giac GPYC Exam Questions
Questions for the GPYC were updated on : Feb 20 ,2026
Page 1 out of 5. Viewing questions 1-15 out of 75
Question 1
An operator able to perform bitwise shifts is coded as (select two answers)
- A. - -
- B. ++
- C. <<
- D. >>
Answer:
CD
Question 2
What will be the value of the i variable when the while loop finishes its execution0
i = 0
while i != 0:
1 = 1-1
else:
i = i + 1
- A. 1
- B. 0
- C. 2
- D. the variable becomes unavailable
Answer:
A
Question 3
An attacker does not yet know the IP address of his target. He uses the "socket" module to create a
backdoor program. He is writing the command to bind the computer's current IP address and port
4444 to the "backdoor" socket. Which command should he use?
- A. backdoor.bind(UDP, 4444)
- B. backdoor.bind()(4444)
- C. backdoor.bind((*))
- D. backdoor.bind(("",4444))
Answer:
D
Question 4
In a SQL injection attack, which character would an attacker use to separate multiple SQL statements
on a single line?
- A. ''(double quotation marks)
- B. ; (semicolon)
- C. . (period)
- D. % (percentage sign)
Answer:
B
Question 5
What will the last value of V be when Python executes the following control loop?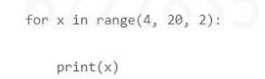
- A. 4
- B. 20
- C. 2
- D. 18
Answer:
D
Question 6
Which of the following modules allows a programmer to specify and spawn new processes, connect
to their input and output pipes, and retrieve returned data?
- A. pip
- B. urllib2
- C. subprocess
- D. prochandle
Answer:
C
Question 7
Which of the lambda definitions of the function some_code is equivalent to the following function
definition?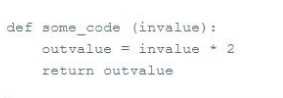
Which of the lambda definitions of the function some_code is equivalent to the following function
definition?
- A. some_code = lambda outvalue:invalue*2
- B. some_code = lambda invalue:outvalue*2
- C. some code = lambda invalue:invalue*2
Answer:
A
Question 8
What does the following command do?
pip search syslog
- A. Searches for python modules related to syslog
- B. Searches for functions in the syslog module
- C. Results in a syntax error for the pip function
- D. Determines whether the syslog module is loaded
Answer:
A
Question 9
With a requests session object named "browser", how can the expiration attribute of a cookie named
"MUID" from "gpyc.com/" be accessed?
- A. browser.cookies._cooktes['.gpyc.com/MUID'] .expires
- B. browser.cookies._cookies['.gpyc.com'] ['/'] ['MUID'].expires
- C. browser.cookies._cookies.gpyc.com.MUID.expires
- D. browser.cookies.gpyc.com['MUID']. expires
- E. browser.cookies.gpyc.com.MUID.expires
Answer:
A
Question 10
What does the attacker do in a SQL Injection attack?
- A. Obtains an administrative login for a SQL database server
- B. Finds and exploits CVSS-SIG vulnerabilities in a particular version of SQL database
- C. Inject information into an SQL server via an undocumented administrative interface
- D. Submits a string that is interpreted as a SQL database command
Answer:
C
Question 11
What is the output of the following line of code typed into a Python interactive session?
>>>print (8 <<1)
- A. False
- B. 16
- C. SyntaxError: invalid syntax
- D. True
Answer:
B
Question 12
What does the following line of code do?
- A. Sends the data stored in the variable "socket" to the IP address stored in AF_INET
- B. Gets data from all network sockets on the system
- C. Creates an instance of a UDP socket for transmitting or receiving data
- D. Transfers data from the local system to a remote system across the network
Answer:
C
Question 13
What will the following code in Python 3 result in?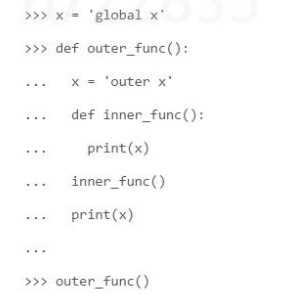
- A. outer x, outer x
- B. inner x, inner x
- C. global x, outer x
- D. NameError, outer
- E. inner x, outer x
Answer:
A
Question 14
During a password guessing attack, which HTTP request method would a Python program most
commonly call to submit a usemame and password to a target website?
- A. OPTIONS
- B. POST
- C. CONNECT
Answer:
B
Question 15
Which of the following is the output when the following program is executed with a Python
Interpreter?
- A. a
- B. 10
- C. -10
- D. -a
Answer:
C