HP HPE6-A78 Exam Questions
Questions for the HPE6-A78 were updated on : Jun 24 ,2025
Page 1 out of 4. Viewing questions 1-15 out of 60
Question 1
What is a vulnerability of an unauthenticated Dime-Heliman exchange?
- A. A hacker can replace the public values exchanged by the legitimate peers and launch an MITM attack.
- B. A brute force attack can relatively quickly derive Diffie-Hellman private values if they are able to obtain public values
- C. Diffie-Hellman with elliptic curve values is no longer considered secure in modem networks, based on NIST recommendations.
- D. Participants must agree on a passphrase in advance, which can limit the usefulness of Diffie- Hell man in practical contexts.
Answer:
A
Question 2
What is a difference between radius and TACACS+?
- A. RADIUS combines the authentication and authorization process while TACACS+ separates them.
- B. RADIUS uses TCP for Its connection protocol, while TACACS+ uses UDP tor its connection protocol.
- C. RADIUS encrypts the complete packet, white TACACS+ only offers partial encryption.
- D. RADIUS uses Attribute Value Pairs (AVPs) in its messages, while TACACS+ does not use them.
Answer:
A
Question 3
A company has an Aruba solution with a Mobility Master (MM) Mobility Controllers (MCs) and
campus Aps. What is one benefit of adding Aruba Airwave from the perspective of forensics?
- A. Airwave can provide more advanced authentication and access control services for the AmbaOS solution
- B. Airwave retains information about the network for much longer periods than ArubaOS solution
- C. Airwave is required to activate Wireless Intrusion Prevention (WIP) services on the ArubaOS solution
- D. AirWave enables low level debugging on the devices across the ArubaOS solution
Answer:
C
Question 4
What role does the Aruba ClearPass Device Insight Analyzer play in the Device Insight architecture?
- A. It resides in the cloud and manages licensing and configuration for Collectors
- B. It resides on-prem and provides the span port to which traffic is mirrored for deep analytics.
- C. It resides on-prem and is responsible for running active SNMP and Nmap scans
- D. It resides In the cloud and applies machine learning and supervised crowdsourcing to metadata sent by Collectors
Answer:
D
Question 5
What is a correct guideline for the management protocols that you should use on ArubaOS-Switches?
- A. Disable Telnet and use TFTP instead.
- B. Disable SSH and use https instead.
- C. Disable Telnet and use SSH instead
- D. Disable HTTPS and use SSH instead
Answer:
B
Question 6
Your ArubaoS solution has detected a rogue AP with Wireless intrusion Prevention (WIP). Which
information about the detected radio can best help you to locate the rogue device?
- A. the match method
- B. the detecting devices
- C. the match type
- D. the confidence level
Answer:
A
Question 7
What is a benefit of deploying Aruba ClearPass Device insight?
- A. Highly accurate endpoint classification for environments with many devices types, including Internet of Things (loT)
- B. visibility into devices' 802.1X supplicant settings and automated certificate deployment
- C. Agent-based analysts of devices' security settings and health status, with the ability to implement quarantining
- D. Simpler troubleshooting of ClearPass solutions across an environment with multiple ClearPass Policy Managers
Answer:
B
Question 8
What is a benefit or using network aliases in ArubaOS firewall policies?
- A. You can associate a reputation score with the network alias to create rules that filler traffic based on reputation rather than IP.
- B. You can use the aliases to translate client IP addresses to other IP addresses on the other side of the firewall
- C. You can adjust the IP addresses in the aliases, and the rules using those aliases automatically update
- D. You can use the aliases to conceal the true IP addresses of servers from potentially untrusted clients.
Answer:
A
Question 9
What is a guideline for managing local certificates on an ArubaOS-Switch?
- A. Before installing the local certificate, create a trust anchor (TA) profile with the root CA certificate for the certificate that you will install
- B. Install an Online Certificate Status Protocol (OCSP) certificate to simplify the process of enrolling and re-enrolling for certificate
- C. Generate the certificate signing request (CSR) with a program offline, then, install both the certificate and the private key on the switch in a single file.
- D. Create a self-signed certificate online on the switch because ArubaOS-Switches do not support CA- signed certificates.
