Juniper JN0-1302 Exam Questions
Questions for the JN0-1302 were updated on : Jun 26 ,2025
Page 1 out of 7. Viewing questions 1-15 out of 96
Question 1
Your data center design must ensure that no access switch can become a single of failure.
Which two actions will satisfy this requirement? (Choose two.)
- A. Use an MC-LAG between two access switches and each server.
- B. Use a LAG between each server and two or more members of a Virtual Chassis.
- C. Use a MC-LAG between two upstream distribution switches and each access switch.
- D. Use a LAG between each access switch and a VRRP interface on a distribution switch.
Answer:
A, C
Question 2
Which two statements describe CoS? (Choose two.)
- A. CoS creates an end-to-end guaranteed bandwidth reservation
- B. CoS can be used to differentiate traffic for different customers.
- C. CoS does not create additional bandwidth.
- D. CoS does not protect sensitive traffic flows
Answer:
BC
Question 3
Exhibit.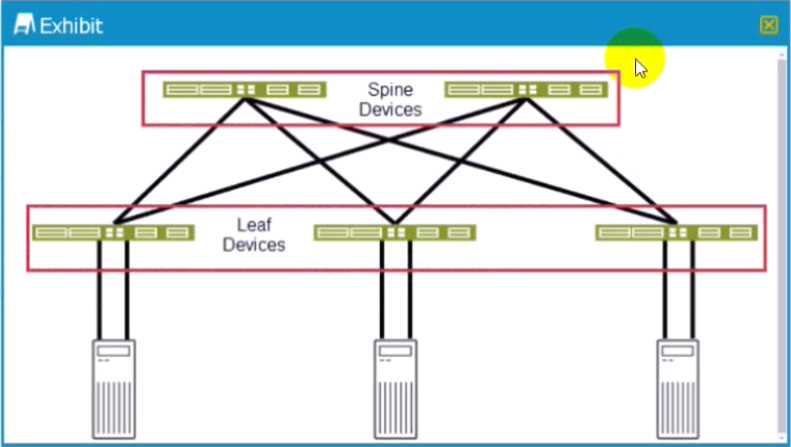
Referring to the exhibit, which two statements are true? (Choose two)
- A. You should use CoS multifield classifiers for traffic coming into the leaf devices from the servers
- B. You should use CoS BA classifiers for traffic leaving the spine devices and going to the leaf devices
- C. You should use CoS BA classifiers for traffic coming into the spine devices from the leaf devices
- D. You should use CoS multifield classifiers for traffic leaving the leaf devices and going to the spine devices
Answer:
BD
Question 4
Exhibit.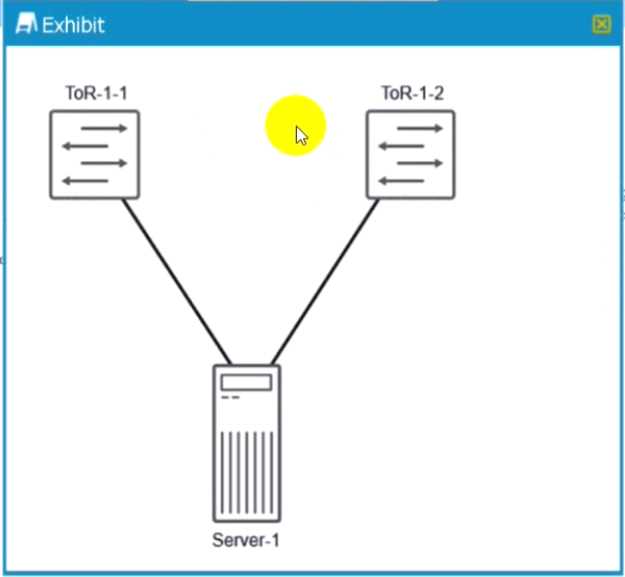
You are designing a data center where all your servers in each rack will be connected to two top-of-
rack (ToR) switches using Layer 2 as shown in the exhibit You must implement a high availability
solution that maintains link layer connectivity to each server when one of the ToR switches fails
in this scenario, which solution will accomplish this task?
- A. VRRP
- B. LAG
- C. GRES with NSB
- D. MC-LAG
Answer:
D
Question 5
You must design a data center (DC) connectivity solution for four data centers located in the US.
Europe, Africa, and China Which three statements are correct in this scenario? (Choose three)
- A. LDP Layer 2 circuits team MAC addresses in the data plane.
