forescout FSCP Exam Questions
Questions for the FSCP were updated on : Feb 20 ,2026
Page 1 out of 6. Viewing questions 1-15 out of 80
Question 1
Which type of signed SSL Certificate file formats are compatible with CounterACT?
- A. .Pfx/.p12, .Pfx/.p7
- B. .p7b, .pem
- C. .X.509, x.507
- D. .Pckcs#7, .pckcs#12
- E. .cer, .crt
Answer:
B
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration
and Deployment:
According to the Forescout CLI Reference - Generating CSRs and Importing Signed Certificates
documentation, the SSL certificate file formats compatible with CounterACT are ".p7b" and ".pem".
Supported Certificate Formats:
According to the CLI Reference documentation:
"To import a certificate from DER or P7B formatted files, convert it to PEM file format. Then convert
the PEM files to a single PFX file as described above."
This indicates that:
P7B format - Supported (PKCS#7 container format)
PEM format - Supported and widely used (ASCII-encoded format)
Certificate Format Conversion Process:
According to the documentation:
The standard import process is:
text
Original Format → Conversion → PEM Format → PFX Format → Import to CounterACT
├
─ DER files → Convert → PEM
─ P7B files → Convert → PEM
├
└─ PEM files → Direct use or convert to PFX
Why Other Options Are Incorrect:
A . .Pfx/.p12, .Pfx/.p7 - Pfx is the final format used, not input; p7 is not a standard format
C . .X.509, x.507 - X.509 is a standard (not a format); x.507 is not valid
D . .Pckcs#7, .pckcs#12 - Spelling is "PKCS," not "Pckcs"; these are standards, not file formats
E . .cer, .crt - These are certificate formats but not listed as directly compatible in the documentation
Certificate Import Workflow:
According to the documentation:
Compatible workflow formats:
Input Formats (that need conversion):
DER files → Convert to PEM
P7B files → Convert to PEM
CER files → Convert to PEM
Intermediate Format:
PEM (ASCII-encoded, universally compatible)
Final Format:
PFX (used for CounterACT import)
Referenced Documentation:
Generating CSRs and Importing Signed Certificates - CLI Reference
Product Questions:
Version: Import and Configure System Certificates
Question 2
When an admission event is seen, how are main rules and sub-rules processed?
- A. Main rules process concurrently, sub-rules process sequentially.
- B. Main rules process in parallel, sub-rules process concurrently.
- C. Main rules process concurrently, sub-rules process in parallel.
- D. Main rules process sequentially, sub-rules process concurrently.
- E. Main rules process sequentially, sub-rules process in parallel.
Answer:
A
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration
and Deployment:
According to the Forescout Administration Guide - Policy Processing, when an admission event
occurs, "Main rules process concurrently, sub-rules process sequentially".
Policy Processing Flow:
According to the Main Rule Advanced Options documentation:
When an admission event triggers policy evaluation:
Main Rules - Process concurrently/in parallel
All main rules are evaluated simultaneously
No ordering or sequencing
Each main rule evaluates independently
Sub-Rules - Process sequentially/in order
Sub-rules within each main rule execute one after another
First match wins - stops evaluating subsequent sub-rules
Order matters for sub-rule execution
Main Rule Concurrent Processing:
According to the documentation:
"Main rules are evaluated independently and concurrently. Multiple main rules can be processed
simultaneously for the same endpoint."
Sub-Rule Sequential Processing:
According to the Defining Policy Sub-Rules documentation:
"Sub-rules are evaluated sequentially in the order defined. When an endpoint matches a sub-rule,
that sub-rule's actions are taken and subsequent sub-rules are not evaluated."
