Juniper JN0-334 Exam Questions
Questions for the JN0-334 were updated on : Jun 25 ,2025
Page 1 out of 7. Viewing questions 1-15 out of 91
Question 1
What are two examples of RTOs? (Choose two.)
A. IPsec SA entries
B. session table entries
C. fabric link probes
D. control link heartbeats
Answer:
AB
The data plane software creates RTOs for UDP and TCP sessions and tracks state changes. It also
synchronizes traffic for IPv4 pass-through protocols such as Generic Routing Encapsulation (GRE) and
IPsec.
//www.juniper.net/documentation/en_US/junos/topics/topic-map/security-chassis-
cluster-data-plane-interfaces.html#id-45975
Question 2
Click the Exhibit button.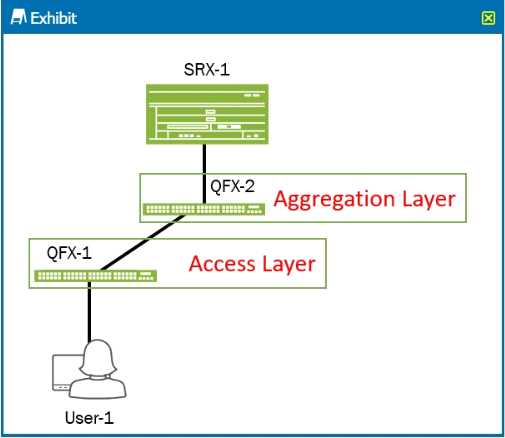
Referring to the exhibit, you want to deploy Sky ATP with Policy Enforcer to block infected hosts at
the access layer.
To complete this task, where should you configure the default gateway for the User-1 device?
A. the irb interface on QFX-2
B. the irb interface on QFX-1
C. the interface of QFX-1 that connects to User-1
D. the interface on SRX-1 that connects to QFX-2
Answer:
A
//www.juniper.net/documentation/en_US/release-independent/nce/topics/example/nce-162-
sdsn-example.html
Question 3
Click the Exhibit button.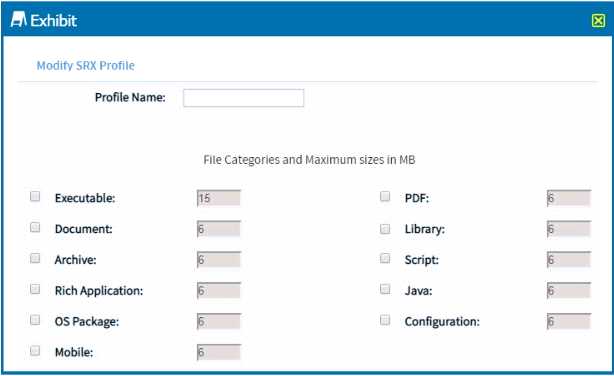
You need to have the JATP solution analyzer .jar, .xls, and .doc files.
Referring to the exhibit, which two file types must be selected to accomplish this task? (Choose two.)
A. Java
B. library
C. document
D. executable
Answer:
AC
//www.juniper.net/documentation/en_US/release-independent/sky-
atp/topics/reference/general/sky-atp-profile-overview.html
Question 4
Which three features are parts of Juniper Networks’ AppSecure suite? (Choose three.)
- A. AppQoE
- B. APBR
- C. Secure Application Manager
- D. AppQoS
- E. AppFormix
Answer:
ABD
Reference:
https://www.juniper.net/documentation/en_US/junos/information-products/pathway-
pages/security/security
- application-identification.pdf
Question 5
Which two statements are correct about server-protection SSP proxy? (Choose two.)
A. The server-protection SSL proxy intercepts the server certificate.
B. The server-protection SSL proxy is also known as SSL reverse proxy.
C. The server-protection SSL proxy forwards the server certificate after modification.
D. The server-protection SSL proxy acts as the server from the clients perspective.
Answer:
BD
//www.juniper.net/documentation/en_US/junos/topics/topic-map/security-ssl-proxy.html
Question 6
Which statement is true about high availability (HA) chassis clusters for the SRX Series device?
- A. Cluster nodes require an upgrade to HA compliant Routing Engines.
- B. Cluster nodes must be connected through a Layer 2 switch.
