cisco 350-901 Exam Questions
Questions for the 350-901 were updated on : Feb 18 ,2026
Page 1 out of 29. Viewing questions 1-15 out of 434
Question 1
DRAG DROP
Refer to the exhibit.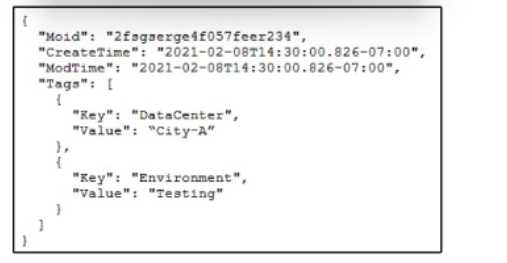
Refer to the exhibit. An engineer is attempting to retrieve information about free resources in the
Cily-Adata center. The engineer wants to know only about resources in the testing environment. Drag
and drop the code snippets from the bottom onto the blanks in the API call to meet this requirement.
Some options may be used more than once. Not all options arc used.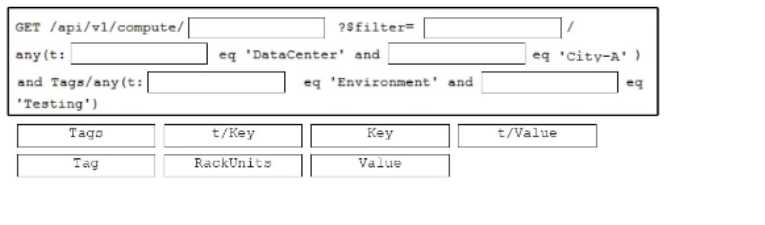
Answer:
None
Explanation:
Question 2
An engineer creates an application that manages the parsing and analysis of data. The data is
continuously generated in bursts and is disrupting the performance of the application by overloading
the provided resources. The engineer wants to implement rate limiting on the receiving endpoint to
ensure that a minimum data sample from every timeframe is parsed and that no more than a specific
number of requests are processed each time. Which rate limiting algorithm must the engineer use?
- A. leaky bucket
- B. sliding window
- C. fixed window
- D. event queue
Answer:
A
Question 3
DRAG DROP
Drag and drop the code snippets from the bottom onto the blanks in the cURL script that uses