Example Processing:
When admission event triggers:
text
CONCURRENT (Main Rules):
├
─ Main Rule 1 evaluation → Sub-rule processing (sequential)
├
─ Main Rule 2 evaluation → Sub-rule processing (sequential)
└─ Main Rule 3 evaluation → Sub-rule processing (sequential)
(All main rules evaluate at the same time)
Why Other Options Are Incorrect:
B . Parallel/Concurrently - "Concurrent" and "parallel" mean the same thing; sub-rules don't process
concurrently
C . Concurrent/Parallel - Sub-rules don't process in parallel; they're sequential
D . Sequential/Concurrently - Main rules don't process sequentially; they're concurrent
E . Sequential/Parallel - Main rules don't process sequentially; they're concurrent
Referenced Documentation:
Main Rule Advanced Options
Defining Policy Sub-Rules
Question 3
Which of the following is an example of a remediation action?
- A. Start SecureConnector
- B. Start Antivirus update
- C. Assign to VLAN
- D. Switch port block
- E. HTTP login
Answer:
B
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration
and Deployment:
According to the Forescout Administration Guide - Remediate Actions, "Start Antivirus update" is an
example of a remediation action.
Remediation Actions Definition:
According to the Remediate Actions documentation:
"Remediation actions are actions that address compliance issues by taking corrective measures on
endpoints. These actions fix, update, or improve the security posture of non-compliant endpoints."
Examples of Remediation Actions:
According to the documentation:
Remediation actions include:
Start Antivirus Update - Updates antivirus definitions on the endpoint
Update Antivirus - Updates antivirus software
Start Windows Updates - Initiates Windows security patches
Enable Firewall - Activates Windows firewall
Disable USB - Restricts USB access
Why Other Options Are Incorrect:
A . Start SecureConnector - This is a deployment action, not remediation
C . Assign to VLAN - This is a containment/isolation action (Switch Remediate Action), not a
remediation action
D . Switch port block - This is a containment/restrict action (Switch Restrict Action), not remediation
E . HTTP login - This is authentication, not a remediation action
Action Categories:
According to the documentation:
Category
Examples
Purpose
Remediate Actions
Start Antivirus, Windows Updates, Enable Firewall
Fix compliance issues
Restrict Actions
Switch Block, Port Block, ACL
Contain threats
Remediate Actions (Switch)
Assign to VLAN (quarantine)
Move to isolated VLAN
Deployment
Start SecureConnector
Deploy agents
Referenced Documentation:
Remediate Actions
Switch Remediate Actions
Switch Restrict Actions
Question 4
When using the "Assign to VLAN action," why might it be useful to have a policy to record the
original VLAN?
Select one:
- A. Since CounterACT reads the startup config to find the original VLAN, network administrators making changes to switch running configs could overwrite this VLAN information
- B. Since CounterACT reads the running config to find the original VLAN, network administrators saving configuration changes to switches could overwrite this VLAN information
- C. Since CounterACT reads the running config to find the original VLAN, network administrators making changes to switch running configs could overwrite this VLAN information
- D. Since CounterACT reads the running config to find the original VLAN, any changes to switch running configs could overwrite this VLAN information
- E. Since CounterACT reads the startup config to find the original VLAN, network administrators saving configuration changes to switches could overwrite this VLAN information
Answer:
D
Explanation:
According to the Forescout Switch Plugin documentation, the correct answer is: "Since CounterACT
reads the running config to find the original VLAN, any changes to switch running configs could
overwrite this VLAN information".
Why Recording Original VLAN is Important:
According to the documentation:
When CounterACT assigns an endpoint to a quarantine VLAN:
Reading Original VLAN - CounterACT reads the switch running configuration to determine the
original VLAN
Temporary Change - The endpoint is moved to the quarantine VLAN
Restoration Issue - If network administrators save configuration changes to the running config,
CounterACT's reference to the original VLAN may be overwritten
Solution - Recording the original VLAN in a policy ensures you have a backup reference
Why Option D is the Most Accurate:
Option D states the key issue clearly: "any changes to switch running configs could overwrite this
VLAN information." This is the most comprehensive and accurate statement because it acknowledges
that ANY changes (not just those by administrators specifically) could cause the issue.
Question 5
Which of the following does NOT need to be checked when you are verifying correct switch plugin
configuration?
