CyberArk EPM-DEF Exam Questions
Questions for the EPM-DEF were updated on : Feb 18 ,2026
Page 1 out of 4. Viewing questions 1-15 out of 60
Question 1
What is the CyberArk recommended practice when deploying the EPM agent to non-persistent VDIs?
- A. A separate set
- B. a VDI advanced policy
- C. a separate license
- D. A separate computer group
Answer:
D
Question 2
How does CyberArk EPM's Ransomware Protection feature monitor for Ransomware Attacks?
- A. It compares known ransomware signatures retrieved from virus databases.
- B. It sandboxes the suspected ransomware and applies heuristics.
- C. It monitors for any unauthorized access to specified files.
- D. It performs a lookup of file signatures against VirusTotal's database.
Answer:
B
Question 3
If Privilege Management is not working on an endpoint, what is the most likely cause that can be
verified in the EPM Agent Log Files?
- A. Behavior of the elevation prompt for administrators in Admin Approval Mode is set to “Prompt for Consent for non-Windows binaries”.
- B. Agent version is incompatible.
- C. UAC policy Admin Approval for the Built-in Administrator Account is set to “Disabled”.
- D. UAC policy Run all administrators in Admin Approval Mode is set to “Enabled”.
Answer:
D
Question 4
When adding the EPM agent to a pre-existing security stack on workstation, what two steps are
CyberArk recommendations. (Choose two.)
- A. Add any pre-existing security application to the Files to Be Ignored Always.
- B. Add EPM agent to the other security tools exclusions.
- C. EPM agent should never be run with any other security tools.
- D. Create new advanced policies for each security tool.
Answer:
A, B
Question 5
For the CyberArk EPM Threat Deception Credential Lure feature, what is the recommendation
regarding the username creation?
- A. The username should match to an existing account.
- B. The username should have a strong password associated.
- C. The username should not match to an existing account.
- D. The username should match the built-in local Administrator.
Answer:
C
Question 6
An EPM Administrator needs to create a policy to allow the MacOS developers elevation to an
application. What type of policy should be used?
- A. Elevate Application Group
- B. Developer Applications Application Group
- C. Elevate Trusted Applications If Necessary Advanced Policy
- D. Elevate MacOS Policy
Answer:
C
Question 7
CyberArk EPM's Ransomware Protection comes with file types to be protected out of the box. If an
EPM Administrator would like to remove a file type from Ransomware Protection, where can this be
done?
- A. Policy Scope within Protect Against Ransomware
- B. Authorized Applications (Ransomware Protection) within Application Groups
- C. Set Security Permissions within Advanced Policies
- D. Protected Files within Agent Configurations
Answer:
D
Question 8
DRAG DROP
Match the Application Groups policy to their correct description.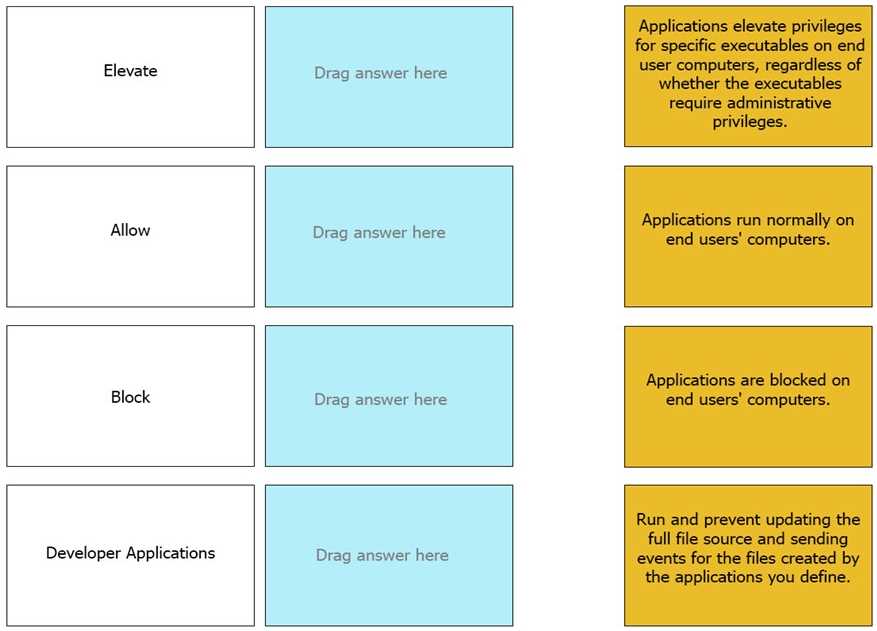