RESTCONF to update an interface on a Cisco IOS XE device. Not all options are used.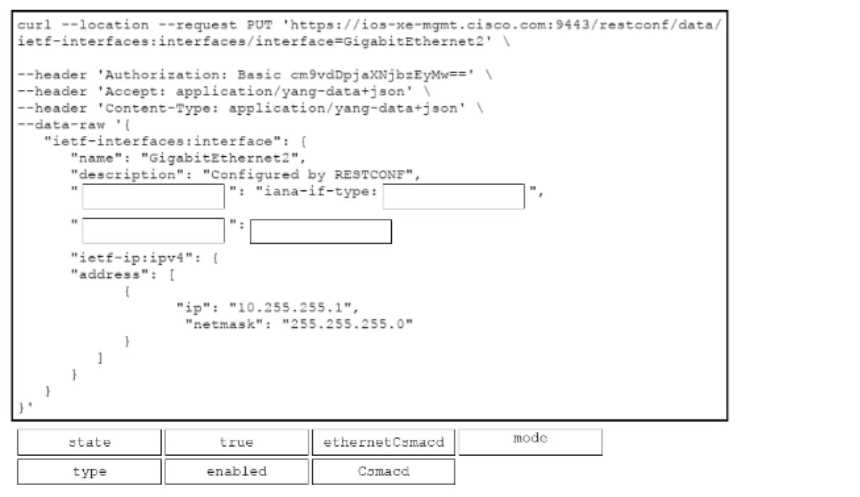
Answer:
None
Explanation: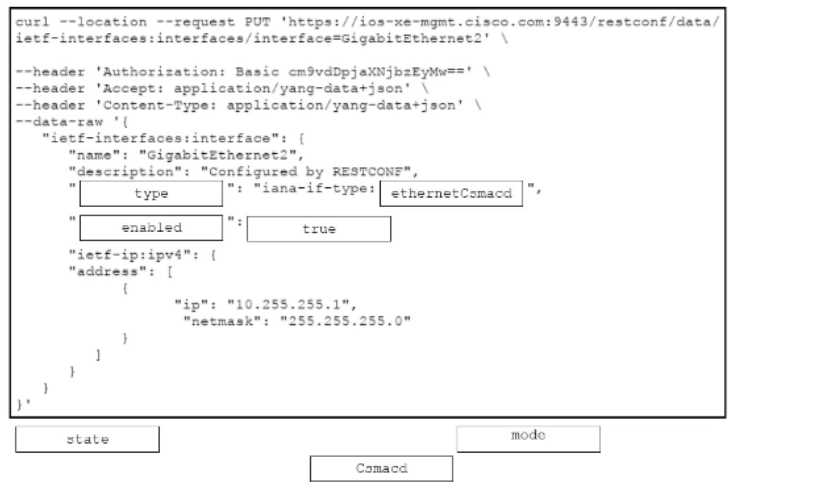
Question 4
DRAG DROP
Refer to the exhibit.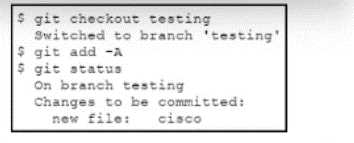
Refer to the exhibit. A new file named Cisco is added to a branch named testing, but it has not been
committed. Drag and drop the Git commands from the left into the order on the right to merge the
testing branch, with the new Cisco frte. into the master branch. Not all options are used.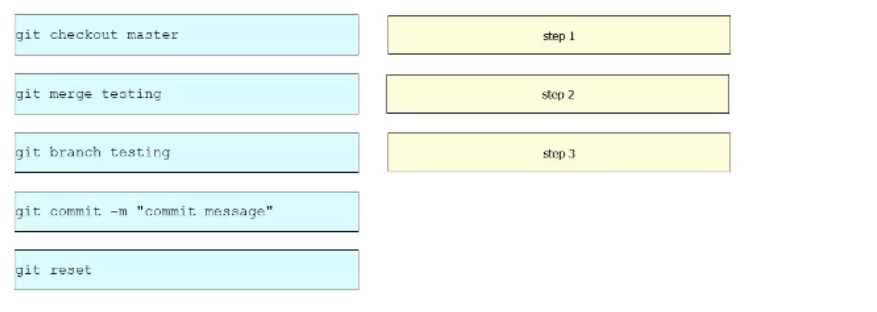
Answer:
None
Explanation: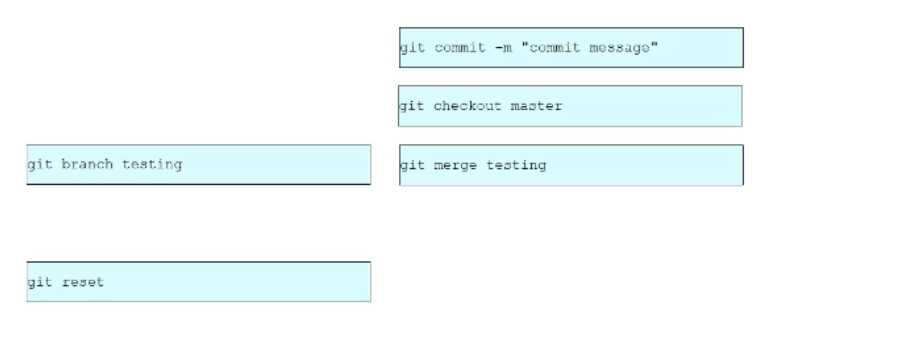
Question 5
What is the first step in the OAuth2 Authorization code grant flow?
- A. Request authorization from the resource owner.
- B. Receive an authorization code from the resource server.
- C. Mutual authentication between client and server.
- D. Authorization tokens are exchanged.
Answer:
A
Question 6
DRAG DROP
Drag and drop the code snippets from the bottom onto the blanks in the Python script to provision a
new Cisco UCS server by using a specific template. Not all options are used.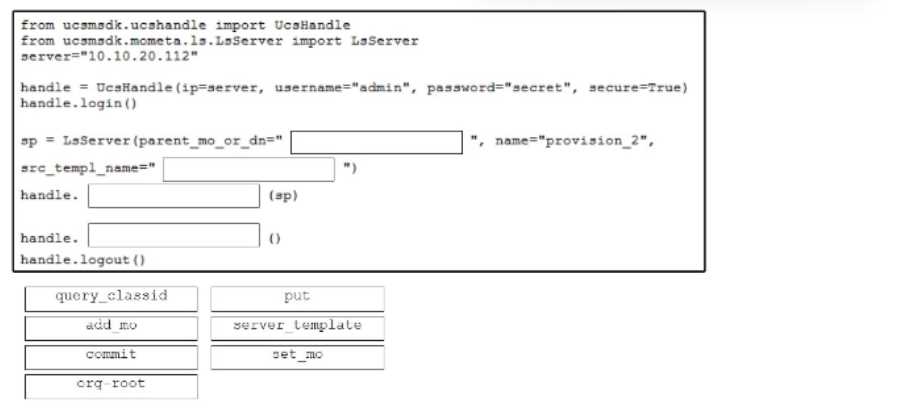
Answer:
None
Explanation:
Question 7
Which load-balancing algorithm balances loads based on configurations to determine the traffic
handling capacity of a server?