- A. The Switch plugin is running
- B. Correct switch management credentials are configured for each switch
- C. IP address ranges are assigned to the correct appliance
- D. Each switch passes the plugin test
- E. Each switch is assigned to the correct appliance
Answer:
C
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration
and Deployment:
According to the Forescout Switch Plugin Configuration Guide, when verifying correct switch plugin
configuration, you do NOT need to check: "IP address ranges are assigned to the correct appliance".
This setting is network/appliance configuration, not switch plugin-specific configuration.
Switch Plugin Configuration Verification Checklist:
According to the Switch Plugin documentation:
When verifying switch plugin configuration, you MUST check:
A . The Switch plugin is running
✓
Plugin status must be active
Verify in plugin management interface
B . Correct switch management credentials
✓
SSH/CLI credentials configured
SNMP credentials (v1/v2/v3) configured
Must have appropriate permissions
D . Each switch passes the plugin test
✓
Use plugin test function to verify connectivity
Confirms credentials and permissions work
Validates communication protocols
E . Each switch is assigned to the correct appliance
✓
Switch must be assigned to managing appliance
Critical for multi-appliance deployments
Ensures proper VLAN management traffic routing
Why C is NOT Required:
According to the documentation:
IP address range assignment (segment assignment) is:
Part of appliance channel/segment configuration
NOT part of switch plugin-specific configuration
Handled at appliance level, not plugin level
Related to appliance management, not switch management
Switch Plugin vs. Appliance Configuration:
According to the configuration guide:
Item
Switch Plugin Config
Appliance Config
Yes
Plugin Running
✓
N/A
Yes
Switch Credentials
✓
N/A
Yes
Plugin Test
✓
N/A
Yes
Switch Assignment
✓
N/A
No
Yes
IP Address Ranges
✗
✓
Referenced Documentation:
CounterACT Switch Plugin Configuration Guide v8.12
Switch Configuration Parameters
Permissions Configuration – Switch
Configuring Switches in the Switch Plugin
Question 6
Which of the following statements is true regarding Layer-2 channel?
- A. Recommended when there are a large number of VLANs
- B. Response interface is a VLAN trunk
- C. Monitor interface is a trunk
- D. Utilizes two interfaces
- E. Appliance monitor interface must be connected to an access layer switch
Answer:
D
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration
and Deployment:
According to the Forescout Installation Guide and Working with Appliance Channel Assignments
documentation, a Layer-2 channel "Utilizes two interfaces" - one monitor interface and one response
interface.
Layer-2 Channel Structure:
According to the documentation:
"A channel defines a pair of interfaces used by the Appliance to protect your network. In general,
one interface monitors traffic going through the network (the monitor interface), and the other
responds to traffic on the network (the response interface)."
Two Interface Components:
According to the Installation Guide:
Monitor Interface:
Monitors and tracks network traffic
Traffic is mirrored from switch ports
No IP address required
Can be any available interface
Response Interface:
Responds to monitored traffic
Used for policy actions and protections
Configuration depends on VLAN tagging
Can be same VLAN or trunk configuration
Layer-2 vs. Layer-3 Channel:
According to the documentation:
Layer-2 Channel - Two interfaces (monitor and response)
Layer-3 Channel - Uses IP layer for response
Why Other Options Are Incorrect:
A . Recommended for large number of VLANs - Actually, Layer-2 channels with VLAN tagging are
recommended for multiple VLANs, but this doesn't define what a Layer-2 channel is
B . Response interface is a VLAN trunk - While response interface CAN be a trunk for multiple VLANs,
it's not required for all configurations
C . Monitor interface is a trunk - The monitor interface receives mirrored traffic; trunk configuration
depends on VLAN setup
E . Must be connected to access layer switch - The appliance can connect to various switch types; not
specifically limited to access layer
Referenced Documentation:
Working with Appliance Channel Assignments
Quick Installation Guide v8.4
Quick Installation Guide v8.2
Add Channels
Monitor Interface
Set up the Forescout Platform Network
Question 7
The host property 'HTTP User Agent banner' is resolved by what function?
