microsoft AZ-304 Exam Questions
Questions for the AZ-304 were updated on : Jul 20 ,2024
Page 1 out of 17. Viewing questions 1-15 out of 247
Question 1 Topic 1, Case Study 1Case Study Question View Case
HOTSPOT
You plan to migrate App1 to Azure.
You need to recommend a storage solution for App1 that meets the security and compliance requirements.
Which type of storage should you recommend, and how should you recommend configuring the storage? To answer, select
the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: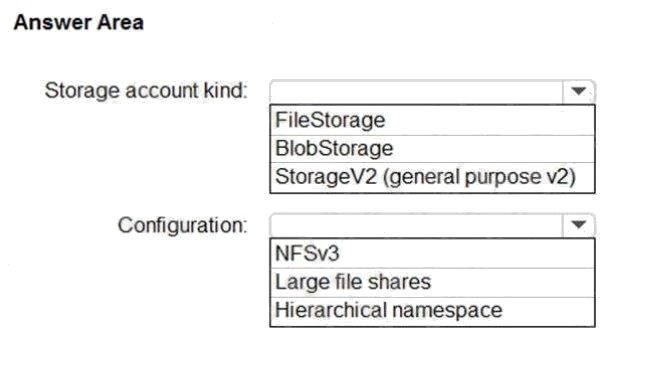
Answer:
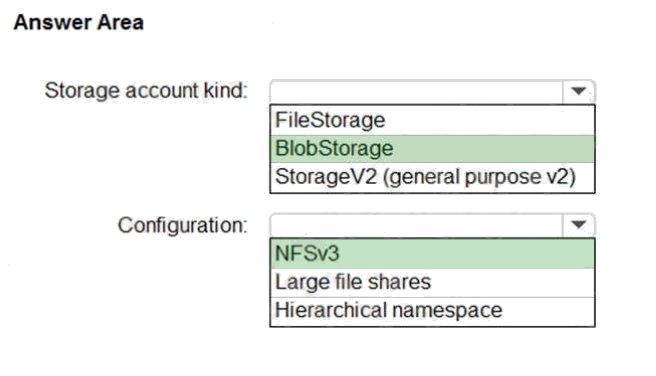
Explanation:
Box 1: BlobStorage
BlobStorage supports NFSv3, see below.
Box 2: NFSv3
Blob storage now supports the Network File System (NFS) 3.0 protocol. This support provides Linux file system compatibility
at object storage scale and prices and enables Linux clients to mount a container in Blob storage from an Azure Virtual
Machine (VM) or a computer on-premises.
Scenario: Litware identifies the following security and compliance requirements:
On-premises users and services must be able to access the Azure Storage account that will host the data in App1.
Reference: https://docs.microsoft.com/en-us/azure/storage/blobs/network-file-system-protocol-support
Question 2 Topic 1, Case Study 1Case Study Question View Case
You migrate App1 to Azure.
You need to ensure that the data storage for App1 meets the security and compliance requirements.
What should you do?
- A. Create Azure RBAC assignments.
- B. Create an access policy for the blob service.
- C. Modify the access level of the blob service.
- D. Implement Azure resource locks.
Answer:
A
Explanation:
Azure Active Directory (Azure AD) authorizes access rights to secured resources through Azure role-based access control
(Azure RBAC). Azure Storage defines a set of Azure built-in roles that encompass common sets of permissions used to
access blob data.
When an Azure role is assigned to an Azure AD security principal, Azure grants access to those resources for that security
principal. An Azure AD security principal may be a user, a group, an application service principal, or a managed identity for
Azure resources.
Scenario:
To access the resources in Azure, App1 must use the managed identity of the virtual machines that will host the app.
The Litware.com tenant contains a custom Azure role-based access control (Azure RBAC) role named Role1 that grants the
DataActions read permission to the blobs and files in Azure Storage.
Litware identifies the following security and compliance requirements:
On-premises users and services must be able to access the Azure Storage account that will host the data in App1.
