Juniper JN0-351 Exam Questions
Questions for the JN0-351 were updated on : Feb 18 ,2026
Page 1 out of 5. Viewing questions 1-15 out of 65
Question 1
You are receiving multiple BGP routes from an upstream neighbor and only want to advertise a single
summarized prefix to your internal OSPF neighbors. This route should only be advertised when you
are receiving these BGP routes from this neighbor.
In this scenario, which type of route should you create?
- A. aggregate route
- B. static route using the resolve feature
- C. generate route
- D. static route using qualified next hops
Answer:
A
Explanation:
In this scenario, you should create an aggregate route1
.
Aggregate routes are used for advertising
summarized network prefixes1
.
They help minimize the number of routing tables in an IP network by
consolidating selected multiple routes into a single route advertisement1
.
This approach is in
contrast to non-aggregation routing, in which every routing table contains a unique entry for each
route1
.
Therefore, option A is correct. Options B, C, and D are not correct because:
Static route using the resolve feature: This type of route uses the resolve feature to install a static
route in the routing table only if a specific condition is met1
. However, it does not provide the
capability to summarize multiple routes into a single prefix.
Generate route: This type of route generates a route that is always present in the routing table and
can be used to summarize routes.
However, it does not have the capability to only advertise the
route when specific BGP routes are being received from a neighbor1
.
Static route using qualified next hops: This type of route allows for the specification of multiple next-
hop addresses for a static route1
. However, it does not provide the capability to summarize multiple
routes into a single prefix.
Question 2
Exhibit
Referring to the exhibit, which two configuration changes must you apply for packets to reach from
R1 to R3 using IS-IS? (Choose two.)
- A. On R1, enable Level 1 on the ge-0/0/1 interface.
- B. On R3 disable Level 2 on the ge-0/0/4 interface.
- C. On R1, disable Level 2 on the ge-0/0/1 interface.
- D. On R3 enable Level 1 on the ge-0/0/4 interface
Answer:
AD
Explanation:
A) On R1, enable Level 1 on the ge-0/0/1 interface. In IS-IS, both levels (Level 1 and Level 2) are
enabled by default when you enable IS-IS on an interface1
.
Level 1 systems route within an area2
.
If
the destination is outside an area, Level 1 systems route toward a Level 2 system2
. Therefore,
enabling Level 1 on the ge-0/0/1 interface on R1 would allow packets to reach from R1 to R3.
D) On R3 enable Level 1 on the ge-0/0/4 interface Similarly, enabling Level 1 on the ge-0/0/4
interface on R3 would allow packets to reach from R1 to R3.
These explanations are based on the IS-IS configuration documents and learning resources available
at Juniper Networks1 and Cisco34
.
Question 3
Which statement about aggregate routes is correct?
- A. Aggregate routes can only be used for static routing but not for dynamic routing protocols.
- B. Aggregate routes are automatically generated for all of the subnets in a routing table.
- C. Aggregate routes are always preferred over more specific routes, even when the specific routes have a better path.
- D. Aggregate routes are used for advertising summarized network prefixes.
Answer:
D
Explanation:
Aggregate routes are used for advertising summarized network prefixes12
.
They help minimize the
number of routing tables in an IP network by consolidating selected multiple routes into a single
route advertisement1
.
This approach is in contrast to non-aggregation routing, in which every
routing table contains a unique entry for each route1
.
Therefore, option D is correct. Options A, B, and C are not correct because:
Aggregate routes can be used with both static routing and dynamic routing protocols1
.
Aggregate routes are not automatically generated for all of the subnets in a routing table.
They need
to be manually configured1
.
Aggregate routes are not always preferred over more specific routes.
The route selection process in
Junos OS considers several factors, including route preference and metric, before determining the
active route1
.