- A. Device classification engine
- B. NetFlow
- C. NMAP scanning
- D. Packet engine
- E. Device profile library
Answer:
D
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration
and Deployment:
According to the Forescout Administration Guide - Advanced Classification Properties, the host
property "HTTP User Agent banner" is resolved by the Packet Engine.
HTTP User Agent Banner Property:
According to the Advanced Classification Properties documentation:
The HTTP User Agent property is captured through passive network traffic analysis by the Packet
Engine, which monitors and analyzes HTTP headers in network traffic.
Packet Engine Function:
According to the Packet Engine documentation:
The Packet Engine provides:
Passive Traffic Monitoring - Analyzes network packets without interfering
HTTP Header Analysis - Extracts HTTP headers from captured traffic
User Agent Detection - Identifies HTTP User Agent strings from web requests
Property Resolution - Populates device properties from observed traffic
HTTP User Agent Examples:
Common User Agent banners that identify device types and browsers:
text
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko)
Chrome/91.0.4472.124 Safari/537.36
Mozilla/5.0 (iPhone; CPU iPhone OS 14_6 like Mac OS X) AppleWebKit/605.1.15
Mozilla/5.0 (Linux; Android 11; SM-G991B) AppleWebKit/537.36
Why Other Options Are Incorrect:
A . Device classification engine - The classification engine uses properties resolved by other
components like the Packet Engine
B . NetFlow - NetFlow provides flow statistics, not application-level data like HTTP headers
C . NMAP scanning - NMAP performs active port scanning, not passive HTTP header analysis
E . Device profile library - The profile library uses properties; it doesn't resolve them
Property Resolution by Function:
According to the documentation:
Property
Packet Engine
NMAP
Device Class Engine
Profile Library
Yes
No
No
No
HTTP User Agent
✓
✗
✗
✗
No
Yes
No
No
Service Banner
✗
✓
✗
✗
Yes
No
OS Classification
Partial
Partial
✓
✗
No
No
Yes
Yes
Function
✗
✗
✓
✓
Referenced Documentation:
Advanced Classification Properties
About the Packet Engine
Forescout Platform Dependencies and Known Issues
Question 8
Which of the following is the best way to brand the CounterACT HTTP pages to look like corporate
internal web pages?
- A. Using the "Reports Portal," modify the CSS for the desired skins
- B. This is not possible with CounterACT portal and HTTP pages
- C. Using the "User Portal Builder," modify the CSS for the desired skins
- D. Have a webmaster modify the HTML pages within the Tomcat web server
- E. Using the "User Portal Builder" basic interface
Answer:
C
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration
and Deployment:
According to the Forescout Administration Guide, the best way to brand CounterACT HTTP pages to
match corporate identity is to use "the 'User Portal Builder' to modify the CSS for the desired skins".
This is the officially supported method for customizing the appearance of Forescout portal pages.
User Portal Builder for Branding:
The User Portal Builder provides:
CSS Customization - Modify cascading stylesheets to match corporate branding
Skin Selection - Choose different portal skins/themes
Logo and Colors - Customize logos, color schemes
Supported Customization - Official, supported method through the GUI
Why Option C is Correct:
The User Portal Builder specifically provides CSS modification capabilities to customize the
appearance of Forescout HTTP portal pages to match organizational branding standards.
Why Other Options Are Incorrect:
A . Reports Portal - Reports Portal is separate from HTTP portal pages; not for branding
B . Not possible - Customization IS possible through User Portal Builder
D . Modify HTML in Tomcat - While technically possible, this is NOT supported; may break with
updates
E . Basic interface only - The full User Portal Builder supports CSS modification, not just basic
interface
Supported Customization Methods:
According to the documentation:
User Portal Builder (CSS) - Supported, recommended method
✓
Direct Tomcat HTML modification - Not supported; unsupported method
✗
Manual CSS editing - Unsupported; may conflict with updates
✗
Referenced Documentation:
Forescout Administration Guide - User Portal Builder section
Question 9
Which type of endpoint can be queried for registry key properties?
