Fortinet NSE8-812 Exam Questions
Questions for the NSE8-812 were updated on : Jul 06 ,2025
Page 1 out of 6. Viewing questions 1-10 out of 60
Question 1
Refer to the exhibit showing a FortiSOAR playbook.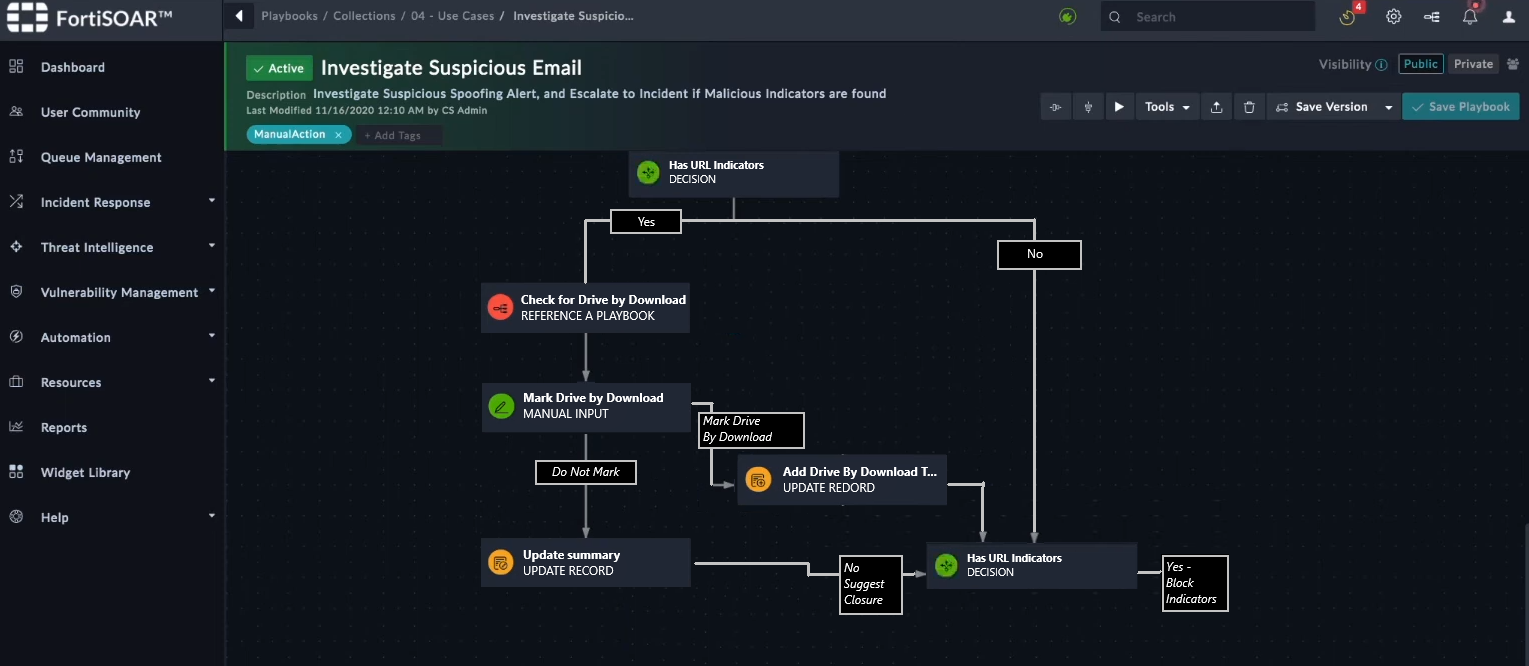
You are investigating a suspicious e-mail alert on FortiSOAR, and after reviewing the executed playbook, you can see that it requires intervention.
What should be your next step?
