Citrix 1Y0-440 Exam Questions
Questions for the 1Y0-440 were updated on : Feb 18 ,2026
Page 1 out of 11. Viewing questions 1-15 out of 152
Question 1
Scenario: A Citrix Architect needs to assess an existing on-premises NetScaler deployment which
includes Advanced Endpoint Analysis scans. During a previous security audit, the team discovered
that certain endpoint devices were able to perform unauthorized actions despite NOT meeting pre-
established criteria.
The issue was isolated to several endpoint analysis (EPA) scan settings.
Click the Exhibit button to view the endpoint security requirements and configured EPA policy
settings.
Which setting is preventing the security requirements of the organization from being met?
- A. Item 6
- B. Item 7
- C. Item 1
- D. Item 3
- E. Item 5
- F. Item 2
- G. Item 4
Answer:
E
Question 2
Scenario: A Citrix Architect needs to design a hybrid Citrix Virtual App and Citrix Virtual Desktop
environment which will include as well as resource locations in an on-premises datacenter and
Microsoft Azure.
Organizational details and requirements are as follows:
Active Citrix Virtual App and Citrix Virtual Desktop Service subscription
No existing Citrix deployment
Minimization of additional costs
All users should use same access point, regardless of network location
No multi-factor authentication is required
Click the Exhibit button to view the conceptual environment architecture.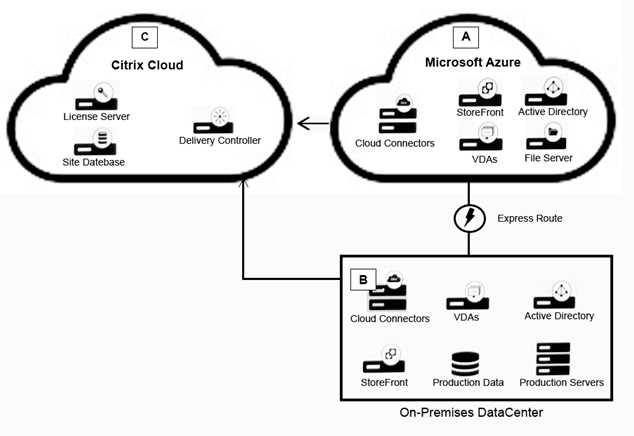
The architect should use___________ in Location A, and should use _______________ in Location B.
(Choose the correct option to complete the sentence.)
- A. No Citrix ADC products; Citrix ICA Proxy (cloud-licensed)
- B. Citrix Gateway as a Service; Citrix ICA Proxy (cloud-licensed)
- C. Citrix Gateway as a Service; no Citrix ADC products
- D. No Citrix ADC products; Citrix Gateway appliance
- E. Citrix gateway as a Service; Citrix ADC (BYO)
- F. No Citrix ADC products; Citrix ADC (BYO)
Answer:
C
Question 3
Scenario: A Citrix Architect needs to design a new multi-datacenter Citrix ADC deployment. The
customer wants Citrix ADC to provide access the various backend resources by using Global Server
Load Balancing (GSLB) in an Active-Active deployment.
Click the Exhibit button to view additional requirements identified by the architect.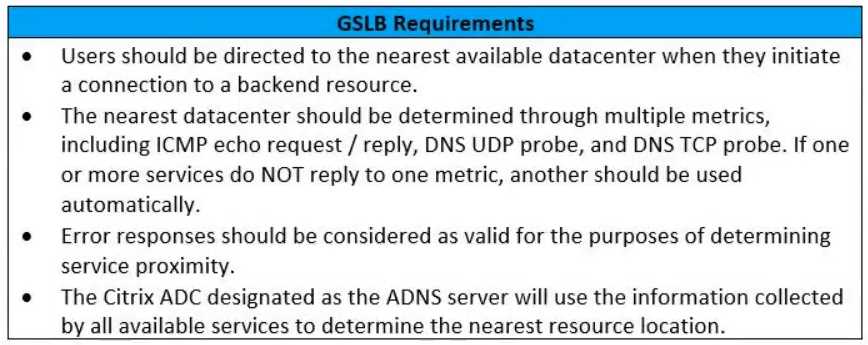
Which GSLB algorithm or method should the architect use for the deployment based on the stated
requirements?
