Juniper JN0-635 Exam Questions
Questions for the JN0-635 were updated on : Jun 25 ,2025
Page 1 out of 6. Viewing questions 1-15 out of 88
Question 1
Click the Exhibit button.
While configuring the SRX345, you review the MACsec connection between devices and note that it
is not working.
Referring to the exhibit, which action would you use to identify problem?
- A. Verify that the formatting settings are correct between the devices and that the software supports the version of MACsec in use
- B. Verify that the connectivity association key and the connectivity association key name match on both devices
- C. Verify that the transmission path is not replicating packets or correcting frame check sequence error packets
- D. Verify that the interface between the two devices is up and not experiencing errors
Answer:
B
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/reference/command-summary/show-security-mka-statistics.html
Question 2
Click the Exhibit button.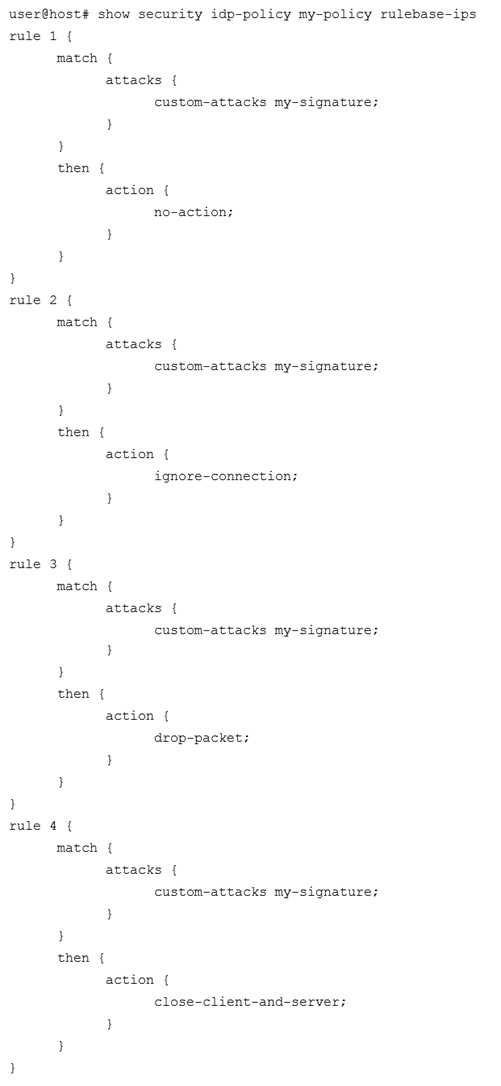
You have recently committed the IPS policy shown in the exhibit. When evaluating the expected
behavior, you notice that you have a session that matches all the rules in your IPS policy.
In this scenario, which action would be taken?
- A. drop packet
- B. no-action
- C. close-client-and-server
- D. ignore-connection
Answer:
B
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-idp-policy-rules-and-rulebases.html
Question 3
Your organization has multiple Active Directory domains to control user access. You must ensure that
security policies are passing traffic based upon the users access rights.
What would you use to assist your SRX Series devices to accomplish this task?
- A. JATP Appliance
- B. JIMS
- C. JSA
- D. Junos Space
Answer:
B
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-user-auth-intergrated-user-firewall-overview.html
Question 4
You are asked to set up notifications if one of your collector traffic feeds drops below 100 kbps.
Which two configuration parameters must be set to accomplish this task? (Choose two.)
- A. Set a traffic SNMP trap on the JATP appliance
- B. Set a logging notification on the JATP appliance
- C. Set a general triggered notification on the JATP appliance
- D. Set a traffic system alert on the JATP appliance
Answer:
BD
Question 5
You have configured static NAT for a webserver in your DMZ. Both internal and external users can
reach the webserver using the webservers IP address. However, only internal users can reach the
webserver using the webservers DNS name. When external users attempt to reach the webserver
using the webservers DNS name, an error message is received.
Which action would solve this problem?
- A. Disable Web filtering
- B. Use DNS doctoring
- C. Modify the security policy
- D. Use destination NAT instead of static NAT
Answer:
B
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-dns-algs.html
Question 6
Which interface family is required for Layer 2 transparent mode on SRX Series devices?
- A. LLDP
- B. Ethernet switching
- C. inet
- D. VPLS
Answer:
B
Question 7
Click the Exhibit button.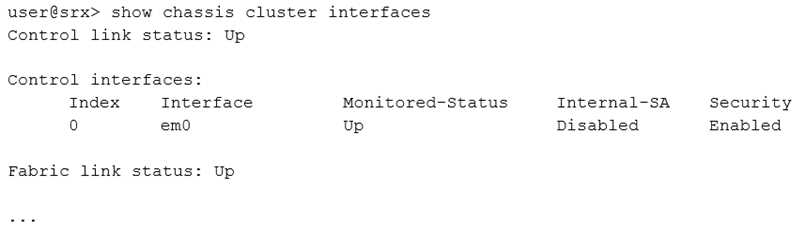
Referring to the exhibit, which statement is true?
