netskope NSK200 Exam Questions
Questions for the NSK200 were updated on : Feb 20 ,2026
Page 1 out of 7. Viewing questions 1-15 out of 93
Question 1
Review the exhibit.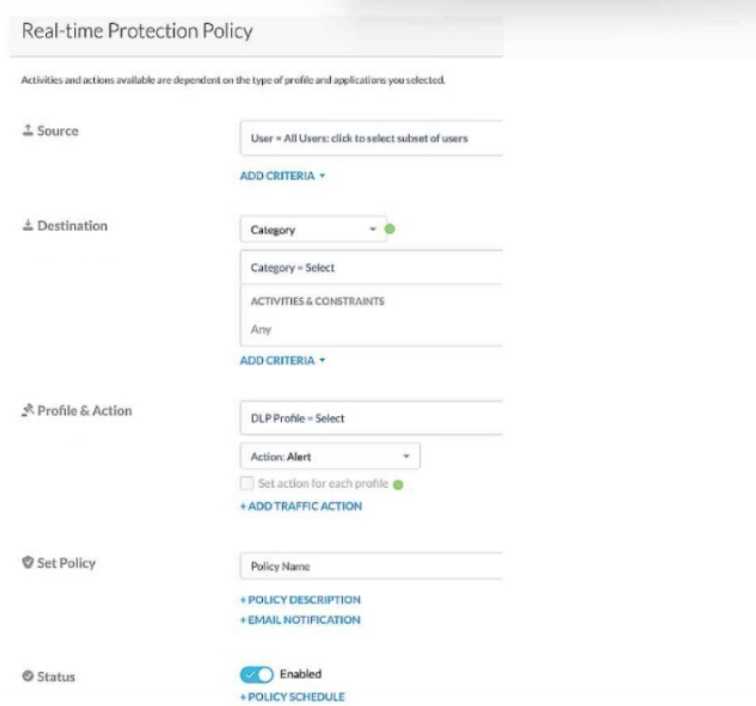
Given the information shown below:
-
for PCI data uploads, you want to provide no notification,
-
for PHI data uploads, you want to allow users to proceed by clicking OK,
-
for GDPR data uploads, you want to provide block notification,
-
if none of the above matches, you want to provide no notification.
You want to reduce the number of policies by combining multiple DLP profiles Into one policy.
Referring to the exhibit, which two statements are true? (Choose two.)
- A. You must open a support ticket to enable the Advanced Policies feature.
- B. You must check the "set action for each profile" flag.
- C. You can have only one action if you use multiple DLP profiles in the same policy.
- D. You can apply a unique action to each profile In the same policy.
Answer:
BD
Explanation:
To apply different actions for each DLP profile in the same policy, you need to enable the "set action
for each profile" flag. This allows you to configure unique actions (e.g., block, allow) for each DLP
profile within a single combined policy, thus reducing the total number of policies needed
Question 2
You are currently migrating users away from a legacy proxy to the Netskope client in the company’s
corporate offices. You have deployed the client to a pilot group; however, when the client attempts
to connect to Netskope, it fails to establish a tunnel.
In this scenario, what would cause this problem?
- A. The legacy proxy is intercepting SSL/TLS traffic to Netskope.
- B. The corporate firewall is blocking UDP port 443 to Netskope.
- C. The corporate firewall is blocking the Netskope EPoT address.
- D. The client cannot reach dns.google for EDNS resolution.
Answer:
B
Explanation:
The corporate firewall blocking UDP port 443 to Netskope could cause tunnel establishment failures.
Netskope clients rely on this port for secure tunneling (via DTLS), so ensuring UDP port 443 is open is
essential for connectivity. Additionally, legacy proxies intercepting traffic could also disrupt the
SSL/TLS traffic necessary for the Netskope tunnel .
Question 3
You are configuring GRE tunnels from a Palo Alto Networks firewall to a Netskope tenant with the
Netskope for Web license enabled. Your tunnel is up as seen from the Netskope dashboard. You are
unable to ping hosts behind the Netskope gateway.
Which two statements are true about this scenario? (Choose two.)
- A. You need to call support to enable the GRE POP selection feature.
- B. Netskope only supports Web traffic through the tunnel.
- C. You can only ping the probe IP provided by Netskope.
- D. There is no client installed on the source hosts in your network.
Answer:
BC
Explanation:
Netskope’s GRE tunneling supports only web traffic, which means ICMP traffic (ping) is not
supported for hosts behind the Netskope gateway. You may, however, ping the probe IP provided by
Netskope to test connectivity, as this IP is designated for diagnostics .
Question 4
You have created a specific Skope IT application events query and want to have the query
automatically run and display the results every time you log into your tenant.
Which two statements are correct in this scenario? (Choose two.)
- A. Add the Watchlist widget from the library to your home page.
- B. Export a custom Skope IT watchlist to a report and then schedule it to run daily.
- C. Save a custom Skope IT watchlist, then manage filters and share with others.
- D. Add your Skope IT query to a custom watchlist.
