isaca CCAK Exam Questions
Questions for the CCAK were updated on : Jul 01 ,2025
Page 1 out of 9. Viewing questions 1-15 out of 126
Question 1
Which of the following is a cloud-specific security standard?
- A. ISO27017
- B. ISO27701
- C. ISO22301
- D. ISO14001
Answer:
A
Explanation:
Reference:
https://en.wikipedia.org/wiki/ISO/IEC_27017#:~:text=ISO%2FIEC%2027017%20is%20a,the%20risk%20of%20security%20p
roblems
Question 2
A cloud service provider does not allow audits using automated tools as these tools could be considered destructive
techniques for the cloud environment. Which of the following aspects of the audit will be constrained?
- A. Purpose
- B. Objectives
- C. Nature of relationship
- D. Scope
Answer:
B
Explanation:
Reference: https://www.isaca.org/-/media/files/isacadp/project/isaca/articles/journal/2018/volume-5/journal-volume-5-2018
Question 3
Which of the following is MOST important to consider when an organization is building a compliance program for the cloud?
- A. The rapidly changing service portfolio and architecture of the cloud.
- B. Cloud providers should not be part of the compliance program.
- C. The fairly static nature of the service portfolio and architecture of the cloud.
- D. The cloud is similar to the on-premise environment in terms of compliance.
Answer:
A
Question 4
Which of the following should be the FIRST step to establish a cloud assurance program during a cloud migration?
- A. Design
- B. Stakeholder identification
- C. Development
- D. Risk assessment
Answer:
C
Question 5
Which of the following is the MOST feasible way to validate the performance of CSPs for the delivery of technology
resources?
- A. Cloud compliance program
- B. Legacy IT compliance program
- C. Internal audit program
- D. Service organization controls report
Answer:
D
Question 6
Which of the following defines the criteria designed by the American Institute of Certified Public Accountants (AICPA) to
specify trusted services?
- A. Security, confidentiality, availability, privacy and processing integrity
- B. Security, applicability, availability, privacy and processing integrity
- C. Security, confidentiality, availability, privacy and trustworthiness
- D. Security, data integrity, availability, privacy and processing integrity
Answer:
A
Explanation:
Reference:
https://us.aicpa.org/content/dam/aicpa/interestareas/frc/assuranceadvisoryservices/downloadabledocuments/trust-services-
criteria.pdf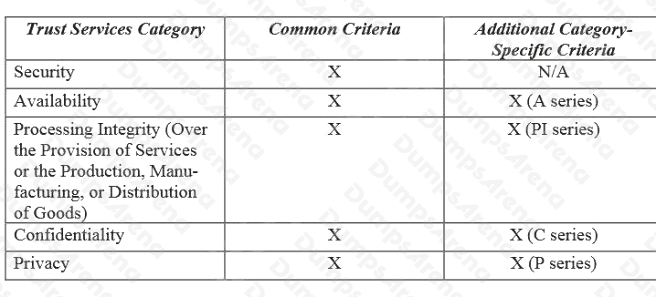
Question 7
Which of the following are the three MAIN phases of the cloud controls matrix (CCM) mapping methodology?
- A. Plan --> Develop --> Release
- B. Deploy --> Monitor --> Audit
- C. Initiation --> Execution --> Monitoring and Controlling
- D. Preparation --> Execution --> Peer Review and Publication
Answer:
D
Explanation:
Reference: https://docplayer.net/153476370-Methodology-for-the-mapping-of-the-cloud-controls-matrix-ccm.html (page 5)
Question 8
While performing the audit, the auditor found that an object storage bucket containing PII could be accessed by anyone on
the Internet. Given this discovery, what should be the most appropriate action for the auditor to perform?
- A. Highlighting the gap to the audit sponsor at the sponsor’s earliest possible availability
- B. Asking the organizations cloud administrator to immediately close the gap by updating the configuration settings and making the object storage bucket private and hence inaccessible from the Internet
- C. Documenting the finding in the audit report and sharing the gap with the relevant stakeholders
- D. Informing the organization’s internal audit manager immediately about the gap
Answer:
C
Explanation:
Reference: https://www.isaca.org/resources/isaca-journal/issues/2020/volume-1/is-audit-basics-the-components-of-the-it-
audit-report
Question 9
What should be an organizations control audit schedule of a cloud service providers business continuity plan and
operational resilience policy?
- A. Annual
- B. Quarterly
- C. Monthly
- D. Semi-annual
Answer:
A
Explanation:
Reference: https://www.isaca.org/why-isaca/about-us/newsroom/press-releases/2021/isaca-provides-guidance-around-eu-
proposed-digital-operational-resilience-act
Question 10
Which of the following attestation allows for immediate adoption of the Cloud Control Matrix (CCM) as additional criteria to
AICPA Trust Service Criteria and provides the flexibility to update the criteria as technology and market requirements
change?
- A. PC-IDSS
- B. CSA STAR Attestation
- C. MTCS
- D. BSI Criteria Catalogue C5
Answer:
B
Explanation:
Reference: https://www.sciencedirect.com/topics/computer-science/cloud-controls-matrix
Question 11
Which of the following standards is designed to be used by organizations for cloud services that intend to select controls
within the process of implementing an Information Security Management System based on ISO/IEC 27001?
- A. ISO/IEC 27017:2015
- B. CSA Cloud Control Matrix (CCM)
- C. NIST SP 800-146
- D. ISO/IEC 27002
Answer:
D
Explanation:
Reference: https://cyber.gc.ca/en/guidance/guidance-cloud-security-assessment-and-authorization-itsp50105
Question 12
To ensure that cloud audit resources deliver the best value to the organization, the PRIMARY step would be to:
- A. develop a cloud audit plan on the basis of a detailed risk assessment.
- B. schedule the audits and monitor the time spent on each audit.
- C. train the cloud audit staff on current technology used in the organization.
- D. monitor progress of audits and initiate cost control measures.
Answer:
A
Explanation:
It delivers value to the organization are the resources and efforts being dedicated to, and focused on, the higher-risk areas.
Question 13
Which of the following approaches encompasses social engineering of staff, bypassing of physical access controls and
penetration testing?
- A. Blue team
- B. White box
- C. Gray box
- D. Red team
Answer:
B
Explanation:
Reference: https://www.isaca.org/resources/isaca-journal/issues/2016/volume-5/planning-for-information-security-testinga-
practical-approach
Question 14
Which of the following aspects of risk management involves identifying the potential reputational harm and/or financial harm
when an incident occurs?
- A. Mitigations
- B. Residual risk
- C. Likelihood
- D. Impact Analysis
Answer:
D
Explanation:
Reference: https://compliancecosmos.org/chapter-5-step-three-determining-impact-occurrence
Question 15
Since CCM allows cloud customers to build a detailed list of requirements and controls to be implemented by the CSP as
part of their overall third-party risk management and procurement program, will CCM alone be enough to define all the items
to be considered when operating/using cloud services?
- A. No. CCM must be completed with definitions established by the CSP because of its relevance to service continuity.
- B. Yes. CCM suffices since it maps a huge library of widely accepted frameworks.
- C. Yes. When implemented in the right manner, CCM alone can help to measure, assess and monitor the risk associated with a CSP or a particular service.
- D. No. CCM can serve as a foundation for a cloud assessment program, but it needs to be completed with requirements applicable to each company.
Answer:
C