Dell EMC DEA-1TT4 Exam Questions
Questions for the DEA-1TT4 were updated on : Jun 27 ,2025
Page 1 out of 9. Viewing questions 1-15 out of 122
Question 1
What is an accurate statement about Governance?
- A. Restrict access to certain users
- B. Ensure removal of security risks
- C. Authorize policy-making decisions
- D. Demonstrate adherence to polices
Answer:
C
Question 2
Which exhibit represents a Type 1 hypervisor?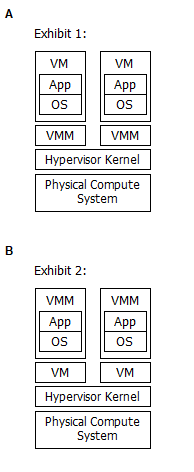
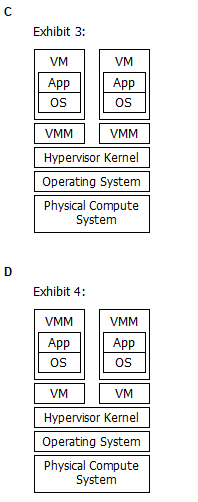
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
A
Question 3
An Ethernet switch has eight ports and all ports must be operational for 24 hours, from Monday
through Friday. However, a failure of Port4 occurs as follows:
Monday = 8 PM to 9 PM
Wednesday 7 PM to 9 PM
Thursday = 6 AM to 9 AM
Saturday = 4 PM to 7 PM
What is the MTTR of Port 4?
A. 2 hours
B. 3 hours
C. 28 hours
D. 38 hours
Answer:
A
MTTR = Total downtime / Number of failures
MTTR = 1+2+3 / 3 = 2
Question 4
What accurately describes an iSCSI HBA?
- A. Performs both iSCSI and TCP/IP processing
- B. Requires CPU cycles for TCP/IP processing
- C. Requires a software adapter with built-in functionality
- D. Enables transmission of data through iSCSI tunneling
Answer:
A
Reference:
https://www.dell.com/downloads/global/power/ps4q09-20090419-McConnell.pdf
Question 5
When using the erasure coding technique in an object-based storage system, data is divided into 12
data segments and 4 coding segments.
What is the maximum number of disk drive failures against which data is protected by the
configuration?
- A. 3
- B. 4
- C. 8
- D. 12
Answer:
A
Question 6
What is a key advantage of cloning a virtual machine (VM)?
A. Ability to run new VMs simultaneously with the same IP address.
B. Reduces the time required to create multiple copies of a VM.
C. Improves the performance of an existing VM and new VMs.
D. Eliminates the need to create multiple snapshots for a VM.
Answer:
B
VM clone Clone is a copy of an existing virtual machine (parent VM) o The clone VMs MAC address
is different from the parent VM Typically clones are deployed when many identical VMs are required
o Reduces the time that is required to deploy a new VM
Question 7
A company is using an intrusion detection and prevention system (IDPS) to scan and analyze
intrusion events.
Which IDPS technique uses a database that contains known attack patterns?
- A. Role-based
- B. Profile-based
- C. Signature-based
- D. Anomaly-based
Answer:
C
Reference:
https://pdfs.semanticscholar.org/e874/32283e90da5bceb3b17550570ec3a210f43c.pdf
Question 8
DRAG DROP
In a backup operation, what are the correct sequence of steps after the backup server initiates the
scheduled backup process?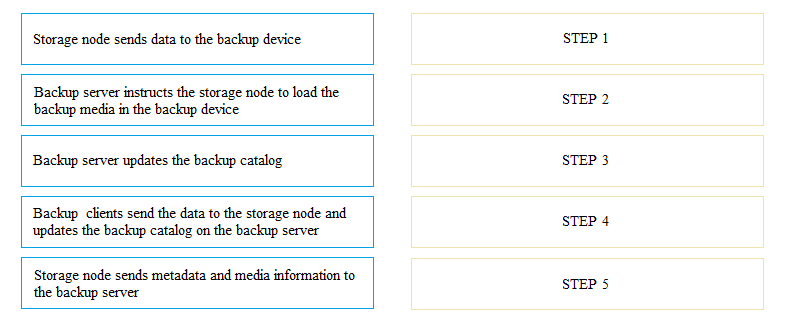
Answer:
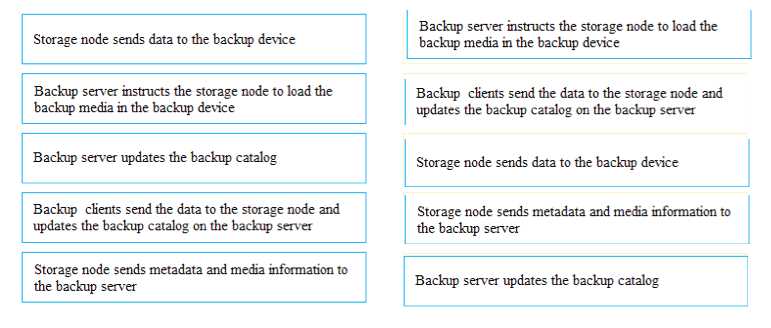
Question 9
In an archiving environment, how is a content address created in a content addressable storage (CAS)
system to store an object?
- A. From the metadata of an object.
- B. By using the logical address of the memory space.
- C. From the binary representation of an object.
- D. By using the physical address of the storage device.
Answer:
C
Question 10
What is a benefit of link aggregation?
- A. Optimizes fabric performance by distributing network traffic across ISLs.
- B. Improves ISL utilization by increasing the network traffic on a specific ISL.
- C. Yields a higher throughput by combining two parallel ISLs into a single physical ISL.
- D. Saves bandwidth by restricting traffic to a specific potentially congested ISL.
Answer:
A
Reference:
https://www.mycloudwiki.com/san/fc-san-topologies/
Question 11
In a compute-based storage area network (SAN), what is a function of the metadata manager?
- A. Holds cluster-wide mapping information and load balancing in a compute-based SAN.
- B. Performs the I/O operations on the local storage of a compute system as requested by a client.
- C. Provides an interface to the software-defined storage controller.
- D. Controls all data read and write operations in a compute-based SAN.
Answer:
A
Question 12
Why is it important for organizations to store, protect, and manage their data?
- A. Reduce the amount of data to be replicated, migrated, and backed up.
- B. Rapidly develop and deploy modern applications for business improvement.
- C. Develop new business opportunities by leveraging existing data.
- D. Reduce the complexity in managing the data center environment.
Answer:
C
Question 13
A Fibre Channel switch has eight ports and all ports must be operational 247. However, a failure of
Port 5 occurs on a particular week as follows:
Monday = 11 AM to 12 PM
Thursday = 7 AM to 11 AM
Saturday = 11 AM to 1 PM
What is the availability of Port 5 in that week?
A. 93%
B. 94.1%
C. 95.8%
D. 97%
Answer:
C
Total uptime / Number of failures
MTBF =
Question 14
Which layer of the OSI model provides the functional and procedural methods to transfer data
between network entities?
- A. Data link
- B. Presentation
- C. Session
- D. Application
Answer:
A
Reference:
https://en.wikibooks.org/wiki/Network_Plus_Certification/Management/OSI_Model
Question 15
What is an accurate statement about variable prefetching?
- A. Many blocks that have recently been written to storage by the compute system are retrieved and placed in cache.
- B. Many non-contiguous blocks that are not currently required can be retrieved from cache in advance.
- C. Storage system prefetches data in multiples of the original I/O request size from the compute system.
- D. Storage system prefetches many non-contiguous blocks of data, with varied sizes, from cache.
Answer:
D