microsoft AZ-305 Exam Questions
Questions for the AZ-305 were updated on : Jul 09 ,2025
Page 1 out of 26. Viewing questions 1-10 out of 252
Question 1
You are designing a microservices architecture that will be hosted in an Azure Kubernetes Service (AKS) cluster. Apps that will consume the microservices will be hosted on Azure virtual machines. The virtual machines and the AKS cluster will reside on the same virtual network.
You need to design a solution to expose the microservices to the consumer apps. The solution must meet the following requirements:
Ingress access to the microservices must be restricted to a single private IP address and protected by using mutual TLS authentication.
The number of incoming microservice calls must be rate-limited.
Costs must be minimized.
What should you include in the solution?
- A. Azure App Gateway with Azure Web Application Firewall (WAF)
- B. Azure API Management Standard tier with a service endpoint
- C. Azure Front Door with Azure Web Application Firewall (WAF)
- D. Azure API Management Premium tier with virtual network connection
Answer:
d
One option is to deploy APIM (API Management) inside the cluster VNet.
The AKS cluster and the applications that consume the microservices might reside within the same VNet, hence there is no reason to expose the cluster publicly as all API traffic will remain within the VNet. For these scenarios, you can deploy API Management into the cluster VNet. API Management Premium tier supports
VNet deployment.
Reference:
https://docs.microsoft.com/en-us/azure/api-management/api-management-kubernetes
Question 2
You are designing an order processing system in Azure that will contain the Azure resources shown in the following table.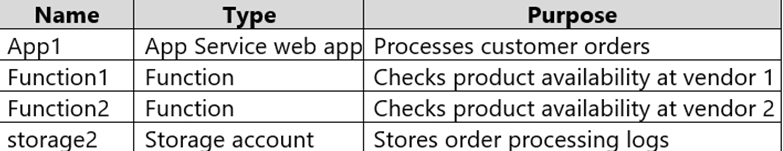
The order processing system will have the following transaction flow:
A customer will place an order by using App1.
When the order is received, App1 will generate a message to check for product availability at vendor 1 and vendor 2.
An integration component will process the message, and then trigger either Function1 or Function2 depending on the type of order.
Once a vendor confirms the product availability, a status message for App1 will be generated by Function1 or Function2.
All the steps of the transaction will be logged to storage1.
Which type of resource should you recommend for the integration component?
- A. an Azure Service Bus queue
- B. an Azure Data Factory pipeline
- C. an Azure Event Grid domain
- D. an Azure Event Hubs capture
Answer:
b
Azure Data Factory is the platform is the cloud-based ETL and data integration service that allows you to create data-driven workflows for orchestrating data movement and transforming data at scale. Using Azure Data Factory, you can create and schedule data-driven workflows (called pipelines) that can ingest data from disparate data stores.
Data Factory contains a series of interconnected systems that provide a complete end-to-end platform for data engineers.
Reference:
https://docs.microsoft.com/en-us/azure/data-factory/introduction
Question 3
You have an on-premises application that consumes data from multiple databases. The application code references database tables by using a combination of the server, database, and table name.
You need to migrate the application data to Azure.
To which two services can you migrate the application data to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. SQL Server Stretch Database
- B. SQL Server on an Azure virtual machine
- C. Azure SQL Database
- D. Azure SQL Managed Instance
Answer:
bd
Cross-database queries are supported by SQL Server, for example on an Azure virtual machine, and also supported by an Azure SQL Managed Instance.
Reference:
https://techcommunity.microsoft.com/t5/azure-database-support-blog/cross-database-queries-between-azure-sql-database-and-managed/ba- p/2706670
Question 4
You have an Azure subscription that contains a custom application named Application1. Application1 was developed by an external company named Fabrikam,
Ltd. Developers at Fabrikam were assigned role-based access control (RBAC) permissions to the Application1 components. All users are licensed for the
Microsoft 365 E5 plan.
You need to recommend a solution to verify whether the Fabrikam developers still require permissions to Application1. The solution must meet the following requirements:
To the manager of the developers, send a monthly email message that lists the access permissions to Application1.
If the manager does not verify an access permission, automatically revoke that permission.
Minimize development effort.
What should you recommend?
- A. In Azure Active Directory (Azure AD), create an access review of Application1.
- B. Create an Azure Automation runbook that runs the Get-AzRoleAssignment cmdlet.
- C. In Azure Active Directory (Azure AD) Privileged Identity Management, create a custom role assignment for the Application1 resources.
- D. Create an Azure Automation runbook that runs the Get-AzureADUserAppRoleAssignment cmdlet.