- C. There can be active/passive or active/active clusters.
- D. HA clusters must use NAT to prevent overlapping subnets between the nodes.
Answer:
C
Question 7
What are two types of attack objects used by IPS on SRX Series devices? (Choose two.)
- A. protocol anomaly-based attacks
- B. spam-based attacks
- C. signature-based attacks
- D. DDoS-based attacks
Answer:
AC
Question 8
When considering managed sessions, which configuration parameter determines how full the
session table must be to implement the early age-out function? (Choose two)
- A. session service timeout
- B. high waremark
- C. low watermark
- D. policy rematch
Answer:
AB
Question 9
You are asked to improve resiliency for individual redundancy groups in an SRX4600 chassis cluster.
Which two features would accomplish this task? (Choose two.)
- A. IP address monitoring
- B. control link recovery
- C. interface monitoring
- D. dual fabric links
Answer:
BD
Question 10
What are two elements of a custom IDP/IPS attack object? (Choose two.)
- A. the attack signature
- B. the severity of the attack
- C. the destination zone
- D. the exempt rulebase
Answer:
AB
Question 11
Click the Exhibit button.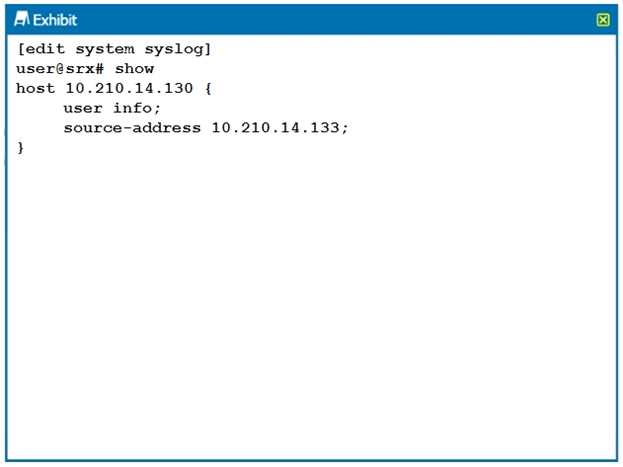
Referring to the configuration shown in the exhibit, which two statements are true? (Choose two.)
A. The log is being stored on the local Routing Engine.
B. The log is being sent to a remote server.
C. The syslog is configured for a user facility.
D. The syslog is configured for an info facility.
Answer:
BC
//www.juniper.net/documentation/en_US/junos/topics/reference/configuration-
statement/syslog-edit-system.html
Question 12
Your network uses a remote e-mail server that is used to send and receive e-mails for your users.
In this scenario, what should you do to protect users from receiving malicious files thorugh e-mail?
- A. Deploy Sky ATP IMAP e-mail protection
- B. Deploy Sky ATP MAPI e-mail protection
- C. Deploy Sky ATP SMTP e-mail protection
- D. Deploy Sky ATP POP3 e-mail protection
Answer:
C
Question 13
Which two statements are true about virtualized SRX Series devices? (Choose two.)
A. vSRX cannot be deployed in transparent mode.
B. cSRX can be deployed in routed mode.
C. cSRX cannot be deployed in routed mode.
D. vSRX can be deployed in transparent mode.
Answer:
BD
//www.juniper.net/documentation/en_US/csrx/information-products/pathway-pages/security-
csrx-contrail-guide-pwp.pdf
Question 14
A routing change occurs on an SRX Series device that involves choosing a new egress interface.
In this scenario, which statement is true for all affected current sessions?
A. The current session are torn dowm only if the policy-rematch option has been enabled.
B. The current sessions do not change.
C. The current sessions are torn down and go through first path processing based on the new route.
D. The current sessions might change based on the corresponding security policy.
Answer:
B
//forums.juniper.net/t5/ScreenOS-Firewalls-NOT-SRX/Affect-of-Route-change-on-Session/m-
p/27810#M11385
Question 15
What information does JIMS collect from domain event log sources? (Choose two.)
- A. For user login events, JIMS collects the username and group membership information.
- B. For device login events. JIMS collects the devide IP address and operating system version.
- C. For device login events, JIMS collects the device IP address and machine name information.
- D. For user login events, JIMS collects the login source IP address and username information.
Answer:
CD