- B. PE routers in an EVPN environment advertise MAC addresses using BGP
- C. EVPN can provide connectivity for four or more DC deployments
- D. VPLS can provide connectivity for four or more DC deployments
- E. BGP Layer 2 VPNs are required due to latency requirements
Answer:
BCD
Question 6
Exhibit.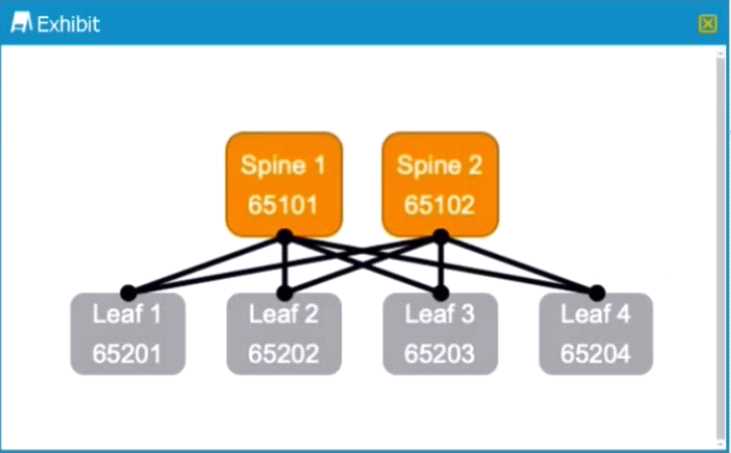
For a fully configured and functional IP fabnc underlay as shown in the exhibit, how many external
BGP neighbors are expected to be in the established state for Spine 1?
- A. 5
- B. 2
- C. 4
- D. 3
Answer:
C
Question 7
Which two characteristics describe a one-arm firewall deployment? (Choose two )
- A. All traffic passes through the firewall before passing through the core and aggregation tiers.
- B. The flexibility of selective services on the firewall is reduced
- C. Select traffic is directed to or bypasses the firewall
- D. The number of interfaces required for the infrastructure increases
Answer:
B, C
Question 8
Within a customer's data center, one departmental server is transmitting all of its network traffic
marked with an IP precedence value of 6 The ingress switch must change this precedence before
forwarding it to the rest of the network.
Which CoS feature would be used to accomplish this task?
- A. multifield classification
- B. rewrite rules
- C. class-based forwarding
- D. behavior aggregate classification
Answer:
B
Question 9
Which two Junos components does cRPD contain? (Choose two.)
- A. Kubernetes
- B. RIB
- C. Kernel
- D. MGD
Answer:
BD
Question 10
When using VPLS for a Data Center Interconnect, which statement about MAC learning is correct?
- A. Management plane MAC learning is used
- B. Data plane MAC learning is used.
- C. MAC learning is not used.
- D. Control plane MAC learning is used
Answer:
B
Question 11
You want to protect a hypervisor in your data center with a security solution that is installed on the
hypervisor and provides firewall protection to applications Traffic to one of the virtual servers must
be subject to a NAT policy before communicating with the virtual server
Which two solutions would you use to satisfy this requirement? (Choose two.)
- A. vSRX
- B. ATP Cloud
- C. vQFX
- D. cSRX
Answer:
A, D
Question 12
You are asked to create an underlay network that will scale from a small system to a large system and
can be integrated into a Contrail solution In this scenario, which protocol satisfies these
requirements'5
- A. EVPN
- B. VXLAN
- C. BGP
- D. MPLS
Answer:
C
Question 13
What are two elements of data center security? (Choose two.)
- A. DDoS protection
- B. segmentation with VLANs in hypervisors
- C. ATP Cloud advanced anti-malware
- D. JIMS for user identify and management
Answer:
A, C
Question 14
You must implement high availability features in the design for a data center. Every network device in
this part of the data center only has one routing engine. Which high availability feature should you
use in this scenario?
- A. GRES
- B. NSB
- C. graceful restart
- D. NSR
Answer:
C
Question 15
During a design requirements gathering meeting for a new data center, your customer indicates that
traffic to and from corporate HR systems is highly sensitive and mat the network design should
ensure that these systems are protected from unauthorized access
Which three design actions would satisfy this requirement? (Choose three.)
- A. Put all HR systems in dedicated racks.
- B. Enable a dedicated VLAN for HR systems.
- C. Use FBF to steer HR traffic to security devices.
- D. Place HR systems in a unique VR.
- E. Disable routing to and from HR systems.
Answer:
B, C, D