Eccouncil 312-96 Exam Questions
Questions for the 312-96 were updated on : Jan 31 ,2026
Page 1 out of 4. Viewing questions 1-15 out of 47
Question 1
Suppose there is a productList.jsp page, which displays the list of products from the database for the
requested product category. The product category comes as a request parameter value. Which of the
following line of code will you use to strictly validate request parameter value before processing it for
execution?
- A. public boolean validateUserName() {String CategoryId= request.getParameter("CatId");}
- B. public boolean validateUserName() { Pattern p = Pattern.compile("[a-zA-Z0-9]*$"); Matcher m = p.matcher(request.getParameter(CatId")); boolean result = m.matches(); return result;}
- C. public boolean validateUserName() { if(request.getParameter("CatId")!=null ) String CategoryId=request.getParameter("CatId");}
- D. public.boolean validateUserName() { if(!request.getParamcter("CatId").equals("null"))}
Answer:
B
Question 2
Identify the type of encryption depicted in the following figure.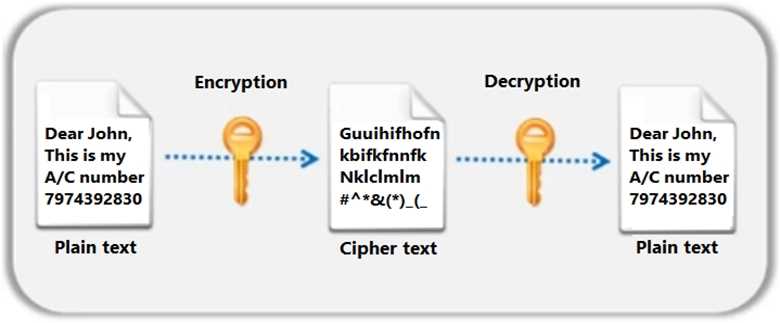
- A. Asymmetric Encryption
- B. Digital Signature
- C. Symmetric Encryption
- D. Hashing
Answer:
C
Question 3
The developer wants to remove the HttpSessionobject and its values from the client' system.
Which of the following method should he use for the above purpose?
- A. sessionlnvalidateil
- B. Invalidate(session JSESSIONID)
- C. isValidateQ
- D. invalidateQ
Answer:
D
Question 4
During his secure code review, John, an independent application security expert, found that the
developer has used Java code as highlighted in the following screenshot. Identify the security
mistake committed by the developer?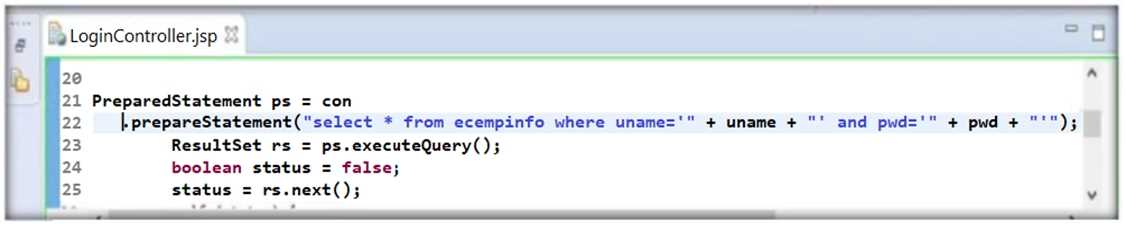
- A. He is trying to use Whitelisting Input Validation
- B. He is trying to use Non-parametrized SQL query
- C. He is trying to use Blacklisting Input Validation
- D. He is trying to use Parametrized SQL Query
Answer:
B
Question 5
Identify the type of attack depicted in the figure below: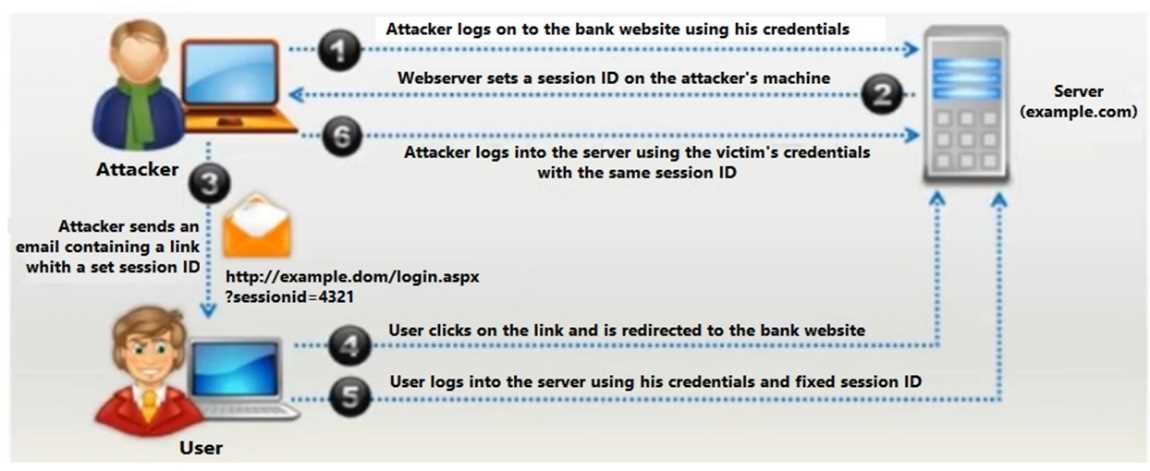
- A. SQL injection attack
- B. Parameter/form attack
- C. Directory traversal attack
- D. Session fixation attack
Answer:
D
Question 6
Thomas is not skilled in secure coding. He neither underwent secure coding training nor is aware of
the consequences of insecure coding. One day, he wrote code as shown in the following screenshot.