- A. Source IP hash
- B. Least response time
- C. Least connections
- D. Least packets
- E. Static proximity
- F. Dynamic round trip time (RTT)
Answer:
F
Question 4
Scenario: A Citrix Architect has deployed load balancing for SharePoint 2010 on a Citrix ADC instance.
While editing the document, the architect observed the error displayed below:
Sorry, we couldn't open
'https://sharepointcs.emea.in/Shared
Documents/Citrix Enhancement
Request Form.doc'
After troubleshooting, the architect discovers the issue. When a user opens a document, it opens in
the browser, but while editing the document, thd session is transferred from the browser to the
Word application During this time, the cookies should be transferred from the browser to the Word
application.
Which two configurations should the architect modify to ensure that the cookies are shared between
the browser and non-browser applications? (Choose two.)
- A. Enable Persistent Cookie
- B. Disable Persistent Cookie
- C. Set HTTPOnly Cookie to NO
- D. Set the NSC_AAAC cookie with HTTPOnly Flag
- E. Set lb vserver -persistenceType COOKIEINSERT
- F. Set HTTPOnly Cookie to Yes
Answer:
A, C
Question 5
Which StyleBook group should a Citrix Architect use to deploy the configuration for Microsoft
SharePoint servers on Citrix ADC Management and Analytics (Citrix Application Delivery
Management)?
- A. Default
- B. Public
- C. Private
- D. Custom
Answer:
A
Question 6
Scenario: A Citrix Architect and a team of Workspacelab members met to discuss a NetScaler design
project. They captured the following requirements from this design discussion:
A pair of NetScaler MPX appliances will be deployed in the DMZ network.
High Availability will be accessible in the NetScaler MPX in the DMZ Network.
Load balancing should be performed for the internal network services like Microsoft Exchange Client
Access Services and Microsoft App-V.
The load balancing should be performed for StoreFront.
The NetScaler Gateway virtual server will be utilizing the StoreFront load-balancing virtual server.
The NetScaler Gateway virtual server and StoreFront.
The NetScaler Gateway virtual service and StoreFront and load-balancing services are publicly
accessible.
The traffic for internal and external services must be isolated.