- A. Managed unknown endpoint
- B. Unmanaged Windows endpoint
- C. Managed Windows endpoint
- D. Windows endpoint
- E. Managed Linux endpoint
Answer:
C
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration
and Deployment:
According to the Forescout Administration Guide - Set Registry Key on Windows action, registry key
properties can only be queried on "Managed Windows endpoints".
Registry Key Property Requirements:
According to the Set Registry Key on Windows documentation:
"Registry key properties can be queried on managed Windows endpoints only. The endpoint must be
a Windows device that is managed (either via SecureConnector deployment or Remote Inspection
with appropriate credentials)."
Managed vs. Unmanaged Endpoints:
According to the Windows Properties documentation:
Managed Windows Endpoint -
Can query registry keys
✓
Has SecureConnector deployed, OR
Has Remote Inspection access via credentials, OR
Is domain-joined with appropriate permissions
Unmanaged Windows Endpoint -
Cannot query registry keys
✗
No agent or access method available
Registry cannot be accessed remotely
Why Other Options Are Incorrect:
A . Managed unknown endpoint - "Unknown" endpoints are not classified as Windows; classification
unknown
B . Unmanaged Windows endpoint - Unmanaged endpoints have no access to registry
D . Windows endpoint - Must be "managed" to query registry; not all Windows endpoints are
managed
E . Managed Linux endpoint - Linux systems don't have Windows registry
Registry Access Methods:
According to the documentation:
Registry keys can be queried on Managed Windows endpoints using:
SecureConnector - Preferred method for interactive registry access
Remote Inspection (MS-WMI/RPC) - When credentials are configured
Domain Credentials - When endpoint is domain-joined
Referenced Documentation:
Set Registry Key on Windows - v9.1.4
Set Registry Key on Windows - v8.5.2
Windows Properties
Question 10
Which of the following lists contain items you should verify when you are troubleshooting a failed
switch change VLAN action?
Select one:
- A. The Switch Vendor is compatible for the change VLAN action The Enterprise manager IP is allowed read VLAN access to the switch The network infrastructure allows CounterACT SSH and SNMP Get traffic to reach the switch The action is disabled in the policy The Switch Model is compatible for ACL actions The Enterprise manager IP is allowed write VLAN changes to the switch The network infrastructure allows CounterACT SSH and SNMP Trap traffic to reach the switch The action is enabled in the policy
- B. The Switch Vendor is compatible for the change VLAN action The managing appliance IP is allowed read VLAN access to the switch The network infrastructure allows CounterACT SSH and SNMP Get traffic to reach the switch The action is disabled in the policy
- C. The Switch Model is compatible for the change VLAN action The managing appliance IP is allowed write VLAN changes to the switch The network infrastructure allows CounterACT SSH and SNMP Set traffic to reach the switch The action is enabled in the policy
- D. The Switch Vendor is compatible for all actions The managing appliance IP is allowed read VLAN access to the switch The network infrastructure allows CounterACT SSH and SNMP Set traffic to reach the switch The action is enabled in the policy
Answer:
C
Explanation:
According to the Forescout Switch Plugin Configuration Guide Version 8.12 and 8.14.2, when
troubleshooting a failed change VLAN action, you should verify: "The Switch Model is compatible for
the change VLAN action, The managing appliance IP is allowed write VLAN changes to the switch,
The network infrastructure allows CounterACT SSH and SNMP Set traffic to reach the switch, The
action is enabled in the policy".
