Dell EMC DEA-3TT2 Exam Questions
Questions for the DEA-3TT2 were updated on : Jul 05 ,2025
Page 1 out of 4. Viewing questions 1-15 out of 60
Question 1
DRAG DROP
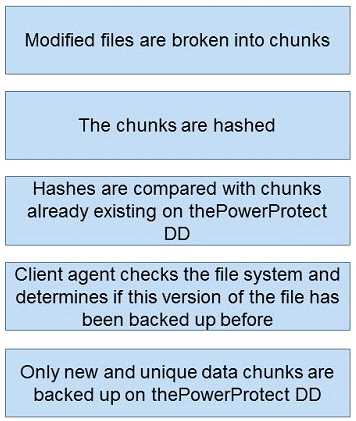
What is the correct sequence of actions during a DDBoost backup?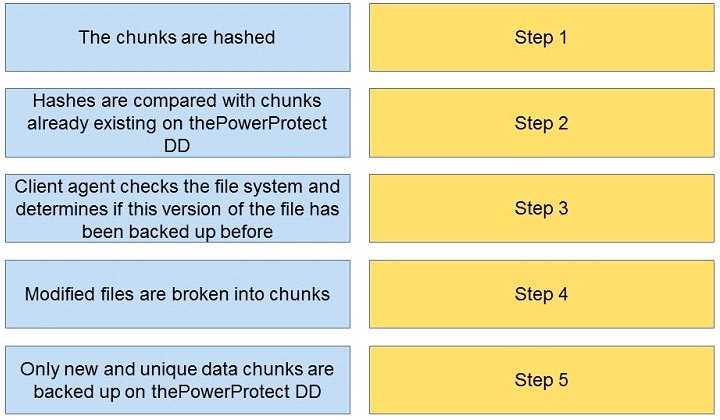
Answer:
Question 2
What is the primary disadvantage of incremental backups?
- A. time-consuming to restore
- B. contain only the blocks that have changed since the previous backup
- C. increased amount of data going across the network
- D. can grow to contain a large amount of data
Answer:
A
Reference:
https://iosafe.com/data-protection-topics/3-types-of-backup
Question 3
What is true of hot-swappable hardware?
- A. All components need to be rearranged after swap
- B. Reboot is required after a change
- C. All fans need to be running to ensure proper cooling
- D. Replaceable with zero downtime
Answer:
D
Reference:
https://whatis.techtarget.com/definition/hot-swap
Question 4
Which Dell EMC Storage product family does SRDF support?
- A. Unity
- B. PowerMax
- C. PowerScale
- D. PowerStore
Answer:
B
Reference:
https://www.delltechnologies.com/asset/en-us/products/storage/technical-
support/docu95482.pdf
Question 5
Which type of virtual machine clone is created from a snapshot of a parent VM?
- A. Mirrored Clone
- B. Full Clone
- C. Linked Clone
- D. Snap Clone
Answer:
C
Reference:
https://www.vmware.com/support/ws5/doc/ws_clone_typeofclone.html
Question 6
A backup of 20 GB of data is reduced by a deduplication algorithm to 4 GB of dat
a. What is the deduplication ratio?
- A. 1:20
- B. 5:1
- C. 20:1
- D. 1:5
Answer:
D
Reference:
https://www.tsmadmin.com/2015/02/data-domain-compression.html
Question 7
What assurance does the content authenticity feature of CAS provide?
- A. Storing only one instance of content
- B. Stored content is protected against erasure
- C. Validity of stored content
- D. There are always multiple copies
Answer:
C
Explanation:
CAS assures the genuineness of stored content. This is achieved by generating a unique content
address for each object and validating the content address for stored objects at regular intervals.
Content authenticity is assured because the address assigned to each object is as unique as a
fingerprint. Every time an object is read, CAS uses a hashing algorithm to recalculate the objects
content address as a validation step and compares the result to its original content address. If the
object fails validation, CAS rebuilds the object using a mirror or parity protection scheme.
Question 8
Which key metric should be used when updating the corporate disaster recovery plan to minimize
data loss?
- A. MTTR
- B. MTBF
- C. RPO
- D. RTO
Answer:
C
Reference:
https://www.cockroachlabs.com/blog/demand-zero-
rpo/#:~:text=RPO%20(which%20stands%20for%20Recovery,to%20recover%20from%20a%20failure
Question 9
Which describes graceful degradation?
- A. The application detects a fault in the system and properly shuts down all modules to keep all data consistent
- B. Some modules are unavailable, but the entire application has not been brought down
- C. All modules are still available, but response times are degraded
- D. The application informs the end user their business is important and that the service will be back up as soon as possible
Answer:
B
Reference:
https://www.techtarget.com/searchnetworking/definition/graceful-degradation
Question 10
An application developer is exploring the best technology to have the application easily
transportable and have a small image footprint. Which technology satisfies the request?