Answer:
C
Question 10
What distinguishes a Distributed Denial of Service (DDoS) attack from a traditional Denial or service
attack (DoS)?
- A. A DDoS attack originates from external devices, while a DoS attack originates from internal devices
- B. A DDoS attack is launched from multiple devices, while a DoS attack is launched from a single device
- C. A DoS attack targets one server, a DDoS attack targets all the clients that use a server
- D. A DDoS attack targets multiple devices, while a DoS Is designed to Incapacitate only one device
Answer:
A
Question 11
You have an Aruba Mobility Controller (MC). for which you are already using Aruba ClearPass Policy
Manager (CPPM) to authenticate access to the Web Ul with usernames and passwords You now want
to enable managers to use certificates to log in to the Web Ul CPPM will continue to act as the
external server to check the names in managers' certificates and tell the MC the managers' correct
rote
in addition to enabling certificate authentication. what is a step that you should complete on the
MC?
- A. Verify that the MC has the correct certificates, and add RadSec to the RADIUS server configuration for CPPM
- B. install all of the managers' certificates on the MC as OCSP Responder certificates
- C. Verify that the MC trusts CPPM's HTTPS certificate by uploading a trusted CA certificate Also, configure a CPPM username and password on the MC
- D. Create a local admin account mat uses certificates in the account, specify the correct trusted CA certificate and external authentication
Answer:
A
Question 12
A company has Aruba Mobility Controllers (MCs). Aruba campus APs. and ArubaOS-CX switches. The
company plans to use ClearPass Policy Manager (CPPM) to classify endpoints by type The ClearPass
admins tell you that they want to run Network scans as part of the solution
What should you do to configure the infrastructure to support the scans?
- A. Create a TA profile on the ArubaOS-Switches with the root CA certificate for ClearPass's HTTPS certificate
- B. Create device fingerprinting profiles on the ArubaOS-Switches that include SNMP. and apply the profiles to edge ports
- C. Create remote mirrors on the ArubaOS-Swrtches that collect traffic on edge ports, and mirror it to CPPM's IP address.
- D. Create SNMPv3 users on ArubaOS-CX switches, and make sure that the credentials match those configured on CPPM
Answer:
B
Question 13
You have deployed a new Aruba Mobility Controller (MC) and campus APs (CAPs). One of the WLANs
enforces 802.IX authentication lo Aruba ClearPass Policy Manager {CPPM) When you test connecting
the client to the WLAN. the test falls You check Aruba ClearPass Access Tracker and cannot find a
record of the authentication attempt You ping from the MC to CPPM. and the ping is successful.
What is a good next step for troubleshooting?
- A. Renew CPPM's RADIUS/EAP certificate
- B. Reset the user credentials
- C. Check CPPM Event viewer.
- D. Check connectivity between CPPM and a backend directory server
Answer:
C
Question 14
Refer to the exhibit.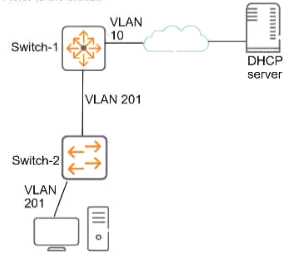
This company has ArubaOS-Switches. The exhibit shows one access layer switch, Swllcn-2. as an
example, but the campus actually has more switches. The company wants to slop any internal users
from exploiting ARP
What Is the proper way to configure the switches to meet these requirements?
- A. On Switch-1, enable ARP protection globally, and enable ARP protection on ail VLANs.
- B. On Switch-2, make ports connected to employee devices trusted ports for ARP protection
- C. On Swltch-2, enable DHCP snooping globally and on VLAN 201 before enabling ARP protection
- D. On Swltch-2, configure static PP-to-MAC bindings for all end-user devices on the network
Answer:
D
Question 15
Which attack is an example or social engineering?
- A. An email Is used to impersonate a Dank and trick users into entering their bank login information on a fake website page.
- B. A hacker eavesdrops on insecure communications, such as Remote Desktop Program (RDP). and discovers login credentials.
- C. A user visits a website and downloads a file that contains a worm, which sell-replicates throughout the network.
- D. An attack exploits an operating system vulnerability and locks out users until they pay the ransom.
Answer:
A