Juniper JN0-637 Exam Questions
Questions for the JN0-637 were updated on : Feb 18 ,2026
Page 1 out of 8. Viewing questions 1-15 out of 115
Question 1
Referring to the exhibit, which two statements are true ?
- A. Every VPN packet that the SRX receives from the VPN peer is outside the ESP sequence window
- B. The SRX is sending traffic into the tunnel and out toward the VPN peer.
- C. The SRX is not sending any packets to the VPN peer.
- D. The SRX is not receiving any packets from the VPN peer.
Answer:
BD
Question 2
Which encapsulation type must be configured on the lt-0/0/0 logical units for an interconnect
logical systems VPLS switch?
- A. encapsulation ethernet-bridge
- B. encapsulation ethernet
- C. encapsulation ethernet-vpls
- D. encapsulation vlan-vpls
Answer:
C
Question 3
Which two statements are correct about DNS doctoring?
- A. The DNS ALG must be disabled.
- B. Proxy ARP is required if your NAT pool for the server is on the same subnet as the uplink interface.
- C. Proxy ARP is required if your NAT pool for the server is on a different subnet as the uplink interface
- D. The DNS ALG must be enabled.
Answer:
BD
Question 4
You are experiencing problem with your ADVPN tunnels getting established. The tunnel
and egress interface are located in different zone. What are two reasons for these problems?
(Choose two.)
- A. IKE is not an allowed protocol in the external interfaces' security zone.
- B. IKE is not an allowed protocol in the tunnel endpoints' security zone.
- C. OSPF is not an allowed protocol in the tunnel endpoints' security zone.
- D. BGP is not an allowed protocol in the tunnel endpoints' security zone.
Answer:
AB
Question 5
Exhibit:
The Ipsec VPN does not establish when the peer initiates, but it does establish when the SRX
series device initiates. Referring to the exhibit, what will solve this problem?
- A. IKE needs to be added for the host-inbound traffic on the VPN zone.
- B. The screen configuration on the untrust zone needs to be modified.
- C. IKE needs to be added to the host-inbound traffic directly on the ge-0/0/0 interface.
- D. Application tracking on the untrust zone needs to be removed.
Answer:
C
Question 6
You have deployed a new site as shown in the exhibit. Hosts in the 10.10.10.0/24 network
must access the DB1 server. The DB1 server must also have internet access the DB1 server encrypted.
Which two configuration statements will be required as part of the configuration on SRX1 to satisfy
this requirement? (Choose two)
- A. set security macsec interfaces ge-0/0/1 connectivity association access-sw
- B. set protocols 12-learning global mode transpårent-bridge
- C. set security forwarding-options secure-wire access-sw interface ge-0/0/1.0
- D. set security macsec connectivity-association access-sw security-mode static-cak
Answer:
AD
Question 7
Which two statements are correct about advanced policy-based routing?
- A. It can use the application system cache to route traffic.
- B. The associated routing instance should be configured as a virtual router instance.
- C. It cannot use the application system cache to route traffic.
- D. The associated routing instance should be configured as a forwarding instance.
Answer:
AD
Question 8
Which two statements describe the behavior of logical systems? (Choose two.)
- A. Each logical system shares the routing protocol process.
- B. A default routing instance must be manually created for each logical system
- C. Each logical system has a copy of the routing protocol process.
- D. A default routing instance is automatically created for each logical system.
Answer:
CD
Question 9
You have cloud deployments in Azure, AWS, and your private cloud. You have deployed
multicloud using security director with policy enforcer to. Which three statements are true in this
scenario? (Choose three.)
- A. You can run Juniper ATP scans only on traffic from your private cloud.
- B. You can run Juniper ATP scans for all three domains.
- C. You must secure the policies individually by domain.
- D. The Policy Enforcer is able to flag infected hosts in all three domains.
- E. You can simultaneously manage the security policies in all three domains.