Answer:
CD
Explanation:
Adding a Skope IT query to a custom watchlist allows the query to be saved and easily accessed.
Saving the watchlist and managing filters also lets you customize it further and share it with others in
your organization if needed .
Question 5
You are an administrator writing Netskope Real-time Protection policies and must determine proper
policy ordering.
Which two statements are true in this scenario? (Choose two.)
- A. You must place DLP policies at the bottom.
- B. You do not need to create an "allow all" Web Access policy at the bottom.
- C. You must place Netskope private access malware policies in the middle.
- D. You must place high-risk block policies at the top.
Answer:
BD
Explanation:
Placing high-risk block policies at the top ensures that critical blocks are enforced first, protecting
against the most severe threats. Additionally, an "allow all" Web Access policy at the bottom is not
necessary, as policy defaults can handle remaining traffic not explicitly addressed by other rules .
Question 6
With Netskope DLP, which feature would be used to detect keywords such as "Confidential" or
"Access key"?
- A. Regular Expression
- B. Exact Match
- C. Fingerprint Classification
- D. Dictionary
Answer:
D
Explanation:
The Dictionary feature in Netskope DLP is designed to detect specific keywords or phrases, such as
"Confidential" or "Access key." By using a pre-defined list of sensitive terms, the Dictionary feature
enables policy enforcement based on the presence of these keywords in data .
Question 7
You want to provide malware protection for all cloud storage applications.
In this scenario, which action would accomplish this task?
- A. Create a real-time threat protection policy with a category of Cloud Storage.
- B. Apply a data protection profile.
- C. Apply a CTEP profile.
- D. Create an API threat protection policy with a category of Cloud Storage.
Answer:
A
Explanation:
Creating a real-time threat protection policy specifically targeting the "Cloud Storage" category
ensures that all supported cloud storage applications are covered by malware protection. This
approach allows real-time scanning and response to malware threats within cloud storage
environments .
Question 8
You use Netskope to provide a default Malware Scan profile for use with your malware policies. Also,
you want to create a custom malware detection profile.
In this scenario, what are two additional requirements to complete this task? (Choose two.)
- A. Add a custom hash list as an allowlist.
- B. Add a quarantine profile.
- C. Add a remediation profile.
- D. Add a custom hash list as a blocklist.
Answer:
BD
Explanation:
To create a custom malware detection profile, adding a quarantine profile ensures that detected
threats are appropriately isolated. Additionally, a custom hash list as a blocklist allows you to block
specific known malware hashes, further enhancing the customization of the malware detection
profile .
Question 9
Review the exhibit.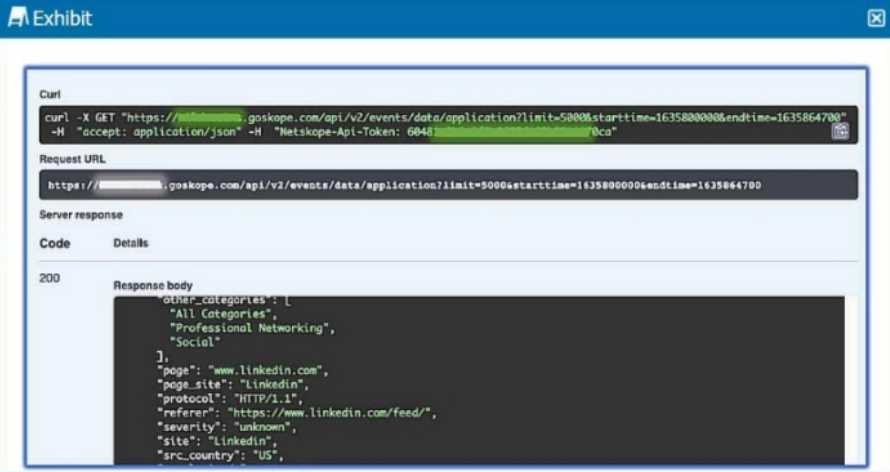
Referring to the exhibit, which three statements are correct? (Choose three.)
- A. The request was processed successfully.
- B. A request was submitted to extract application event details.
- C. An invalid token was used.
- D. The request was limited to the first 5000 records.
- E. The request was confined to only the "Professional Networking and Social" category.
Answer:
ABD
Explanation:
The "200" response code confirms that the request was processed successfully. The request URL
indicates that it was set to retrieve application event data with a limit of 5000 records. Additionally,
the response includes categories such as "Professional Networking and Social," verifying that these
were part of the requested data .
Question 10
A company allows their users to access OneDrive on their managed laptops. It is against corporate
policy to upload any documents to their personal OneDrive. The company needs to enforce this
policy to protect their customer’s sensitive data.
What are two ways to enforce this policy? (Choose two.)
- A. Create DLP policies to block the upload of all the identified documents.
- B. Create DLP policies to allow document uploading only to the corporate OneDrive instance.
- C. Create a new application instance for the corporate OneDrive.
