HP HPE6-A68 Exam Questions
Questions for the HPE6-A68 were updated on : Jun 28 ,2025
Page 1 out of 8. Viewing questions 1-15 out of 116
Question 1
Refer to the exhibit.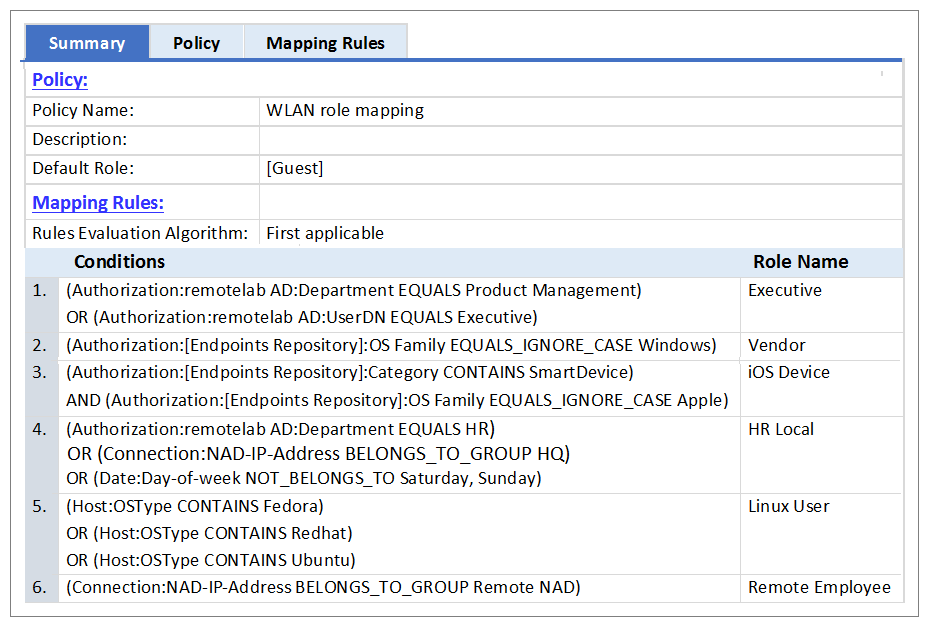
An AD users department attribute value is configured as QA. The user authenticates from a laptop
running MAC OS X.
Which role is assigned to the user in ClearPass?
- A. HR Local
- B. Remote Employee
- C. [Guest]
- D. Executive
- E. IOS Device
Answer:
C
Explanation:
None of the Listed Role Name conditions are met.
Question 2
Refer to the exhibit.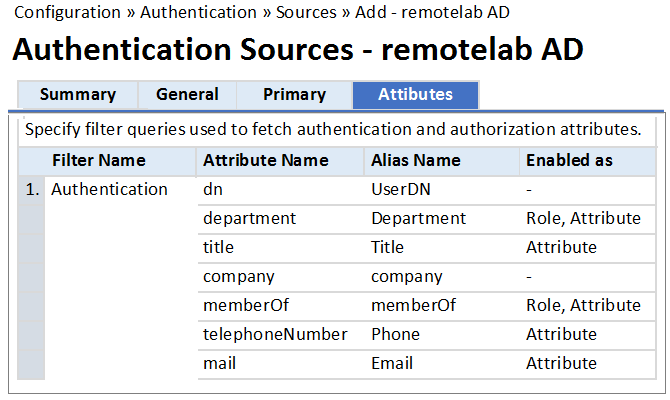
Based on the Attribute configuration shown, which statement accurately describes the status of
attribute values?
- A. Only the attribute values of department and memberOf can be used in role mapping policies.
- B. The attribute values of department, title, memberOf, telephoneNumber, and mail are directly applied as ClearPass.
- C. Only the attribute value of company can be used in role mapping policies, not the other attributes.
- D. The attribute values of department and memberOf are directly applied as ClearPass roles.
