mcafee MA0-107 Exam Questions
Questions for the MA0-107 were updated on : Feb 20 ,2026
Page 1 out of 5. Viewing questions 1-15 out of 70
Question 1
An engineer needs to allow a specific application to run. The engineer just finished creating an
Exploit Prevention process exclusion. After applying the exclusion, the engineer notices the
application is not being run. The following information is provided to the engineer: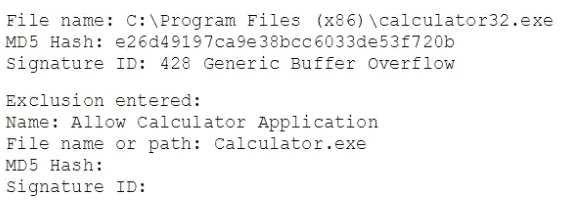
Which of the following is the error with the engineer's exclusion?
- A. A signature ID was not entered.
- B. Exclusions are case sensitive.
- C. A hash was not specified.
- D. Wildcard was not used.
Answer:
B
Question 2
Joe, an administrator, runs a policy-based, on-demand scan on a system and notices that after the
scan, a threat event was created for what appears to be a false positive. Joe wants to submit the file
for analysis to McAfee Labs; but every time he accesses the file, it is detected. In which of the
following default locations can Joe find the backups of the detected files?
- A. %ProgramData%\McAfee\Common Framework\AgentEvents
- B. C:\Quarantine
- C. C:\Windows\Temp\Quarantine
- D. %deflogfir%\Quarantine
Answer:
A
Question 3
An ePO administrator wants to configure system utilization for on-demand scanning to conform to
best-practice recommendations based on the ENS Product Guide. To do this, the administrator
should:
- A. set system utilization to "Normal" for systems with end-user activity and "Low" for systems with large volumes/little end-user activity.
- B. set system utilization to "Low" for systems with end-user activity and "Normal" for systems with large volumes/little end-user activity.
- C. set system utilization to "Low" for systems with end-user activity and "Low" for systems with large volumes/little end-user activity.
- D. set system utilization to "Below Normal" for systems with end-user activity and "Normal" for systems with large volumes/little end-user activity.
Answer:
A
Question 4
A security professional is configuring ENS for a client and wants to ensure applications will be
prevented from executing software locally from the browser or email client. Which of the following
McAfee-defined rules should be implemented?
- A. Creating new executable files in the Windows folder
- B. Installing browser helper objects or shell extensions
- C. Registering programs to autorun
- D. Running files from common user folders by common programs
Answer:
B
Question 5
After installing ENS on a server, the server administrator finds that a specific application runs very
slow, yet communication flows are still present. Which of the following remediation steps should the
administrator take?
- A. Remove an exclusion.
- B. Create a whitelist.
- C. Create an exclusion.
- D. Remove a whitelist.
Answer:
C
Question 6
Which of the following is the benefit of a TIE server with regard to the Adaptive Threat Protection
module?
- A. It communicates with McAfee GTI for file and certificate reputation for malicious code.
- B. It is required, and the Adaptive Threat Protection will only work with the TIE server.
- C. The Threat Protection cache flushes when the reputation rules change.
- D. The stored file and certificate reputations are locally stored, making the remediation automatically quicker.
Answer:
A
Question 7
When configuring the Adaptive Threat Protection Options policy, which of the following is a rule
assignment group that needs to be selected to accommodate an environment consisting of high-
change systems with frequent installations and updates of trusted software?
- A. Adaptive
- B. Productivity
- C. Balanced
- D. Security
Answer:
D
Question 8
Which of the following fields can an ePO administrator use when creating exclusions for Dynamic
Application Containment?
- A. Certificate
- B. Rule
- C. File version
- D. MD5 hash
Answer:
D
Question 9
Organizational security policy requires a host-based firewall on endpoints. Some endpoints have
applications where documentation depicting network traffic flows is not readily available. Which of
the following ENS 10.5 firewall features should be used to develop rules for their firewall policy?
- A. Location-aware Groups
- B. Trusted Networks
- C. Trusted Executables
- D. Adaptive Mode
Answer:
B
Question 10
Which of the following groups of legacy products can be migrated to ENS 10.5?
- A. VirusScan Enterprise, Host Intrusion Prevention, and SiteAdvisor Enterprise
- B. Host Intrusion Prevention, SiteAdvisor Enterprise, and Data Loss Prevention
- C. VirusScan Enterprise, Host Intrusion Prevention, and Data Loss Prevention
- D. Host Intrusion Prevention, SiteAdvisor Enterprise, and Application Control
Answer:
C
Question 11
By using which of the following techniques does Real Protect scanner inspect suspicious files and
activities on an endpoint to detect malicious patterns?
- A. Machine learning
- B. Intrusion prevention
- C. Sandboxing
- D. Static code analysis
Answer:
B
Question 12
On Windows 8 and 10 machines, Windows places a flag in the tile of an app, causing Windows to
notify the user of a problem and directing the user to the Windows Store to reinstall. This flag is
placed on the tile when the Threat Prevention scanner detects a threat in the path of an installed
Windows Store app, and marks the application as:
- A. malicious.
- B. suspicious.
- C. questionable.
- D. tampered.
Answer:
A
Question 13
The organization's desktop engineering team wants to include ENS 10 within their desktop imaging
process. They would like to install all modules silently. Which of the following is the correct
command-line syntax to accomplish this task?
- A. setupEP.exe ADDLOCAL="all" /qb!
- B. setupEP.exe ADDLOCAL="all" /qn
- C. setupEP.exe ADDLOCAL="fw,tp,wc" /qb!
- D. setupEP.exe ADDLOCAL="fw,tp,wc" /qn
Answer:
C
Question 14
Dynamic Application Containment uses which of the following attributes of an executable to provide
advanced protection?
- A. File behavior
- B. File name
- C. File size
- D. File source
Answer:
C
Question 15
An ENS administrator wants to dynamically create firewall rules required for the environment. In
Enable Firewall Policies/Options, which of the following should be utilized?
- A. Retain existing user added rules
- B. Adaptive mode
- C. Log all blocked traffic
- D. Log all allowed traffic
Answer:
C