IBM C9530-001 Exam Questions
Questions for the C9530-001 were updated on : Jul 06 ,2025
Page 1 out of 8. Viewing questions 1-15 out of 121
Question 1
What is the first step in creating an IBM Integration Bus (IIB) based pattern?
- A. Every new application may require a pattern. So start with creating a pattern project.
- B. Identify an exemplar project and the variants to be replaced in the generated instance.
- C. Create a Java class that may be used in the pattern generation for changing the default behavior.
- D. Investigate how to create eclipse plugin since the IIB patterns are built as eclipse plugins for the toolkit.
Answer:
B
Explanation:
The three stages of creating a user-defined pattern are performed by the IBM Integration Bus
developer, the pattern author, and the pattern user.
References:
https://www.ibm.com/support/knowledgecenter/en/SSMKHH_9.0.0/com.ibm.etools.mft.doc/bc683
80_.htm
Question 2
How can WebSphere Service Registry & Repository (WSRR) information be pre-loaded into the IBM
Integration BUS (IIB) cache before sending any messages to the message flow?
- A. By subscribing to WSRR notifications.
- B. Adding predefinedCacheQueries to a custom policy within WSRR.
- C. By using the predefinedCacheQueries parameter in the Configurable Services for the broker.
- D. WSRR data cannot be loaded into the IBB cache without sending a message that accesses the WSRR node.
Answer:
C
Explanation:
Enabling cache preloading
After the query file is created and placed on the server, configure the broker to use the text file at
execution group start up. The change properties command will be used to achieve this and is
accomplished by running the following command:
Command to enable preloading of the WSRR cache from file
mqsichangeproperties <broker_name> -c ServiceRegistries -p
"<wsrr_query_text_file>" -o DefaultWSRR -n predefinedCacheQueries
Replace <broker_name> with the name of the broker that is being used. Replace
<wsrr_query_text_file> with the absolute file path location and name of the query file.
References:
https://www.ibm.com/developerworks/websphere/library/techarticles/1404_smithson7/1404_smithson7.html
Question 3
Which statement about the Cloned node is true?
- A. The Cloned node can be used to create reusable templates for Mapping node.
- B. The Cloned node can be used to create reusable templates for .NetInput node.
- C. The Cloned node can be used to create reusable templates for XSLTransform node.
- D. A new Cloned node can be used selected from a palette drawer and be assigned properties.
Answer:
B
Explanation:
Cloning a .NETInput node
You can reproduce parameters and attributes that you customized for a .NETInput node by creating a
Cloned node from it. The Cloned node has no special properties of its own, and cannot be created
from the palette drawer. You can create it only from an existing, configured .NETInput node. You
must have administrator privileges to be able to create a Cloned node.
References:
https://www.ibm.com/support/knowledgecenter/en/SSMKHH_9.0.0/com.ibm.etools.mft.doc/bc162
90_.htm
Question 4
When using the set of aggregation nodes, how does a developer tie the fan-out flow with the fan-in
flow when it is included within the same message flow?
- A. No properties need to be set, since the fan-out and fan-in flows are in the same messages flow.
- B. Set the Aggregate Name property of the AggregateReply Node to the same value that you set for the Aggregate Name property in the corresponding Collector Node.
- C. Set the Aggregate Name property of the AggregateReply Node to the same value that you set for the Aggregate Name property in the corresponding AggregateControl Node.
- D. Set the Aggregate Name property of the AggregateReply Node to the same value that you set for the Aggregate Name property on each of the corresponding AggregateRequest Nodes in the fan-out flow.
Answer:
C
Explanation:
Set the Aggregate Name property of the AggregateReply node to the same value that you set for the
Aggregate Name property in the corresponding AggregateControl node in the fan-out flow.
References:
https://www.ibm.com/support/knowledgecenter/en/SSMKHH_9.0.0/com.ibm.etools.mft.doc/ac123
11_.htm
Question 5
Which tool allows a configurable service to be imported and exported between systems?
- A. Broker Explorer
- B. Web User interface
- C. IBM Integration Toolkit
- D. IBM Integration Explorer
Answer:
D
Explanation:
Use the IBM Integration Explorer to export a configurable service to use on another integration node
(broker).
References:
https://www.ibm.com/support/knowledgecenter/en/SSMKHH_9.0.0/com.ibm.etools.mft.doc/be103
90_.htm
Question 6
A message flow reads messages from a queue Database Node fails to insert data in the table. If no
error handling and rollback is implemented in the message flow, which of the following statements is
true?
