giac GSEC Exam Questions
Questions for the GSEC were updated on : Feb 20 ,2026
Page 1 out of 26. Viewing questions 1-15 out of 385
Question 1
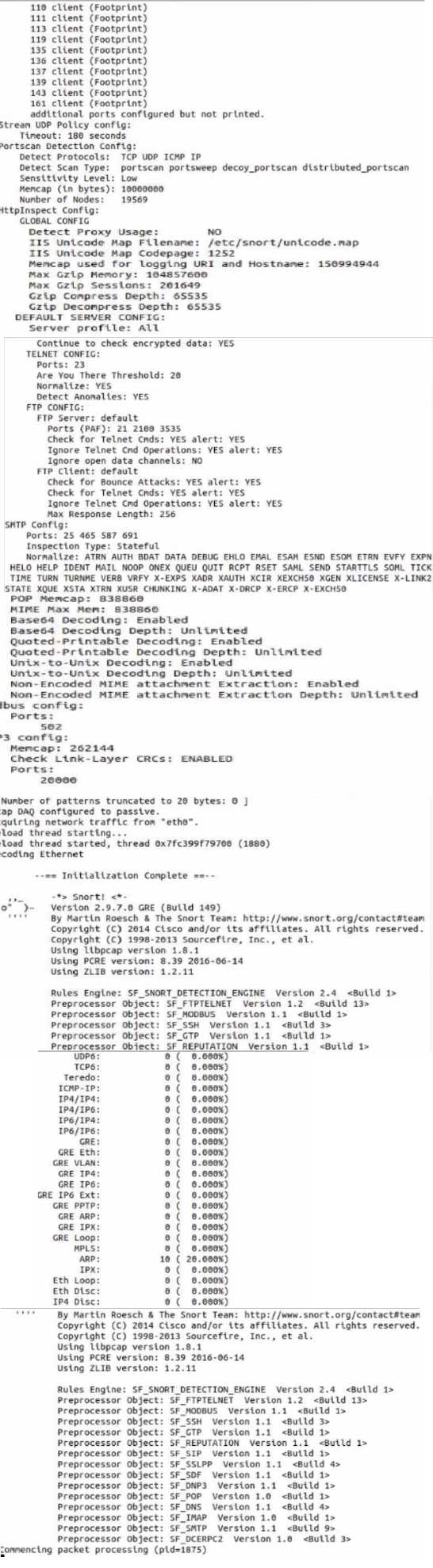
Use sudo to launch Snort with the, /etc /snort /snort.conf file In full mode to generate alerts based
on incoming traffic to echo. What is the source IP address of the traffic triggering an alert with a
destination port of 156?
Note: Snort Is configured to exit after It evaluates 50 packets.
- A. 192.168.^.30
- B. 10.72.101.210
- C. 10.10.28.19
- D. 10.11.10.11
- E. 10.10.10.66
- F. 192.168.87.68
- G. 10.12.10.112
- H. 10.11.12.13
- I. 10.10.201.150
- J. 10.10.199.146
Answer:
I
Question 2
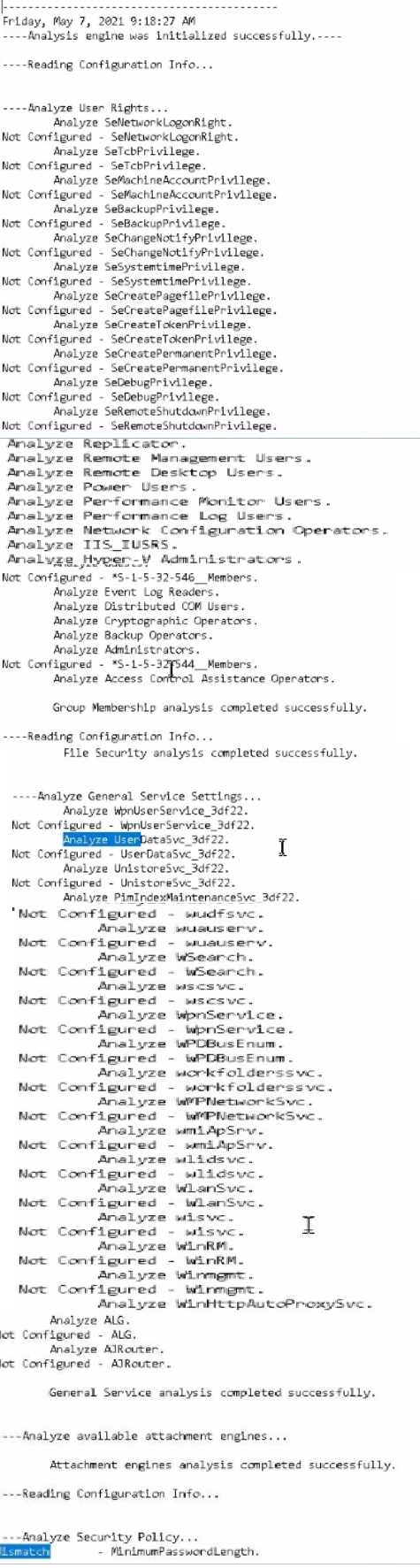
Using PowerShell ISE running as an Administrator, navigate to the
C:\hlindows\security\tevplatesdirectory
. Use secedit.exe in analyze mode to compare the temp.sdb
and uorkstdtionSecureTmplate.inf files, and output the findings to a file called log.txt. Which
configuration setting under Analyze User Rights reports a mismatch?