Reference: https://docs.microsoft.com/en-us/azure/storage/blobs/assign-azure-role-data-access
Question 3 Topic 1, Case Study 1Case Study Question View Case
HOTSPOT
You need to ensure that users managing the production environment are registered for Azure MFA and must authenticate by
using Azure MFA when they sign in to the Azure portal. The solution must meet the authentication and authorization
requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: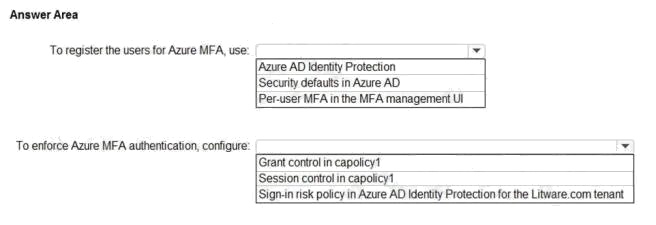
Answer:
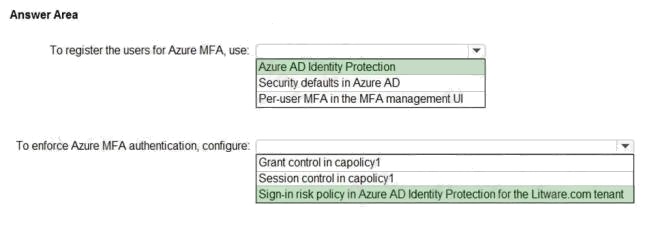
Explanation:
Box 1: Azure AD Identity Protection
Azure AD Identity Protection helps you manage the roll-out of Azure AD Multi-Factor Authentication (MFA) registration by
configuring a Conditional Access policy to require MFA registration no matter what modern authentication app you are
signing in to.
Scenario: Users that manage the production environment by using the Azure portal must connect from a hybrid Azure AD-
joined device and authenticate by using Azure Multi-Factor Authentication (MFA).
Box 2: Sign-in risk policy...
Scenario: The Litware.com tenant has a conditional access policy named capolicy1. Capolicy1 requires that when users
manage the Azure subscription for a production environment by using the Azure portal, they must connect from a hybrid
Azure AD-joined device.
Identity Protection policies we have two risk policies that we can enable in our directory. Sign-in risk policy User risk

policy
Reference: https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-configure-
mfa-policy https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-configure-risk-
policies
Question 4 Topic 1, Case Study 1Case Study Question View Case
You plan to migrate App1 to Azure.
You need to recommend a network connectivity solution for the Azure Storage account that will host the App1 data. The
solution must meet the security and compliance requirements.
What should you include in the recommendation?
- A. a private endpoint
- B. a service endpoint that has a service endpoint policy
- C. Azure public peering for an ExpressRoute circuit
- D. Microsoft peering for an ExpressRoute circuit
Answer:
D
Explanation:
By default, Azure service resources secured to virtual networks aren't reachable from on-premises networks. If you want to
allow traffic from on-premises, you must also allow public (typically, NAT) IP addresses from your on-premises or
ExpressRoute. You can add these IP addresses through the IP firewall configuration for Azure service resources.
You can use ExpressRoute for public peering and Microsoft peering.
Scenario:
On-premises users and services must be able to access the Azure Storage account that will host the data in App1.

Access to the public endpoint of the Azure Storage account that will host the App1 data must be prevented.
Incorrect Answers:
C: Public Peering is deprecated for new circuits.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-service-endpoints-overview
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-circuit-peerings
Question 5 Topic 1, Case Study 1Case Study Question View Case
You plan to migrate App1 to Azure. The solution must meet the authentication and authorization requirements.
Which type of endpoint should App1 use to obtain an access token?
- A. Azure Instance Metadata Service (IMDS)
- B. Azure AD
- C. Azure Service Management
- D. Microsoft identity platform
Answer:
D
Explanation:
Scenario: To access the resources in Azure, App1 must use the managed identity of the virtual machines that will host the
app.
Managed identities provide an identity for applications to use when connecting to resources that support Azure Active
Directory (Azure AD) authentication. Applications may use the managed identity to obtain Azure AD tokens.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/overview
Question 6 Topic 1, Case Study 1Case Study Question View Case
DRAG DROP
You need to configure an Azure policy to ensure that the Azure SQL databases have TDE enabled. The solution must meet
the security and compliance requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the
answer area and arrange them in the correct order.