- A. sticky session
- B. least connections
- C. weighted round robin
- D. IP source affinity
Answer:
C
Question 8
DRAG DROP
Drag and drop the code snippets from the bottom onto the blanks in the Python script to retrieve a
list of all the Cisco Webex rooms using pagination and the Webex API. Not all options are used.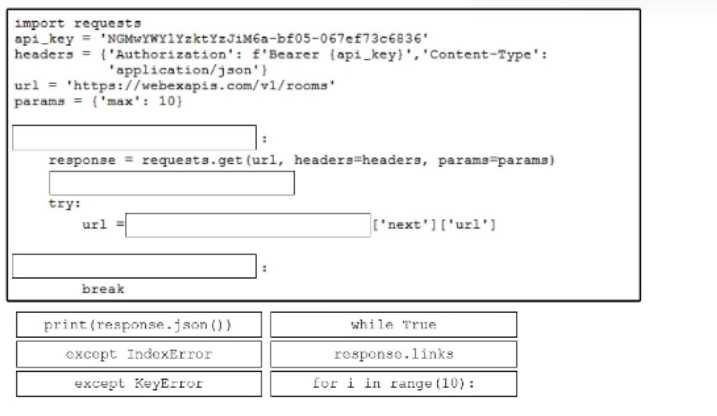
Answer:
None
Explanation: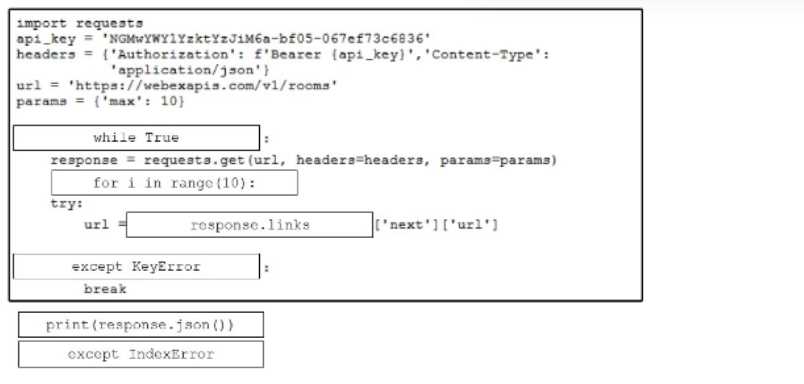
Question 9
DRAG DROP
Drag and drop the code snippets from the bottom onto the blanks in the code to deploy the last
version of a previously created Python Flask application called app-updates onto a Kubernetes
cluster. Not all options ate used.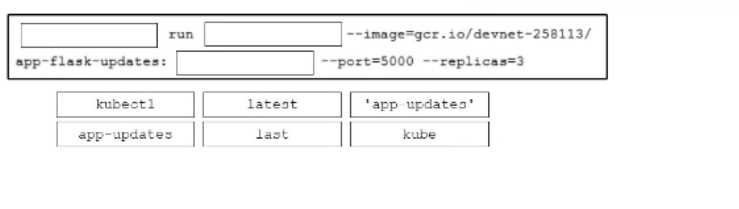
Answer:
None
Explanation: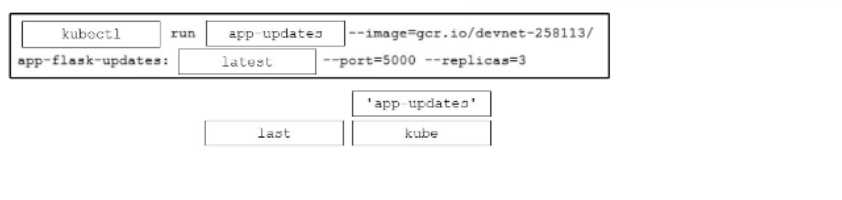
Question 10
Which authorization steps are required to obtain an access token according to the OAuth2
authorization code grant flow?