Answer:
BDE
Question 10
A user reports that a specific application is not working properly. This application makes
multiple connection to the server and must have the same address every time from a pool and this
behavior needs to be changed.
What would solve this problem?
- A. Use STUN.
- B. Use DNS doctoring.
- C. Use the address-persistent parameter.
- D. Use the persistent-nat parameter.
Answer:
D
Question 11
Referring to the exhibit, you are assigned the tenantSYS1 user credentials on an SRX series
device.
In this scenario, which two statements are correct? (Choose two.)
- A. When you log in to the device, you will be located at the operational mode of the main system hierarchy.
- B. When you log in to the device, you will be located at the operational mode of the Tenant.SY51 logical system hierarchy.
- C. When you log in to the device, you will be permitted to view only the routing tables for the Tenant SYS1 logical system.
- D. When you log in to the device, you will be permitted to view all routing tables available on the on an SYS1 Series device.
Answer:
BC
Question 12
Which two statements about the differences between chassis cluster and multinode HA on
SRX series devices are true? (Choose Two)
- A. Multinode HA member nodes require Layer 2 connectivity.
- B. Multinode HA supports Layer 2 and Layer 3 connectivity between nodes.
- C. Multinode HA requires Layer 3 connectivity between nodes.
- D. Chassis cluster member nodes require Layer 2 connectivity.
Answer:
BD
Question 13
You Implement persistent NAT to allow any device on the external side of the firewall to
initiate traffic.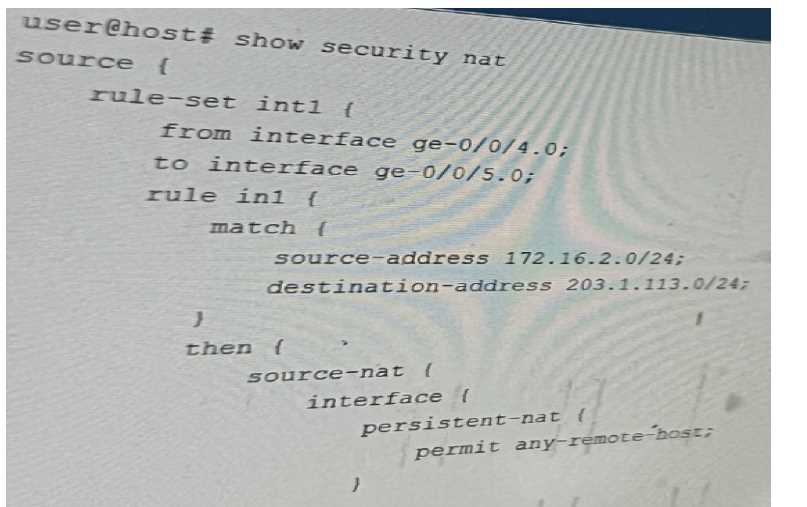
Referring to the exhibit, which statement is correct?
- A. The target-host parameter should be used instead of the any-remote-host parameter.
- B. The port-overloading parameter needs to be turned off in the NAT source interface configuration
- C. The target-host-port parameter should be used instead of the any-remote-host parameter
- D. The any-remote-host parameter does not support interface-based NAT and needs an IP pod to work.
Answer:
D
Question 14
Which three statements about persistent NAT are correct? (Choose Three)
- A. New sessions can only be initiated from a source towards the reflexive address.
- B. New sessions can be initiated from a destination towards the reflexive address.
- C. Persistent NAT only applies to source NAT.
- D. All requests from an internal address are mapped to the same reflexive address.
- E. Persistent NAT applies to both destination and source NAT.
Answer:
BCD
Question 15
Which two statements about policy enforcer and the forescout integration are true? (Choose two)
- A. 802.1X authenticated devices are supported.
- B. 802.1X authenticated devices are not supported.
- C. A Forescout CounterACT agent must be installed on third-party devices
- D. A Forescout CounterACT agent is agentless and does not need to be installed on third-party device
Answer:
AD