google PROFESSIONAL CLOUD SECURITY ENGINEER Exam Questions
Questions for the PROFESSIONAL CLOUD SECURITY ENGINEER were updated on : Jul 08 ,2025
Page 1 out of 9. Viewing questions 1-15 out of 134
Question 1
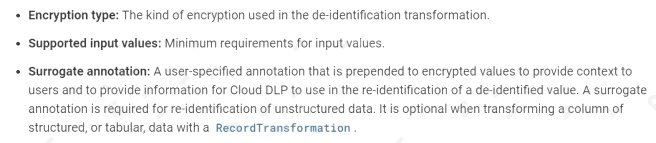
You are a member of your company's security team. You have been asked to reduce your Linux bastion host external attack
surface by removing all public IP addresses. Site Reliability Engineers (SREs) require access to the bastion host from public
locations so they can access the internal VPC while off-site. How should you enable this access?
- A. Implement Cloud VPN for the region where the bastion host lives.
- B. Implement OS Login with 2-step verification for the bastion host.
- C. Implement Identity-Aware Proxy TCP forwarding for the bastion host.
- D. Implement Google Cloud Armor in front of the bastion host.
Answer:
C
Explanation:
Reference: https://cloud.google.com/architecture/building-internet-connectivity-for-private-vms
Question 2
You are designing a new governance model for your organization's secrets that are stored in Secret Manager. Currently,
secrets for Production and Non-Production applications are stored and accessed using service accounts. Your proposed
solution must:
Provide granular access to secrets
Give you control over the rotation schedules for the encryption keys that wrap your secrets
Maintain environment separation Provide ease of management

Which approach should you take?
- A. 1. Use separate Google Cloud projects to store Production and Non-Production secrets. 2. Enforce access control to secrets using project-level identity and Access Management (IAM) bindings. 3. Use customer-managed encryption keys to encrypt secrets.
- B. 1. Use a single Google Cloud project to store both Production and Non-Production secrets. 2. Enforce access control to secrets using secret-level Identity and Access Management (IAM) bindings. 3. Use Google-managed encryption keys to encrypt secrets.
- C. 1. Use separate Google Cloud projects to store Production and Non-Production secrets. 2. Enforce access control to secrets using secret-level Identity and Access Management (IAM) bindings. 3. Use Google-managed encryption keys to encrypt secrets.
- D. 1. Use a single Google Cloud project to store both Production and Non-Production secrets. 2. Enforce access control to secrets using project-level Identity and Access Management (IAM) bindings. 3. Use customer-managed encryption keys to encrypt secrets.
Answer:
A
Question 3
A customer implements Cloud Identity-Aware Proxy for their ERP system hosted on Compute Engine. Their security team
wants to add a security layer so that the ERP systems only accept traffic from Cloud Identity-Aware Proxy.
What should the customer do to meet these requirements?
- A. Make sure that the ERP system can validate the JWT assertion in the HTTP requests.
- B. Make sure that the ERP system can validate the identity headers in the HTTP requests.
- C. Make sure that the ERP system can validate the x-forwarded-for headers in the HTTP requests.
- D. Make sure that the ERP system can validate the user’s unique identifier headers in the HTTP requests.
Answer:
A
Question 4
A customer wants to deploy a large number of 3-tier web applications on Compute Engine.
How should the customer ensure authenticated network separation between the different tiers of the application?
- A. Run each tier in its own Project, and segregate using Project labels.
- B. Run each tier with a different Service Account (SA), and use SA-based firewall rules.
- C. Run each tier in its own subnet, and use subnet-based firewall rules.
- D. Run each tier with its own VM tags, and use tag-based firewall rules.
Answer:
C
Question 5
You plan to deploy your cloud infrastructure using a CI/CD cluster hosted on Compute Engine. You want to minimize the risk
of its credentials being stolen by a third party. What should you do?
- A. Create a dedicated Cloud Identity user account for the cluster. Use a strong self-hosted vault solution to store the user's temporary credentials.
- B. Create a dedicated Cloud Identity user account for the cluster. Enable the constraints/iam.disableServiceAccountCreation organization policy at the project level.
- C. Create a custom service account for the cluster Enable the constraints/iam.disableServiceAccountKeyCreation organization policy at the project level
- D. Create a custom service account for the cluster Enable the constraints/iam.allowServiceAccountCredentialLifetimeExtension organization policy at the project level.
Answer:
D
Explanation:
Reference: https://cloud.google.com/resource-manager/docs/organization-policy/restricting-service-accounts
Question 6
When creating a secure container image, which two items should you incorporate into the build if possible? (Choose two.)
- A. Ensure that the app does not run as PID 1.
- B. Package a single app as a container.
- C. Remove any unnecessary tools not needed by the app.
- D. Use public container images as a base image for the app.
- E. Use many container image layers to hide sensitive information.
Answer:
B C
Explanation:
Reference: https://cloud.google.com/solutions/best-practices-for-building-containers
Question 7
You need to follow Google-recommended practices to leverage envelope encryption and encrypt data at the application
layer.
What should you do?
- A. Generate a data encryption key (DEK) locally to encrypt the data, and generate a new key encryption key (KEK) in Cloud KMS to encrypt the DEK. Store both the encrypted data and the encrypted DEK.
- B. Generate a data encryption key (DEK) locally to encrypt the data, and generate a new key encryption key (KEK) in Cloud KMS to encrypt the DEK. Store both the encrypted data and the KEK.
