giac GCED Exam Questions
Questions for the GCED were updated on : Feb 20 ,2026
Page 1 out of 6. Viewing questions 1-15 out of 88
Question 1
Which statement below is the MOST accurate about insider threat controls?
A. Classification of information assets helps identify data to protect.
B. Security awareness programs have a minimal impact on reducing the insider threat.
C. Both detective and preventative controls prevent insider attacks.
D. Rotation of duties makes an insider threat more likely.
E. Separation of duties encourages one employee to control a great deal of information.
Answer:
A
A company needs to classify its information as a key step in valuing it and knowing where to focus its
protection.
Rotation of duties and separation of duties are both key elements in reducing the scope of
information access and the ability to conceal malicious behavior.
Separation of duties helps minimize “empire building” within a company, keeping one individual
from controlling a great deal of information, reducing the insider threat.
Security awareness programs can help other employees notice the signs of an insider attack and thus
reduce the insider threat.
Detection is a reactive method and only occurs after an attack occurs. Only preventative methods can
stop or limit an attack.
Question 2
Which tool keeps a backup of all deleted items, so that they can be restored later if need be?
A. ListDLLs
B. Yersinia
C. Ettercap
D. ProcessExplorer
E. Hijack This
Answer:
E
After selecting “fix it!” with Hijack This you can always restore deleted items, because Hijack This
keeps a backup of them.
Question 3
A compromised router is reconfigured by an attacker to redirect SMTP email traffic to the attacker’s
server before sending packets on to their intended destinations. Which IP header value would help
expose anomalies in the path outbound SMTP/Port 25 traffic takes compared to outbound packets
sent to other ports?
A. Checksum
B. Acknowledgement number
C. Time to live
D. Fragment offset
Answer:
C
In a case study of a redirect tunnel set up on a router, some anomalies were noticed while watching
network traffic with the TCPdump packet sniffer.
Packets going to port 25 (Simple Mail Transfer Protocol [SMTP] used by mail servers and other Mail
Transfer Agents [MTAs] to send and receive e-mail) were apparently taking a different network path.
The TLs were consistently three less than other destination ports, indicating another three network
hops were taken.
Other IP header values listed, such as fragment offset. The acknowledgement number is a TCP, not IP,
header field.
Question 4
What is needed to be able to use taskkill to end a process on remote system?
A. Svchost.exe running on the remote system
B. Domain login credentials
C. Port 445 open
D. Windows 7 or higher on both systems
Answer:
B
Domain login credentials are needed to kill a process on a remote system using taskkill.
Question 5
What are Browser Helper Objects (BHO)s used for?
A. To provide multi-factor authentication support for Firefox
B. To provide a more feature-rich interface for Internet Explorer
C. To allow Internet Explorer to process multi-part URLs
D. To allow Firefox to process JavaScript in a sandbox
Answer:
B
When scanning your system, you may notice many BHOs since they are widely used by software
developers to provide a more feature rich interface for Microsoft Internet Explorer.
Question 6
What information would the Wireshark filter in the screenshot list within the display window?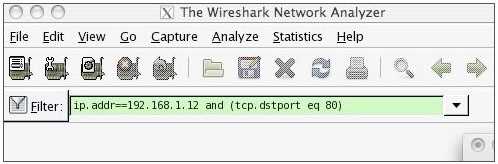
- A. Only HTTP traffic to or from IP address 192.168.1.12 that is also destined for port 80
- B. Only traffic to or from IP address 192.168.1.12 and destined for port 80
- C. Only traffic with a source address of 192.168.1.12 to or from port 80
- D. Only traffic with a destination address of 192.168.1.12 to or from port 80
Answer:
B
Question 7
What would the output of the following command help an incident handler determine?
cscript manage-bde . wsf –status
- A. Whether scripts can be run from the command line
- B. Which processes are running on the system
- C. When the most recent system reboot occurred
- D. Whether the drive has encryption enabled
Answer:
D
Question 8
Which of the following is a major problem that attackers often encounter when attempting to
develop or use a kernel mode rootkit?
- A. Their effectiveness depends on the specific applications used on the target system.
- B. They tend to corrupt the kernel of the target system, causing it to crash.
- C. They are unstable and are easy to identify after installation
- D. They are highly dependent on the target OS.
Answer:
B
Question 9
Which of the following is an SNMPv3 security feature that was not provided by earlier versions of the
protocol?
- A. Authentication based on RSA key pairs
- B. The ability to change default community strings
- C. AES encryption for SNMP network traffic
- D. The ability to send SNMP traffic over TCP ports
Answer:
C
Question 10
What is the BEST sequence of steps to remove a bot from a system?
- A. Terminate the process, remove autoloading traces, delete any malicious files
- B. Delete any malicious files, remove autoloading traces, terminate the process
- C. Remove autoloading traces, delete any malicious files, terminate the process
- D. Delete any malicious files, terminate the process, remove autoloading traces
Answer:
A
Question 11
What would be the output of the following Google search?
filetype:doc inurl:ws_ftp
- A. Websites running ws_ftp that allow anonymous logins
- B. Documents available on the ws_ftp.com domain
- C. Websites hosting the ws_ftp installation program
- D. Documents found on sites with ws_ftp in the web address
Answer:
D
Question 12
What attack was indicated when the IDS system picked up the following text coming from the
Internet to the web server?
select user, password from user where user= “jdoe” and password= ‘myp@55!’ union select “text”,2
into outfile “/tmp/file1.txt” - - ’
A. Remote File Inclusion
B. URL Directory Traversal
C. SQL Injection
D. Binary Code in HTTP Headers
Answer:
C
An example of manipulating SQL statements to perform SQL injection includes using the semi-colon
‘ or 1=1; drop table users; - -
[Anything]
Question 13
Which of the following would be used in order to restrict software form performing unauthorized
operations, such as invalid access to memory or invalid calls to system access?
- A. Perimeter Control
- B. User Control
- C. Application Control
- D. Protocol Control
- E. Network Control
Answer:
C
Question 14
When running a Nmap UDP scan, what would the following output indicate?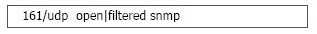
A. The port may be open on the system or blocked by a firewall
B. The router in front of the host accepted the request and sent a reply
C. An ICMP unreachable message was received indicating an open port
D. An ACK was received in response to the initial probe packet
Answer:
A
When Nmap shows an “open filtered” response for the scan results, this indicates a couple of
different reasons. The port could be open but a firewall could be blocking the use ACK flags; only TCP
packets do.
Question 15
How does an Nmap connect scan work?
A. It sends a SYN, waits for a SYN/ACK, then sends a RST.
B. It sends a SYN, waits for a ACK, then sends a RST.
C. It sends a SYN, waits for a ACK, then sends a SYN/ACK.
D. It sends a SYN, waits for a SYN/ACK, then sends a ACK
Answer:
A
An Nmap connect scan sends a SYN, waits for a SYN/ACK, then sends a ACK to complete the three-
way handshake. A Nmap half-open scan sends a SYN, waits for a SYN/ACK, then sends a RST.