic will be blocked and logged.
- B. Traffic will be allowed and logged.
- C. Traffic will be blocked, but not logged.
- D. Traffic will be allowed, but not logged.
Answer:
B
Explanation:
In the scenario where CASB traffic steering is enabled using the Netskope Client without a Real-time
Protection policy being activated, the default behavior of the traffic is to allow and log it (B). This
means that the traffic will not be blocked; instead, it will be permitted to pass through and will be
recorded for monitoring and analysis purposes.
This default setting ensures visibility into the traffic
and user activities without immediately enforcing a block, allowing for a period of observation and
policy tuning before potentially more restrictive actions are taken1
.
Reference: The default behavior of traffic steering in Netskope, including the logging of allowed
traffic, is detailed in Netskope’s best practices and community discussions on Real-time Protection
policies1
.