Question 4
Exhibit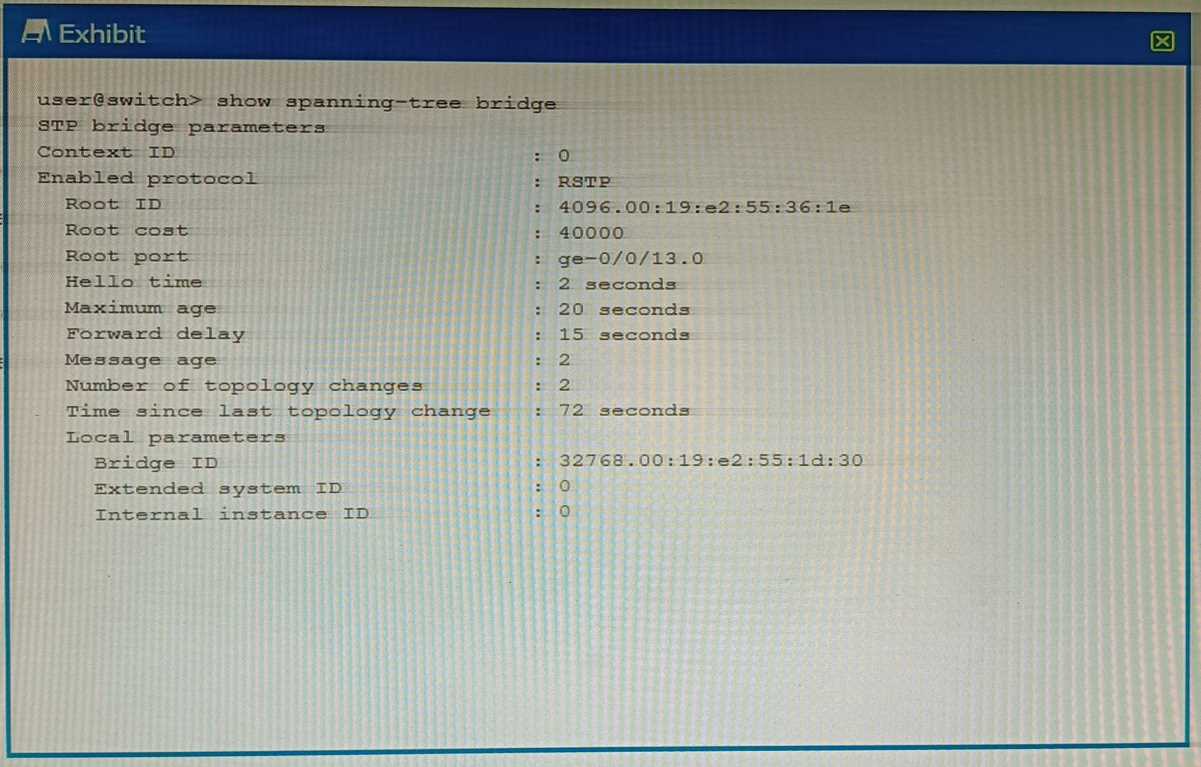
Referring to the exhibit, which statement is correct?
- A. The local device is using a bridge priority of 4k.
- B. The root bridge is using a bridge priority of 4k.
- C. The root bridge has not been elected for this RSTP topology.
- D. The local device is the root bridge for this RSTP topology.
Answer:
D
Explanation:
In a Rapid Spanning Tree Protocol (RSTP) topology, the root bridge is determined by the switch with
the lowest bridge priority value12
.
If all switches have the same priority, then the root bridge is
assigned to the switch whose MAC address’s hex value is the lowest2
.
The default bridge priority
value is 3276832
. However, without the actual exhibit, it’s difficult to definitively determine which
device is the root bridge.
But based on the options provided, if we assume that the local device has a
lower bridge priority or a lower MAC address than other devices in the network, then it could be
considered as the root bridge for this RSTP topology45
.
Question 5
An update to your organization's network security requirements document requires management
traffic to be isolated in a non-default routing-instance. You want to implement this requirement on
your Junos-based devices.
Which two commands enable this behavior? (Choose two.)