- A. Log in with a username and password using a form, get a token, and include the token in the body.
- B. Send the base64 encoded username, password, client ID, and client secret to the single sign-on manager.
- C. Send the client ID and client secrets by using the grant flow type, get the token, and authorize by using a callback.
- D. Authenticate, get the authorization code, and send it with the client ID and client secret.
Answer:
D
Question 11
DRAG DROP
Refer to the exhibit.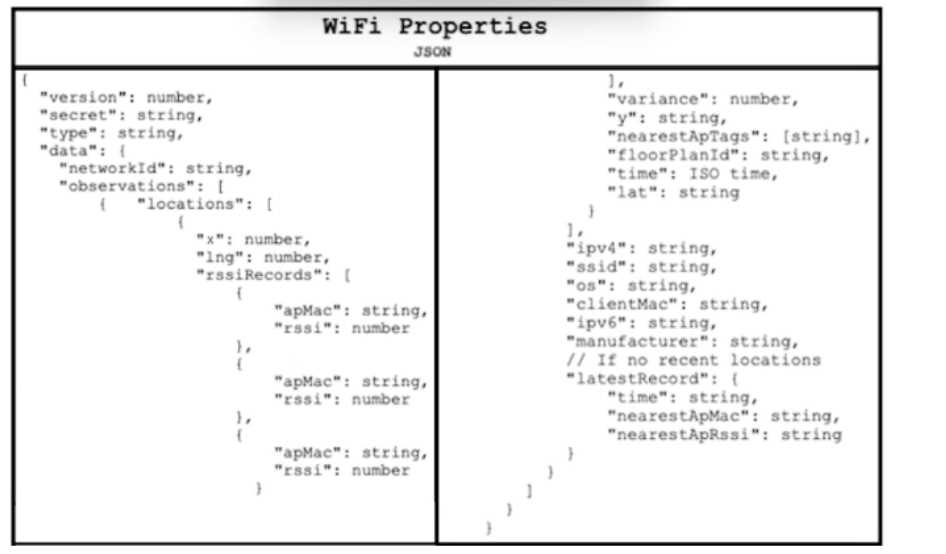
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the Python
script to retrieve location data from the Cisco Meraki Location API by using a webhook receiver. Not
all options are used.
Answer:
None
Explanation: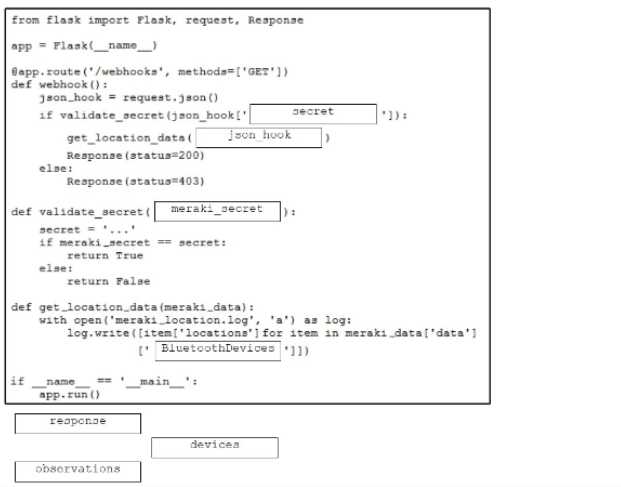
Question 12
An engineer is managing the development of an application hosted in the Python Django framework.
A remote database for state deposition and containerized microservices are used for the application
logic. Which two monitoring solutions enable the application observability to assist with
troubleshooting and debugging? (Choose two.)
- A. security information and event management
- B. resource utilization monitor
- C. integrated configuration environment
- D. Cisco Intersight view
- E. continuous deployment pipeline
Answer:
B, E
Question 13
DRAG DROP
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the code to
complete the playbook for creation of an Ansible role that configures VPC on a Cisco Nexus switch.
Not all options are used.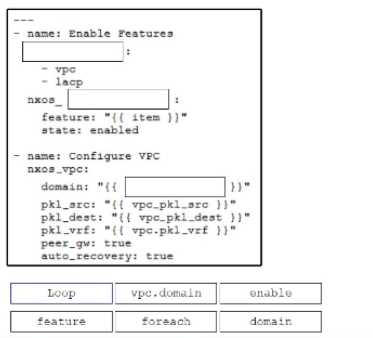
Answer:
None
Explanation: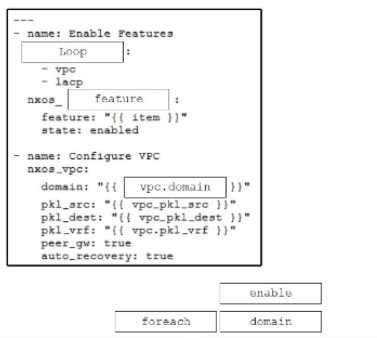
Question 14
During the final step in the OAuth2 authorization process, what must the client send to the OAuth
authorization server to obtain a data access token?
