netskope NSK101 Exam Questions
Questions for the NSK101 were updated on : Feb 20 ,2026
Page 1 out of 9. Viewing questions 1-15 out of 129
Question 1
A company user cannot open a sports news site. You want to review the category of the website and
see how the rules are applied even though this category is allowed. In this scenario, which action will
accomplish this task?
- A. Use the Forensic profile
- B. Use www.netskope.com/url-lookup.
- C. Use the URL Lookup page in the dashboard.
- D. Verify with your own computer and use Advanced Debugging.
Answer:
C
Explanation:
To review the category of a website and understand how the rules are applied, the following action
can be taken:
Use the URL Lookup page in the dashboard: The URL Lookup page in the Netskope dashboard allows
administrators to enter a URL and view its categorization. This tool provides information on how the
website is classified and which policies apply to it. It helps in troubleshooting why a user might be
unable to access a specific site, even if the category is generally allowed.
Reference:
Netskope documentation on using the URL Lookup tool to review website categories and policy
applications.
Guidelines for troubleshooting web access issues using the Netskope dashboard tools.
Question 2
When comparing data in motion with data at rest, which statement is correct?
- A. Data at rest cannot be scanned for malware until a user opens the file.
- B. Data in motion requires API integration.
- C. Data in motion requires the Netskope client.
- D. Data at rest requires API integration.
Answer:
CD
Explanation:
When comparing data in motion with data at rest, the following statements are correct:
Data in motion requires the Netskope client: To inspect and enforce policies on data as it is being
transmitted across the network (data in motion), the Netskope client is required. The client steers the
traffic through the Netskope cloud where it is analyzed and policies are applied in real-time.
Data at rest requires API integration: To scan and enforce policies on data stored in cloud applications
(data at rest), API integration is required. This allows Netskope to directly interact with cloud services
and perform actions such as scanning for malware, applying DLP policies, and ensuring compliance.
Reference:
Netskope documentation on data protection strategies, including data in motion and data at rest.
Best practices for implementing API integrations for data at rest and using the Netskope client for
data in motion.
Question 3
An administrator wants to determine to which data plane a user is traversing. In this scenario, what
are two ways to accomplish this task? (Choose two.)
- A. Settings -> Security Cloud Platform -> Devices
- B. Settings -> Security Cloud Platform -> Client Configuration
- C. SkopeIT -> Alerts -> View Details
- D. System Tray -> Configuration
Answer:
BC
Explanation:
To determine which data plane a user is traversing, an administrator can use the following methods:
Settings -> Security Cloud Platform -> Client Configuration: This section provides details about the
client configurations and the data planes assigned to different users or groups. By reviewing the
client configuration, administrators can determine the data plane a user is connected to.
SkopeIT -> Alerts -> View Details: In the SkopeIT alerts, administrators can view detailed information
about user activities, including the data plane through which the user traffic is being routed. This
provides real-time insights into the user's path through the Netskope infrastructure.
Reference:
Netskope documentation on configuring and managing the Security Cloud Platform and client
configurations.
Guides on using SkopeIT to monitor user activities and view detailed alert information.
Question 4
What are two valid use cases for the Cloud Confidence Index (CCI)? (Choose two.)
- A. To recategorize cloud applications in the database
- B. To delete cloud applications from the database
- C. To identify the activities that Netskope supports for cloud applications
- D. To compare similar cloud applications
Answer:
CD
Explanation:
The Cloud Confidence Index (CCI) has several use cases, including:
To identify the activities that Netskope supports for cloud applications: The CCI helps administrators
understand which activities are supported and monitored by Netskope for various cloud applications.
This includes knowing the types of data that can be protected and the actions that can be controlled
within those applications.
To compare similar cloud applications: The CCI provides a comparative assessment of cloud
applications based on their security and compliance postures. This allows organizations to make
informed decisions about which applications to approve or restrict based on their confidence levels.
These use cases help organizations enhance their security posture by using the CCI to guide
application usage policies and ensure compliance with internal standards.
Reference:
Netskope documentation on Cloud Confidence Index and its applications in policy creation and
management.
Guides on using CCI to assess and compare cloud applications for better security and compliance.