- A. The transaction is by default rolled back in a globally coordinated manner.
- B. The message fails the Input Node and cannot be propagated out of the Out terminal. The transaction is rolled back.
- C. The error is caught by the MQ Input Node and if the Catch terminal is not connected the message is rolled back into the queue.
- D. The message flow rolls back the database transaction but not the MQ transaction unless a XA coordinated transaction is configured.
Answer:
C
Explanation:
The MQInput node takes certain actions when handling errors with persistent and transactional
messages. The node attempts retry processing when a transactional message is rolled back to the
input queue. Non-transactional messages are not rolled back to the input queue when an exception
occurs.
If the MQInput node has successfully propagated the message to the out terminal and an exception
is thrown in the out flow, the message is returned to the MQInput node:
References:
https://www.ibm.com/support/knowledgecenter/SSMKHH_9.0.0/com.ibm.etools.mft.doc/ac00414_
.htm
Question 7
A developer creates a message flow that uses a DecisionService Node. Which command must the
developer use before deploying the message flow?
- A. mqsicvp
- B. mqsimode
- C. mqsichangebroker
- D. mqsichangeproperties
Answer:
B
Explanation:
Before you deploy message flows that contain a DecisionService node, you must enable the mode
extension by using the mqsimode command:
mqsimode -x DecisionServices
Question 8
In the User Trace output shows the following message:
2016-04-12 16:17:18.242605 5344 UserTrace BIP2539I: Node
'Reply.MapToRequestor':
Evaluating expression ''I + 1''
at
('MapToRequestor.CopyMessageHeaders', '6.14'). This resolved to ''1 + 1''. The result was ''2''.
What does 6.14 indicate here?
- A. Line 6, Column 14 in the CopyMessageHeaders node.
- B. Line 14, Column 6 in CopyMessageHeaders node.
- C. Column 6, line 14 in the CopyMessageHeaders function of MapToRequestor.
- D. Line 6, Column 14 in the CopyMessageHeaders function of MapToRequestor.
Answer:
D
Explanation:
References such as '6.14' apply to the row and column number within a function that specify the
location of the command that is being executed; in this case, row 6, column 14.
Example:
2005-07-12 16:17:18.2426055344 UserTrace BIP2539I: Node 'Reply.MapToRequestor':
Evaluating expression ''I'' at
('.MapToRequestor.CopyMessageHeaders',
'6.12'). This resolved to ''I''. The
result was ''1''.
References:
https://www.ibm.com/support/knowledgecenter/en/SSMKHH_9.0.0/com.ibm.etools.mft.doc/au143
20_.htm
Question 9
Which protocol for security is not supported by IBM Integration Bus?
- A. OAuth 2.0
- B. SAML assertion
- C. X.509 certificate
- D. User Id + Password
Answer:
A
Explanation:
Setting up message flow security
Set up security on a message flow to control access based on the identity of a message passing
through the message flow.
You can configure the broker to perform end-to-end processing of an identity carried in a message
through a message flow. Administrators can configure security at message flow level, controlling
access based on the identity flowed in a message. This security mechanism is independent of both
the transport and the message format.
To work with an identity, you must configure the policy sets and bindings for the relevant capabilities:
References:
https://www.ibm.com/support/knowledgecenter/en/SSMKHH_9.0.0/com.ibm.etools.mft.doc/ap041
70_.htm
Question 10
A developer is trying to investigate slow processing times with a specific message flow. What tool
would be used to investigate this?
- A. Service trace
- B. Debug mode
- C. Resource Statistics
- D. Accounting and Statistics
Answer:
C
Explanation:
You can use the message flow statistics data to help you identify aspects of a message flow that
might be reducing the performance of the flow, and to help you understand how you can optimize it.
If you detect that system resources are under pressure, you can examine the statistics collected by
the broker to assess whether the cause of the concern is the use of those resources by processes in
IBM Integration Bus.
References:
https://www.ibm.com/support/knowledgecenter/en/SSMKHH_9.0.0/com.ibm.etools.mft.doc/bj433
10_.htm
Question 11
A service interacts with a backend system which replies with a message correlation. When
processing request/response messages from the backend, no messages were received by the flow.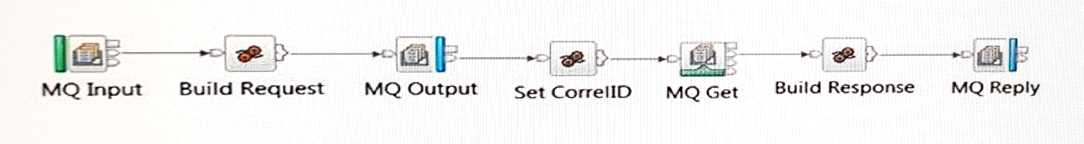
Which may be the probable cause of failure?