- A. Go to the Incident Response tasks dashboard and run the pending actions
- B. Click on the notification icon on FortiSOAR GUI and run the pending input action
- C. Run the Mark Drive by Download playbook action
- D. Reply to the e-mail with the requested Playbook action
Answer:
a
Question 2
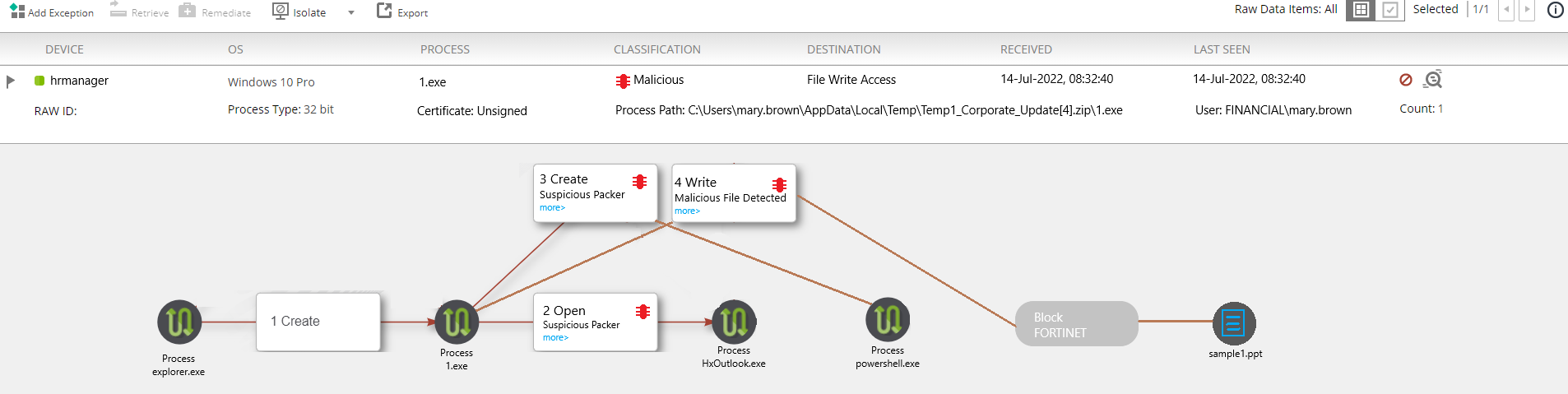
Refer to the exhibit.
The exhibit shows the forensics analysis of an event detected by the FortiEDR core.
In this scenario, which statement is correct regarding the threat?
- A. This is an exfiltration attack and has been stopped by FortiEDR
- B. This is an exfiltration attack and has not been stopped by FortiEDR
- C. This is a ransomware attack and has not been stopped by FortiEDR
- D. This is a ransomware attack and has been stopped by FortiEDR
Answer:
c
Question 3
Refer to the exhibits.
Exhibit A 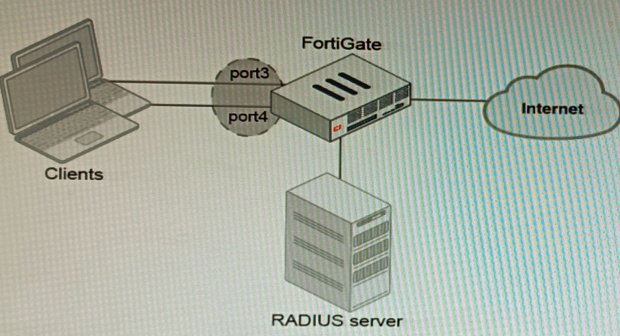
Exhibit B 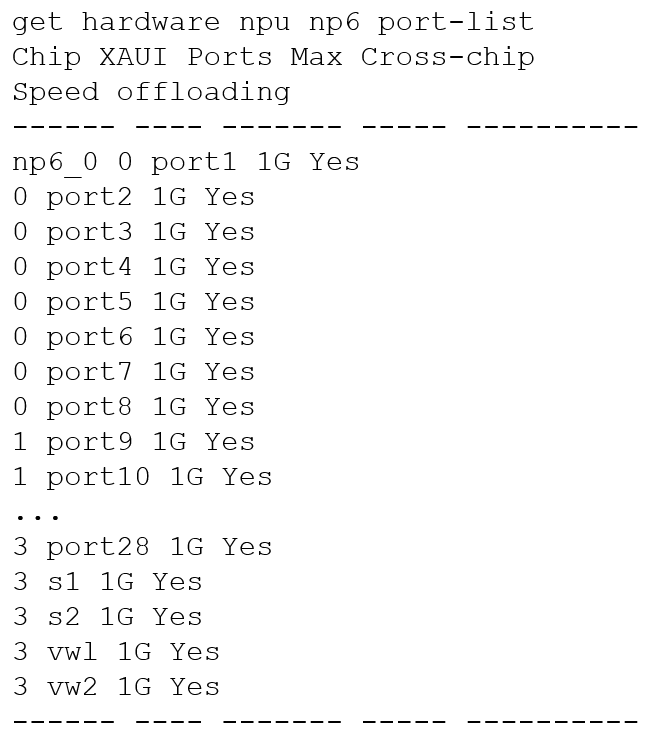
A customer is looking for a solution to authenticate the clients connected to a hardware switch interface of a FortiGate 400E.