Question 5
You are required to provide an additional pop-up warning to users before allowing them to proceed
to Web applications categorized as "low" or "poor" by Netskope's Cloud Confidence Index. Which
action would allow you to accomplish this task?
- A. Enable RBI on the uncategorized domains
- B. Create a policy limiting usage of generative AI.
- C. Redirect the user to the company banner page for the Web usage policy.
- D. Enable real-time user coaching based on CCL.
Answer:
D
Explanation:
To provide an additional pop-up warning to users before allowing them to proceed to web
applications categorized as "low" or "poor" by Netskope's Cloud Confidence Index (CCI), you can:
Enable real-time user coaching based on CCL: This feature allows administrators to create policies
that provide real-time guidance and warnings to users when they attempt to access web applications
with low or poor confidence levels. This helps in educating users about the potential risks and
ensures that they proceed with caution.
Reference:
Netskope documentation on configuring real-time user coaching and leveraging the Cloud
Confidence Index for policy enforcement.
Best practices for using CCL to guide user behavior and enhance security awareness.
Question 6
Which three status indicators does the NPA Troubleshooter Tool provide when run? (Choose three)
- A. Steering configuration
- B. Client configuration timestamp
- C. Publisher connectivity
- D. Client version
- E. Reachability of the private app
Answer:
ACE
Explanation:
The NPA (Netskope Private Access) Troubleshooter Tool provides the following status indicators when
run:
Steering configuration: This indicates whether the traffic is being correctly steered through the
Netskope infrastructure according to the defined policies.
Publisher connectivity: This status shows whether the Netskope Publisher is correctly connected and
able to communicate with the Netskope cloud. It ensures that the Publisher, which acts as a gateway,
is functioning correctly.
Reachability of the private app: This status verifies if the private application is reachable from the
Netskope infrastructure, ensuring that users can access the necessary internal resources.
These indicators help administrators troubleshoot and ensure that the NPA setup is working
correctly, providing secure and reliable access to private applications.
Reference:
Netskope documentation on using the NPA Troubleshooter Tool and the status indicators it provides.
Best practices for troubleshooting NPA connectivity and performance issues.
Question 7
When designing an architecture with Netskope Private Access, which element guarantees
connectivity between the Netskope cloud and the private application?
- A. Netskope Publisher
- B. API connector
- C. Third-party router with GRE/IPsec support
- D. Netskope Client
Answer:
A
Explanation:
When designing an architecture with Netskope Private Access, the Netskope Publisher is the element
that guarantees connectivity between the Netskope cloud and the private application. The Publisher
acts as a gateway, securely connecting users to private applications hosted on-premises or in data
centers.
Netskope Publisher: This component facilitates secure access to private applications by connecting
the Netskope cloud with the internal network. It ensures that users can access private applications
seamlessly while maintaining security and compliance.
Reference:
Netskope documentation on Private Access and the role of the Publisher.
Best practices for configuring and deploying Netskope Publisher to ensure secure connectivity to
private applications.
Question 8
API-enabled Protection traffic is sent to which Netskope component?
- A. Netskope Publisher
- B. Netskope Management Plane
- C. Netskope Data Plane
- D. Netskope Reverse Proxy
Answer:
C
Explanation:
API-enabled Protection traffic is sent to the Netskope Data Plane. The Netskope Data Plane is
responsible for processing and inspecting data in real-time, applying security policies, and ensuring
that the traffic conforms to organizational policies.
Netskope Data Plane: This component handles the inline inspection and enforcement of security
policies, including API-enabled protection. It ensures that all traffic is securely processed and
monitored according to the defined policies.
Reference:
Netskope architecture documentation describing the roles of different components.
Detailed guides on how API-enabled protection integrates with the Netskope Data Plane for real-
time traffic inspection.
Question 9
A user has performed a bulk delete activity. In this scenario, which Netskope feature monitors
potential risky users for a malicious activity that would cause data loss?
- A. Netskope's Threat Protection inline policies
- B. Netskope's Behavior Analytics rule-based policies
- C. Netskope's API Data Protection policies
- D. Netskope's Cloud Threat Exchange integration
Answer:
B
Explanation:
Netskope's Behavior Analytics rule-based policies are designed to monitor user behavior for patterns
that may indicate risky or malicious activities, such as bulk deletions. These policies can identify
anomalies in user behavior that deviate from the norm, flagging potential threats and taking
appropriate actions to prevent data loss.