Troubleshooting Switch VLAN Changes:
According to the Switch Plugin documentation:
When a VLAN assignment fails, verify:
Switch Model Compatibility
Not all switch models support VLAN changes via SNMP/SSH
Consult Forescout compatibility matrix
Refer to Appendix 1 of Switch Plugin guide for capability summary
Managing Appliance Permissions
The managing appliance must have write access to VLAN settings
Requires appropriate SNMP community strings or SNMPv3 credentials
Must be allowed to execute SNMP Set commands
Network Infrastructure
SSH access to the switch (CLI) - typically port 22
SNMP Set traffic to the switch - port 161
NOT "SNMP Get" (read-only) or "SNMP Trap" (notifications)
SNMP Set is specifically for write operations like VLAN assignment
Policy Action Status
The action must be enabled in the policy
If the action is disabled, it won't execute regardless of other settings
Why Option C is Correct:
According to the documentation:
Switch Model (not Vendor) - Model-specific capabilities matter
✓
Managing appliance (not Enterprise Manager) - For distributed deployments
✓
SNMP Set (not Get or Trap) - Required for write/change operations
✓
Action enabled (not disabled) - Prerequisite for execution
✓
Why Other Options Are Incorrect:
A - Mixes incorrect items: "action is disabled" is wrong; "SNMP Trap" is for notifications, not VLAN
changes
B - States "SNMP Get" (read-only) instead of "SNMP Set" (write); has "action is disabled"
D - Says "all actions" instead of "change VLAN action"; uses "SNMP Set" correctly but other details
wrong
Referenced Documentation:
Forescout CounterACT Switch Plugin Configuration Guide v8.12
Switch Plugin Configuration Guide v8.14.2
Switch Configuration Parameters
Switch Restrict Actions
Question 11
Based on ForeScout's recommended troubleshooting approach, where should you start the
troubleshooting process?
- A. Run fstool tech-support
- B. Check that requirements are met
- C. Look at dependencies
- D. Examine the GUI Logs
- E. Review command line logs
Answer:
B
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration
and Deployment:
According to the Forescout troubleshooting methodology, the recommended starting point for the
troubleshooting process is to "Check that requirements are met". This foundational step must come
before any detailed investigation.
Forescout Troubleshooting Approach:
The basic troubleshooting workflow consists of:
text
Step 1: CHECK THAT REQUIREMENTS ARE MET (START HERE)
├
─ System requirements
├
─ Software versions
─ Network connectivity
├
└─ Licensing
Step 2: Look at Dependencies
─ Network dependencies
├
├
─ Service dependencies
└─ Appliance dependencies
Step 3: Gather Information from CounterACT
├
─ GUI logs
├
─ Properties
└─ Policies
Step 4: Gather Information from Command Line
─ CLI logs
├
└─ Network diagnostics
Step 5: Form Hypothesis and Diagnose
─ Analyze findings
├
└─ Determine root cause
Why Checking Requirements is the First Step:
According to the troubleshooting best practices:
Foundation - Verifying requirements prevents wasting time on invalid configurations
System Integrity - Ensures all prerequisites are met before investigating issues
Efficiency - Many issues stem from unmet requirements; fixing these resolves the problem
immediately
Logical Flow - Without meeting requirements, no further troubleshooting will be effective
Why Other Options Are Incorrect:
A . Run fstool tech-support - This is an advanced diagnostic tool, not the starting point
C . Look at dependencies - Dependencies are examined AFTER confirming requirements are met
D . Examine the GUI Logs - Logs are reviewed AFTER requirements and dependencies are checked
E . Review command line logs - CLI logs are examined later in the process, not first
Requirements Verification Includes:
According to the methodology:
System Requirements
Supported OS versions
Memory and storage requirements
CPU specifications
Software Versions
Forescout platform version
Plugin/module compatibility
Browser versions for Console
Network Connectivity
IP address configuration
Network interfaces
Firewall rules
Licensing
Valid licenses
License not expired
License for required modules
Referenced Documentation:
Basic troubleshooting approach methodology
Question 12
Which field in the User Directory plugin should be configured for Active Directory subdomains?