- C. Generate a new data encryption key (DEK) in Cloud KMS to encrypt the data, and generate a key encryption key (KEK) locally to encrypt the key. Store both the encrypted data and the encrypted DEK.
- D. Generate a new data encryption key (DEK) in Cloud KMS to encrypt the data, and generate a key encryption key (KEK) locally to encrypt the key. Store both the encrypted data and the KEK.
Answer:
A
Explanation:
Reference: https://cloud.google.com/kms/docs/envelope-encryption
Question 8
You want to evaluate GCP for PCI compliance. You need to identify Googles inherent controls.
Which document should you review to find the information?
- A. Google Cloud Platform: Customer Responsibility Matrix
- B. PCI DSS Requirements and Security Assessment Procedures
- C. PCI SSC Cloud Computing Guidelines
- D. Product documentation for Compute Engine
Answer:
C
Explanation:
Reference: https://cloud.google.com/solutions/pci-dss-compliance-in-gcp
Question 9
What are the steps to encrypt data using envelope encryption?
- A. Generate a data encryption key (DEK) locally.
- B. Generate a key encryption key (KEK) locally.
- C. Generate a data encryption key (DEK) locally. Encrypt data with the DEK.
- D. Generate a key encryption key (KEK) locally.
Answer:
C
Explanation:
Reference: https://cloud.google.com/kms/docs/envelope-encryption
Question 10
You need to set up two network segments: one with an untrusted subnet and the other with a trusted subnet. You want to
configure a virtual appliance such as a next-generation firewall (NGFW) to inspect all traffic between the two network
segments. How should you design the network to inspect the traffic?
- A. 1. Set up one VPC with two subnets: one trusted and the other untrusted. 2. Configure a custom route for all traffic (0.0.0.0/0) pointed to the virtual appliance.
- B. 1. Set up one VPC with two subnets: one trusted and the other untrusted. 2. Configure a custom route for all RFC1918 subnets pointed to the virtual appliance.
- C. 1. Set up two VPC networks: one trusted and the other untrusted, and peer them together. 2. Configure a custom route on each network pointed to the virtual appliance.
- D. 1. Set up two VPC networks: one trusted and the other untrusted. 2. Configure a virtual appliance using multiple network interfaces, with each interface connected to one of the VPC networks.
Answer:
B
Question 11
An employer wants to track how bonus compensations have changed over time to identify employee outliers and correct
earning disparities. This task must be performed without exposing the sensitive compensation data for any individual and
must be reversible to identify the outlier.
Which Cloud Data Loss Prevention API technique should you use to accomplish this?
- A. Generalization
- B. Redaction
- C. CryptoHashConfig
- D. CryptoReplaceFfxFpeConfig
Answer:
B
Question 12
A business unit at a multinational corporation signs up for GCP and starts moving workloads into GCP. The business unit
creates a Cloud Identity domain with an organizational resource that has hundreds of projects.
Your team becomes aware of this and wants to take over managing permissions and auditing the domain resources.
Which type of access should your team grant to meet this requirement?
- A. Organization Administrator
- B. Security Reviewer
- C. Organization Role Administrator
- D. Organization Policy Administrator
Answer:
C
Question 13
You want to limit the images that can be used as the source for boot disks. These images will be stored in a dedicated
project.
What should you do?
- A. Use the Organization Policy Service to create a compute.trustedimageProjects constraint on the organization level. List the trusted project as the whitelist in an allow operation.
- B. Use the Organization Policy Service to create a compute.trustedimageProjects constraint on the organization level. List the trusted projects as the exceptions in a deny operation.
- C. In Resource Manager, edit the project permissions for the trusted project. Add the organization as member with the role: Compute Image User.
- D. In Resource Manager, edit the organization permissions. Add the project ID as member with the role: Compute Image User.
Answer:
B
Explanation:
Reference: https://cloud.google.com/compute/docs/images/restricting-image-access
Question 14
Your company operates an application instance group that is currently deployed behind a Google Cloud load balancer in us-
central-1 and is configured to use the Standard Tier network. The infrastructure team wants to expand to a second Google
Cloud region, us-east-2. You need to set up a single external IP address to distribute new requests to the instance groups in
both regions.
What should you do?
- A. Change the load balancer backend configuration to use network endpoint groups instead of instance groups.
- B. Change the load balancer frontend configuration to use the Premium Tier network, and add the new instance group.
- C. Create a new load balancer in us-east-2 using the Standard Tier network, and assign a static external IP address.
- D. Create a Cloud VPN connection between the two regions, and enable Google Private Access.
Answer:
A
Question 15
You are working with protected health information (PHI) for an electronic health record system. The privacy officer is
concerned that sensitive data is stored in the analytics system. You are tasked with anonymizing the sensitive data in a way
that is not reversible. Also, the anonymized data should not preserve the character set and length. Which Google Cloud
solution should you use?
- A. Cloud Data Loss Prevention with deterministic encryption using AES-SIV
- B. Cloud Data Loss Prevention with format-preserving encryption
- C. Cloud Data Loss Prevention with cryptographic hashing
- D. Cloud Data Loss Prevention with Cloud Key Management Service wrapped cryptographic keys
Answer:
D
Explanation:
Reference: https://cloud.google.com/dlp/docs/pseudonymization