Hints:
Use files located in the C \windows\security\templates\ directory
The log. txt file will be created in the directory the secedit.exe command is run from
- A. RemoteAccess
- B. •S-l-5-32-544__ Members
- C. Enable Admin Account
- D. UseManger
- E. AuditSystemEvents
- F. AuditDSAccess.
- G. SeSecurityPrivilege
- H. SeinteractivelogonRight
- I. SeServiceLogonRight:
- J. lockoutBadCount
Answer:
J
Question 3
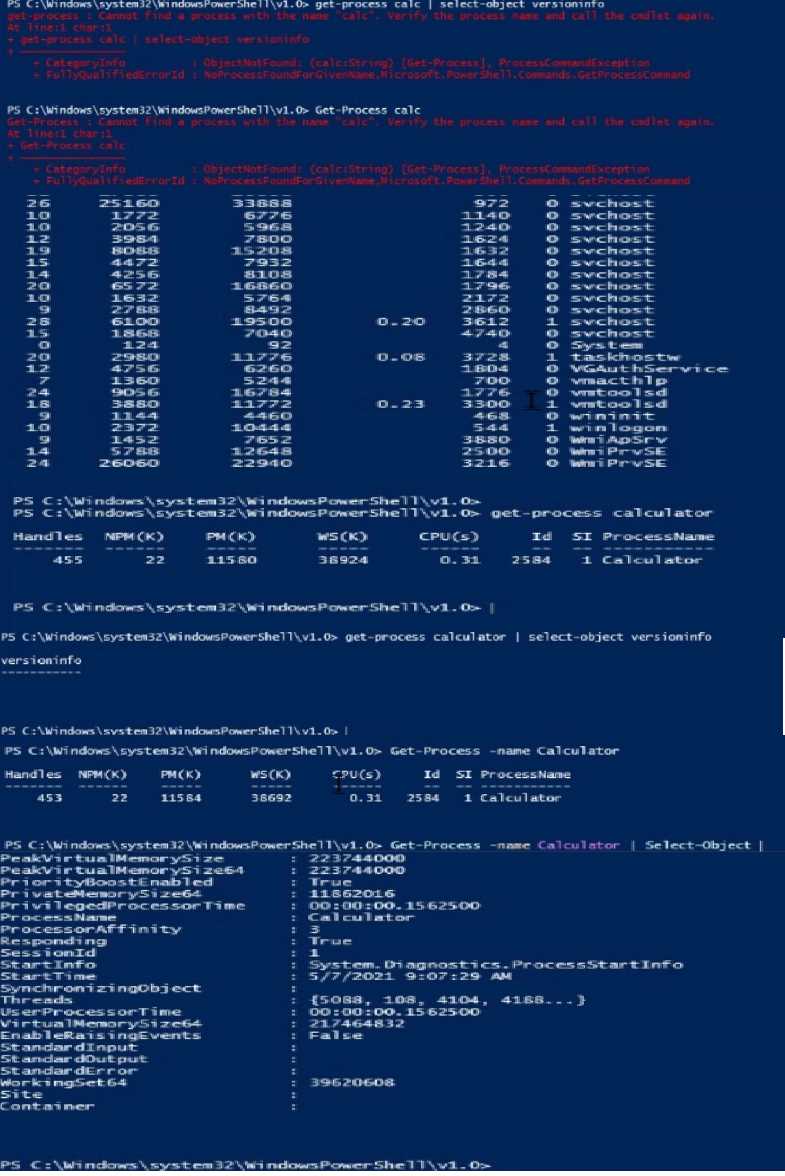
Launch Calculator (calc.exe). Using PowerShell, retrieve the Calculator Process Information. What is
the value of the File Version property?