Click the Exhibit button to review the logical network diagram.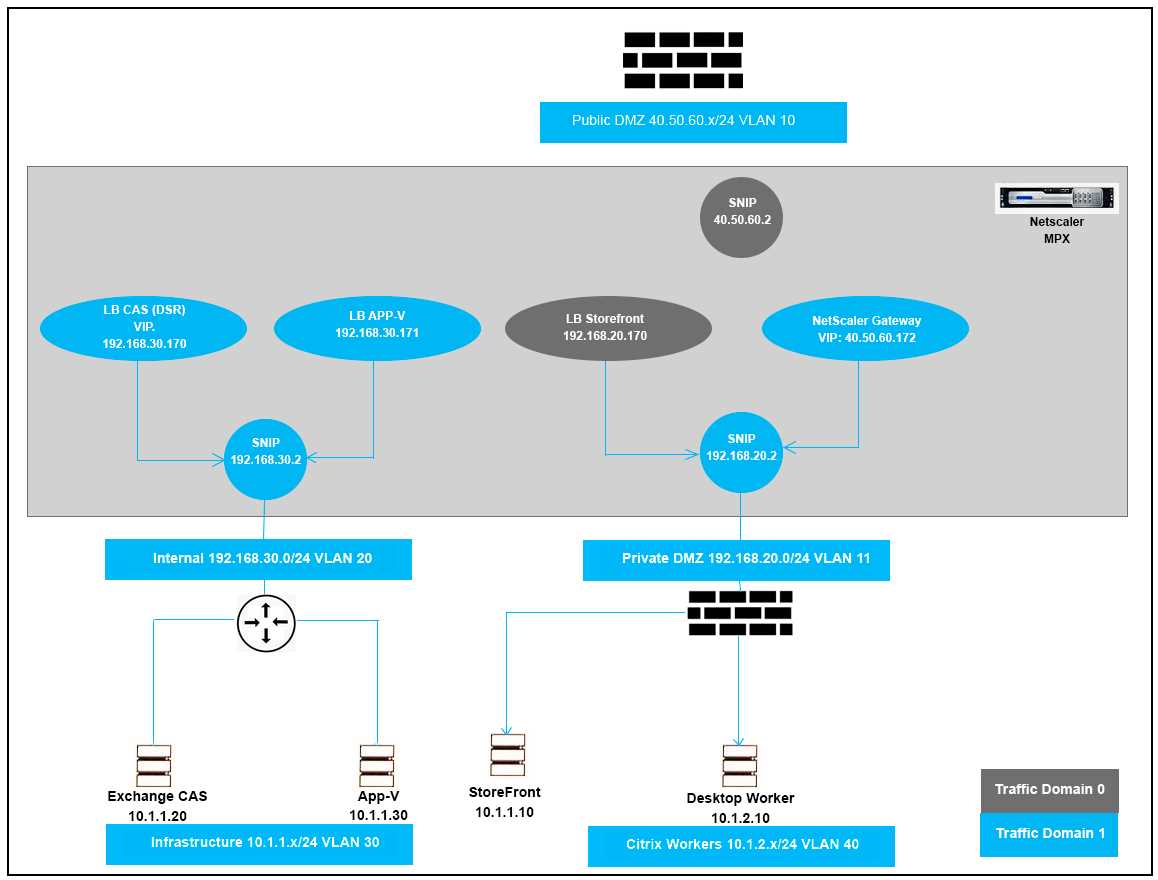
Which two design decisions are incorrect based on these requirements? (Choose two.)
- A. LB StoreFront bound to traffic Domain 0
- B. Citrix Gateway VIP bound to Traffic Domain 1
- C. LB APP-V bound to Traffic Domain 1
- D. SNIP 192.168.20.2 bound to Traffic Domain 1
Answer:
A, B
Question 7
Scenario: A Citrix Architect has met with a team of Workspacelab members for a design discussion
They have captured the following requirements for the Citrix ADC design project:
The authentication must be deployed for the users from the workspacelab com and vendorlab com
domains.
The workspacelab users connecting from the internal (workspacelab) network should be
authenticated using LDAP
The workspacelab users connecting from the external network should be authenticated using LDAP
and RADIUS.
The vendorlab users should be authenticated using Active Directory Federation Service
The user credentials must NOT be shared between workspacelab and vendorlab
Single Sign-on must be performed between StoreFront and Citrix Gateway
A domain drop down list must be provided if the user connects to the Citrix Gateway virtual server
externally
Which method must the architect utilize for user management between the two domains?
- A. Create a global catalog containing the objects of Vendorlab and Workspacelab domains.
- B. Create shadow accounts for the users of the Vendorlab domain in the Workspacelab domain
- C. Create a two-way trust between the Vendorlab and Workspacelab domains
- D. Create shadow accounts for the users of the Workspacelab domain in the Vendorlab domain
Answer:
B
Question 8
Scenario: A Citrix Architect and a team of Workspacelab members met to discuss a Citrix ADC design
project. They captured the following requirements from this design discussion:
All three (3) Workspacelab sites (DC. NDR. and DR) will have similar Citrix ADC configurations and
design.
The external Citrix ADC MPX appliances will have Global Server Load Balancing (GSLB) configured and
deployed in Active/Active mode
ADNS service should be configured on the Citrix ADC to make it authoritative for domain nsg
Workspacelab.com.
In GSLB deployment, the DNS resolution should be performed to connect the user to the site with
least network latency.