Select and Place: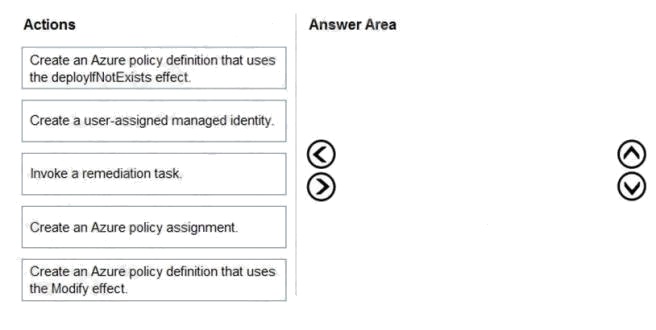
Answer:
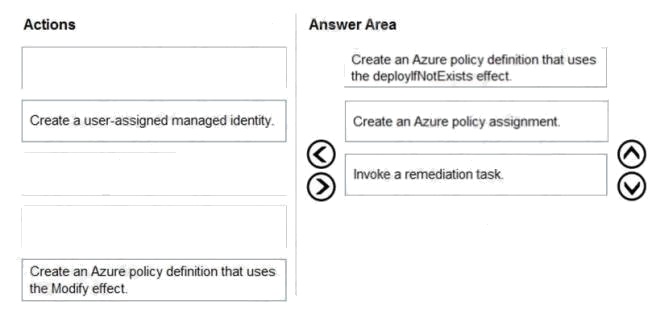
Explanation:
Scenario: All Azure SQL databases in the production environment must have Transparent Data Encryption (TDE) enabled.
Step 1: Create an Azure policy definition that uses the deployIfNotExists identity.
The first step is to define the roles that deployIfNotExists and modify needs in the policy definition to successfully deploy the
content of your included template.
Step 2: Create an Azure policy assignment
When creating an assignment using the portal, Azure Policy both generates the managed identity and grants it the roles
defined in roleDefinitionIds.
Step 3: Invoke a remediation task
Resources that are non-compliant to a deployIfNotExists or modify policy can be put into a compliant state through
Remediation. Remediation is accomplished by instructing Azure Policy to run the deployIfNotExists effect or the modify
operations of the assigned policy on your existing resources and subscriptions, whether that assignment is to a management
group, a subscription, a resource group, or an individual resource.
During evaluation, the policy assignment with deployIfNotExists or modify effects determines if there are non-compliant
resources or subscriptions. When non-compliant resources or subscriptions are found, the details are provided on the
Remediation page.
Reference: https://docs.microsoft.com/en-us/azure/governance/policy/how-to/remediate-resources
Question 7 Topic 2, Case Study 2Case Study Question View Case
What should you include in the identity management strategy to support the planned changes?
- A. Move all the domain controllers from corp.fabrikam.com to virtual networks in Azure.
- B. Deploy domain controllers for the rd.fabrikam.com forest to virtual networks in Azure.
- C. Deploy domain controllers for corp.fabrikam.com to virtual networks in Azure.
- D. Deploy a new Azure AD tenant for the authentication of new R&D projects.
Answer:
C
Explanation:
Directory synchronization between Azure Active Directory (Azure AD) and corp.fabrikam.com must not be affected by a link
failure between Azure and the on-premises network. (This requires domain controllers in Azure)
Users on the on-premises network must be able to authenticate to corp.fabrikam.com if an Internet link fails. (This requires
domain controllers on-premises)
Question 8 Topic 2, Case Study 2Case Study Question View Case
HOTSPOT
To meet the authentication requirements of Fabrikam, what should you include in the solution? To answer, select the
appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: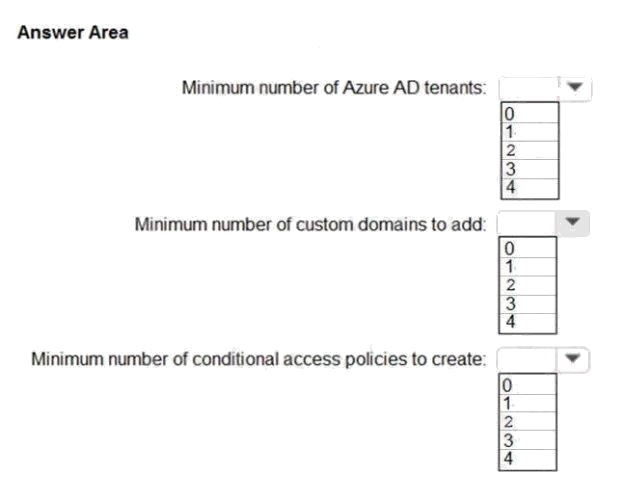
Answer:
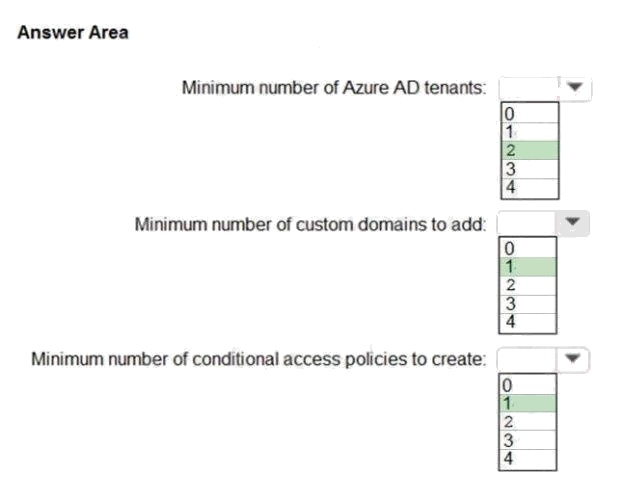
Explanation:
Box 1: 2
The network contains two Active Directory forests named corp.fabrikam.com and rd.fabrikam.com. There are no trust
relationships between the forests.