Answer:
a
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/governance/manage-user-access-with-access-reviews
Question 5
You have the resources shown in the following table.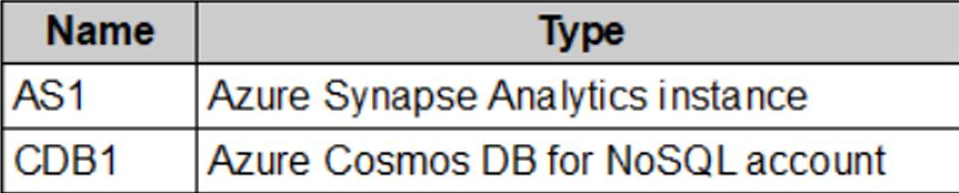
CDB1 hosts a container that stores continuously updated operational data.
You are designing a solution that will use AS1 to analyze the operational data daily.
You need to recommend a solution to analyze the data without affecting the performance of the operational data store.
What should you include in the recommendation?
- A. Azure Data Factory with Azure Cosmos DB and Azure Synapse Analytics connectors
- B. Azure Synapse Analytics with PolyBase data loading
- C. Azure Synapse Link for Azure Cosmos DB
- D. Azure Cosmos DB change feed
Answer:
c
Question 6
You are developing a sales application that will contain several Azure cloud services and handle different components of a transaction. Different cloud services will process customer orders, billing, payment, inventory, and shipping.
You need to recommend a solution to enable the cloud services to asynchronously communicate transaction information by using XML messages.
What should you include in the recommendation?
- A. Azure Application Gateway
- B. Azure Queue Storage
- C. Azure Data Lake
- D. Azure Traffic Manager
Answer:
b
Question 7
HOTSPOT You plan to deploy an Azure web app named App1 that will use Azure Active Directory (Azure AD) authentication.
App1 will be accessed from the internet by the users at your company. All the users have computers that run Windows 10 and are joined to Azure AD.
You need to recommend a solution to ensure that the users can connect to App1 without being prompted for authentication and can access App1 only from company-owned computers.
What should you recommend for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: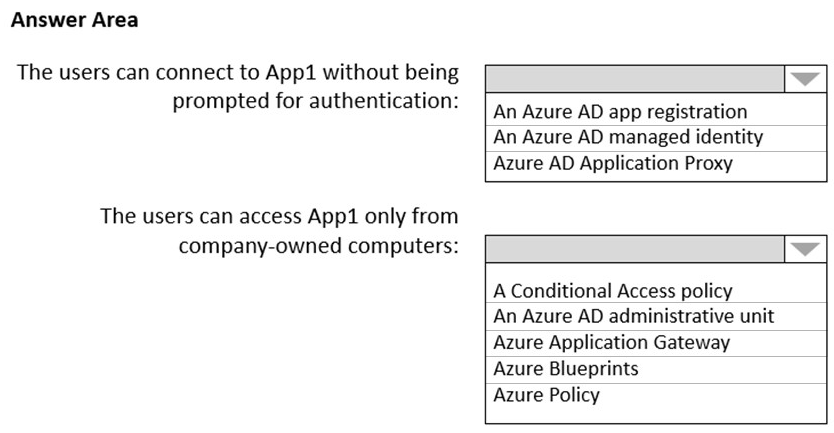
Answer:
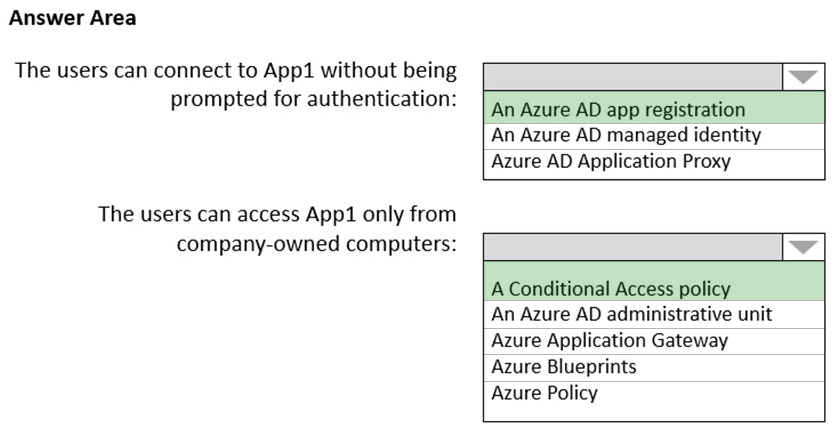
Box 1: An Azure AD app registration
Azure active directory (AD) provides cloud based directory and identity management services.You can use azure AD to manage users of your application and authenticate access to your applications using azure active directory.
You register your application with Azure active directory tenant.