Answer:
None
Explanation: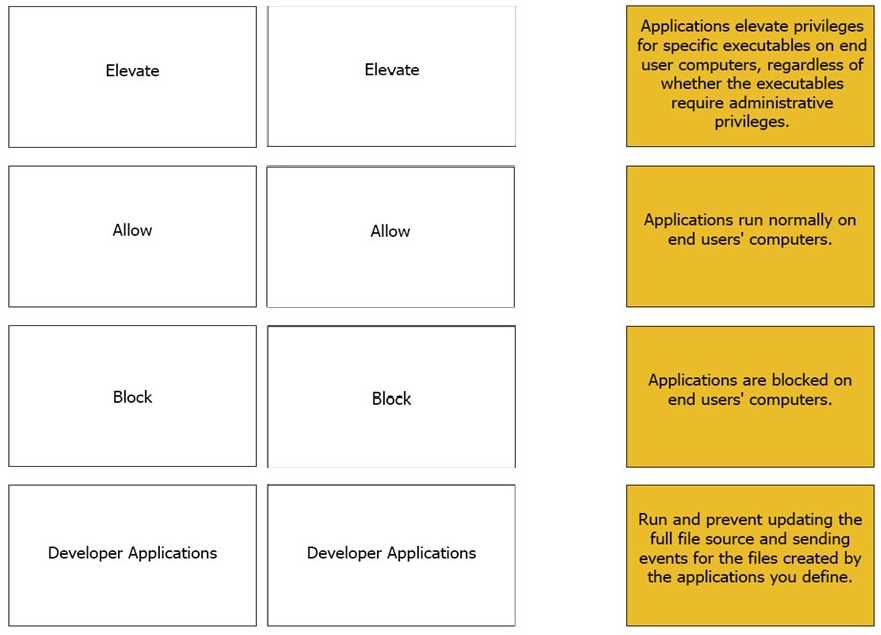
Question 9
Where can you view CyberArk EPM Credential Lures events?
- A. Application Catalog
- B. Threat Protection Inbox
- C. Events Management
- D. Policy Audit
Answer:
B
Explanation:
Reference:
https://docs.cyberark.com/Product-
Doc/OnlineHelp/EPM/21.7/en/Content/EPM/Server%20User%20Guide/Threat%20Detection%20Eve
nts.htm#:~:text=View%20events&text=You%20can%20filter%20the%20list,event%20and%20display
%20more%20details
Question 10
When blocking applications, what is the recommended practice regarding the end-user UI?
- A. Show a block prompt for blocked applications.
- B. Show no prompts for blocked applications.
- C. Hide the CyberArk EPM Agent icon in the system tray.
- D. Enable the Default Deny policy.
Answer:
A
Question 11
A company is looking to manage their Windows Servers and Desktops with CyberArk EPM.
Management would like to define different default policies between the Windows Servers and
Windows Desktops.
What should the EPM Administrator do?
- A. In the Default Policies, exclude either the Windows Servers or the Windows Desktops.
- B. Create Advanced Policies to apply different policies between Windows Servers and Windows Desktops.
- C. CyberArk does not recommend installing EPM Agents on Windows Servers.
- D. Create a separate Set for Windows Servers and Windows Desktops.
Answer:
B
Question 12
Can the EPM Set Administrator configure Audit Dialog Pop-ups for the Record Audit Video option?
- A. Yes, when Audit Video recording started, when Audit Video recording stopped, and when Audit Recording video reached size limit.
- B. Yes, when Audit Video recording started, when not enough disk space to start the video recording, and when video recording is initializing.
- C. Yes, when Audit Video recording started, when Audit Video recording is uploaded to the EPM server, and when audit recording cannot be initialized.
- D. No, Audit Video is only available without the possibility of having End-User dialog pop-ups.
Answer:
D
Question 13
What is required to configure SAML authentication on EPM?
- A. OAuth token
- B. Signed Authentication Request
- C. Encrypted Assertion
- D. Signed SAML Response
Answer:
D
Question 14
An EPM Administrator is looking to enable the Threat Deception feature, under what section should
the EPM Administrator go to enable this feature?
- A. Threat Protection Inbox
- B. Policies
- C. Threat Intelligence
- D. Policy Audit
Answer:
B
Question 15
On the Default Policies page, what are the names of policies that can be set as soon as EPM is
deployed?
- A. Privilege Escalation, Privilege Management, Application Management
- B. Privilege Management, Application Control, Threat analysis
- C. Privilege Management, Threat Protection, Application Escalation Control
- D. Privilege Management, Privilege Threat Protection, Local Privileged Accounts Management
Answer:
D