Referring to the exhibits, which two conditions allow authentication to the client devices before assigning an IP address? (Choose two.)
- A. FortiGate devices with NP6 and hardware switch interfaces cannot support 802.1X authentication
- B. Devices connected directly to ports 3 and 4 can perform 802.1X authentication
- C. Ports 3 and 4 can be part of different switch interfaces
- D. Client devices must have 802.1X authentication enabled
Answer:
bd
Question 4
Review the VPN configuration shown in the exhibit.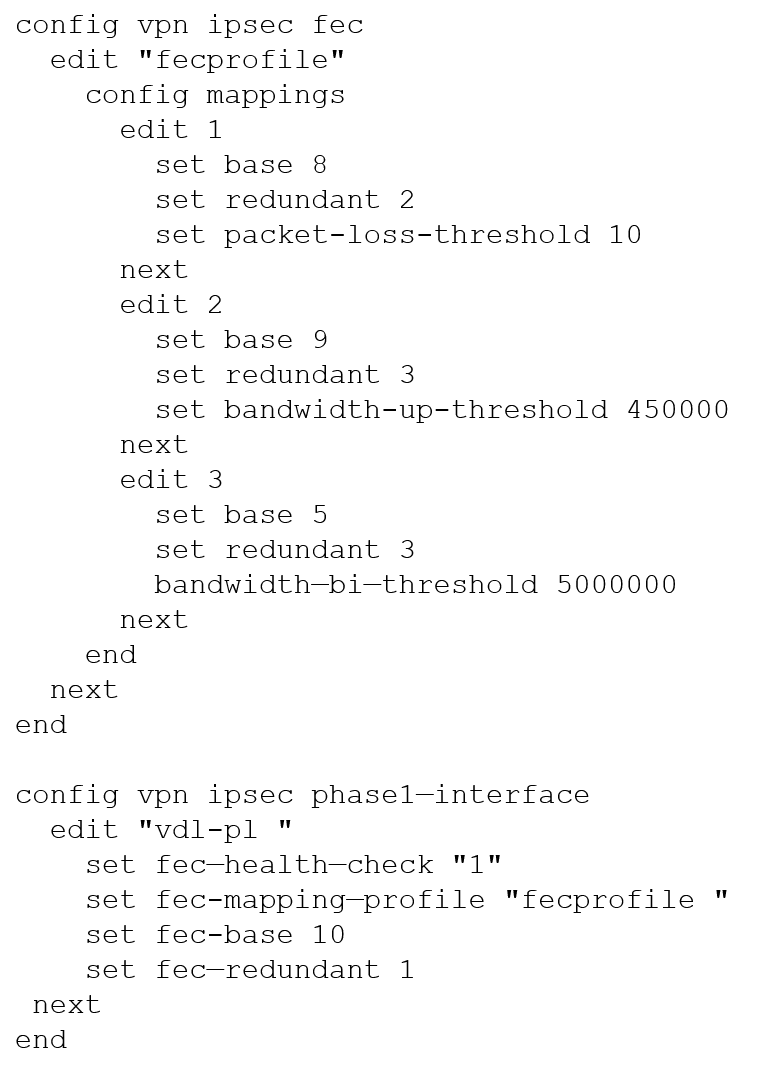
What is the Forward Error Correction behavior if the SD-WAN network traffic download is 500 Mbps and has 8% of packet loss in the environment?
