Dell EMC DES-DD33 Exam Questions
Questions for the DES-DD33 were updated on : Jul 20 ,2024
Page 1 out of 4. Viewing questions 1-15 out of 54
Question 1
Which PowerProtect DD technology provides fast and efficient deduplication while minimizing disk
access?
- A. SISL
- B. Cloud Tier
- C. Cache Tier
- D. DIA
Answer:
B
Reference:
https://www.delltechnologies.com/asset/en-in/products/data-protection/technical-
support/h17926-dellemc-powerprotect-dd-ds.pdf
Question 2
Backup administrators have noticed slow backups on the AIX environment.
To fix the issue, what should the set large_send be for each NIC, and what should the NFS option be
set to?
- A. no and nfs_rfc1323=0
- B. yes and nfs_rfc1323=0
- C. no and nfs_rfc1323=1
- D. yes and nfs_rfc1323=1
Answer:
D
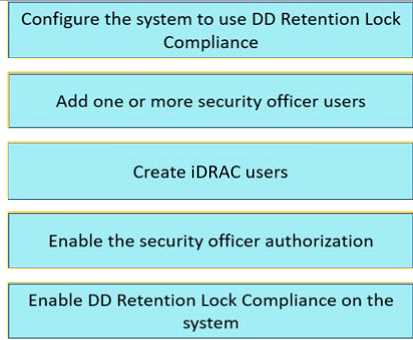
Question 3
DRAG DROP
What are the steps to configure the Retention Lock Compliance?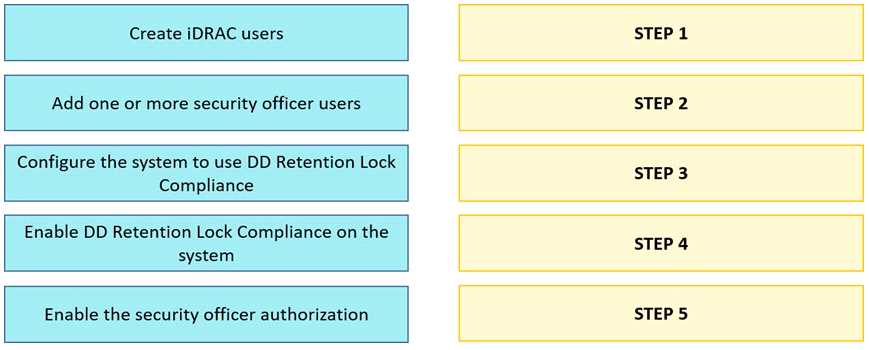
Answer:
Question 4
An administrator is scaling Cloud Tier for a DD9400 by adding a second cloud unit.
What is the required amount of metadata storage ()?
- A. 120
- B. 240
- C. 300
- D. 500
Answer:
B
Question 5
A storage administrator finished the zoning between the PowerProtect DD and the NetWorker
backup server.
How can they verify that the zoning was completed properly and the server HBA are visible?
- A. scsitarget initiator show list
- B. scsitarget initiator list
- C. scsitarget show initiator
- D. scsitarget show initiator list
Answer:
A
Question 6
A PowerProtect DD backup administrator wants to delegate some Operations to their Monitoring
and Control team. The administrator wants to add a user to the Monitoring and Control team with
limited access to only check the health of the PowerProtect DD appliance.
Which role must be applied to the new user?
- A. Backup Operator
- B. Limited Admin
- C. User
- D. Tenant Admin
Answer:
C
Explanation:
The User role provides read-only access to monitor activities and operations.
Reference:
https://www.delltechnologies.com/asset/en-us/products/data-protection/technical-
support/docu95705.pdf
Question 7
Following best practices for a PowerProtect DD NFS environment, what is the recommended value
for rsize and wsize?