- E. Only the attribute values of title, telephoneNumber, and mail can be used in role mapping policies.
Answer:
D
Question 3
Which components can use Active Directory authorization attributes for the decision-making
process? (Select two.)
- A. Profiling policy
- B. Certificate validation policy
- C. Role Mapping policy
- D. Enforcement policy
- E. Posture policy
Answer:
C,D
Explanation:
C: Role Mappings Page - Rules Editor Page Parameters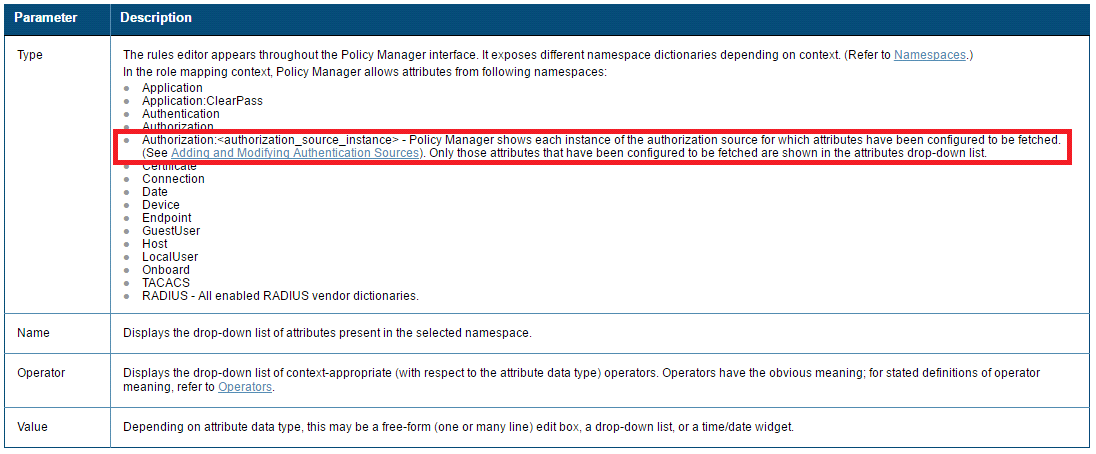
D: Enforcement Policy Attributes tab Parameters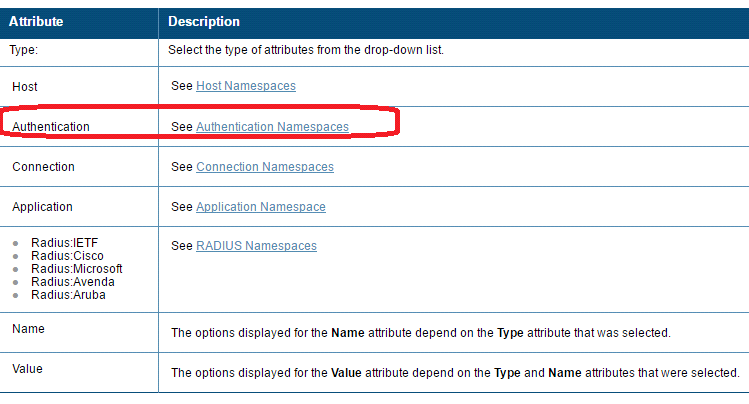
References:
http://www.arubanetworks.com/techdocs/ClearPass/Aruba_CPPMOnlineHelp/Content/CPPM_UserGuide/identity/RoleMappingPolicies.html
http://www.arubanetworks.com/techdocs/ClearPass/Aruba_CPPMOnlineHelp/Content/CPPM_User
Guide/PolicySim/PS_Enforcement_Policy.htm
Question 4
Refer to the exhibit.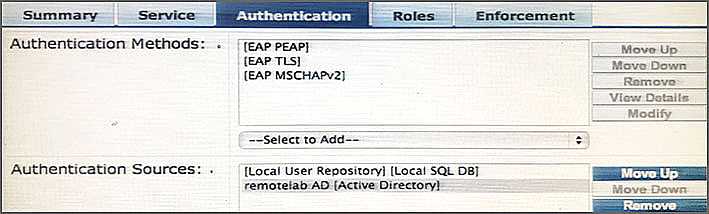
Based on the Authentication sources configuration shown, which statement accurately describes the
outcome if the user is not found?