On the internal Citrix ADC, load balancing for StoreFront services, Citrix XML services, and Citrix
Director services must be configured
On the external Citrix ADC. the Gateway virtual server must be configured in ICA proxy mode
Click the Exhibit button to view the logical representation of the network and the firewall policy
prerequisites provided by the architect. On which two firewalls should the architect configure the
policies? (Choose two.)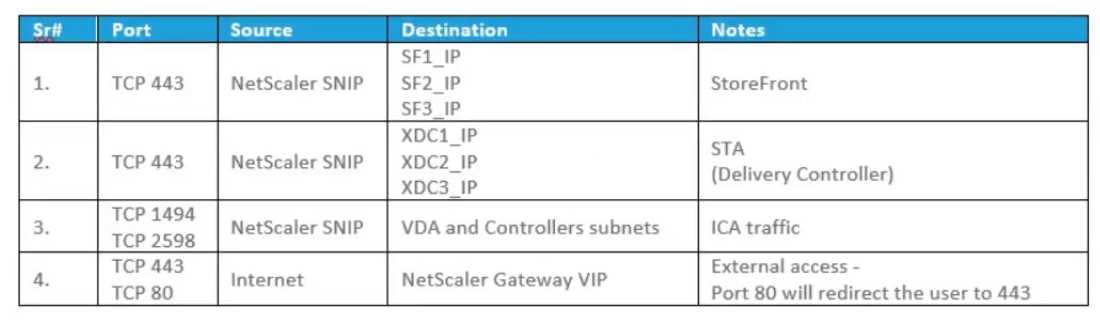
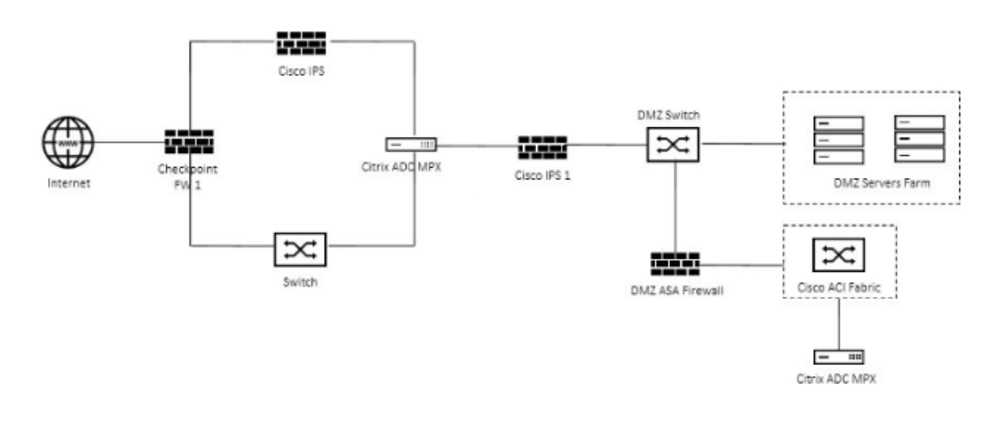
- A. CISCO IPS
- B. CISCO IPS 1
- C. DMZ ASA Firewall
- D. Checkpoint FW1
Answer:
C, D
Question 9
Scenario: A Citrix Architect has configured two MPX devices in high availability mode with version
12.0.53.13 nc. After a discussion with the security team, the architect enabled the Application
Firewall feature for additional protection.
In the initial deployment phase, the following security features were enabled:
IP address reputation
HTML SQL injection check
Start URL
HTML Cross-site scripting
Form-field consistency
After deployment in pre-production, the team identifies the following additional security features
and changes as further requirements:
Application Firewall should retain the response of form field in its memory When a client submits the
form in the next request. Application Firewall should check for inconsistency in the request before
sending it to the web server
All the requests dropped by Application Firewall should receive a pre-configured HTML error page
with appropriate information.
The Application Firewall profile should be able to handle the data from the RSS feed and an ATOM-
based site.
Click the Exhibit button to view an excerpt of the existing configuration.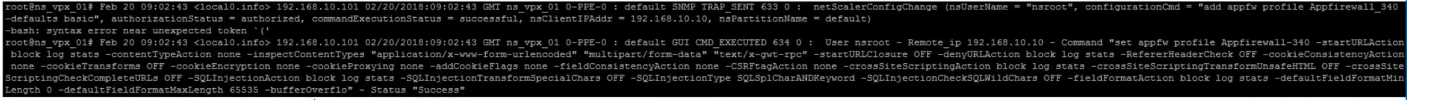
What should the architect do to meet these requirements?