- A. The transaction was set to automatic on the MQOutput Node.
- B. The developer should have used the MQInput Node instead of the MQGet Node.
- C. The Integration Node is configured in a MQ cluster for load balancing and the object descriptor is set to the ReplyToQueueManager.
- D. The backend request/reply message processing can only be accomplished by breaking up the flow into two flows.
Answer:
A
Explanation:
When you define an MQOutput node, the option that you select for the Transaction Mode property
defines whether the message is written under sync point:
If you select Yes, the message is written under sync point (that is, within a WebSphere MQ unit of
work).
If you select Automatic (the default), the message is written under sync point if the incoming input
message is marked as persistent.
If you select No, the message is not written under sync point.
Question 12
A developer plans to create two new message flows. Flow1 that uses TimeoutControl and
TimeoutNotification nodes in Controlled mode, and Flow2 that uses only the TimeoutNotification
node in Automatic mode.
The Integration Node is installed on a system without IBM MQ installed. What problems will the
developer encounter?
- A. Flow1 will not deploy successfully. Flow2 will not deploy successfully.
- B. Flow1 will not deploy successfully. Flow2 will deploy and execute successfully.
- C. Flow1 will not deploy successfully. Flow2 will deploy successfully but will produce an error when execution is attempted.
- D. Flow1 will deploy successfully but produce an error when execution is attempted. Flow2 will deploy and execute successfully.
Answer:
B
Explanation:
Information about the state of in-flight messages is held on storage queues that are controlled by
WebSphere MQ, so you must install WebSphere MQ on the same computer as your integration node
if you want to use the capabilities provided by the TimeoutControl node.
References:
https://www.ibm.com/support/knowledgecenter/SSMKHH_10.0.0/com.ibm.etools.mft.doc/bc28150
_.htm
Question 13
While developing a REST API what node should a developer use to receive messages?
- A. MQInput Node
- B. JMSInput Node
- C. HTTPInput Node
- D. SOAPInput Node
Answer:
C
Explanation:
Each resource in the REST API has a set of operations that can be called by an HTTP client. An
operation in a REST API has a name and an HTTP method (such as GET, POST, or DELETE).
Use the HTTPInput node to receive an HTTP message from an HTTP client for processing by a
message flow.
References:
https://www.ibm.com/support/knowledgecenter/en/SSMKHH_10.0.0/com.ibm.etools.mft.doc/bi12
017_.htm
Question 14
An Integration Server contains a shared library with a common error handling routine. The shared
library is redeployed with an updated error handling routine with some new logging. When will the
applications that use the shared library start using the updated routine?
- A. Immediately.
- B. When the Integration Node is restarted.
- C. When the Integration Server is restarted.
- D. After each application that uses the shared library is redeployed.
Answer:
A
Explanation:
If a shared library is updated, the changes are immediately visible to all referencing applications.
If you want to deploy and manage just one copy of those common resources, use a shared library. A
shared library can be deployed directly to an integration server. Any application can reference the
resources in that deployed shared library.
References:
https://www.ibm.com/support/knowledgecenter/en/SSMKHH_10.0.0/com.ibm.etools.mft.doc/bc23
066_.htm
Question 15
Which statement regarding security profiles is true?
- A. Multiple security providers cannot be created in one security profile.
- B. A security profile can be created for LDAP or a WS-Trust V1.3 STS.
- C. The command mqsichangeconfigurableservice can be used to change a security profile.
- D. If WS-Trust v1.3.STS is selected for more than one operation, the WS-Trust URL must be different and unique for each of the operations.
Answer:
B
Explanation:
You can create a security profile for use with Lightweight Directory Access Protocol (LDAP) or a WS-
Trust V1.3 compliant security token server (STS), such as Tivoli Federated Identity Manager (TFIM)
V6.2. Support is also provided for TFIM V6.1, for compatibility with previous versions of IBM
Integration Bus. You can create the security profile by using either the mqsicreateconfigurableservice
command or an editor in the IBM Integration Explorer.
References:
https://www.ibm.com/support/knowledgecenter/en/SSMKHH_9.0.0/com.ibm.etools.mft.doc/ap041
70_.htm