Hint: The process name of Calculator is calculator
- A. 10.1705.12507.0
- B. 10.1902.1603.06155
- C. 10.0.19041.1
- D. 8.1.2017.26587
- E. 8.2017.1009.04153
- F. 10.1705.1809.07007
- G. 8.2017.0908.29102
- H. 8.1902.6547.63452
- I. 10.0.14395.693
- J. 8.1.875.154873
Answer:
F
Question 4
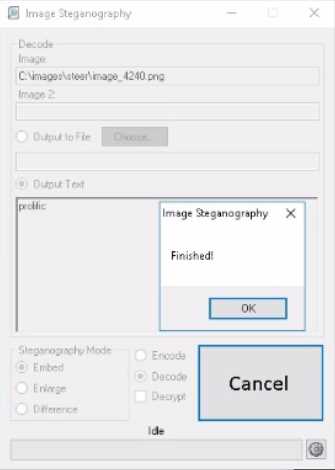
In the directory
C:\lmages\steer
there Is an Image file lmage_4240.png with a data string encoded
inside the file. What word is hidden in the file?
- A. pontine
- B. prolific
- C. abysmal
- D. petroleum
- E. mushroom
- F. Chicago
- G. marshmallow
- H. flying
- I. shocking
Answer:
B.
Question 5
Use PowerShell ISE to
examineC:\Windows\security\templates\WorkstationSecureTemplate.inf.
Which
setting
is
configured in the template?
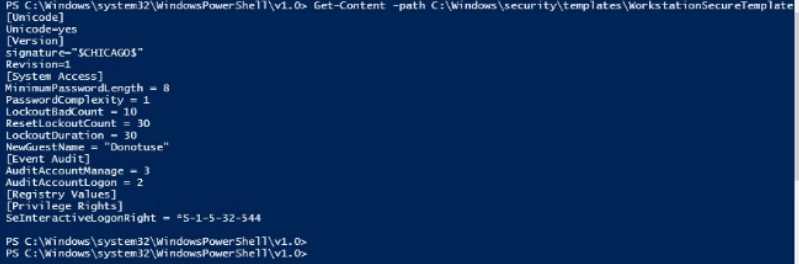
- A. ResetLockoutCount
- B. NewAdministratorName
- C. MinirnumPasswordAge
- D. Require logonToChangoPassword
- E. SeRemotPlnteractiveLogonRlght
- F. MaxRenewAge
- G. AuditSystemEvents
- H. EnableGuestAccount
- I. AuditPolicyChange
Answer:
A
Question 6
What is the SHA1 hash of the Ale /bin/Is?
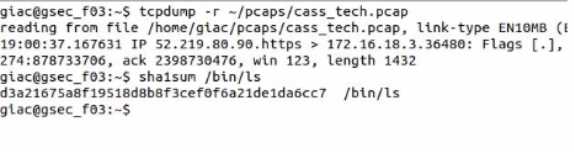
- A. a895bac9c3<M75d5fa7fb5820b35568cedb5dc23
- B. 54771b4r<d7tKb4382e670b4465O265206cf09e9
- C. a39bed3C496fC764fc518d3e2d56f7d0f4C625fb
- D. 93c1 ffbd22ebcad798886fb4aa46fa 357b23d80a
- E. aa40739f465ded2245872b1e4972e33d5bObb1cb
- F. 494a 192859f 244c69d5bdc46255d b44l9e 7d051 f
- G. d3a21675a8f 19518d8b8f3cefOf6a21 del da6cc7
- H. 84611 eOb6d59045bOcf 189fca9bc760afdf b7372
- I. 8873 5f5cb7CCf7b2d 137944ab1 2d 116808310500
- J. 2cadod58fbd0345c2ced336f9a3ae6f43cf355fi
Answer:
G
Question 7
Open the MATE terminal and use the tcpdump program to read - /pcaps /cass tech.pcap.
What is the source port number?