- A. Containers
- B. Traditional application
- C. Virtual machines
- D. Monolithic application
Answer:
A
Reference:
https://searchcloudsecurity.techtarget.com/feature/Cloud-containers-what-they-are-and-
how-they-work
Question 11
Refer to the exhibit.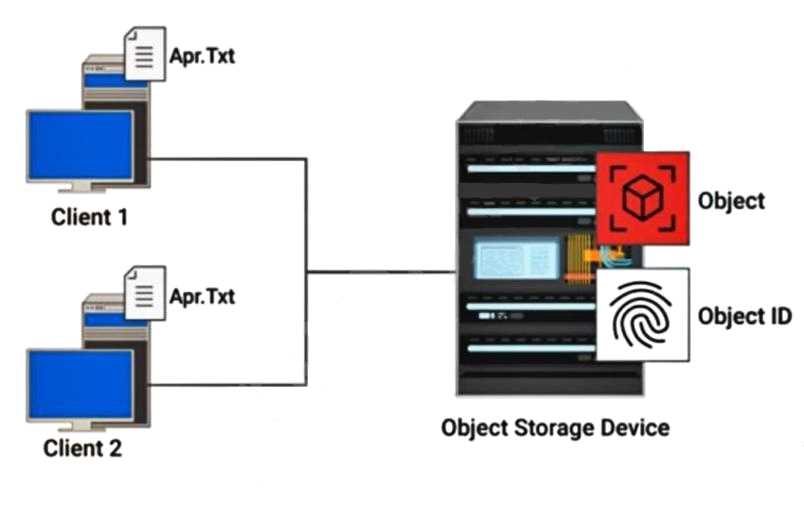
How is a hash created on file Apr.Txt in an object-level deduplication?
- A. from content with variable-length
- B. from the metadata of the file
- C. from the content of the file
- D. from content with fixed-length
Answer:
B
Reference:
https://www.delltechnologies.com/asset/he-il/products/storage/industry-
market/h17072-data-reduction-with-dell-emc-powermax.pdf
Question 12
What are the key functions of data management?
- A. detection and orchestration management
- B. discovery and operations management
- C. configuration and detection management
- D. rollout and configuration management
Answer:
B
Reference:
https://www.delltechnologies.com/en-gb/learn/data-protection/intelligent-data-
management.htm
Question 13
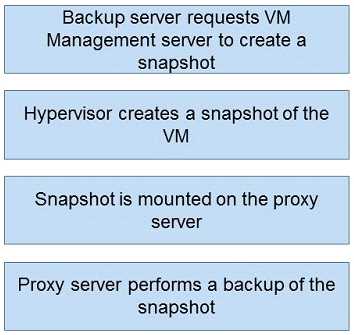
DRAG DROP
What is the correct sequence of steps during an image-based backup?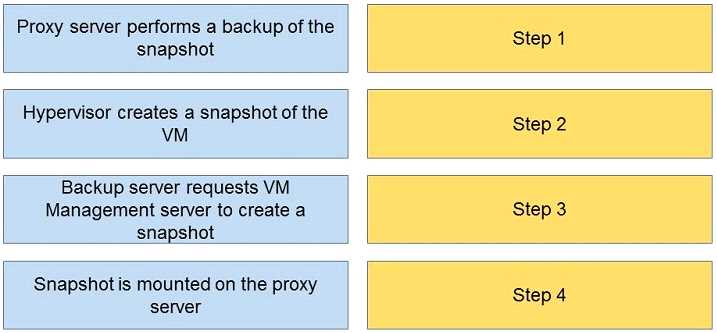
Answer:
Question 14
What does the Cloud Gateway Appliance provide?
- A. translation layer between standard storage interfaces and cloud service provider
- B. backup access to the cloud service provider
- C. translation layer between standard network interfaces and cloud service provider
- D. VPN access to the cloud service provider
Answer:
C
Reference:
https://education.dellemc.com/content/dam/dell-emc/documents/en-
us/2013KS_Panchanathan-What_Why_and_How_of_Cloud_Storage_Gateway.pdf
(3)
Question 15
When is the target available for use in pointer-based replication?
- A. once the fracture log has been created
- B. after the mirror has been fractured
- C. immediately after session activation
- D. after synchronization has completed
Answer:
C
Reference:
https://webcache.googleusercontent.com/search?q=cache:IGSfpLzWKy8J:https://www.shcollege.ac.
in/wp-content/uploads/NAAC_Documents_IV_Cycle/Criterion-
II/2.3.2/Semester5_FOS_Storagebasedarray.pptx+&cd=7&hl=en&ct=clnk&gl=pk