- A. If the user is not found in the remotelab AD but is present in the local user repository, a reject message is sent back to the NAD.
- B. If the user is not found in the local user repository but is present in the remotelab AD, a reject message is sent back to the NAD.
- C. If the user is not found in the local user repository a reject message is sent back to the NAD.
- D. If the user is not found in the local user repository and remotelab AD, a reject message is sent back to the NAD.
- E. If the user is not found in the local user repository a timeout message is sent back to the NAD.
Answer:
D
Explanation:
Policy Manager looks for the device or user by executing the first filter associated with the
authentication source.
After the device or user is found, Policy Manager then authenticates this entity against this
authentication
source. The flow is outlined below:
* On successful authentication, Policy Manager moves on to the next stage of policy evaluation,
which
collects role mapping attributes from the authorization sources.
* Where no authentication source is specified (for example, for unmanageable devices), Policy
Manager
passes the request to the next configured policy component for this service.
* If Policy Manager does not find the connecting entity in any of the configured authentication
sources, it
rejects the request.
References: ClearPass Policy Manager 6.5 User Guide (October 2015), page 134
https://community.arubanetworks.com/aruba/attachments/aruba/SoftwareUserReferenceGuides/5
2/1/ClearPass%20Policy%20Manager%206.5%20User%20Guide.pdf
Question 5
Which authorization servers are supported by ClearPass? (Select two.)
- A. Aruba Controller
- B. LDAP server
- C. Cisco Controller
- D. Active Directory
- E. Aruba Mobility Access Switch
Answer:
B,D
Explanation:
Authentication Sources can be one or more instances of the following examples:
* Active Directory
* LDAP Directory
* SQL DB
* Token Server
* Policy Manager local DB
References: ClearPass Policy Manager 6.5 User Guide (October 2015), page 114
https://community.arubanetworks.com/aruba/attachments/aruba/SoftwareUserReferenceGuides/5
2/1/ClearPass%20Policy%20Manager%206.5%20User%20Guide.pdf
Question 6
Which CLI command is used to upgrade the image of a ClearPass server?
- A. Image update
- B. System upgrade
- C. Upgrade image
- D. Reboot
- E. Upgrade software
Answer:
B
Explanation:
When logged in as appadmin, you can manually install the Upgrade and Patch binaries imported via
the CLI using the
following commands:
* system update (for patches)
* system upgrade (for upgrades)
References: ClearPass Policy Manager 6.5 User Guide (October 2015), page 564
https://community.arubanetworks.com/aruba/attachments/aruba/SoftwareUserReferenceGuides/5
2/1/ClearPass%20Policy%20Manager%206.5%20User%20Guide.pdf
Question 7
Which steps are required to use ClearPass as a TACACS+ Authentication server for a network device?
(Select two.)
- A. Configure a TACACS Enforcement Profile on ClearPass for the desired privilege level.
- B. Configure a RADIUS Enforcement Profile on ClearPass for the desired privilege level.
- C. Configure ClearPass as an Authentication server on the network device.
- D. Configure ClearPass roles on the network device.
- E. Enable RADIUS accounting on the NAD.
Answer:
A,C
Explanation:
You need to make sure you modify your policy (Configuration Enforcement Policies Edit -
[Admin Network Login Policy]) and add your AD group settings in to the corresponding privilege
level.
Question 8
What are Operator Profiles used for?