He passed 'false' parameter to setHttpOnly() method that may result in the existence of a certain
type of vulnerability. Identify the attack that could exploit the vulnerability in the above case.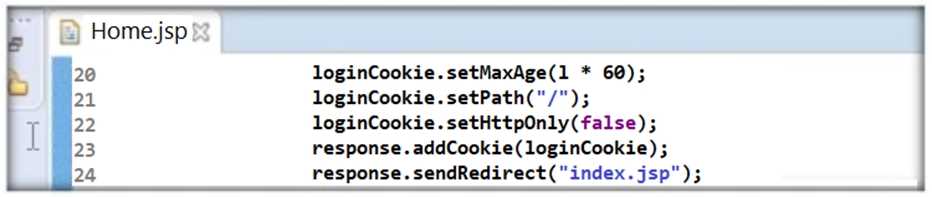
- A. Denial-of-Service attack
- B. Client-Side Scripts Attack
- C. SQL Injection Attack
- D. Directory Traversal Attack
Answer:
B
Question 7
Which of the following method will you use in place of ex.printStackTrace() method to avoid printing
stack trace on error?
- A. ex.StackTrace.getError();
- B. ex.message();
- C. ex.getMessage();
- D. ex.getError();
Answer:
C
Question 8
Identify what should NOT be catched while handling exceptions.
A EOFException
B. SecurityException
C. IllegalAccessException
D. NullPointerException
Answer:
B
Question 9
To enable the struts validator on an application, which configuration setting should be applied in the
struts validator configuration file?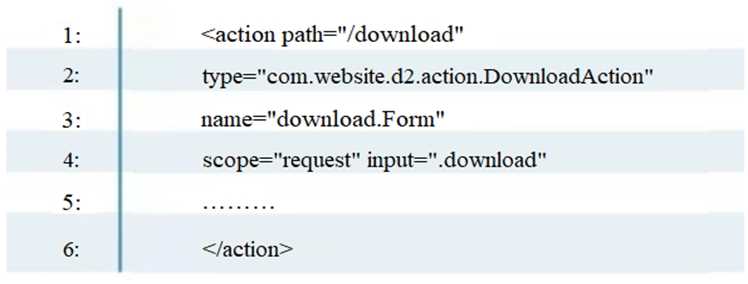
- A. valid ate-'true"
- B. lsNotvalidate="disabled"
- C. lsNotvalidate="false"
- D. validate="enabled"
Answer:
A
Question 10
Which of the following relationship is used to describe abuse case scenarios?
- A. Include Relationship
- B. Threatens Relationship
- C. Extend Relationship
- D. Mitigates Relationship
Answer:
B
Question 11
It is recommended that you should not use return, break, continue or throw statements in
_________
- A. Finally block
- B. Try-With-Resources block
- C. Try block
- D. Catch block
Answer:
A
Question 12
Which of the following is used to mapCustom Exceptions to Statuscode?
- A. @ResponseStatus
- B. @ResponseStatusCode
- C. @ResponseCode
- D. @ScacusCode
Answer:
A
Question 13
Which of the following authentication mechanism does J2EE support?
- A. Windows, Form based. Role Based, Client/Server Mutual Authentication
- B. Role Based, Http Basic, Windows, Http Digest Authentication
- C. Http Basic, Form Based, Client/Server Mutual, Role Based Authentication
- D. Http Basic, Form Based, Client/Server Mutual, HTTP Digest Authentication
Answer:
D
Question 14
Which of the following state management method works only for a sequence of dynamically
generated forms?
- A. Cookies
- B. Sessions
- C. Hidden Field
- D. URL-rewriting
Answer:
C
Question 15
Which of the following can be derived from abuse cases to elicit security requirements for software
system?
- A. Misuse cases
- B. Data flow diagram
- C. Use cases
- D. Security use cases
Answer:
D