- A. set routing—instances mgmtjunoa interface ge-0/0/0.0
- B. set routing—instances mgmt_junos interface em1
- C. set system management—instance
- D. set routing—instances mgmt_junos
Answer:
CD
Explanation:
To isolate management traffic in a non-default routing-instance on Junos-based devices, you can use
the set system management-instance and set routing-instances mgmt_junos commands12
.
set system management-instance: This command associates the management interface (usually
named fxp0 or em0 for Junos OS, or re0:mgmt-* or re1:mgmt-* for Junos OS Evolved) with the non-
default virtual routing and forwarding (VRF) instance1
.
After you configure the non-default
management VRF instance, management traffic no longer has to share a routing table with other
control traffic or protocol traffic1
.
set routing-instances mgmt_junos: This command creates a new routing instance
named mgmt_junos.
The name of the dedicated management VRF instance is reserved and
hardcoded as mgmt_junos; you cannot configure any other routing instance by the
name mgmt_junos1
.
Therefore, options C and D are correct.
Options A and B are not correct because they attempt to
assign an interface to the mgmt_junos routing instance, which is not necessary for isolating
management traffic1
.
Question 6
You implemented the MAC address limit feature with the shutdown action on all interfaces on your
switch.
In this scenario, which statement is correct when a violation occurs?
- A. By default, you must manually clear the violation for the interface to send and receive traffic again.
- B. By default, the violation will automatically be cleared after 300 seconds and the interface will resume sending and receiving traffic for all learned devices.
- C. By default, devices that are learned before the violation occurs are still allowed to send and receive traffic through the specific interface.
- D. By default, the interface will continue to send and receive traffic for all connected devices after a violation has occurred.
Answer:
A
Explanation:
When the MAC address limit feature with the shutdown action is implemented on a switch, if a
violation occurs, the interface is disabled and a system log entry is generated1
.
If the switch has been
configured with the port-error-disable statement, the disabled interface recovers automatically upon
expiration of the specified disable timeout1
.
However, if the switch has not been configured for auto-
recovery from port error disabled conditions, you must manually clear the violation by running the
clear ethernet-switching port-error command for the interface to send and receive traffic again1
.
This
explanation is based on the Enterprise Routing and Switching Specialist (JNCIS-ENT) documents and
learning resources available at Juniper Networks1
.
Question 7
You have DHCP snooping enabled but no entries are automatically created in the snooping database
for an interface on your EX Series switch. What are two reasons for the problem? (Choose two.)
- A. The device that is connected to the interface has performed a DHCPRELEASE.
- B. MAC limiting is enabled on the interface.
- C. The device that is connected to the interface has a static IP address.
- D. Dynamic ARP inspection is enabled on the interface.
Answer:
BC
Explanation:
The DHCP snooping feature in Juniper Networks’ EX Series switches works by building a binding
database that maps the IP address, MAC address, lease time, binding type, VLAN number, and
interface information1
.
This database is used to filter and validate DHCP messages from untrusted
sources1
.
However, there are certain conditions that could prevent entries from being automatically created in
the snooping database for an interface:
MAC limiting: If MAC limiting is enabled on the interface, it could potentially interfere with the
operation of DHCP snooping.
MAC limiting restricts the number of MAC addresses that can be
learned on a physical interface to prevent MAC flooding attacks1
. This could inadvertently limit the
number of DHCP clients that can be learned on an interface, thus preventing new entries from being
added to the DHCP snooping database.
Static IP address: If the device connected to the interface is configured with a static IP address, it will
not go through the DHCP process and therefore will not have an entry in the DHCP snooping
database1
.
The DHCP snooping feature relies on monitoring DHCP messages to build its database1
,
so devices with static IP addresses that do not send DHCP messages will not have their information
added.
Therefore, options B and C are correct.
Options A and D are not correct because performing a
DHCPRELEASE would simply remove an existing entry from the database1, and Dynamic ARP
inspection (DAI) uses the information stored in the DHCP snooping binding database but does not
prevent entries from being created1
.
Question 8
You are an operator for a network running 1S-IS. Two routers are failing to form an adjacency. What
are two reasons for this problem? (Choose two.)