- A. to enforce role based access control for Aruba Controllers
- B. to enforce role based access control for ClearPass Policy Manager admin users
- C. to enforce role based access control for ClearPass Guest Admin users
- D. to assign ClearPass roles to guest users
- E. to map AD attributes to admin privilege levels in ClearPass Guest
Answer:
C
Explanation:
An operator profile determines what actions an operator is permitted to take when using ClearPass
Guest.
References:
http://www.arubanetworks.com/techdocs/ClearPass/CPGuest_UG_HTML_6.5/Content/OperatorLog
ins/OperatorProfiles.htm
Question 9
Refer to the exhibit.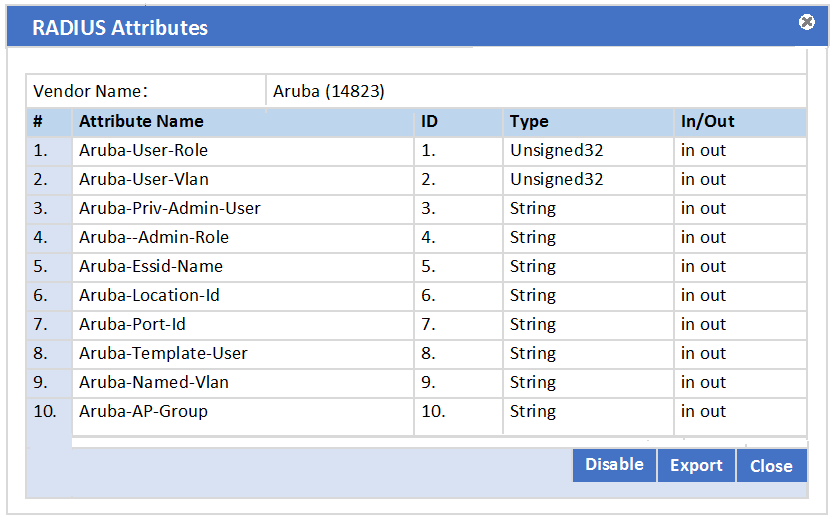
In the Aruba RADIUS dictionary shown, what is the purpose of the RADIUS attributes?
In the Aruba RADIUS dictionary shown, what is the purpose of the RADIUS attributes?
- A. to send information via RADIUS packets to Aruba NADs
- B. to gather and send Aruba NAD information to ClearPass
- C. to send information via RADIUS packets to clients
- D. to gather information about Aruba NADs for ClearPass
- E. to send CoA packets from ClearPass to the Aruba NAD
Answer:
C
Question 10
Refer to the exhibit.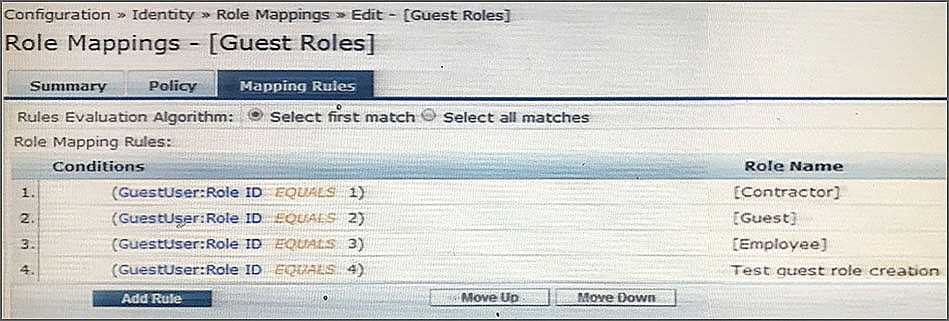
Based on the Guest Role Mapping Policy shown, what is the purpose of the Role Mapping Policy?
- A. to display a role name on the Self-registration receipt page
- B. to send a firewall role back to the controller based on the Guest User’s Role ID
- C. to assign Controller roles to guests
- D. to assign three roles of [Contractor], [Guest] and [Employee] to every guest user
- E. to create additional account roles for guest administrators to assign to guest accounts
Answer:
C
Question 11
A customer wants all guests who access a companys guest network to have their accounts approved
by the receptionist, before they are given access to the network.