- A. Delete the existing profile and create a new profile of type: XML Application (SOAP)
- B. Modify the existing profile to include sessionization
- C. Create a new basic profile and use pre-existing HTML settings.
- D. Modify existing profile settings, change HTML settings, and ensure to exclude uploaded files from security checks.
Answer:
B
Question 10
A Citrix Architect needs to configure advanced features of Citrix ADC by using StyleBooks as a
resource in the Heat service.
What is the correct sequence of tasks to be completed for configuring Citrix ADC using the Heat
stack?
A.
1. Install Citrix ADC Bundle for OpenStack
2 Register OpenStack with Citrix Application Delivery Management
3. Add Citrix ADC instances (Optional)
4. Create service packages (Add OpenStack tenants)
5. Prepare the HOT by using the Citrix ADC Heat resources and Citrix ADC Network Resource
6. Deploy the Heat stack
B.
1. Install Citrix ADC Bundle for OpenStack
2 Add Citrix ADC instances (Optional)
3. Create service packages (Add OpenStack tenants)
4. Prepare the HOT by using the Citrix ADC Heat resources and Citrix ADC Network Resource
5. Register OpenStack with Citrix Application Delivery Management
6. Deploy the Heat stack
C.
1. Install Citrix ADC Bundle for OpenStack
2. Deploy the Heat stack
3. Register OpenStack with Citrix Application Delivery Management
4. Add Citrix ADC instances (Optional)
5. Prepare the HOT by using the Citrix ADC Heat resources and Citrix ADC Network Resource
6. Create service packages (Add OpenStack tenants)
D.
1. Install NetScaler Bundle for OpenStack
2. Prepare the HOT by using the NetScaler heat resources and NetScaler Network Resource
3. Register OpenStack with NMAS
4. Deploy the Heat stack
5. Add NetScaler instances (Optional)
6. Create service packages (Add OpenStack tenants)
Answer:
A
Explanation: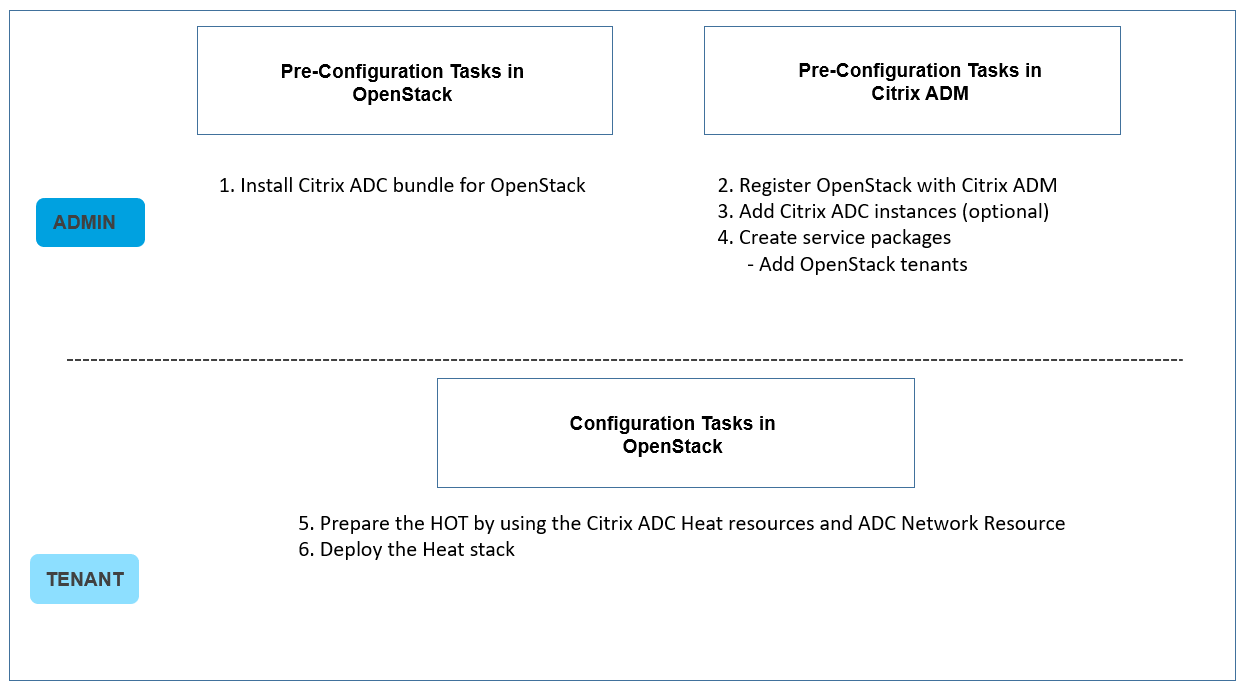
Question 11
Scenario: A Citrix Architect needs to assess a Citrix Gateway deployment that was recently
completed by a customer and is currently in pre-production testing. The Citrix Gateway needs to use
ICA proxy to provide access to a Citrix Virtual Apps and Citrix Virtual Desktops environment. During
the assessment, the customer informs the architect that users are NOT able to launch published
resources using the Gateway virtual server.