- D. Fingerprint all the documents to have a catalog of all the documents that the company needs to protect.
Answer:
AB
Explanation:
By setting DLP policies that either block uploads of sensitive documents or restrict them to only the
corporate OneDrive, the company can enforce its policy. These policies ensure that sensitive data
remains within approved environments and does not get uploaded to personal instances .
Question 11
You want to prevent a document stored in Google Drive from being shared externally with a public
link.
- A. Quarantine
- B. Threat Protection policy
- C. API Data Protection policy
- D. Real-time Protection policy
Answer:
C
Explanation:
An API Data Protection policy is appropriate for controlling document sharing permissions in Google
Drive. This policy type can enforce restrictions on file sharing, such as preventing public links, which
ensures data protection within cloud storage applications .
Question 12
Your company has many users that are remote and travel often. You want to provide the greatest
visibility into their activities, even while traveling.
Using Netskope, which deployment method would be used in this scenario?
- A. Use a Netskope client.
- B. Use an IPsec tunnel.
- C. Use a GRE tunnel.
- D. Use proxy chaining.
Answer:
A
Explanation:
Deploying the Netskope client on remote and traveling users' devices provides the highest level of
visibility into their activities regardless of their location. The Netskope client can steer traffic securely
to the Netskope Security Cloud, offering consistent monitoring and protection .
Question 13
Your customer is using a virtual desktop infrastructure (VDI) for their support engineers. Multiple
users will be logging into the same device, and they want to detect activities for each user.
- A. Install Netskope client in default mode and enable DTLS.
- B. Install Netskope client and create a separate steering configuration for each user.
- C. Install Netskope client in peruserconfig mode.
- D. Install Netskope client and create a separate device configuration for each user.
Answer:
C
Explanation:
Installing the Netskope client in "peruserconfig" mode allows for user-specific configurations on
shared devices like those in a VDI environment. This mode enables Netskope to detect and report
activities separately for each user, even if multiple users are logged into the same device .
Question 14
Your company asks you to use Netskope to integrate with Endpoint Detection and Response (EDR)
vendors such as Crowdstrike.
Which two requirements are needed for a successful integration and sharing of threat data? (Choose
two.)
- A. Remediation profile
- B. Device classification
- C. API Client ID
- D. Custom log parser
Answer:
AC
Explanation:
Integrating with EDR vendors like Crowdstrike requires an API Client ID for authentication and data
sharing. A remediation profile is also necessary to define automated actions that can be taken when
threats are detected, ensuring effective response to endpoint threats .
Question 15
Review the exhibit.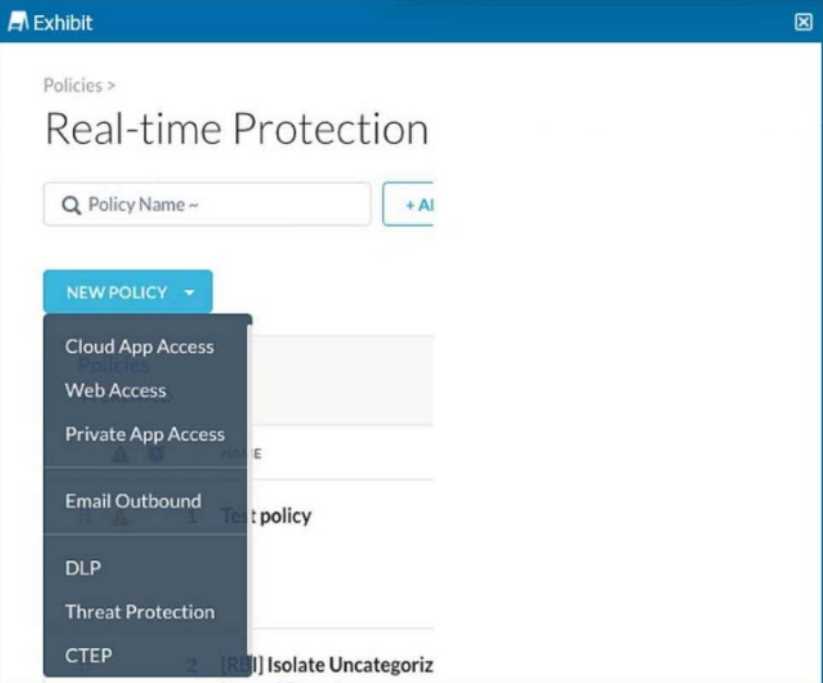
You are asked to create a new Real-time Protection policy to scan SMTP emails using data loss
prevention (DLP) for personal health information (PHI). The scope is limited to only emails being sent
from Microsoft Exchange Online to outside recipients.
- A. Web Access policy
- B. Email Outbound policy
- C. CTEP policy
- D. DLP policy
Answer:
B
Explanation:
An "Email Outbound" policy is specifically designed to apply data loss prevention controls on
outbound emails, such as SMTP traffic from Exchange Online. This policy type enables granular
control over outbound email content, ensuring compliance with DLP policies for PHI data .