How should the network administrator set this up in ClearPass? (Select two.)
- A. Enable sponsor approval confirmation in Receipt actions.
- B. Configure SMTP messaging in the Policy Manager.
- C. Configure a MAC caching service in the Policy Manager.
- D. Configure a MAC auth service in the Policy Manager.
- E. Enable sponsor approval in the captive portal authentication profile on the NAD.
Answer:
A,D
Explanation:
A: Sponsored self-registration is a means to allow guests to self-register, but not give them full access
until a sponsor (could even be a central help desk) has approved the request. When the registration
form is completed by the guest/user, an on screen message is displayed for the guest stating the
account requires approval.
Guests are disabled upon registration and need to wait on the receipt page for the confirmation until
the login button gets enabled.
D. Device Mac Authentication is designed for authenticating guest devices based on their MAC
address.
References: ClearPass Policy Manager 6.5 User Guide (October 2015), page 94
https://community.arubanetworks.com/aruba/attachments/aruba/SoftwareUserReferenceGuides/5
2/1/ClearPass%20Policy%20Manager%206.5%20User%20Guide.pdf
Question 12
Refer to the exhibit.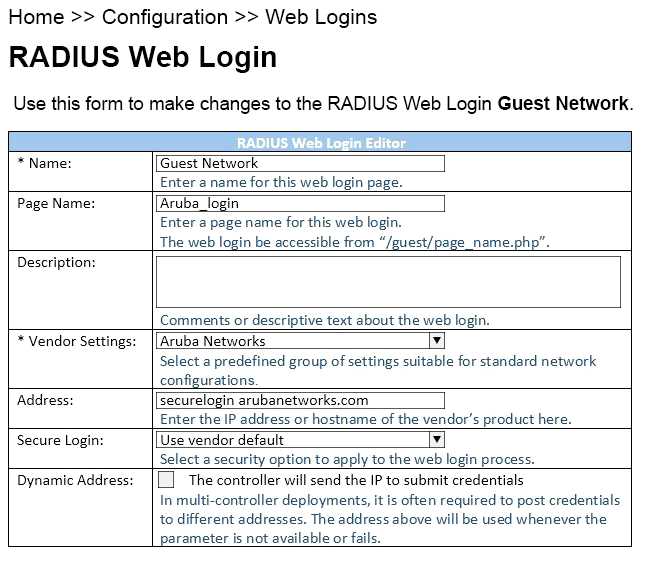
When configuring a Web Login Page in ClearPass Guest, the information shown is displayed.
What is the page name field used for?
- A. for forming the Web Login Page URL
- B. for Administrators to access the PHP page, but not guests
- C. for Administrators to reference the page only
- D. for forming the Web Login Page URL where Administrators add guest users
- E. for informing the Web Login Page URL and the page name that guests must configure on their laptop wireless supplicant.
Answer:
A
Explanation:
The Page Name is an identifier page name that will appear in the URL -- for example,
"/guest/page_name.php".
References:
http://www.arubanetworks.com/techdocs/ClearPass/CPGuest_UG_HTML_6.5/Content/Configuratio
n/CreateEditWebLogin.htm
Question 13
Refer to the exhibit.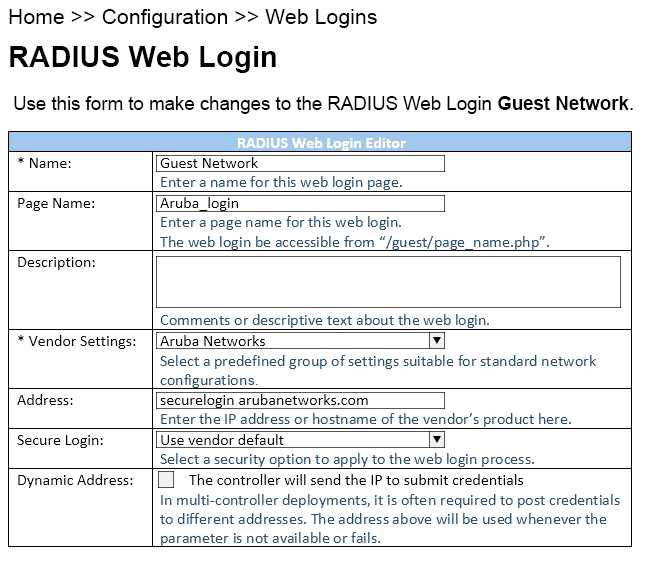
When configuring a Web Login Page in ClearPass Guest, the information shown is displayed.
