cisco 350-701 Exam Questions
Questions for the 350-701 were updated on : Feb 18 ,2026
Page 1 out of 49. Viewing questions 1-15 out of 727
Question 1
For which type of attack is multifactor authentication an effective deterrent?
- A. Ping of death
- B. Teardrop
- C. SYN flood
- D. Phishing
Answer:
D
Question 2
An engineer is deploying a Cisco Secure Email Gateway and must configure a sender group that
decides which mail policy will process the mail. The configuration must accept incoming mails and
relay the outgoing mails from the internal server. Which component must be configured to accept
the connection to the listener and meet these requirements on a Cisco Secure Email Gateway?
- A. RAT
- B. HAT
- C. Sender list
- D. Access list
Answer:
B
Question 3
How does a Cisco Secure Firewall help to lower the risk of exfiltration techniques that steal customer
data?
- A. Blocking UDP port 53
- B. Blocking TCP port 53
- C. Encrypting the DNS communication
- D. Inspecting the DNS traffic
Answer:
D
Question 4
What is a feature of an endpoint detection and response solution?
- A. Preventing attacks by identifying harmful events with machine learning and conduct-based defense
- B. Rapidly and consistently observing and examining data to mitigate threats
- C. Capturing and clarifying data on email, endpoints, and servers to mitigate threats
- D. Ensuring the security of network devices by choosing which devices are allowed to reach the network
Answer:
B
Question 5
What are two differences between a Cisco Secure Web Appliance that is running in transparent mode
and one running in explicit mode? (Choose two.)
- A. The Cisco Secure Web Appliance responds with its own IP address only if it is running in transparent mode.
- B. When the Cisco Secure Web Appliance is running in transparent mode, it uses the Secure Web Appliance's own IP address as the HTTP request destination.
- C. The Cisco Secure Web Appliance responds with its own IP address only if it is running in explicit mode.
- D. The Cisco Secure Web Appliance is configured in a web browser only if it is running in transparent mode.
- E. The Cisco Secure Web Appliance uses a Layer 3 device to redirect traffic only if it is running in transparent mode.
Answer:
C, E
Question 6
An administrator has been tasked with configuring the Cisco Secure Email Gateway to ensure there
are no viruses before quarantined emails are delivered. In addition, delivery of mail from known bad
mail servers must be prevented. Which two actions must be taken in order to meet these
requirements? (Choose two.)
- A. Deploy the Secure Email Gateway in the DMZ.
- B. Use outbreak filters from Cisco Talos.
- C. Configure a recipient access table.
- D. Enable a message tracking service.
- E. Scan quarantined emails using AntiVirus signatures.
Answer:
B, E
Question 7
A security engineer is tasked with configuring TACACS on a Cisco ASA firewall. The engineer must be
able to access the firewall command line interface remotely. The authentication must fall back to the
local user database of the Cisco ASA firewall. AAA server group named TACACS-GROUP is already
configured with TACACS server IP address 192.168.10.10 and key C1sc0512222832!. Which
configuration must be done next to meet the requirement?
- A. aaa authentication ssh console LOCAL TACACS-GROUP
- B. aaa authentication ssh console TACACS-GROUP LOCAL
- C. aaa authentication serial console LOCAL TACACS-GROUP
- D. aaa authentication http console TACACS-GROUP LOCAL
Answer:
B
Question 8
In which cloud services model is the customer responsible for scanning for and mitigation of
application vulnerabilities?
- A. PaaS
- B. VMaaS
- C. IaaS
- D. SaaS
Answer:
C
Question 9
A security engineer must create a policy based on the reputation verdict of a file from a Cisco Secure
Email Gateway. The file with an undetermined verdict must be dropped. Which action must the
security engineer take to meet the requirement?
- A. Configure threshold settings for files with no score to be allowed.
- B. Set up a policy to automatically drop files with no reputation score.
- C. Implement a policy to disable file analysis.
- D. Create a policy to send a file to quarantine.
Answer:
B
Question 10
Which API technology with SDN architecture is used to communicate with a controller and network
devices such as routers and switches?
- A. REST APIs
- B. Northbound APIs
- C. Unprotected APIs
- D. Southbound APIs
Answer:
D
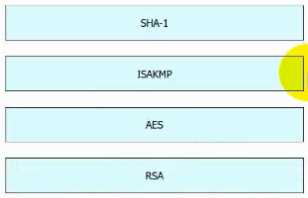
Question 11
DRAG DROP
Drag and drop the VPN functions from the left onto the descriptions on the right.
Answer:
Question 12
A network administrator needs a solution to match traffic and allow or deny the traffic based on the
type of application, not just the source or destination address and port used. Which kind of security
product must the network administrator implement to meet this requirement?
- A. Next-generation Intrusion Prevention System
- B. Next-generation Firewall
- C. Web Application Firewall
- D. Intrusion Detection System
Answer:
B
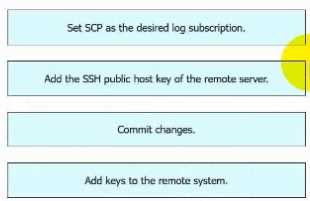
Question 13
DRAG DROP
An engineer must configure AsyncOS for Cisco Secure Web Appliance to push log files to a syslog
server using the SCP retrieval method. Drag and drop the steps from the left into the sequence on
the right to complete the configuration.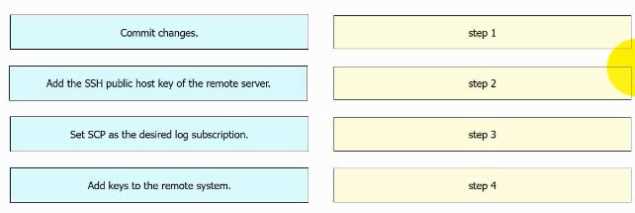
Answer:
Question 14
Refer to the exhibit.
Refer to the exhibit. An engineer must configure an incoming mail policy so that each email sent
from [email protected] to a domain of @cisco.com is scanned for antispam and advanced
malware protection. All other settings will use the default behavior. What must be configured in the
incoming mail policy to meet the requirements?
- A. Policy Name: Default Policy Sender: [email protected] Recipient: @cisco.com
- B. Policy Name: usera1 policy Sender: [email protected] Recipient: @cisco.com
- C. Policy Name: Anti-Malware policy Sender: [email protected] Recipient: @cisco.com
- D. Policy Name: cisco.com policy Sender: [email protected] Recipient: @cisco.com
Answer:
B
Question 15
A company deploys an application that contains confidential data and has a hybrid hub-and-spoke
topology. The hub resides in a public cloud environment, and the spoke resides on-premises. An
engineer must secure the application to ensure that confidential data in transit between the hub-
and-spoke servers is accessible only to authorized users. The engineer performs these configurations:
Segregation of duties
Role-based access control
Privileged access management
What must be implemented to protect the data in transit?
- A. MD5
- B. AES-256
- C. SHA-512
- D. TLS 1.3
Answer:
D