Click the Exhibit button to view the troubleshooting details collected by the customer.
What is the cause of this issue?
- A. The Secure Ticket Authority (STA) servers are load balanced on the Citrix ADC.
- B. The required ports have NOT been opened on the firewall between the Citrix Gateway and the Virtual Delivery Agent (VDA) machines
- C. The StoreFront URL configured in the Citrix Gateway session profile is incorrect
- D. The Citrix License Server is NOT reachable
Answer:
A
Question 12
Scenario: Based on a discussion between a Citrix Architect and a team of Workspacelab members,
the MPX Logical layout for Workspacelab has been created across three (3) sites.
They captured the following requirements during the design discussion held for a Citrix ADC design
project:
All three (3) Workspacelab sites (DC NDR and DR) will have similar Citrix ADC configurations and
design
Both external and internal Citrix ADC MPX appliances will have Global Server Load Balancing (GSLB)
configured and deployed in Active/Passive mode
GSLB should resolve both A and AAA DNS queries.
In the GSLB deployment the NDR site will act as backup for the DC site, whereas the DR site will act
as backup for the NDR site
When the external Citrix ADC replies to DNS traffic coming in through Cisco Firepower IPS the replies
should be sent back through the same path
On the internal Citrix ADC. both front-end VIP and back-end SNIP will be part of the same subnet
USIP is configured on the DMZ Citrix ADC appliances
The external Citrix ADC will act as default gateway for back-end servers.
All three (3) sites (DC, NDR, and DR) will have two (2) links to the Internet from different service
providers configured in Active/Standby mode
Which design decision must the architect make to meet the design requirements above?
- A. Mac Based Routing must be configured on the External Citrix ADC
- B. Interface 0/1 must be used for DNS traffic
- C. The SNIP of the external Citrix ADC must be configured as default gateway on the back-end servers
- D. ADNS service must be used with IPv6 address
- E. The SNIP of the internal Citrix ADC must be configured as the default gateway on the back-end servers.
Answer:
E
Question 13
Scenario: A Citrix Architect needs to design a new solution within Amazon Web Services (AWS) The
architect would like to create a high availability Citrix ADC VPX pair to provide load balancing for
applications hosted in the AWS deployment within a single availability zone which will receive traffic
arriving from the Internet.
Which configuration should the architect choose to accomplish this?
- A. Two standalone Citrix ADC instances in the AWS marketplace, then deploy them as a cluster in the AWS management console
- B. A Citrix ADC AWS-VPX Cluster using a Citrix CloudFormation template in the AWS marketplace, then deploy it to create an Active-Passive high availability pair
- C. Two standalone Citrix ADC instances in the AWS marketplace, then deploy them as an Active- Passive high availability pair in the AWS management console
- D. Two standalone Citrix ADC instances in the AWS marketplace, deploy them in the AWS management console, then use an AWS Elastic Load Balancing load balancer to distribute client traffic across both instances
- E. Two Single AMI Citrix CloudFormation templates in the AWS marketplace then configure a high availability pair
Answer:
C
Question 14
Scenario: A Citrix Architect needs to assess a Citrix Gateway deployment that was recently
completed by a customer and is currently in pre-production testing The Citrix Gateway needs to use
ICA proxy to provide access to a Citrix Virtual Apps and Citrix Virtual Desktops environment. During
the assessment, the customer informs the architect that users are NOT able to launch published
resources using the Gateway virtual server.