Box 2: 1
Box 3: 1
Scenario:
Users on the on-premises network must be able to authenticate to corp.fabrikam.com if an Internet link fails.
Administrators must be able authenticate to the Azure portal by using their corp.fabrikam.com credentials. All

administrative access to the Azure portal must be secured by using multi-factor authentication.
Note:
Users must always authenticate by using their corp.fabrikam.com UPN identity.
The network contains two Active Directory forests named corp.fabrikam.com and rd.fabrikam.com. There are no trust
relationships between the forests.
Corp.fabrikam.com is a production forest that contains identities used for internal user and computer authentication.
Rd.fabrikam.com is used by the research and development (R&D) department only.
Design Identity and Security
Question 9 Topic 3, Case Study 3Case Study Question View Case
You need to recommend a solution for protecting the content of the payment processing system.
What should you include in the recommendation?
- A. Always Encrypted with deterministic encryption
- B. Always Encrypted with randomized encryption
- C. Transparent Data Encryption (TDE)
- D. Azure Storage Service Encryption
Answer:
A
Question 10 Topic 3, Case Study 3Case Study Question View Case
HOTSPOT
You need to recommend a solution for the data store of the historical transaction query system.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: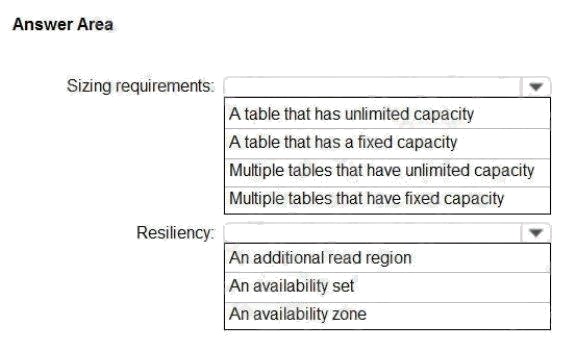
Answer:
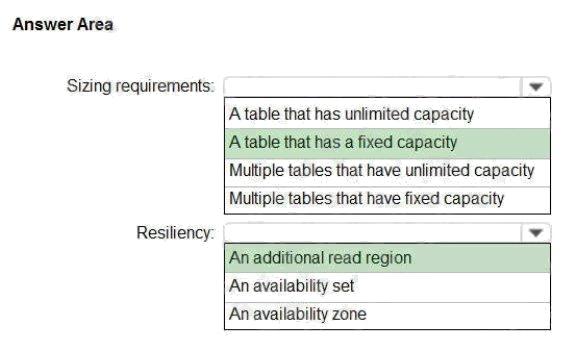
Explanation:
Design Business Continuity
Question 11 Topic 4, Case Study 4Case Study Question View Case
You need to recommend a backup solution for the data store of the payment processing system.
What should you include in the recommendation?
- A. Microsoft System Center Data Protection Manager (DPM)
- B. Azure Backup Server
- C. Azure SQL long-term backup retention
- D. Azure Managed Disks
Answer:
C
Explanation:
Reference:
https://docs.microsoft.com/en-us/azure/sql-database/sql-database-long-term-backup-retention-configure
Question 12 Topic 4, Case Study 4Case Study Question View Case
You need to recommend a disaster recovery solution for the back-end tier of the payment processing system.
What should you include in the recommendation?
- A. Azure Site Recovery
- B. an auto-failover group
- C. Always On Failover Cluster Instances
- D. geo-redundant database backups
Answer:
B
Explanation:
Scenario:
The back-end data store is implemented as a Microsoft SQL Server 2014 database.
If a data center fails, ensure that the payment processing system remains available without any administrative
intervention.