What is the Address field value securelogin.arubanetworks.com used for?
- A. for ClearPass to send a TACACS+ request to the NAD
- B. for appending to the Web Login URL, before the page name
- C. for the client to POST the user credentials to the NAD
- D. for ClearPass to send a RADIUS request to the NAD
- E. for appending to the Web Login URL, after the page name.
Answer:
C
Question 14
Refer to the exhibit.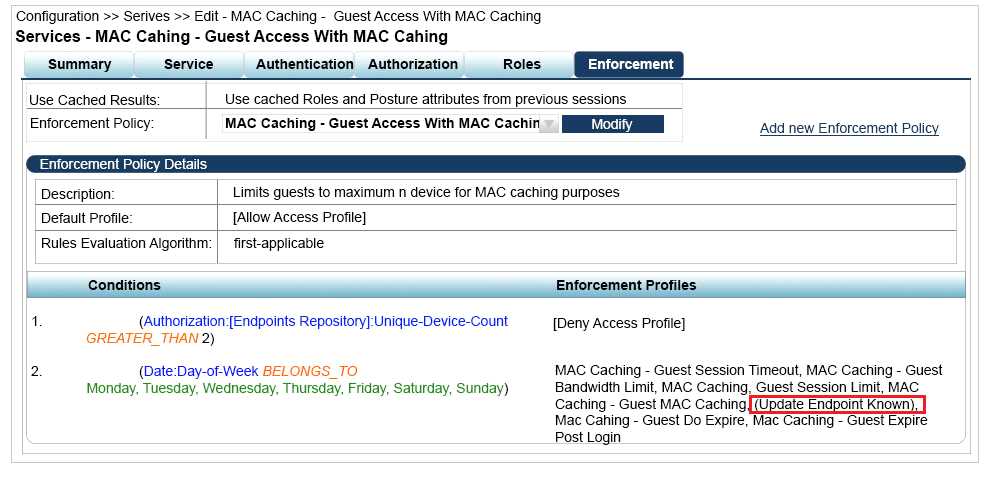
A guest connects to the Guest SSID and authenticates successfully using the guest.php web login
page.
Based on the MAC Caching service information shown, which statement about the guests MAC
address is accurate?
- A. It will be visible in the Guest User Repository with Unknown Status
- B. It will be deleted from the Endpoint table.
- C. It will be visible in the Guest User Repository with Known Status.
- D. It will be visible in the Endpoints table with Known Status.
- E. It will be visible in the Endpoints table with Unknown Status.
Answer:
D
Question 15
A university wants to deploy ClearPass with the Guest module. The university has two types that
need to use web login authentication. The first type of users are students whose accounts are in an
Active Directory server. The second type of users are friends of students who need to self-register to
access the network.
How should the service be set up in the Policy Manager for this network?
- A. Guest User Repository and Active Directory server both as authentication sources
- B. Active Directory server as the authentication source, and Guest User Repository as the authorization source
- C. Guest User Repository as the authentication source, and Guest User Repository and Active Directory server as authorization sources
- D. Either the Guest User Repository or Active Directory server should be the single authentication source
- E. Guest User Repository as the authentication source and the Active Directory server as the authorization source
Answer:
A