- A. Replicas
- B. Address
- C. Parent Groups
- D. Domain Aliases
- E. DNS Detection
Answer:
D
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration
and Deployment:
According to the Forescout User Directory Plugin Configuration Guide - Microsoft Active Directory
Server Settings, the field that should be configured for Active Directory subdomains is "Domain
Aliases".
Domain Aliases for Subdomains:
According to the Microsoft Active Directory Server Settings documentation:
"Configure the following additional server settings in the Directory and Additional Domain Aliases
sections: Domain Aliases - Configure additional domain names that users can use to log in, such as
subdomains."
Purpose of Domain Aliases:
According to the documentation:
Domain Aliases are used to specify:
Subdomains - Alternative domain names like subdomain.company.com
Alternative Domain Names - Other domain name variations
User Login Options - Additional domains users can use to authenticate
Alias Resolution - Maps aliases to the primary domain
Example Configuration:
For an organization with the primary domain company.com and subdomain accounts.company.com:
Domain Field - Set to: company.com
Domain Aliases Field - Add: accounts.company.com
This allows users from either domain to authenticate successfully.
Why Other Options Are Incorrect:
A . Replicas - Replicas configure redundant User Directory servers, not subdomains
B . Address - Address field specifies the server IP/FQDN, not domain aliases
C . Parent Groups - Parent Groups relate to group hierarchy, not domain subdomains
E . DNS Detection - DNS Detection is not a User Directory configuration field
Additional Domain Configuration:
According to the documentation:
text
Primary Configuration:
─ Domain: company.com
├
├
─ Domain Aliases: accounts.company.com
│
services.company.com
│
mail.company.com
└─ Port: 636 (default)
Referenced Documentation:
Microsoft Active Directory Server Settings
Define User Directory Servers - Domain Aliases section
Question 13
When configuring a Send Email action to notify CounterACT administrators, how do you add
endpoint specific host information to the message?
- A. Create criteria in sub-rules to detect the desired specific host information. The "Send Email" action will send this information to the CounterACT administrator.
- B. Edit the "Message to Email Recipient" Field of the Send Email action Parameters tab, then click 'Tag" to add the desired property value.
- C. Edit the Options > General > Mail settings and click "Tag" to add the desired property values.
- D. It is not possible to add specific host information for detected endpoints.
- E. Edit the "Message to Email Recipient" Field of the Send Email action Parameters tab, then click 'Tag" to add the desired keyword tag.
Answer:
B
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration
and Deployment:
According to the Forescout Administration Guide - Send Email action documentation, to add
endpoint-specific host information to a Send Email notification, you should "Edit the 'Message to
Email Recipient' Field of the Send Email action Parameters tab, then click 'Tag' to add the desired
property value".
Property Tags in Send Email Action:
According to the Property Tags documentation:
"Property tags insert endpoint values into condition or action fields, and are replaced by the actual
endpoint property value when the field is evaluated."
Property tags allow dynamic insertion of endpoint-specific data into email messages.
How to Add Property Tags to Email:
According to the documentation:
Edit Send Email Action - Open the Send Email action configuration
Navigate to Parameters Tab - Select the Parameters tab
Edit Message Field - Edit the "Message to Email Recipient" field
Click Tag Button - Select the "Tag" button/option
Choose Property - Select the endpoint property to insert (e.g., IP address, OS, etc.)
Confirm - The property tag is inserted into the message
Example Email Message with Property Tags:
According to the More Action Tools documentation:
text
Example message:
"Endpoint [IP.Address] with hostname [IP.Hostname]
has failed compliance check for operating system [OS]."
When evaluated:
"Endpoint 192.168.1.50 with hostname WORKPC-01
has failed compliance check for operating system Windows 10."
Available Properties for Tags:
According to the documentation:
Property tags can reference:
IP Address
MAC Address
Hostname
Operating System
Device Function
User information
Custom endpoint properties
Why Other Options Are Incorrect:
A . Create criteria in sub-rules - Sub-rules don't send email; they're for conditional logic
C . Edit Options > General > Mail settings - This is for global email configuration, not message
customization
D . It is not possible - Incorrect; property tags specifically enable this functionality
E . "Keyword tag" - The feature uses "property tags" or "tags," not "keyword tags"
Referenced Documentation:
Send Email action
Property Tags
More Action Tools - Property tags section
Question 14
Which of the following requires secure connector to resolve?