- A. There are mismatched router IDs on the L2 routers.
- B. There is no configured ISO address on any IS-IS interface.
- C. There is a mismatched area ID between the L2 routers.
- D. The family iso configuration is missing from the adjacency interface.
Answer:
BD
Explanation:
The two reasons for the failure to form an adjacency in a network running IS-IS could be:
B) There is no configured ISO address on any IS-IS interface. IS-IS requires each router interface to
have an ISO address configured.
Without this address, the routers cannot form an adjacency1
.
D) The family iso configuration is missing from the adjacency interface. The ‘family iso’ configuration
is essential for IS-IS to function correctly.
If this configuration is missing from the adjacency interface,
it could prevent the formation of an adjacency1
.
These explanations are based on the Enterprise Routing and Switching Specialist (JNCIS-ENT)
documents and learning resources available at Juniper Networks23
.
Question 9
Which two events cause a router to advertise a connected network to OSPF neighbors? (Choose
two.)
- A. When an OSPF adjacency is established.
- B. When an interface has the OSPF passive option enabled.
- C. When a static route to the 224.0.0.6 address is created.
- D. When a static route to the 224.0.0.5 address is created.
Answer:
AD
Explanation:
A is correct because when an OSPF adjacency is established, a router will advertise a connected
network to OSPF neighbors.
An OSPF adjacency is a logical relationship between two routers that
agree to exchange routing information using the OSPF protocol1
.
To establish an OSPF adjacency, the
routers must be in the same area, have compatible parameters, and exchange hello packets1
.
Once
an OSPF adjacency is formed, the routers will exchange database description (DBD) packets, which
contain summaries of their link-state databases (LSDBs)1
.
The LSDBs include information about the
connected networks and their costs2
. Therefore, when an OSPF adjacency is established, a router will
advertise a connected network to OSPF neighbors through DBD packets.
D is correct because when a static route to the 224.0.0.5 address is created, a router will advertise a
connected network to OSPF neighbors.
The 224.0.0.5 address is the multicast address for all OSPF
routers3
.
A static route to this address can be used to send OSPF hello packets to all OSPF neighbors
on a network segment3
.
This can be useful when the network segment does not support multicast or
when the router does not have an IP address on the segment3
.
When a static route to the 224.0.0.5
address is created, the router will send hello packets to this address and establish OSPF adjacencies
with other routers on the segment3
. As explained above, once an OSPF adjacency is formed, the
router will advertise a connected network to OSPF neighbors through DBD packets.
Question 10
What are two reasons for creating multiple areas in OSPF? (Choose two.)
- A. to reduce the convergence time
- B. to increase the number of adjacencies in the backbone
- C. to increase the size of the LSDB
- D. to reduce LSA flooding across the network
Answer:
AD
Explanation:
Option A is correct. Creating multiple areas in OSPF can help to reduce the convergence time . This is
because changes in one area do not affect other areas, so fewer routers need to run the SPF
algorithm in response to a change.
Option D is correct. Creating multiple areas in OSPF can help to reduce Link State Advertisement
(LSA) flooding across the network. This is because LSAs are not flooded out of their area of origin.
Question 11
After receiving a BGP route, which two conditions are verified by the receiving router to ensure that
the received route is valid? (Choose two)
- A. The AS-path length is greater than 0.
- B. The loops do not exist.
- C. The next hop is reachable.
- D. The local preference is greater than 0.
Answer:
BC
Explanation:
B is correct because the loops do not exist is one of the conditions that are verified by the receiving
router to ensure that the received BGP route is valid.
A loop in BGP means that a route has been
advertised by the same AS more than once, which can cause routing instability and inefficiency1
.
To
prevent loops, BGP uses the AS-path attribute, which lists the AS numbers that a route has traversed
from the origin to the destination2
.
The receiving router checks the AS-path attribute of the received
route and discards it if it finds its own AS number in the list2
. This way, BGP avoids accepting routes
that contain loops.
