Fortinet NSE6-FAC-6-1 Exam Questions
Questions for the NSE6-FAC-6-1 were updated on : Jun 29 ,2025
Page 1 out of 2. Viewing questions 1-15 out of 30
Question 1
Which interface services must be enabled for the SCEP client to connect to Authenticator?
- A. OCSP
- B. REST API
- C. SSH
- D. HTTP/HTTPS
Answer:
D
Question 2
Which FSSO discovery method transparently detects logged off users without having to rely on
external features such as WMI polling?
- A. Windows AD polling
- B. FortiClient SSO Mobility Agent
- C. Radius Accounting
- D. DC Polling
Answer:
B
Question 3
How can a SAML metada file be used?
- A. To defined a list of trusted user names
- B. To import the required IDP configuration
- C. To correlate the IDP address to its hostname
- D. To resolve the IDP realm for authentication
Answer:
B
Question 4
Which two are supported captive or guest portal authentication methods? (Choose two)
- A. Linkedln
- B. Apple ID
- C. Instagram
- D. Email
Answer:
A, D
Question 5
Which option correctly describes an SP-initiated SSO SAML packet flow for a host without a SAML
assertion?
- A. Service provider contacts idendity provider, idendity provider validates principal for service provider, service provider establishes communication with principal
- B. Principal contacts idendity provider and is redirected to service provider, principal establishes connection with service provider, service provider validates authentication with identify provider
- C. Principal contacts service provider, service provider redirects principal to idendity provider, after succesfull authentication identify provider redirects principal to service provider
- D. Principal contacts idendity provider and authenticates, identity provider relays principal to service provider after valid authentication
Answer:
C
Question 6
A device or user identity cannot be established transparently, such as with non-domain BYOD
devices, and allow users to create their own credentialis.
In this case, which user idendity discovery method can Fortiauthenticator use?
- A. Syslog messaging or SAML IDP
- B. Kerberos-base authentication
- C. Radius accounting
- D. Portal authentication
Answer:
D
Question 7
Which two SAML roles can Fortiauthenticator be configured as? (Choose two)
- A. Idendity provider
- B. Principal
- C. Assertion server
- D. Service provider
Answer:
A, D
Question 8
What happens when a certificate is revoked? (Choose two)
- A. Revoked certificates cannot be reinstated for any reason
- B. All certificates signed by a revoked CA certificate are automatically revoked
- C. Revoked certificates are automatically added to the CRL
- D. External CAs will priodically query Fortiauthenticator and automatically download revoked certificates
Answer:
C, D
Question 9
Which two types of digital certificates can you create in Fortiauthenticator? (Choose two)
- A. User certificate
- B. Organization validation certificate
- C. Third-party root certificate
- D. Local service certificate
Answer:
A, D
Question 10
You are the administrator of a large network that includes a large local user datadabase on the
current Fortiauthenticatior. You want to import all the local users into a new Fortiauthenticator
device.
Which method should you use to migrate the local users?
- A. Import users using RADIUS accounting updates.
- B. Import the current directory structure.
- C. Import users from RADUIS.
- D. Import users using a CSV file.
Answer:
D
Question 11
Which three of the following can be used as SSO sources? (Choose three)
- A. FortiClient SSO Mobility Agent
- B. SSH Sessions
- C. FortiAuthenticator in SAML SP role
- D. Fortigate
- E. RADIUS accounting
Answer:
A, C, E
Question 12
Which two capabilities does FortiAuthenticator offer when acting as a self-signed or local CA?
(Choose two)
- A. Validating other CA CRLs using OSCP
- B. Importing other CA certificates and CRLs
- C. Merging local and remote CRLs using SCEP
- D. Creating, signing, and revoking of X.509 certificates
Answer:
B, D
Question 13
Which statement about the guest portal policies is true?
- A. Guest portal policies apply only to authentication requests coming from unknown RADIUS clients
- B. Guest portal policies can be used only for BYODs
- C. Conditions in the policy apply only to guest wireless users
- D. All conditions in the policy must match before a user is presented with the guest portal
Answer:
D
Question 14
Refer to the exhibit.
Examine the screenshot shown in the exhibit.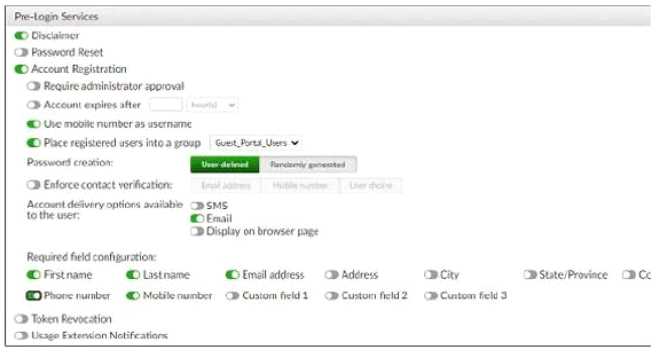
Which two statements regarding the configuration are true? (Choose two)
- A. All guest accounts created using the account registration feature will be placed under the Guest_Portal_Users group
- B. All accounts registered through the guest portal must be validated through email
- C. Guest users must fill in all the fields on the registration form
- D. Guest user account will expire after eight hours
Answer:
A, B
Question 15
Which EAP method is known as the outer authentication method?
- A. PEAP
- B. EAP-GTC
- C. EAP-TLS
- D. MSCHAPV2
Answer:
A