Click the Exhibit button to view the troubleshooting details collected by the customer.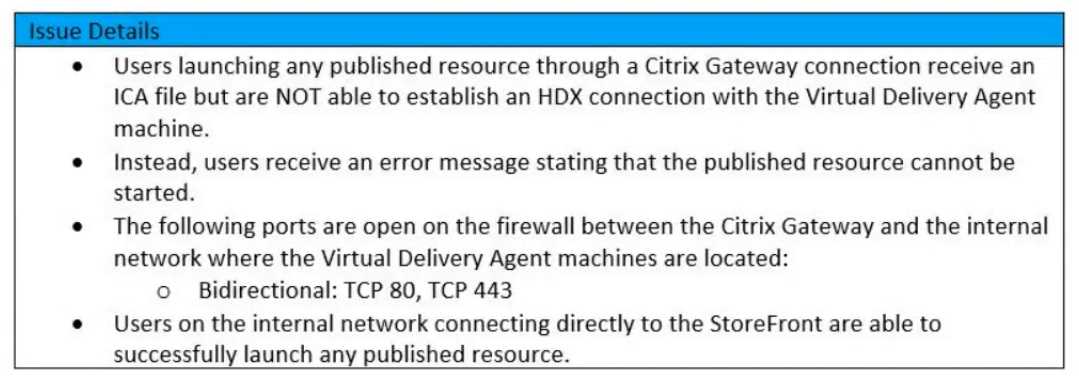
Which two reasons could cause this issue? (Choose two)
- A. The StoreFront URL configured in the Citrix Gateway session profile is NOT correct.
- B. The required ports have NOT been opened on the firewall between the Citrix Gateway and the Virtual Delivery Agent machines
- C. There are no backend Virtual Delivery Agent (VDA) machines available to host the selected published resource
- D. The Secure Ticket Authority (STA) servers have NOT been configured in the Citrix Gateway settings
- E. The two-factor authentication is NOT configured on the Citrix Gateway
Answer:
B, D
Question 15
Scenario: A Citrix Architect has set up Citrix ADC MPX devices in high availability mode with version
12.0.53.13 nc. These are placed behind a Cisco ASA 5505 firewall. The Cisco ASA firewall is configured
to block traffic using access control lists. The network address translation (NAT) is also performed on
the firewall.
The following requirements were captured by the architect during the discussion held as part of the
Citrix ADC security implementation project with the customers security team:
The Citrix ADC MPX device:
should monitor the rate of traffic either on a specific virtual entity or on the device It should be able
to mitigate the attacks from a hostile client sending a flood of requests. The Citrix ADC device should
be able to stop the HTTP TCP. and DNS based requests
needs to protect backend servers from overloading
needs to queue all the incoming requests on the virtual server level instead of the service level
should provide access to resources on the basis of priority
should provide protection against well-known Windows exploits virus-infected personal computers,
centrally managed automated botnets, compromised webservers, known spammers/hackers, and
phishing proxies
should provide flexibility to enforce the desired level of security check inspections for the requests
originating from a specific geolocation database.
should block the traffic based on a pre-determined header length. URL length and cookie length. The
device should ensure that characters such as a single straight quote ('): backslash (\); and semicolon
(;) are either blocked, transformed, or dropped while being sent to the backend server.
Which security feature should the architect configure to meet these requirements?
- A. Configure Application Firewall with HTML cross-site scripting to block unwanted traffic
- B. Configure pattern sets using regular expressions to block attacks
- C. Configure Signatures manually and apply them to the Application Firewall profile
- D. Configure signatures to auto-update and apply them to the Application Firewall profile
- E. Configure IP address reputation and use IPREP and webroot to block the traffic
Answer:
A