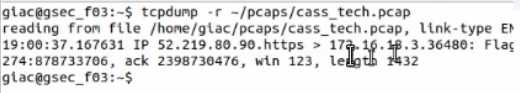
- A. 878733706
- B. 123
- C. 443
- D. 878732274
- E. 36480
- F. 2398730476
- G. 1432
- H. 80
- I. 25
Answer:
E
Question 8
Use Hashcat to crack a local shadow file. What Is the password for the user account AGainsboro?
Hints
Hints
• The shadow file (shadow) and Hashcat wordlist (gsecwordlist.txt) are located in the directory.
home giac PasswordHashing
- Run Hashcat in straight mod* (flag -a 0) to crack the MD5 hashes (flag -m 500) in the shadow file.
• Use the hash values from the Hashcat output file and the shadow file to match the cracked
password with the user name.
• If required, a backup copy of the original files can be found in the shadowbackup directory.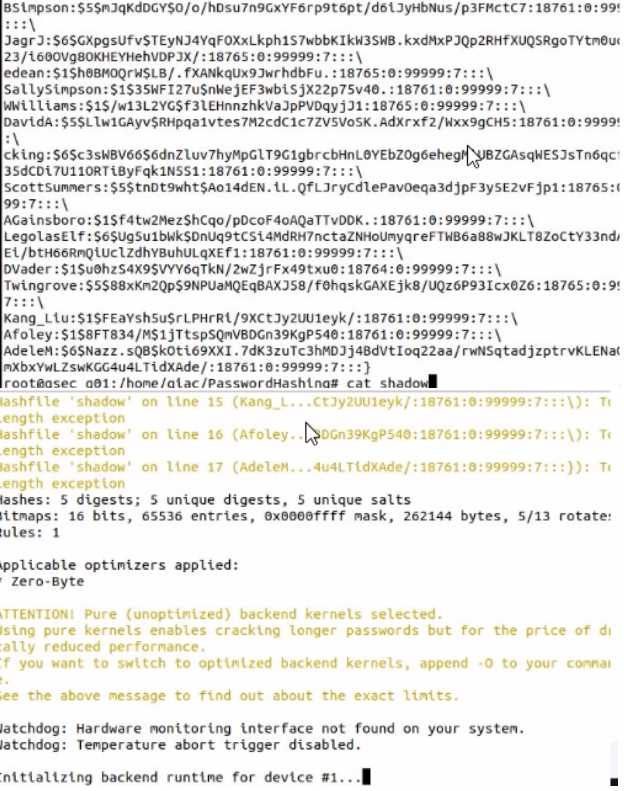
- A. J3@nGr3y
- B. WwBoj25tT7
- C. MsconfiG35
- D. Noregrets2
- E. HowAreWeToday?19
- F. Prometheus
- G. 6dWalking8
- H. IM-O-O-NI
- I. yoshiro392
- J. MEWRULES
Answer:
D
Question 9
Use Hashcat to crack a local shadow file. What Is the password for the user account AGainsboro?
Hints
• The shadow file (shadow) and Hashcat wordlist (gsecwordlist.txt) are located in the directory
/home /giac /PasswordHashing/
• Run Hashcat in straight mode (flag -a 0) to crack the MD5 hashes (flag -m 500) In the shadow file.
• Use the hash values from the Hashcat output file and the shadow file to match the cracked
password with the user name.
• If required, a backup copy of the original files can be found in the shadowbackup directory.
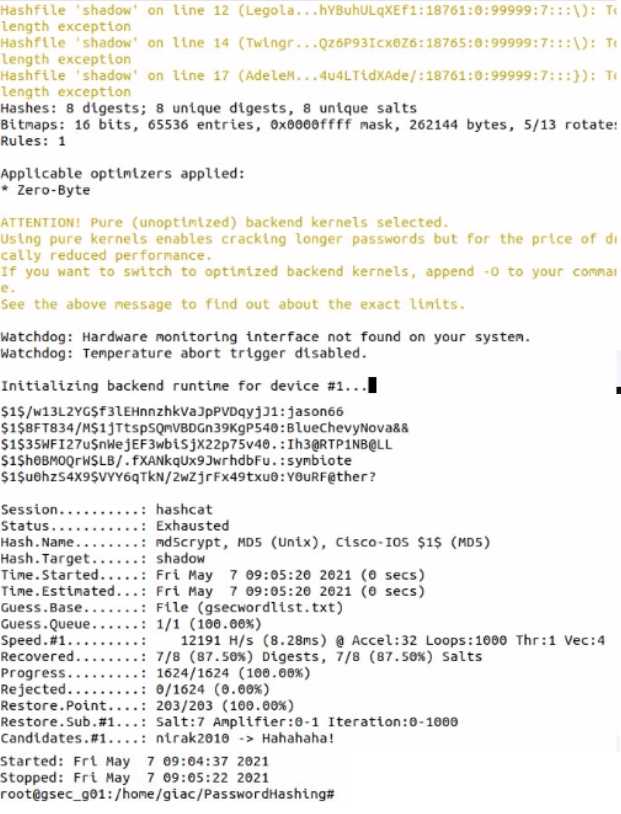
- A. 52345234
- B. YOuRF ether?