- A. 1 redundant packet for every 10 base packets
- B. 3 redundant packet for every 5 base packets
- C. 2 redundant packet for every 8 base packets
- D. 3 redundant packet for every 9 base packets
Answer:
b
Question 5
Refer to the exhibit showing the history logs from a FortiMail device.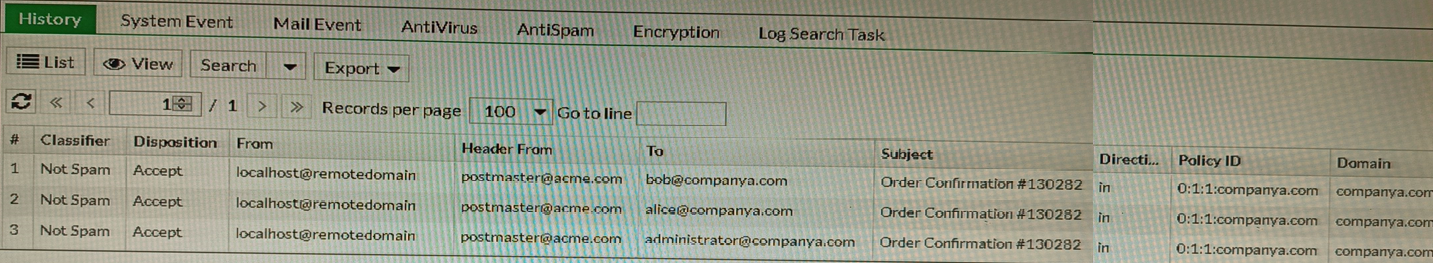
Which FortiMail email security feature can an administrator enable to treat these emails as spam?
- A. DKIM validation in a session profile
- B. Sender domain validation in a session profile
- C. Impersonation analysis in an antispam profile
- D. Soft fail SPF validation in an antispam profile
Answer:
c
Question 6
Review the following FortiGate-6000 configuration excerpt:
Based on the configuration, which statement is correct regarding SNAT source port partitioning behavior?
- A. It dynamically distributes SNAT source ports to operating FPCs or FPMs.
- B. It is the default SNAT configuration and preserves active sessions when an FPC or FPM goes down.
- C. It statically distributes SNAT source ports to operating FPCs or FPMs.
- D. It equally distributes SNAT source ports across chassis slots.
Answer:
c
Question 7
A remote IT Team is in the process of deploying a FortiGate in their lab. The closed environment has been configured to support zero-touch provisioning from the FortiManager, on the same network, via DHCP options. After waiting 15 minutes, they are reporting that the FortiGate received an IP address, but the zero-touch process failed.
The exhibit below shows what the IT Team provided while troubleshooting this issue:
Which statement explains why the FortiGate did not install its configuration from the FortiManager?
- A. The FortiGate was not configured with the correct pre-shared key to connect to the FortiManager
- B. The DHCP server was not configured with the FQDN of the FortiManager
- C. The DHCP server used the incorrect option type for the FortiManager IP address
- D. The configuration was modified on the FortiGate prior to connecting to the FortiManager
Answer:
c
Question 8
A remote worker requests access to an SSH server inside the network. You deployed a ZTNA Rule to their FortiClient. You need to follow the security requirements to inspect this traffic.
Which two statements are true regarding the requirements? (Choose two.)
- A. FortiGate can perform SSH access proxy host-key validation.
- B. You need to configure a FortiClient SSL-VPN tunnel to inspect the SSH traffic.
- C. SSH traffic is tunneled between the client and the access proxy over HTTPS.
- D. Traffic is discarded as ZTNA does not support SSH connection rules.
Answer:
ac
Question 9
SD-WAN is configured on a FortiGate. You notice that when one of the internet links has high latency the time to resolve names using DNS from FortiGate is very high.
You must ensure that the FortiGate DNS resolution times are as low as possible with the least amount of work.
What should you configure?
- A. Configure local out traffic to use the outgoing interface based on SD-WAN rules with a manual defined IP associated to a loopback interface and configure an SD-WAN rule from the loopback to the DNS server.
- B. Configure an SD-WAN rule to the DNS server and use the FortiGate interface IPs in the source address.
- C. Configure two DNS servers and use DNS servers recommended by the two internet providers.
- D. Configure local out traffic to use the outgoing interface based on SD-WAN rules with the interface IP and configure an SD-WAN rule to the DNS server.
Answer:
d
Question 10
You want to use the MTA adapter feature on FortiSandbox in an HA-Cluster.
Which statement about this solution is true?
- A. The configuration of the MTA Adapter Local Interface is different than on port1
- B. The MTA adapter is only available in the primary node
- C. The MTA adapter mode is only detection mode
- D. The configuration is different than on a standalone device
Answer:
d