Box 2: A conditional access policy
Conditional Access policies at their simplest are if-then statements, if a user wants to access a resource, then they must complete an action.
By using Conditional Access policies, you can apply the right access controls when needed to keep your organization secure and stay out of your user's way when not needed.
Reference:
https://codingcanvas.com/using-azure-active-directory-authentication-in-your-web-application/ https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
Question 8
Your company has the divisions shown in the following table.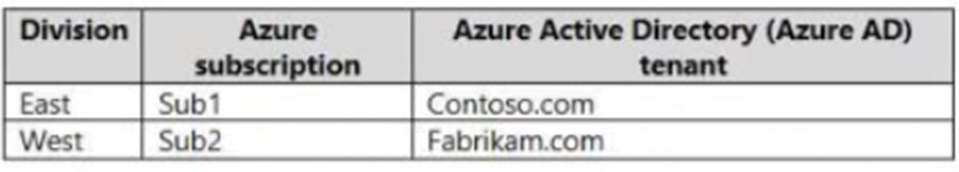
Sub1 contains an Azure App Service web app named App1. App1 uses Azure AD for single-tenant user authentication. Users from contoso.com can authenticate to App1.
You need to recommend a solution to enable users in the fabrikam.com tenant to authenticate to App1.
What should you recommend?
- A. Configure the Azure AD provisioning service.
- B. Configure assignments for the fabrikam.com users by using Azure AD Privileged Identity Management (PIM).
- C. Use Azure AD entitlement management to govern external users.
- D. Configure Azure AD Identity Protection.
Answer:
c
Entitlement management is an identity governance capability that enables organizations to manage identity and access lifecycle at scale by automating access request workflows, access assignments, reviews, and expiration. Entitlement management allows delegated non-admins to create access packages that external users from other organizations can request access to. One and multi-stage approval workflows can be configured to evaluate requests, and provision users for time-limited access with recurring reviews. Entitlement management enables policy-based provisioning and deprovisioning of external accounts.
Note: Access Packages -
An access package is the foundation of entitlement management. Access packages are groupings of policy-governed resources a user needs to collaborate on a project or do other tasks. For example, an access package might include: access to specific SharePoint sites. enterprise applications including your custom in-house and SaaS apps like Salesforce.
Microsoft Teams.
Microsoft 365 Groups.
Incorrect:
Not A: Automatic provisioning refers to creating user identities and roles in the cloud applications that users need access to. In addition to creating user identities, automatic provisioning includes the maintenance and removal of user identities as status or roles change.
Not B: Privileged Identity Management provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources that you care about. Here are some of the key features of Privileged Identity Management:
Provide just-in-time privileged access to Azure AD and Azure resources
Assign time-bound access to resources using start and end dates
Etc.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/6-secure-access-entitlement-managment https://docs.microsoft.com/en-us/azure/active-directory/app-provisioning/how-provisioning-works https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
Question 9
You need to recommend an Azure Storage solution that meets the following requirements:
The storage must support 1 PB of data.
The data must be stored in blob storage.
The storage must support three levels of subfolders.
The storage must support access control lists (ACLs).
What should you include in the recommendation?
- A. a premium storage account that is configured for block blobs
- B. a general purpose v2 storage account that has hierarchical namespace enabled
- C. a premium storage account that is configured for page blobs
- D. a premium storage account that is configured for file shares and supports large file shares
Answer:
b
Default limits for Azure general-purpose v2 (GPv2), general-purpose v1 (GPv1), and Blob storage accounts include:
* Default maximum storage account capacity: 5 PiB
Blob storage supports Azure Data Lake Storage Gen2, Microsoft's enterprise big data analytics solution for the cloud. Azure Data Lake Storage Gen2 offers a hierarchical file system as well as the advantages of Blob storage.
Blob storage supports Azure Data Lake Storage Gen2, Microsoft's enterprise big data analytics solution for the cloud. Azure Data Lake Storage Gen2 offers a hierarchical file system as well as the advantages of Blob storage
Incorrect:
Not D: In a Premium FileStorage account, storage size is limited to 100 TB.
Reference:
https://docs.microsoft.com/en-us/azure/storage/blobs/storage-blobs-introduction https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/azure-subscription-service-limits#storage-limits
Question 10
You need to implement the Azure RBAC role assignments for the Network Contributor role. The solution must meet the authentication and authorization requirements.
What is the minimum number of assignments that you must use?
- A. 1
- B. 2
- C. 5
- D. 10
- E. 15
Answer:
a
Scenario: The Network Contributor built-in RBAC role must be used to grant permissions to the network administrators for all the virtual networks in all the Azure subscriptions.
RBAC roles must be applied at the highest level possible.