- A. Authentication login (advanced)
- B. Authentication certificate status
- C. HTTP login user
- D. Authentication login
- E. Signed-In status
Answer:
D
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration
and Deployment:
According to the Forescout HPS Inspection Engine Configuration Guide and Remote Inspection
Feature Support documentation, "Authentication login" requires SecureConnector to resolve.
Authentication Login Property:
According to the Remote Inspection and SecureConnector Feature Support documentation:
The "Authentication login" property requires SecureConnector because:
Interactive User Information - Requires access to active user session data
Real-Time Verification - Must check current login status
Endpoint Agent Needed - Cannot be determined via passive network monitoring or remote registry
SecureConnector Required - Installed agent must report login status
SecureConnector vs. Remote Inspection:
According to the HPS Inspection Engine guide:
Some properties require different capabilities:
Property
Remote Inspection (MS-WMI/RPC)
SecureConnector
No
Yes
Authentication login
✗
✓
No
Yes
Authentication login (advanced)
✗
✓
No
Yes
Signed-In status
✗
✓
No
Yes
HTTP login user
✗
✓
Yes
Yes
Authentication certificate status
✓
✓
Why Other Options Are Incorrect:
A . Authentication login (advanced) - While this also requires SecureConnector, the base
"Authentication login" is the more accurate answer
B . Authentication certificate status - This can be resolved via Remote Inspection using certificate
stores
C . HTTP login user - This is resolved by SecureConnector, but not listed as requiring it in the same
way
E . Signed-In status - While this requires SecureConnector, the more specific answer is
"Authentication login"
SecureConnector Capabilities:
According to the documentation:
SecureConnector resolves endpoint properties that require:
Active user session information
Real-time application/browser monitoring
Deep endpoint inspection
Interactive user credentials
Referenced Documentation:
Remote Inspection and SecureConnector – Feature Support
Using Certificates to Authenticate the SecureConnector Connection
Question 15
Irresolvable hosts would match the condition. When configuring policies, which of the following
statements is true regarding this image?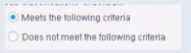
Select one:
- A. Has no effect on irresolvable hosts
- B. Generates a NOT condition in the sub-rule condition
- C. Negates the criteria outside the property
- D. Modifies the irresolvable condition to TRUE
Answer:
A
Explanation:
Based on the image showing "Meets the following criteria" radio button selected (as opposed to
"Does not meet the following criteria"), the correct statement is: "Has no effect on irresolvable
hosts".
Understanding "Meets the following criteria":
According to the Forescout policy configuration documentation:
When "Meets the following criteria" is selected:
Normal Evaluation - The condition is evaluated as written
No Negation - There is NO inversion of logic
Irresolvable Handling - Separate setting; the "Meets" choice does NOT affect irresolvable handling
Irresolvable Hosts - Independent Setting:
According to the policy sub-rule advanced options documentation:
"The 'Meets the following criteria' radio button and the 'Evaluate irresolvable as' checkbox are
independent settings."
"Meets the following criteria" - Controls normal/negated evaluation
"Evaluate irresolvable as" - Controls how unresolvable properties are treated
The selection of "Meets the following criteria" has no specific effect on how irresolvable hosts are
handled.
Why Other Options Are Incorrect:
B . Generates a NOT condition - "Meets" does NOT generate NOT; it's the normal condition
C . Negates the criteria outside - "Meets" does not negate anything; it's the affirmative option
D . Modifies irresolvable condition to TRUE - The "Evaluate irresolvable as" setting controls that, not
"Meets"
Referenced Documentation:
Define policy scope
Forescout eyeSight policy sub-rule advanced options
Forescout Platform Policy Sub-Rule Advanced Options