Note: Auto-failover groups is a SQL Database feature that allows you to manage replication and failover of a group of
databases on a SQL Database server or all databases in a managed instance to another region. It is a declarative
abstraction on top of the existing active geo-replication feature, designed to simplify deployment and management of geo-
replicated databases at scale. Reference:
https://docs.microsoft.com/en-us/azure/sql-database/sql-database-auto-failover-group
Question 13 Topic 4, Case Study 4Case Study Question View Case
You need to recommend a high-availability solution for the middle tier of the payment processing system.
What should you include in the recommendation?
- A. the Premium App Service plan
- B. an availability set
- C. availability zones
- D. the Isolated App Service plan
Answer:
C
Question 14 Topic 5, Case Study 5Case Study Question View Case
You need to recommend a solution to meet the database retention requirement.
What should you recommend?
- A. Configure geo-replication of the database.
- B. Configure a long-term retention policy for the database.
- C. Configure Azure Site Recovery.
- D. Use automatic Azure SQL Database backups.
Answer:
B
Question 15 Topic 5, Case Study 5Case Study Question View Case
HOTSPOT
You design a solution for the web tier of WebApp1 as shown in the exhibit.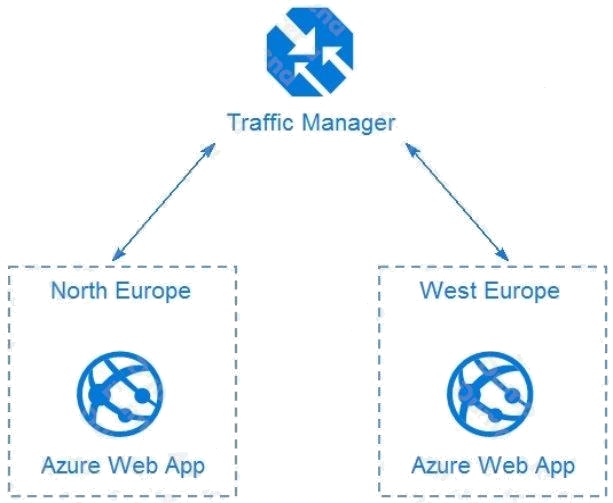
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: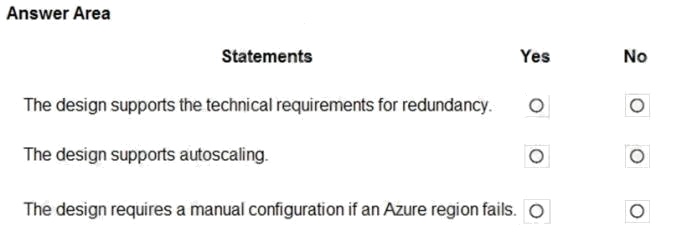
Answer:
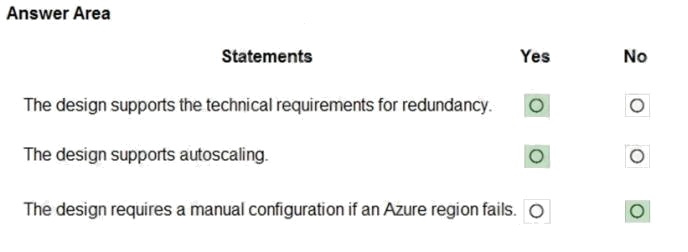
Explanation:
Box 1: Yes
Any new deployments to Azure must be redundant in case an Azure region fails.
Traffic Manager uses DNS to direct client requests to the most appropriate service endpoint based on a traffic-routing
method and the health of the endpoints. An endpoint is any Internet-facing service hosted inside or outside of Azure. Traffic
Manager provides a range of traffic-routing methods and endpoint monitoring options to suit different application needs and
automatic failover models. Traffic Manager is resilient to failure, including the failure of an entire Azure region.
Box 2: Yes
Recent changes in Azure brought some significant changes in autoscaling options for Azure Web Apps (i.e. Azure App
Service to be precise as scaling happens on App Service plan level and has effect on all Web Apps running in that App
Service plan).
Box 3: No
Traffic Manager provides a range of traffic-routing methods and endpoint monitoring options to suit different application
needs and automatic failover models. Traffic Manager is resilient to failure, including the failure of an entire Azure region.
Reference:
https://docs.microsoft.com/en-us/azure/traffic-manager/traffic-manager-overview
https://blogs.msdn.microsoft.com/hsirtl/2017/07/03/autoscaling-azure-web-apps/
Design Infrastructure