- A. ARP security is securing data across the control interface
- B. IPsec is securing data across the control interface
- C. SSH is securing data across the control interface
- D. MACsec is securing data across the control interface
Answer:
D
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/reference/command-summary/show-chassis-cluster-interfaces.html
Question 8
You have configured three logical tunnel interfaces in a tenant system on an SRX1500 device. When
committing the configuration, the commit fails.
In this scenario, what would cause this problem?
- A. There is no GRE tunnel between the tenant system and master system allowing SSH traffic
- B. There is no VPLS switch on the tenant system containing a peer It-0/0/0 interface
- C. The SRX1500 device does not support more than two logical interfaces per tenant system
- D. The SRX1500 device requires a tunnel PIC to allow for logical tunnel interfaces
Answer:
B
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/logical-systems-overview.html
Question 9
You are asked to merge to corporate network with the network from a recently acquired company.
Both networks use the same private IPv4 address space (172.25.126.0/24). An SRX Series device
servers as the gateway for each network.
Which solution allows you to merge the two networks without modifying the current address
assignments?
- A. persistent NAT
- B. NAT46
- C. source NAT
- D. double NAT
Answer:
D
Explanation:
Reference:
https://kb.juniper.net/InfoCenter/index?page=content&id=KB21286
Question 10
You have set up Security Director with Policy Enforcer and have configured 12 third-party feeds and a
Sky ATP feed. You are also injecting 16 feeds using the available open API. You want to add another
compatible feed using the available open API, but Policy Enforcer is not receiving the new feed.
What is the problem in this scenario?
- A. You must wait 48 hours for the feed to update
- B. You cannot add more than 16 feeds through the available open API
- C. You have reached the maximum limit of 29 total feeds
- D. You cannot add more than 16 feeds with the available open API
Answer:
C
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/release-independent/sky-
atp/information-products/
pathway-pages/sky-atp-admin-guide.pdf page 110
There is a limit to the number of feeds you can have. When you enable feeds from this page, they
count toward your limit of 29 feeds. This is applicable if you are injecting additional feeds using the
available open API.
Question 11
Which three types of peer devices are supported for CoS-based IPsec VPNs? (Choose three.)
- A. branch SRX Series device
- B. third-party device
- C. cSRX
- D. high-end SRX Series device
- E. vSRX
Answer:
ADE
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/secuirty-cos-based-ipsec-vpns.html
Question 12
You are asked to configure a new SRX Series CPE device at a remote office. The device must
participate in forwarding MPLS and IPsec traffic.
Which two statements are true regarding this implementation? (Choose two.)
- A. Host inbound traffic must not be processed by the flow module
- B. Host inbound traffic must be processed by the flow module
- C. The SRX Series device can process both MPLS and IPsec with default traffic handling
- D. A firewall filter must be configured to enable packet mode forwarding
Answer:
BD
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-packet-based-forwarding.html
Question 13
Which three roles or protocols are required when configuring an ADVPN? (Choose three.)
- A. OSPF
- B. shortcut partner
- C. shortcut suggester
- D. IKEv1
- E. BGP
Answer:
ABC
Explanation:
Reference:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-auto-discovery-vpns.html
Question 14
You must troubleshoot ongoing problems with IPsec tunnels and security policy processing. Your
network consists of SRX340s and SRX5600s.
In this scenario, which two statements are true? (Choose two.)
- A. IPsec logs are written to the kmd log file by default
- B. IKE logs are written to the messages log file by default
- C. You must enable data plane logging on the SRX340 devices to generate security policy logs
- D. You must enable data plane logging on the SRX5600 devices to generate security policy logs
Answer:
AD
Question 15
Click the Exhibit button.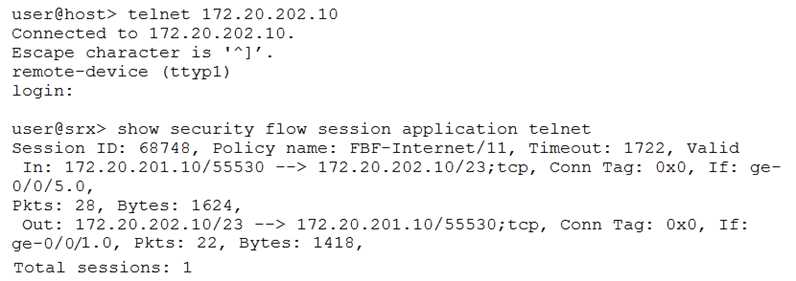
You are implementing a new branch site and want to ensure Internet traffic is sent directly to your
ISP and other traffic is sent to your company headquarters. You have configured filter-based
forwarding to accomplish this objective. You verify proper functionality using the outputs shown in
the exhibit.
Which two statements are true in this scenario? (Choose two.)
- A. The session utilizes one routing instance
- B. The ge-0/0/5 and ge-0/0/1 interfaces must reside in a single security zone
- C. The ge-0/0/5 and ge-0/0/1 interfaces can reside in different security zones
- D. The session utilizes two routing instances
Answer:
AC