- A. 22768
- B. 30008
- C. 32768
- D. 42768
Answer:
C
Reference:
https://docs.oracle.com/en/database/oracle/oracle-database/18/cwlin/configuring-nfs-buffer-size-parameters-for-oracle-database.html#GUID-5F14F816-445B-4EBB-BBA2-E9DFD7E5EF96
Question 8
What is the maximum capacity that a cloud unit can have with DD9900?
- A. 64 TB
- B. 576 TB
- C. 1,536 TB
- D. 2,016 TB
Answer:
B
Reference:
https://nsrd.info/blog/2019/09/26/powerprotect-dd-unleash-the-beast/
Question 9
What system role is required to create the second security officer for a PowerProtect DD?
- A. limited-admin
- B. security officer
- C. sysadmin
- D. admin
Answer:
B
Explanation:
A security role user, who may be referred to as a security officer, can manage other security officers,
authorize procedures that require security officer approval, and perform all tasks supported for user-
role users.
Reference:
https://www.delltechnologies.com/asset/en-us/products/data-protection/technical-
support/docu97051.pdf
Question 10
Which are supported compression algorithms in DDOS?
- A. lz, gz, and gzfast
- B. bmp, lz, and gz
- C. rle, lzw, and lz
- D. dsp, gz, and lz
Answer:
A
Explanation:
Prior generation appliances compressed data using the default lz algorithm. Other types of
compression algorithms such as gzfast and gz were also available.
Reference:
https://www.delltechnologies.com/asset/en-sa/products/data-protection/industry-
market/dell-emc-powerprotect-dd-series-appliances-hardware-assisted-compression.pdf
Question 11
Which component executes the read/write requests in a backup environment consisting of a
PowerProtect DD appliance and IBM Spectrum Protect?
- A. Media Server
- B. Media Agent
- C. Spectrum Protect Server
- D. Master Server
Answer:
B
Question 12
When using the DD VTL Tape Out to Cloud feature, which status will a tape show once it is in the
cloud tier vault?
- A. Vaulted
- B. Archived
- C. Offline
- D. Offsite
Answer:
B
Question 13
Which protocol is used for communications between a PowerProtect DD appliance and cloud tier to
Dell EMC ECS?
- A. HTTP
- B. SSH
- C. FTP
- D. SSL
Answer:
A
Reference:
https://www.dell.com/support/kbdoc/en-pk/000020178/data-domain-import-ssl-root-ca-
cert-from-load-balancer-for-ecs-cloud-tier-and-best-practices
Question 14
DRAG DROP
What is the correct sequence of steps to configure storage for Dell EMC Cloud Tier in the DD System
Manager?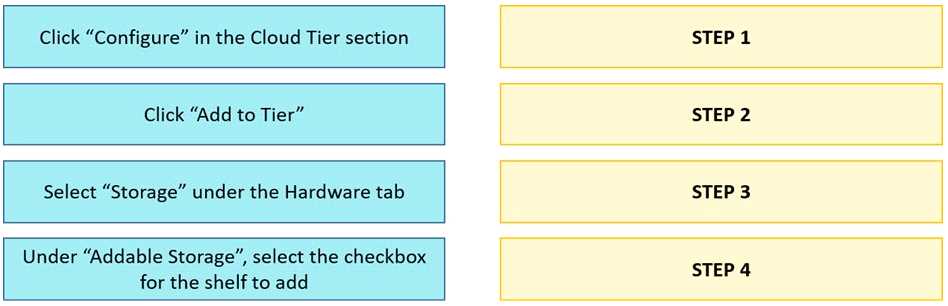
Answer:

Reference:
https://www.delltechnologies.com/asset/en-us/products/data-protection/technical-
support/docu95865.pdf
Question 15
Which statement is correct regarding backup flow without PowerProtect DD?
- A. Data is replicated between primary storage and tape storage
- B. Both the backup server and backup clients connect directly to tapes and save the backup
- C. Only the backup server connects directly to tapes and saves the backup
- D. Only backup clients connect directly to tapes and save the backup
Answer:
C
Reference:
https://www.ibm.com/cloud/learn/backup-and-restore