giac GCCC Exam Questions
Questions for the GCCC were updated on : Feb 20 ,2026
Page 1 out of 7. Viewing questions 1-15 out of 93
Question 1
The settings in the screenshot would be configured as part of which CIS Control?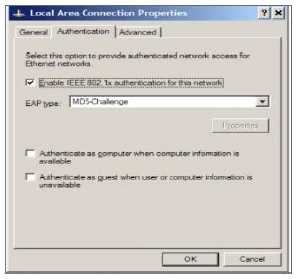
- A. Application Software Security
- B. Inventory and Control of Hardware Assets
- C. Account Monitoring and Control
- D. Controlled Use of Administrative Privileges
Answer:
B
Question 2
Which of the following will decrease the likelihood of eavesdropping on a wireless network?
- A. Broadcasting in the 5Ghz frequency
- B. Using Wired Equivalent Protocol (WEP)
- C. Using EAP/TLS authentication and WPA2 with AES encryption
- D. Putting the wireless network on a separate VLAN
Answer:
C
Question 3
What is an organization’s goal in deploying a policy to encrypt all mobile devices?
- A. Enabling best practices for the protection of their software licenses
- B. Providing their employees, a secure method of connecting to the corporate network C. Controlling unauthorized access to sensitive information
- D. Applying the principle of defense in depth to their mobile devices
Answer:
C
Question 4
A breach was discovered after several customers reported fraudulent charges on their accounts. The
attacker had exported customer logins and cracked passwords that were hashed but not salted.
Customers were made to reset their passwords.
Shortly after the systems were cleaned and restored to service, it was discovered that a
compromised system administrator’s account was being used to give the attacker continued access
to the network. Which CIS Control failed in the continued access to the network?
- A. Maintenance, Monitoring, and Analysis of Audit Logs
- B. Controlled Use of Administrative Privilege
- C. Incident Response and Management
- D. Account Monitoring and Control
Answer:
C
Question 5
What is a zero-day attack?
- A. An attack that has a known attack signature but no available patch
- B. An attack that utilizes a vulnerability unknown to the software developer
- C. An attack that deploys at the end of a countdown sequence
- D. An attack that is launched the day the patch is released
Answer:
B
Question 6
Of the options shown below, what is the first step in protecting network devices?
- A. Creating standard secure configurations for all devices
- B. Scanning the devices for known vulnerabilities
- C. Implementing IDS to detect attacks
- D. Applying all known security patches
Answer:
A
Question 7
Which type of scan is best able to determine if user workstations are missing any important patches?
- A. A network vulnerability scan using aggressive scanning
- B. A source code scan
- C. A port scan using banner grabbing
- D. A web application/database scan
- E. A vulnerability scan using valid credentials
Answer:
E
Question 8
Acme Corporation is doing a core evaluation of its centralized logging capabilities. Which of the
following scenarios indicates a failure in more than one CIS Control?
- A. The loghost is missing logs from 3 servers in the inventory
- B. The loghost is receiving logs from hosts with different timezone values
- C. The loghost time is out-of-sync with an external host
- D. The loghost is receiving out-of-sync logs from undocumented servers
Answer:
D
Question 9
Which of the following actions will assist an organization specifically with implementing web
application software security?
- A. Making sure that all hosts are patched during regularly scheduled maintenance
- B. Providing end-user security training to both internal staff and vendors
- C. Establishing network activity baselines among public-facing servers
- D. Having a plan to scan vulnerabilities of an application prior to deployment
Answer:
D
Question 10
An organization is implementing an application software security control their custom-written code
that provides web—based database access to sales partners. Which action will help mitigate the risk
of the application being compromised?
- A. Providing the source code for their web application to existing sales partners
- B. Identifying high-risk assets that are on the same network as the web application server
- C. Creating signatures for their IDS to detect attacks specific to their web application
- D. Logging the connection requests to the web application server from outside hosts
Answer:
C
Question 11
An organization has implemented a control for penetration testing and red team exercises conducted
on their network. They have compiled metrics showing the success of the penetration testing
(Penetration Tests), as well as the number of actual adversary attacks they have sustained (External
Attacks). Assess the metrics below and determine the appropriate interpretation with respect to this
control.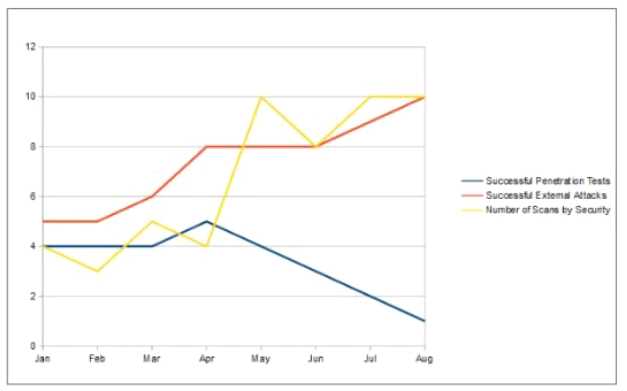
- A. The blue team is adequately protecting the network
- B. There are too many internal penetration tests being conducted
- C. The methods the red team is using are not effectively testing the network
- D. The red team is improving their capability to measure network security
Answer:
C
Question 12
Which of the following assigns a number indicating the severity of a discovered software
vulnerability?
- A. CPE
- B. CVE
- C. CCE
- D. CVSS
Answer:
D
Question 13
If an attacker wanted to dump hashes or run wmic commands on a target machine, which of the
following tools would he use?
- A. Mimikatz
- B. OpenVAS
- C. Metasploit
Answer:
C
Question 14
An attacker is able to successfully access a web application as root using ‘ or 1 = 1 . as the password.
The successful access
indicates a failure of what process?
- A. Input Validation
- B. Output Sanitization
- C. URL Encoding
- D. Account Management
Answer:
A
Question 15
An auditor is validating the policies and procedures for an organization with respect to a control for
Data Recovery. The organization’s control states they will completely back up critical servers weekly,
with incremental backups every four hours. Which action will best verify success of the policy?
- A. Verify that the backup media cannot be read without the encryption key
- B. Check the backup logs from the critical servers and verify there are no errors
- C. Select a random file from a critical server and verify it is present in a backup set
- D. Restore the critical server data from backup and see if data is missing
Answer:
D