C is correct because the next hop is reachable is one of the conditions that are verified by the
receiving router to ensure that the received BGP route is valid.
The next hop is the IP address of the
next router that is used to forward packets to the destination network3
.
The receiving router checks
the next hop attribute of the received route and verifies that it has a valid route to reach it3
.
If the
next hop is not reachable, the received route is not usable and is rejected by the receiving router3
.
This way, BGP ensures that only feasible routes are accepted.
Question 12
Which statement is correct about the storm control feature?
- A. The storm control feature is enabled in the factory-default configuration on EX Series switches.
- B. The storm control feature requires a special license on EX Series switches.
- C. The storm control feature is not supported on aggregate Ethernet interfaces.
- D. The storm control configuration only applies to traffic being sent between the forwarding and control plane.
Answer:
A
Explanation:
Option A is correct.
The storm control feature is enabled in the factory-default configuration on EX
Series switches12
.
On EX2200, EX3200, EX3300, EX4200, and EX6200 switches, the factory default
configuration enables storm control for broadcast and unknown unicast traffic on all switch
interfaces2
.
On EX4300 switches, the factory default configuration enables storm control on all Layer
2 switch interfaces1
.
Option B is incorrect.
The storm control feature does not require a special license on EX Series
switches34
.
Option C is incorrect. There’s no information available that suggests the storm control feature is not
supported on aggregate Ethernet interfaces.
Option D is incorrect.
The storm control configuration applies to traffic at the ingress of an interface5
,
not just between the forwarding and control plane.
Question 13
Exhibit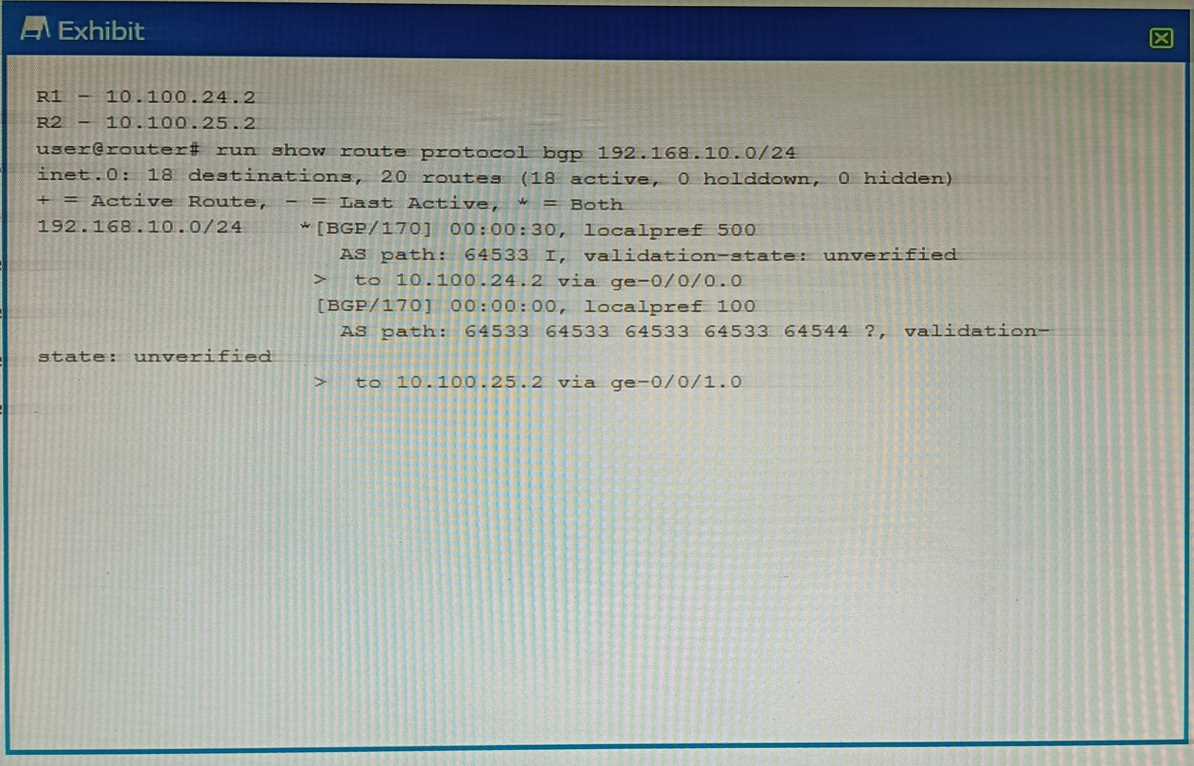
You are troubleshooting an issue where traffic to 192.168.10.0/24 is being sent to R1 instead of your
desired path through R2.