- A. resource owner's permission
- B. refresh access token
- C. authorization challenge request
- D. short-lived access code
Answer:
D
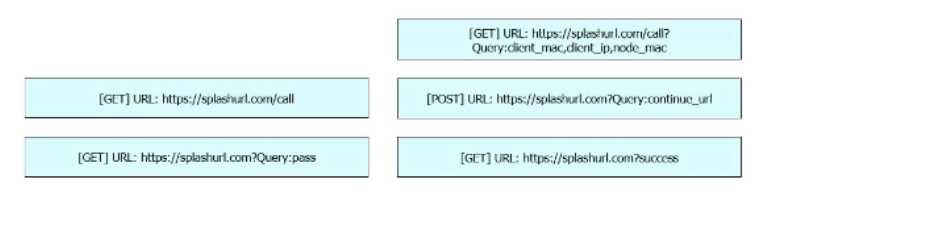
Question 15
DRAG DROP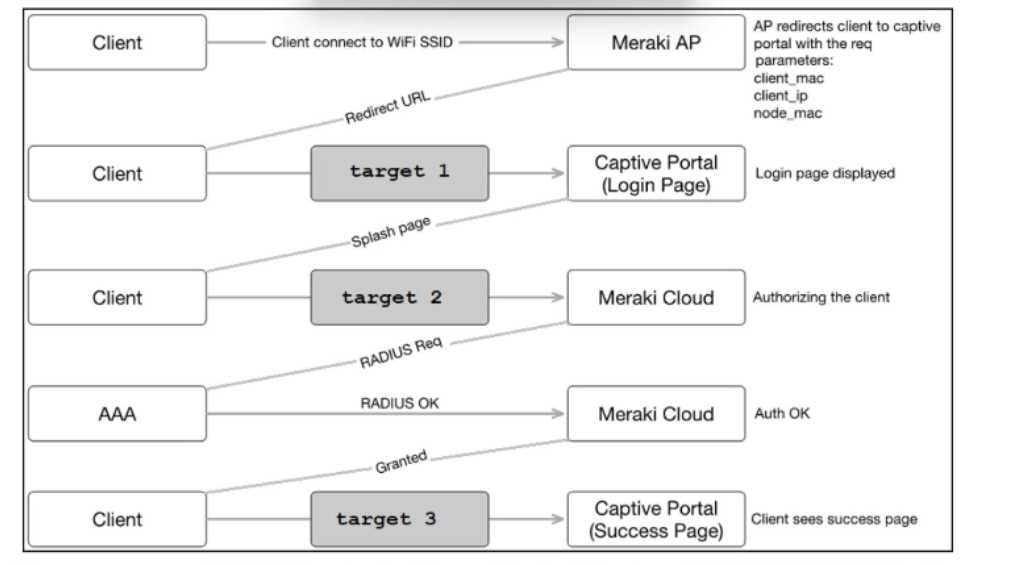
Refer to the exhibit. Drag and drop the code snippets from the left onto the targets on the right to
complete the Cisco Meraki Captive Portal REST API call. Not all options are used.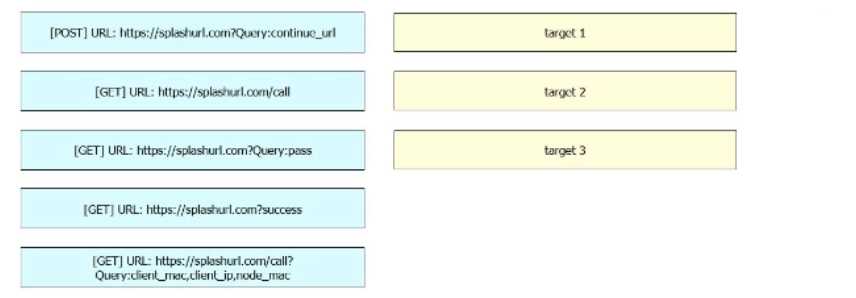
Answer:
None
Explanation: