cisco 400-007 Exam Questions
Questions for the 400-007 were updated on : Feb 18 ,2026
Page 1 out of 27. Viewing questions 1-15 out of 397
Question 1
Company XYZ, a global content provider, owns data centers on different continents. Their data center
design involves a standard three-layer design with a Layer 3-only core. HSRP is used as the FHRP.
They require VLAN extension across access switches in all data centers, and they plan to purchase a
Layer 2 interconnection between two of their data centers in Europe. In the absence of other
business or technical constraints, which termination point is optimal for the Layer 2 interconnection?
- A. at the core layer, to otter the possibility to isolate STP domains
- B. at me aggregation layer because it is the Layer 2 to Layer 3 demarcation point
- C. at the access layer because the STP root bridge does not need to align with the HSRP active node.
- D. at the core layer because all external connections must terminate there for security reasons
Answer:
B
Question 2
When a company network architect is working on a new network design, they are expected to
ensure that business requirements and technical aspects are factored in, but often there are other
factors that comes into play as well Which non-business constraint must also be considered
throughout the design phase?
- A. location
- B. cost
- C. time
- D. compliance
Answer:
D
Question 3
During a pre-sales meeting with a potential customer the customer CTO asks a question about
advantages of controller-based networks versus a traditional network What are two advantages to
mention? (Choose two)
- A. per device forwarding tables
- B. programmatic APIs available per device
- C. abstraction of individual network devices
- D. distributed control plane
- E. consistent device configuration
Answer:
C, E
Question 4
An Agile for Infrastructure transition often means dismantling traditional IT hierarchies and
rebuilding it to align with business objectives and workflows Organizations are seeing the benefits of
using automation tools in the network such as faster more efficient more effective delivery of
products and services. Which two components help increasing overall productivity and improve
company culture? (Choose two.)
dedicated infrastructure
- A. Agile code practices
- B. infra structure-as-code
- C. controlled infrastructure
- D. DevOps practices
Answer:
B, D
Question 5
DRAG DROP
As technologies such as big data, cloud, and loT continue to grow, so will the demand for network
bandwidth Business strategies must be flexible to accommodate these changes when it comes to
priorities and direction and the network design strategy also must be agile and adaptable Drag and
drop the benefits from the left onto the corresponding strategic approaches on the right as they
relate to network design and management.
Answer:
None
Explanation:
Question 6
Over the years, many solutions have been developed to limit control plane state which reduces the
scope or the speed of control plane information propagation Which solution removes more specific
information about a particular destination as topological distance is covered in the network?
- A. aggregation
- B. summarization
- C. back-off timers
- D. layering
Answer:
B
Question 7
The goal for any network designer is to strive to build a resilient network that adapts to changing
conditions rapidly with minimal impact on the services running over the network A resilient network
can adapt to failures but which soft failure can be harder to define and detect?
- A. a network with operational challenges due to lack of skills
- B. a network that is not running in an optimal way
- C. a network which does not solve complexity issues
- D. a network or service that experiences outages
Answer:
B
Question 8
Refer to the exhibit.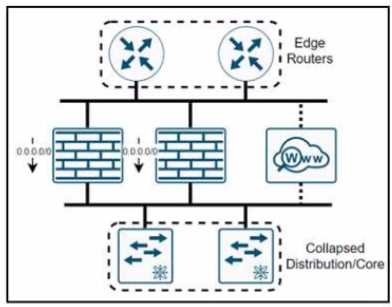
A company named XYZ needs to apply security policies for end-user browsing by installing a secure
web proxy appliance All the web traffic must be inspected by the appliance, and the remaining traffic
must be inspected by an NGFW that has been upgraded with intrusion prevention system
functionality In which two ways must the routing be performed? (Choose two )
constraint-based OSPF routing
- A. policy-based routing on the collapsed core
- B. policy-based routing on the internet edge
- C. policy-based routing on firewalls
- D. static routing on the appliance
Answer:
B, D
Question 9
A company is reviewing their technology roadmap ahead of their cloud journey The as-is assessment
found that a large inventory (5000+) of servers sees less than 50% capacity utilization Which cloud
architecture model supports the company to optimize the resource utilization'?
- A. homogenous cloud
- B. heterogenous cloud
- C. hybrid-private cloud
- D. public cloud
Answer:
B
Question 10
Feature-rich networks are complex network models that provide one or more features in addition to
the network topology In attributed networks, attributes are assigned to the nodes to describe the
corresponding entities For example, in a friendship network the actors can be described by their
genre and their age Which two alternative network models can be used to model interaction over
time or to model each attribute by a specific relationship?
- A. heterogeneous network
- B. information network
- C. location-aware network
- D. multilayer network
- E. probabilistic network
- F. temporal network
Answer:
D, F
Question 11
DRAG DROP
While computer networks and sophisticated applications have allowed individuals to be more
productive the need to prepare for security threats has increased dramatically A six-step
methodology on security incident handling has been adopted by many organizations including
service providers enterprises, and government organizations to ensure that organizations are aware
of significant security incidents and act quickly to stop the attacker, minimize damage caused, and
prevent follow on attacks or similar incidents in the future Drag and drop the actions on the left to
the targets on the right in the correct order.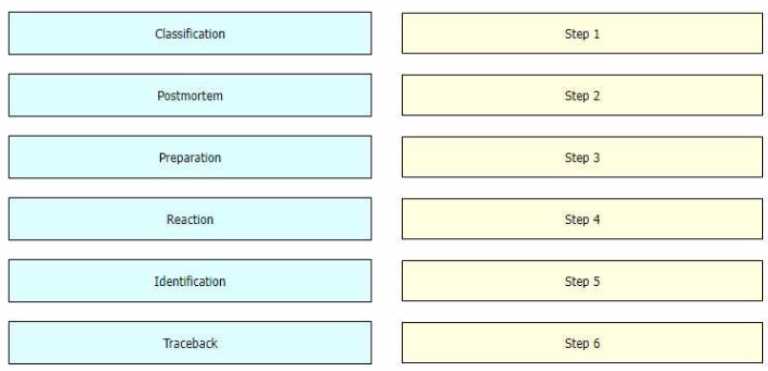
Answer:
None
Explanation:
Question 12
A company created an IPv6 adoption plan for its campus network that requires dual-stack
connectivity on the network Campus users must have IPv6 connectivity to an HR management
application which is the first IPv6-only application hosted in the company s data center. Which two
security mechanisms can be used to prevent a malicious user from masquerading as the IPv6
gateway? (Choose two)
- A. IPv6 RA guard
- B. IPv6 snooping
- C. IPv6 device tracking
- D. IPv6 address glean
- E. port ACLs
Answer:
A, D
Question 13
Most security monitoring systems use a signature-based approach to detect threats In which two
instances are systems based on Network Behavior Anomaly Detection better than signature-based
systems when it comes to detecting security threat vectors'? (Choose two.)
- A. malware detection
- B. encrypted threat traffic
- C. spyware detection
- D. intrusion threat detection
- E. new zero-day attacks
Answer:
B, E
Question 14
What are three examples of solution components of the network infrastructure that help enforce
security policy compliance on all devices as they seek to access the network and computing
resources, thereby limiting damage from emerging security threats such as viruses worms and
spyware? (Choose three.)
- A. posture agent
- B. audit and decision point servers
- C. management and reporting tools
- D. endpoint security application
- E. network access devices
- F. web filtering devices
Answer:
A, B, E
Question 15
Refer to the exhibit.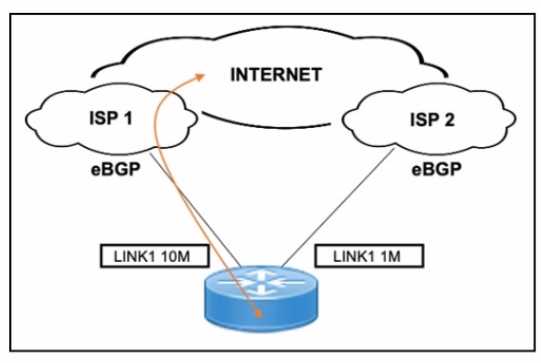
A customer needs to implement a connectivity model by using one active link for inbound and
outbound traffic and a second link for backup The backup link is low speed and is required only
during outages of the primary link. Which design solution should be implemented?
- A. Advertise a higher local preference to ISP 2 Increase the AS PATH inbound from ISP 1
- B. Advertise a longer AS PATH to ISP 2 Increase the MED to ISP 2.
- C. Advertise more specific routes to ISP 1 Increase the local preference attribute of inbound BGP from ISP1
- D. Advertise less specific routes to ISP 2 Increase the AS PATH inbound from ISP 1
Answer:
B