Referring to the exhibit, what is the reason for the problem?
- A. R2's route is not the best path due to loop prevention.
- B. R2's route is not the best path due to a lower origin code.
- C. R1's route is the best path due to a higher local preference
- D. R1's route is the best path due to the shorter AS path.
Answer:
C
Explanation:
The exhibit shows the output of the command show ip bgp, which displays information about the
BGP routes in the routing table1
. The output shows two routes for the destination 192.168.10.0/24,
one from R1 and one from R2.
The route from R1 has a local preference of 200, while the route from R2 has a local preference of
100.
Local preference is a BGP attribute that indicates the degree of preference for a route within an
autonomous system (AS)2
.
A higher local preference means a more preferred route2
.
BGP uses a best path selection algorithm to choose the best route for each destination among
multiple paths.
The algorithm compares different attributes of the routes in a specific order of
precedence3
.
The first attribute that is compared is weight, which is a Cisco-specific attribute that is
local to the router3
.
If the weight is equal or not set, the next attribute that is compared is local
preference3
.
In this case, both routes have the same weight of 0, which means that they are learned from external
BGP (eBGP) peers3
. Therefore, the next attribute that is compared is local preference.
Since R1’s
route has a higher local preference than R2’s route, it is chosen as the best path and installed in the
routing table3
. The other attributes, such as origin code and AS path, are not considered in this case.
Question 14
You want to ensure traffic is routed through a GRE tunnel.
In this scenario, which two statements will satisfy this requirement? (Choose two.)
- A. Tunnel endpoints must have a route that directs traffic into the tunnel.
- B. All intermediary devices must have a route to the tunnel endpoints.
- C. Keepalives must be used on stateless tunneling protocols.
- D. BFD must be used on the stateless tunneling protocols.
Answer:
AB
Explanation:
Option A is correct. For traffic to be sent through a GRE tunnel, there must be a route that directs the
traffic into the tunnel. This is typically accomplished through the use of a static route or a dynamic
routing protocol.
Option B is correct. All intermediary devices must have a route to the tunnel endpoints34. In real-
world scenarios, the tunnel endpoints for a tunnel going over the Internet must have globally
reachable internet addresses. Otherwise, intermediate routers in the Internet cannot forward the
tunneled packets.
Question 15
You want to use filter-based forwarding (FBF) on your Internet peering router to load-balance traffic
to two directly connected ISPs based on the source address.
Which two statements are correct in this scenario? (Choose two.)
- A. FBF uses the no-forwarding routing instance type.
- B. FBF uses the forwarding routing instance type.
- C. RIB groups are used to copy routes from the inet. o routing table.
- D. RIB groups are used to hide routes in the inet. 0 routing table.
Answer:
BC
Explanation:
Option B is correct.
Filter-based forwarding (FBF), also known as Policy Based Routing (PBR), uses the
forwarding routing instance type12
.
Option C is correct.
Routing Information Base (RIB) groups are used to copy routes from one routing
table to another34
.
In the context of FBF, RIB groups can be used to copy routes from the inet.0
routing table34
.
Option A is incorrect.
FBF does not use the no-forwarding routing instance type15
.
Option D is incorrect.
RIB groups are not used to hide routes in the inet.0 routing table34
.
They are
used to share or copy routes between different routing tables34
.