Netskope's Behavior Analytics rule-based policies: This feature analyzes user actions and behaviors
to detect anomalies and potentially malicious activities. It helps in identifying and mitigating risks
associated with compromised accounts, insider threats, and other suspicious activities.
Reference:
Netskope documentation on Behavior Analytics and its capabilities.
Security best practices for detecting and responding to insider threats and anomalous user behavior.
Question 10
Which Netskope component would an administrator use to see an overview of private application
usage and performance?
- A. Digital Experience Management
- B. Publishers page
- C. Incident Management
- D. Cloud Exchange
Answer:
A
Explanation:
An administrator would use the Digital Experience Management (DEM) component to see an
overview of private application usage and performance. DEM provides comprehensive insights into
the performance and user experience of private applications, including metrics on latency,
bandwidth, and application health.
Digital Experience Management (DEM): This component focuses on monitoring and optimizing the
user experience for private and public applications by collecting detailed performance data and
providing actionable insights.
The other options do not provide the same level of detailed performance and usage overview for
private applications:
Publishers page: Typically used for managing and configuring Netskope Publishers.
Incident Management: Focuses on tracking and resolving security incidents.
Cloud Exchange: Deals with integrations and data sharing between Netskope and other security
solutions.
Reference:
Netskope documentation on Digital Experience Management and its capabilities.
Best practices for using DEM to monitor application performance and enhance user experience.
Question 11
Digital Experience Management (DEM) allows an administrator to monitor which two areas? (Choose
two.)
- A. User activities
- B. Bandwidth consumption
- C. Information on triggered policies
- D. Client steering data
Answer:
BD
Explanation:
Digital Experience Management (DEM) in Netskope allows administrators to monitor the following
areas:
Bandwidth consumption: DEM provides insights into how much bandwidth is being used by different
applications and services, helping administrators to optimize network performance and ensure
efficient use of resources.
Client steering data: DEM collects data on how traffic is being steered through the Netskope
infrastructure, including details about routing decisions, performance metrics, and user experiences.
This helps administrators understand the impact of their steering policies and make adjustments to
improve performance.
User activities (option A) and information on triggered policies (option C) are more directly related to
other features such as activity logs and policy enforcement dashboards rather than DEM.
Reference:
Netskope documentation on Digital Experience Management.
Guides on monitoring and optimizing network performance using DEM.
Question 12
As an administrator, you are investigating an increase in the number of incidents related to
compromised credentials. You are using the Netskope Compromised Credentials feature on your
tenant to assess the situation. Which insights would you find when using this feature? (Choose two)
- A. Compromised usernames
- B. Breach information source
- C. Compromised passwords
- D. Affected managed applications
Answer:
AB
Explanation:
When using the Netskope Compromised Credentials feature, administrators can gain valuable
insights into security incidents related to compromised credentials. The insights provided by this
feature include:
Compromised usernames: This information helps identify which user accounts have been
compromised, allowing administrators to take necessary actions such as resetting passwords and
notifying affected users.
Breach information source: Netskope provides details on the source of the breach, such as which
third-party service or data breach resulted in the compromise of credentials. This helps in
understanding the context of the breach and implementing measures to prevent future incidents.
While compromised passwords (option C) are indirectly involved, they are not explicitly listed as an
insight provided by this feature. Similarly, affected managed applications (option D) are related but
not directly part of the primary insights.
Reference:
Netskope documentation on Compromised Credentials feature and incident response.
Security best practices for managing and mitigating compromised credential incidents.
Question 13
Your customer asks you to secure all Web traffic as part of the initial configuration. In the Netskope
platform, which statement is correct in this scenario?
- A. Add the all Web traffic option to the steering configuration.
- B. Netskope automatically steers all Web traffic.
- C. Netskope cannot steer Web traffic.
- D. Select all Web traffic in the SSL decryption section.
Answer:
A
Explanation:
To secure all web traffic as part of the initial configuration in the Netskope platform, you need to:
Add the all Web traffic option to the steering configuration: This ensures that all web traffic is routed
through Netskope for inspection and policy enforcement. By steering all web traffic, you enable
Netskope to apply security measures, such as SSL decryption, threat protection, and DLP, to all HTTP
and HTTPS traffic.
