comptia SY0-601 Exam Questions
Questions for the SY0-601 were updated on : Jul 11 ,2025
Page 1 out of 72. Viewing questions 1-10 out of 711
Question 1
A multinational organization that offers web-based services has datacenters that are located only in the United States; however, a large number of its customers are in Australia, Europe, and China. Payments for services are managed by a third party in the United Kingdom that specializes in payment gateways. The management team is concerned the organization is not compliant with privacy laws that cover some of its customers. Which of the following frameworks should the management team follow?
- A. Payment Card Industry Data Security Standard
- B. Cloud Security Alliance Best Practices
- C. ISO/IEC 27032 Cybersecurity Guidelines
- D. General Data Protection Regulation
Answer:
a
Question 2
Security analysts notice a server login from a user who has been on vacation for two weeks. The analysts confirm that the user did not log in to the system while on vacation. After reviewing packet capture logs, the analysts notice the following: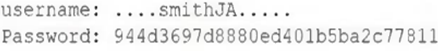
Which of the following occurred?
- A. A buffer overflow was exploited to gain unauthorized access.
- B. The users account was compromised, and an attacker changed the login credentials.
- C. An attacker used a pass-the-hash attack to gain access.
- D. An insider threat with username smithJA logged in to the account.
Answer:
c
Question 3
A database administrator needs to ensure all passwords are stored in a secure manner, so the administrator adds randomly generated data to each password before storing.
Which of the following techniques BEST explains this action?
- A. Predictability
- B. Key stretching
- C. Salting
- D. Hashing
Answer:
c
Question 4
The website http://companywebsite.com requires users to provide personal information, including security question responses, for registration. Which of the following would MOST likely cause a data breach?
- A. Lack of input validation
- B. Open permissions
- C. Unsecure protocol
- D. Missing patches
Answer:
c
Question 5
A security analyst is configuring a large number of new company-issued laptops. The analyst received the following requirements:
The devices will be used internationally by staff who travel extensively.
Occasional personal use is acceptable due to the travel requirements.
Users must be able to install and configure sanctioned programs and productivity suites.
The devices must be encrypted.
The devices must be capable of operating in low-bandwidth environments.
Which of the following would provide the GREATEST benefit to the security posture of the devices?
- A. Configuring an always-on VPN
- B. Implementing application whitelisting
- C. Requiring web traffic to pass through the on-premises content filter
- D. Setting the antivirus DAT update schedule to weekly
Answer:
d
Question 6
In which of the following risk management strategies would cybersecurity insurance be used?
- A. Transference
- B. Avoidance
- C. Acceptance
- D. Mitigation
Answer:
a
Question 7
A security analyst is scanning a company's public network and discovers a host is running a remote desktop that can be used to access the production network. Which of the following changes should the security analyst recommend?
- A. Changing the remote desktop port to a non-standard number
- B. Setting up a VPN and placing the jump server inside the firewall
- C. Using a proxy for web connections from the remote desktop server
- D. Connecting the remote server to the domain and increasing the password length
Answer:
b
Question 8
In which of the following common use cases would steganography be employed?
- A. Obfuscation
- B. Integrity
- C. Non-repudiation
- D. Blockchain
Answer:
a
Question 9
Which of the following examples would be best mitigated by input sanitization?
- A. None
- B. nmap -p- 10.11.1.130
- C. Email message: Click this link to get your free gift card.
- D. Browser message: Your connection is not private.
Answer:
a
Question 10
A security analyst is reviewing the following command-line output: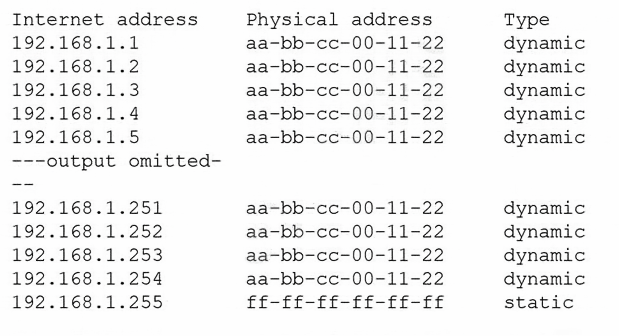
Which of the following is the analyst observing?
- A. ICMP spoofing
- B. URL redirection
- C. MAC address cloning
- D. DNS poisoning
Answer:
a