- C. symbiote
- D. Volcano
- E. QX689PJ688
- F. LlqMM@qe
- G. Noregrets2
- H. Learn2Write
- I. Th 3D5@60n
- J. jason66
Answer:
E
Question 10
Use nmap to discover a host on the 10.10.10.0/24 network, scanning only port 8082 and using the
SYN or Stealth scan approach. Which host has a service called -blackice-alerts"?
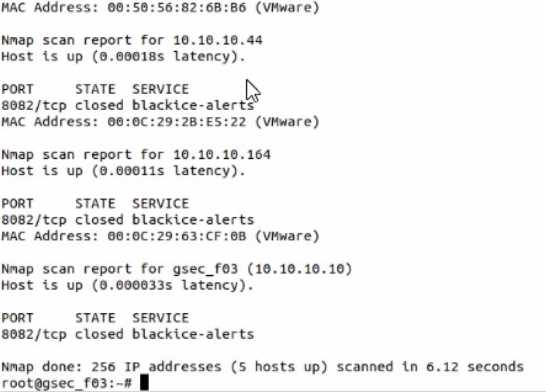
- A. 10.10.10.115
- B. 10.10.10.80
- C. 10.10.10.5
- D. 10.10.10
- E. 10.10.10.30
- F. 10.10.10.164
- G. 10.10.10.37
- H. 10.10.10.20
- I. 10.10.10.7
Answer:
F
Question 11
Use Wireshark to analyze Desktop;PCAP FILES/charile.pcap
What is the destination IP address in packet #3?
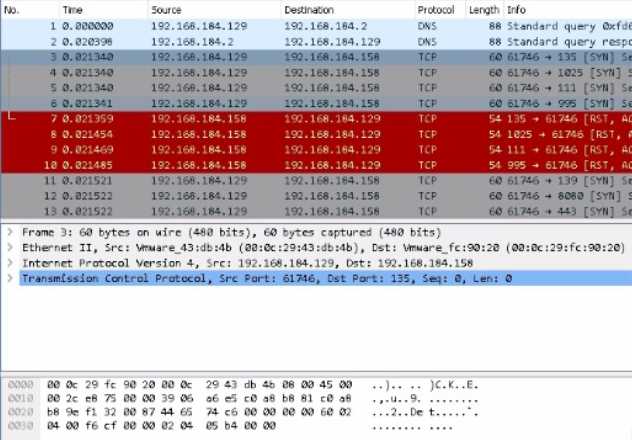
- A. 192.168.184.2
- B. 192.168.184.73
- C. 192.168.184.129
- D. 192.168.184.111
- E. 197.168.184.13
- F. 197.168.184.158
- G. 192.168.184.201
- H. 192.168.184.17
- I. 19Z168.184222
Answer:
F
Question 12
Which of the following attacks can be mitigated by avoiding making system calls from within a web
application?
- A. Denial of Service
- B. OS command injection
- C. SQL Injection
- D. Buffer Overflows
Answer:
B, C
Question 13
Which of the following is an example of a BitLocker recovery password?
- A. 01 E6 0J4CCEAF 79A481 08BAC59I 7I BE8B
- B. 389627 801256690151785527 909978 568638 271012 905516
- C. 6c0b48fafaecb0bf8c2610253ee717at
- D. 42VgYAjYV+C7ff6MdeqBGx5Y7V2zFQA=
Answer:
B
Question 14
Which of the following is Azure's version of a superuser?
- A. Network administrator
- B. Global administrator
- C. Security administrator
- D. Intune administrator
Answer:
B
Question 15
Which asymmetric algorithm is used only for key exchange?
- A. EI Gamal
- B. Diffuse-H an
- C. ECC
- D. DSA
Answer:
B