Netskope does not automatically steer all web traffic by default; it requires configuration in the
steering policies. Selecting all web traffic in the SSL decryption section only pertains to decrypting
traffic, not the actual steering of the traffic.
Reference:
Netskope documentation on configuring steering settings and policies.
Guidelines for setting up web traffic steering and SSL decryption in the Netskope platform.
Question 14
You are asked to review files affected by malware in your organization. In this scenario, which two
actions are possible and would be accessible from the Netskope UI -> Incidents --> Malware?
(Choose two)
- A. Download the original malware file generating the alert to be analyzed by the SOC team
- B. Identify the exposure of the file identified as malware.
- C. Remediate the compromised devices.
- D. Determine the Detection Engine used to identify the malware.
Answer:
BD
Explanation:
When reviewing files affected by malware in the Netskope UI under Incidents -> Malware, you have
the following options:
Identify the exposure of the file identified as malware: This allows you to see where the malware has
spread within the organization, which users or systems are affected, and any potential data exposure
resulting from the malware.
Determine the Detection Engine used to identify the malware: Netskope provides details on which
detection engine (such as AV, sandboxing, or other heuristic engines) identified the malware. This
helps in understanding the threat vector and the reliability of the detection.
Downloading the original malware file (option A) is generally not recommended for security reasons
and may not be supported directly from the Netskope UI. Remediation of compromised devices
(option C) would typically be handled through endpoint security solutions rather than directly from
the Netskope UI.
Reference:
Netskope documentation on malware detection and incident response.
Best practices for handling malware incidents and using the Netskope UI for threat analysis.
Question 15
Click the Exhibit button.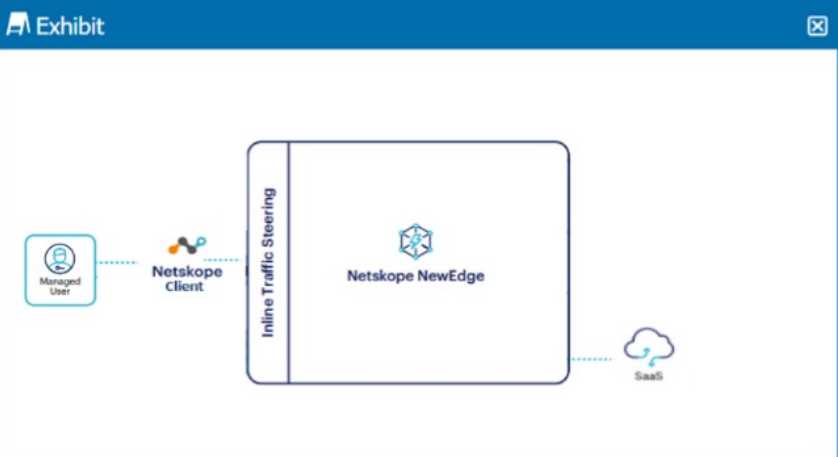
A user is connected to a SaaS application through Netskope's Next Gen SWG with SSL inspection
enabled. In this scenario, what information is available in SkopeIT? (Choose three.)
- A. User activity, CCL
- B. Destination IP, OS patch version
- C. Account instance, category
- D. Username, source location
- E. File version, shared folder
Answer:
ACD
Explanation:
In the scenario where a user is connected to a SaaS application through Netskope's Next Gen Secure
Web Gateway (SWG) with SSL inspection enabled, the following information is available in SkopeIT:
User activity, CCL: SkopeIT provides detailed logs of user activities, including actions taken within
SaaS applications, and uses the Cloud Confidence Level (CCL) to rate the trustworthiness of cloud
applications.
Account instance, category: It logs information about the specific instance of the account being
accessed and categorizes the type of service or application in use, which helps in identifying the
context of the user’s activities.
Username, source location: The username of the user accessing the SaaS application and their source
location (such as IP address or geographic location) are logged for audit and compliance purposes.
Reference:
Netskope documentation on SSL inspection and SkopeIT logging.
Detailed configuration guides on using Next Gen SWG and the types of data collected by SkopeIT.